Asset Discovery & Vulnerability Scanning
This workflow is designed to identify vulnerabilities and gather information about the technologies and web servers in an infrastructure. It produces several output files, including a list of vulnerabilities ranked by severity, a list of open ports, details about the technologies used in the infrastructure, a list of available web servers, and a zip file containing screenshots of those web servers. These outputs can be used to assess the security of the infrastructure and identify any potential weaknesses that may need to be addressed.
Complexity: advanced
Category: Attack Surface Management
Workflow

Asset Discovery and Vulnerability Scanning
Tools
- amass
- subfinder
- oneforall
- vita
- cewl
- mksub
- dsieve
- puredns
- goaltdns
- naabu
- httpx
- cent
- nuclei
- webanalyze
- sslyze
- generate-yaml-report
Setup
You can set up this workflow by changing following input values:
- ROOT DOMAIN - provide root domain, e.g. trickest.com, as a target
- YOUR TRICKEST TOKEN - provide your Trickest authentication token
- YOUR WORKFLOW ID - provide the workflow's ID available in URL e.g https://trickest.io/editor/a4f61662-915f-4e15-8d94-1114152c36b3
- 1000 - optionally provide your wordlist brute-force limit
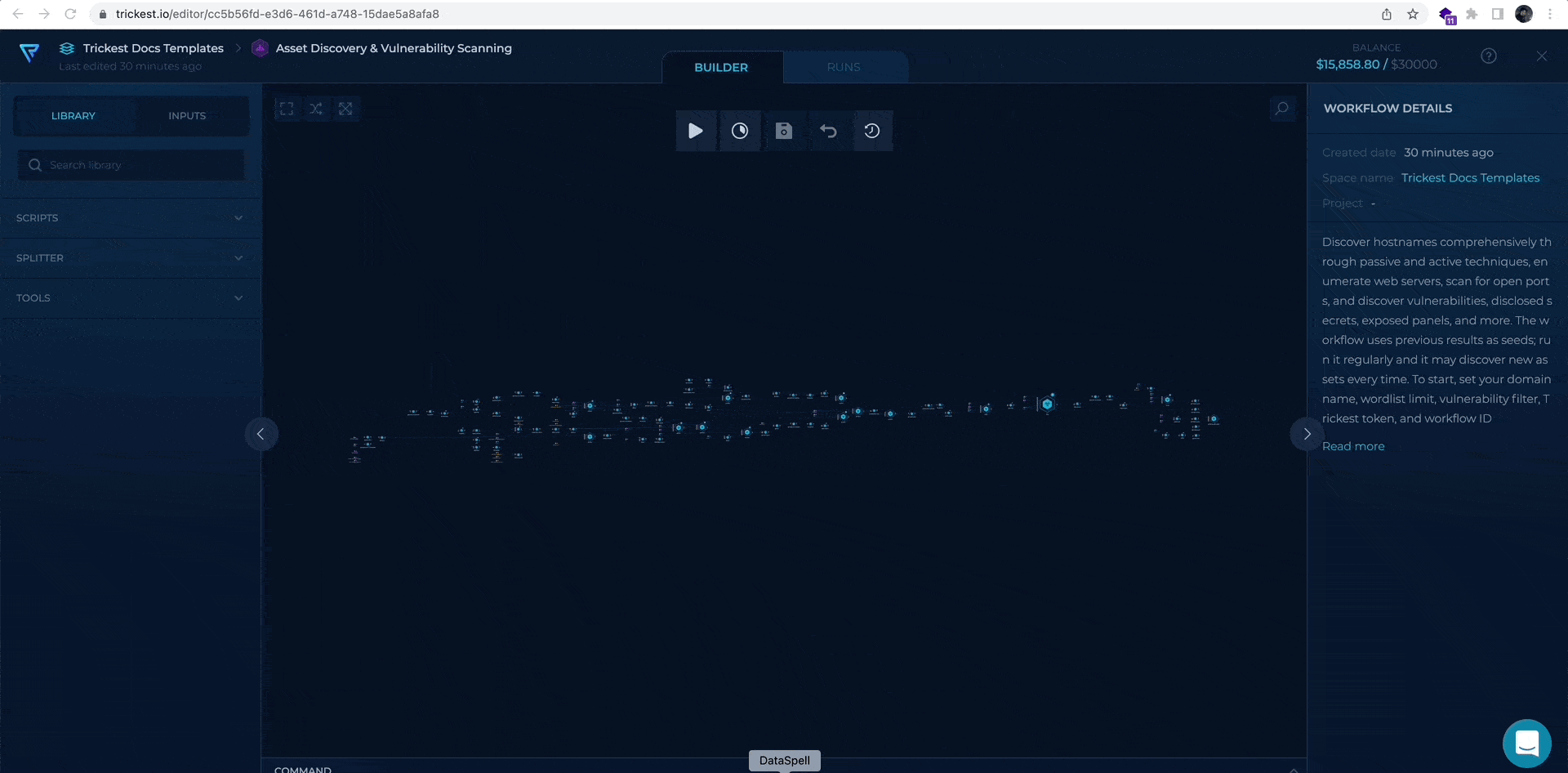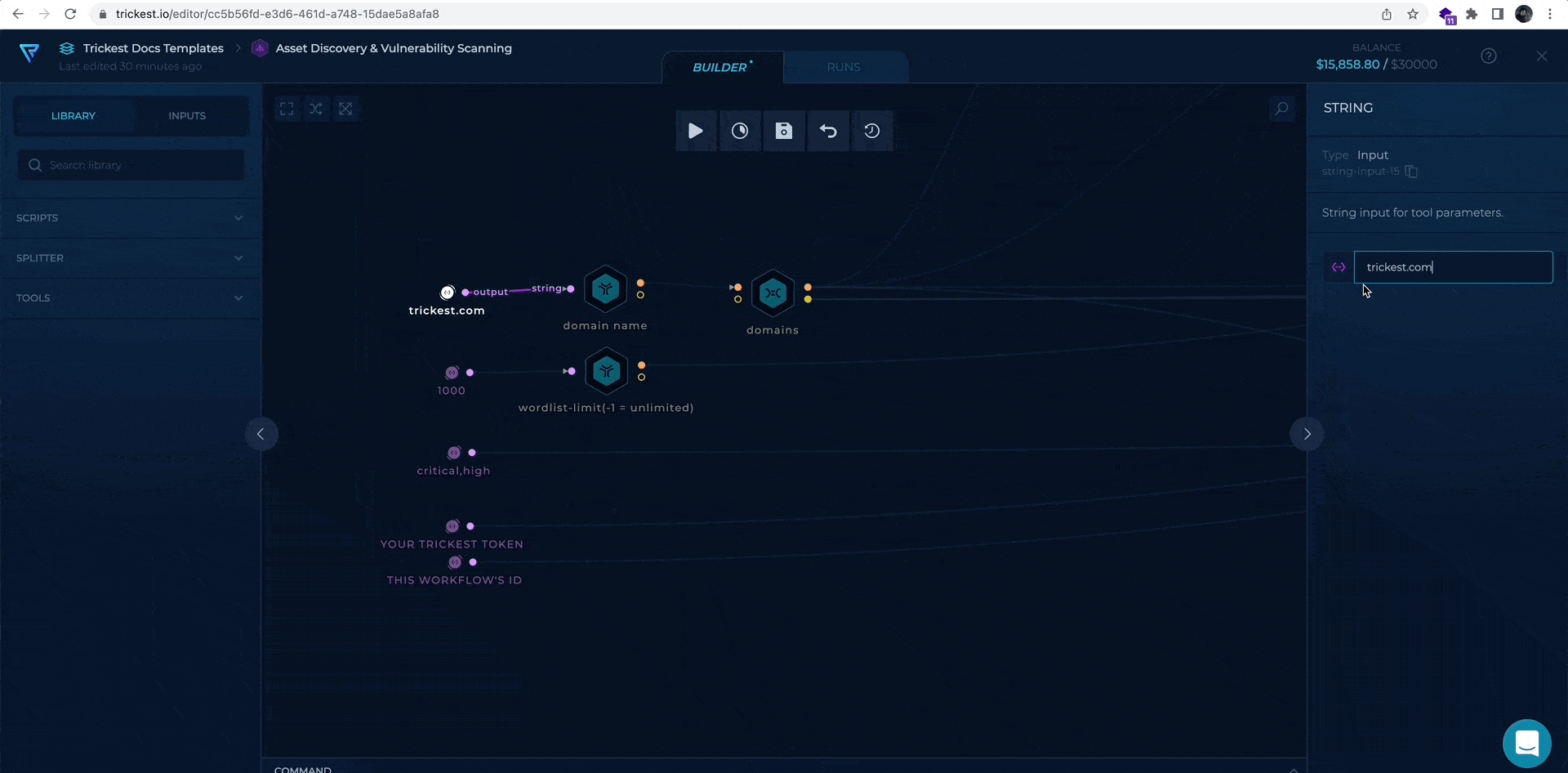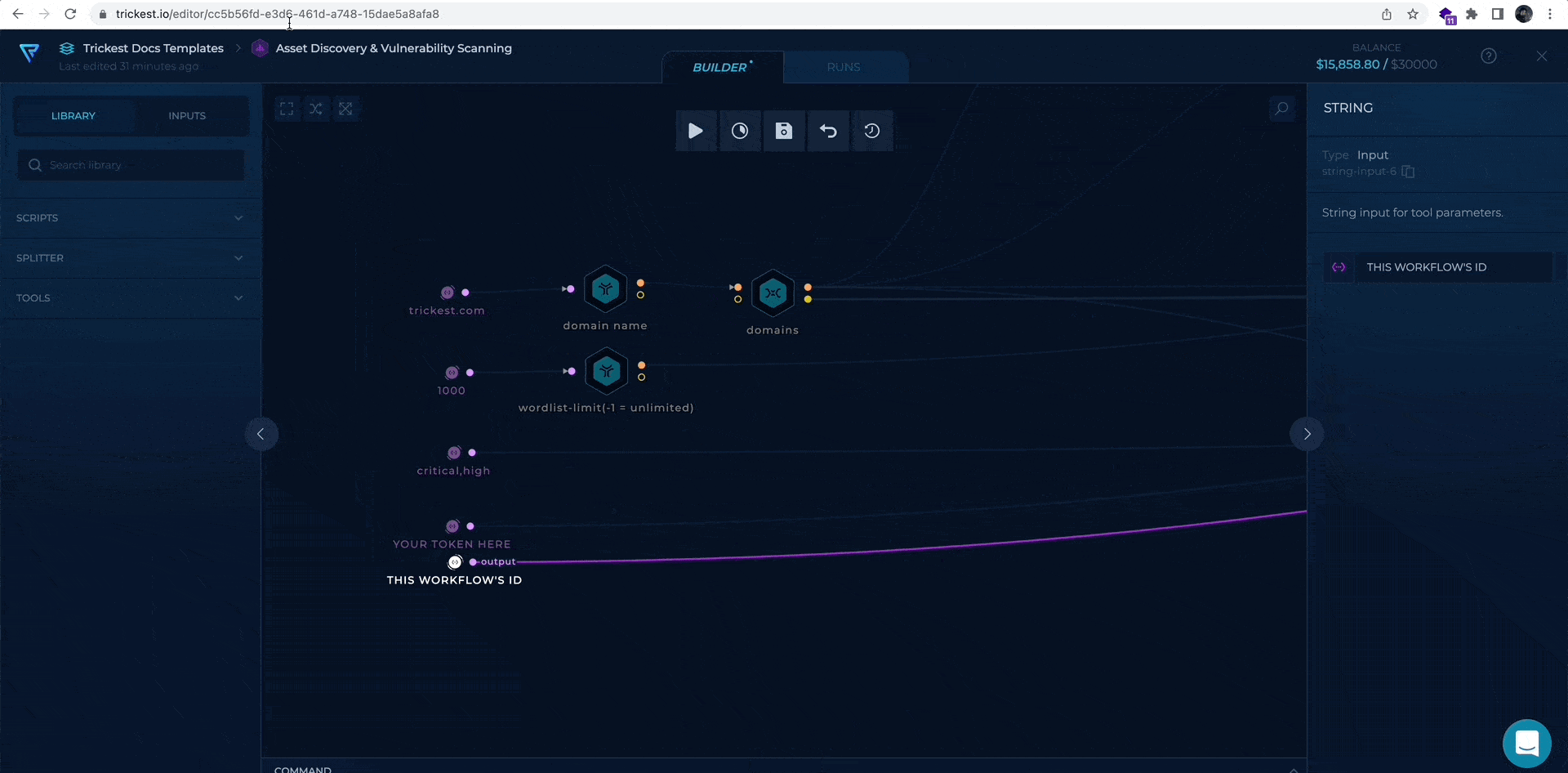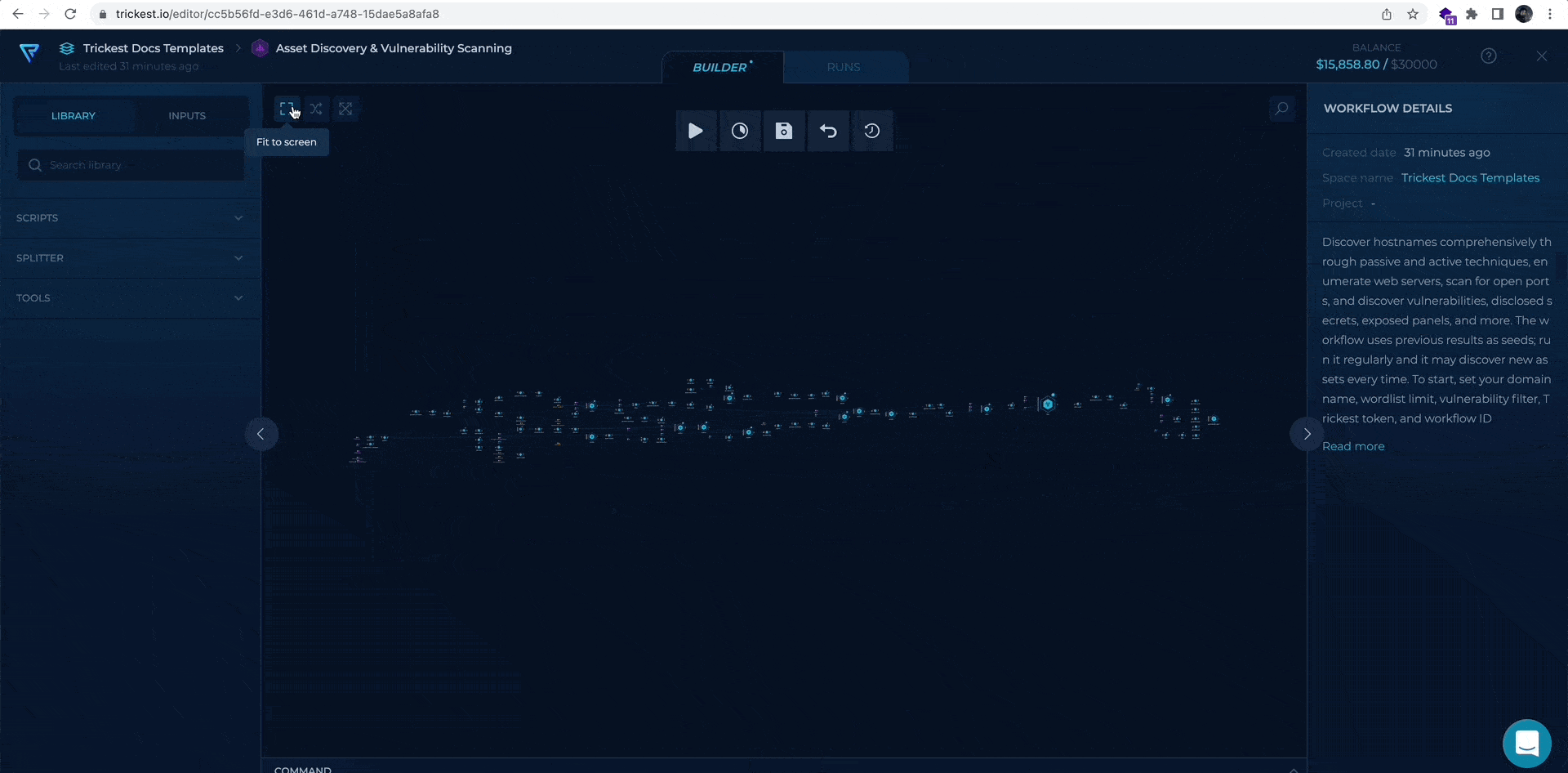
Workflow Targets Setup
Execution and results
After setup workflow is ready to be executed. Once workflow's last node, report script, is finished result can be viewed and downloaded.
report script node will contain the following files:
nuclei.json- output of nuclei containing all of the vulnerabilities connected to parameterseverityused as input to the workflowopen-ports.txt- output of naabu with all of the ports open from hostnames found in the current runtechnologies.json- output of webanalyze containing the valuable info about the infrastructure technologies from hostnames found in the current runwebservers.json- all of the available web servers from httpx;results.zip- eyeballer output containing all screenshots from found web servers

Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Check out how our CEO used Asset Discovery & Vulnerability Scanning Workflow in a Twitch session with Carlos Polop from Hacktricks!