amass
There are three versions of amass available in the Trickest library. Each one is packaged a little differently to be suitable and more convenient for a particular use case and usage pattern.
amass
This is the base version of amass, amass enum. It enumerates subdomains for a domain or a list of domains and outputs the results as a simple list of hostnames.
Basic Usage Examples
Subdomain Enumeration of One Domain
Pass a domain (e.g. trickest.io) to thedomain input (type string)
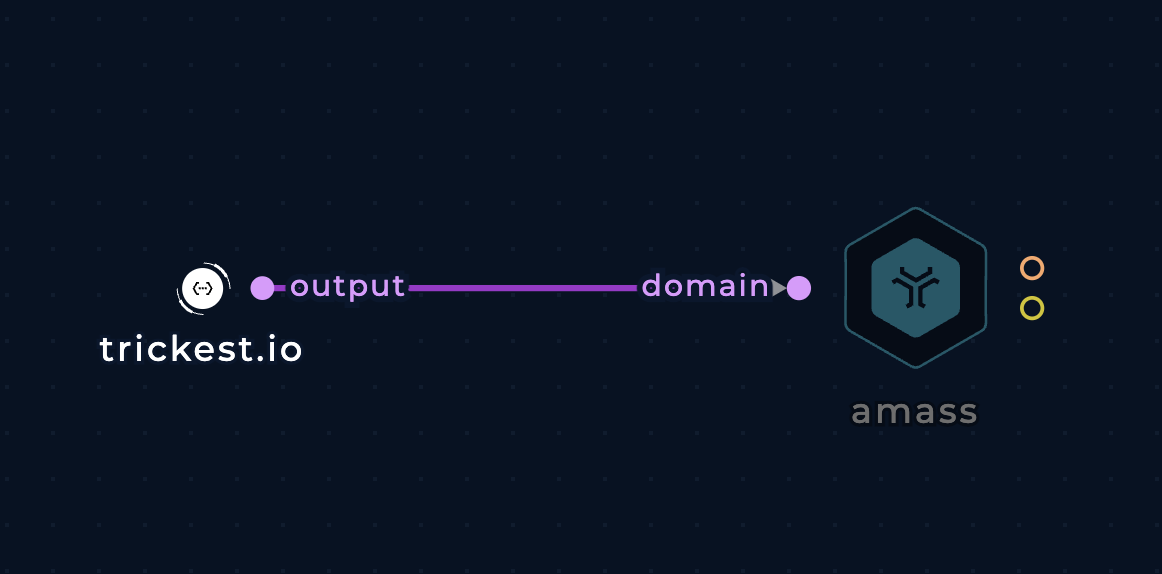
Enumerate subdomains of one domain with amass
Subdomain Enumeration of Multiple Domains
Pass a list of domains to the domain-list input (type file)
trickest.com
trickest.io
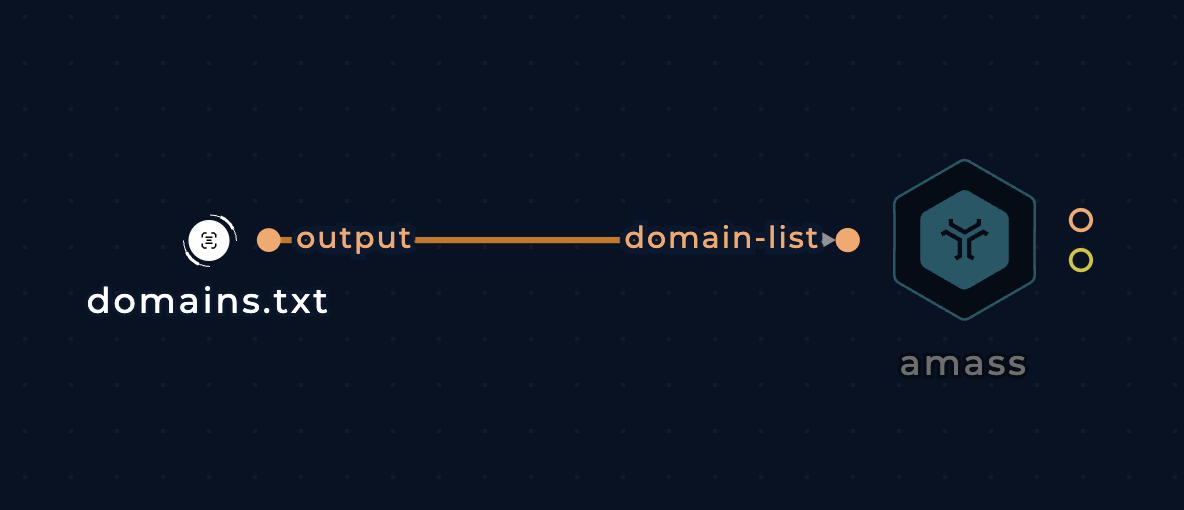
Enumerate subdomains of a list of domains with amass
Improvements
API Keys
Pass API keys to the ini-config-file parameter to allow the tool to query more data sources. Config file format (Wiki):
# Provide data source configuration information.
# See the following format:
#
# The SOURCENAME must match the name in the data source implementation.
[data_sources.SOURCENAME]
#
# Time-to-live value sets the number of minutes that the responses are cached.
ttl = 4320
#
# Unique identifier for this set of SOURCENAME credentials.
# Multiple sets of credentials can be provided and will be randomly selected.
[data_sources.SOURCENAME.CredentialSetID]
# Each data source uses potentially different keys for authentication.
apikey =
secret =
username =
password =
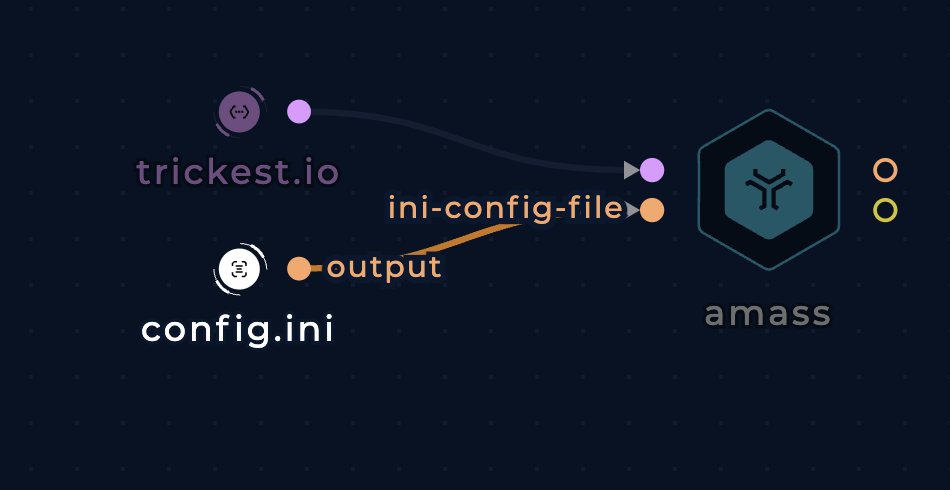
Add config.ini to amass to customize settings and query more data sources
Active methods
Use the active-methods boolean input to enable active recon methods such as zone transfer, certificate pulling, etc.
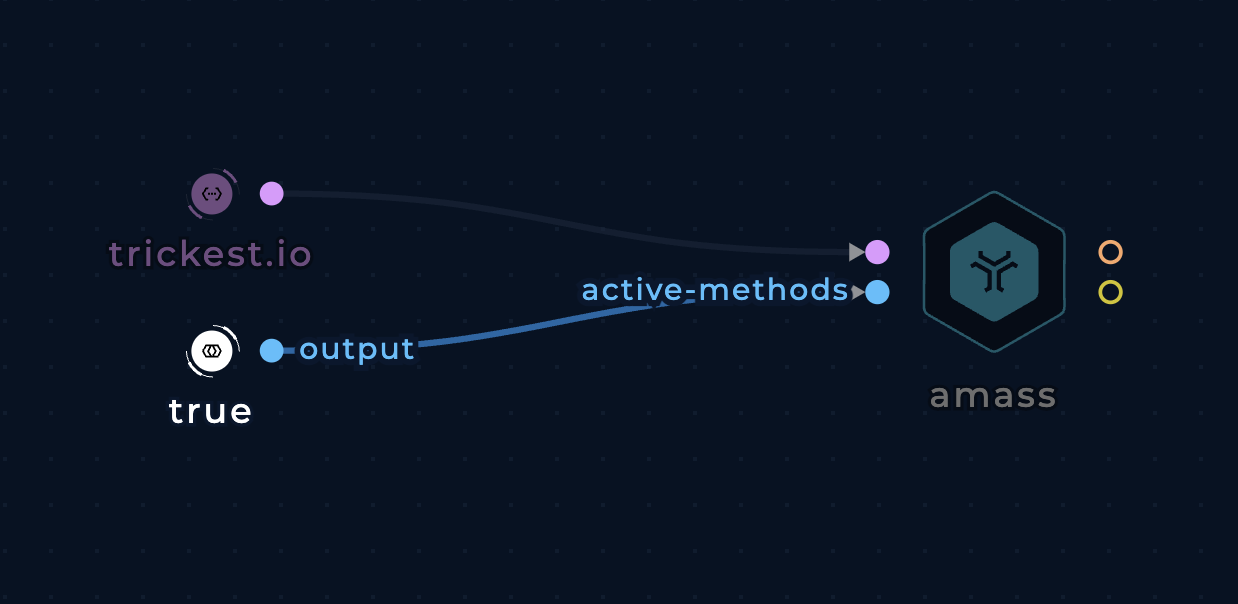
Use active recon methods with amass
Purely passive execution
Use the passive boolean input to use amass's completely passive mode that doesn't interact with the target's infrastructure.
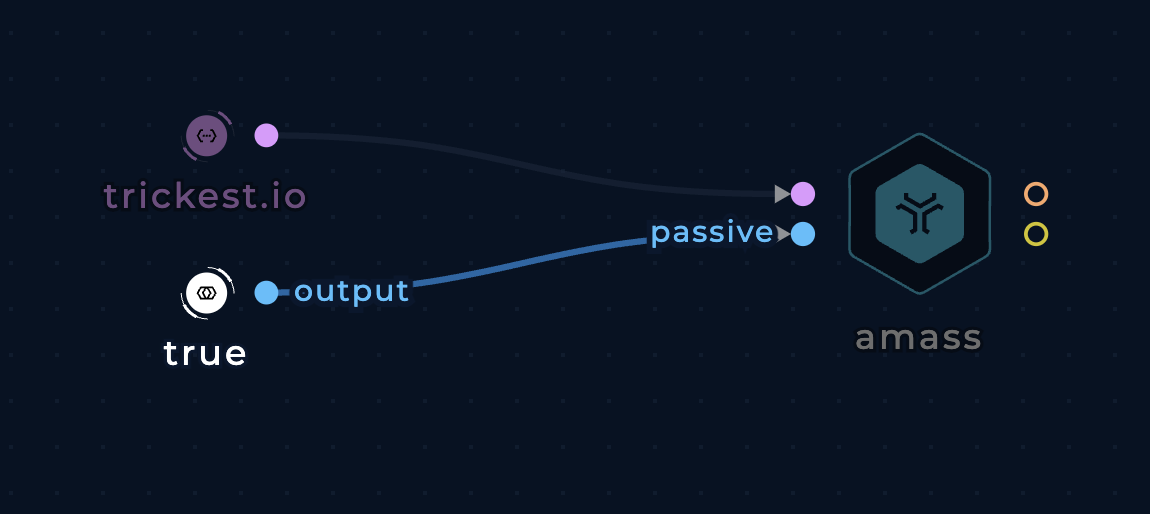
Use amass's passive mode
Show IP addresses
Use the show-ip (or show-ipv4 / show-ipv6) boolean input to include the IP addresses of each domain in the output. The output format will be a CSV file of hostnames and IP addresses with the exception that the subdomain and the IP addresses will be separated by a space (while the IP addresses are separated by commas).
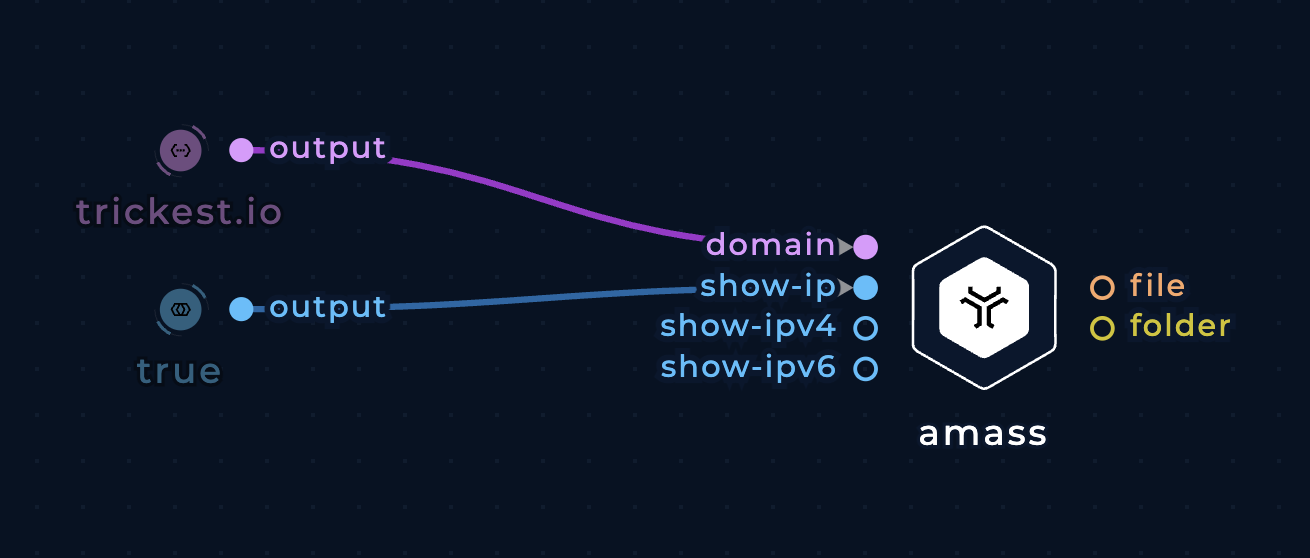
Show IP addresses in amass's output
Brute force subdomains
Use the brute-flag boolean input to brute force for subdomains. You can also use the following inputs to further customize and improve this process:
trusted-dns-resolvers-fileanduntrusted-dns-resolvers-file: Add custom resolvers. Check out the Resolvers project for a regularly validated list of resolvers and a list of trusted resolvers.wordlist-brute: Add a custom subdomain enumeration wordlist.wordlist-alterations: Add a custom subdomain alterations wordlist.
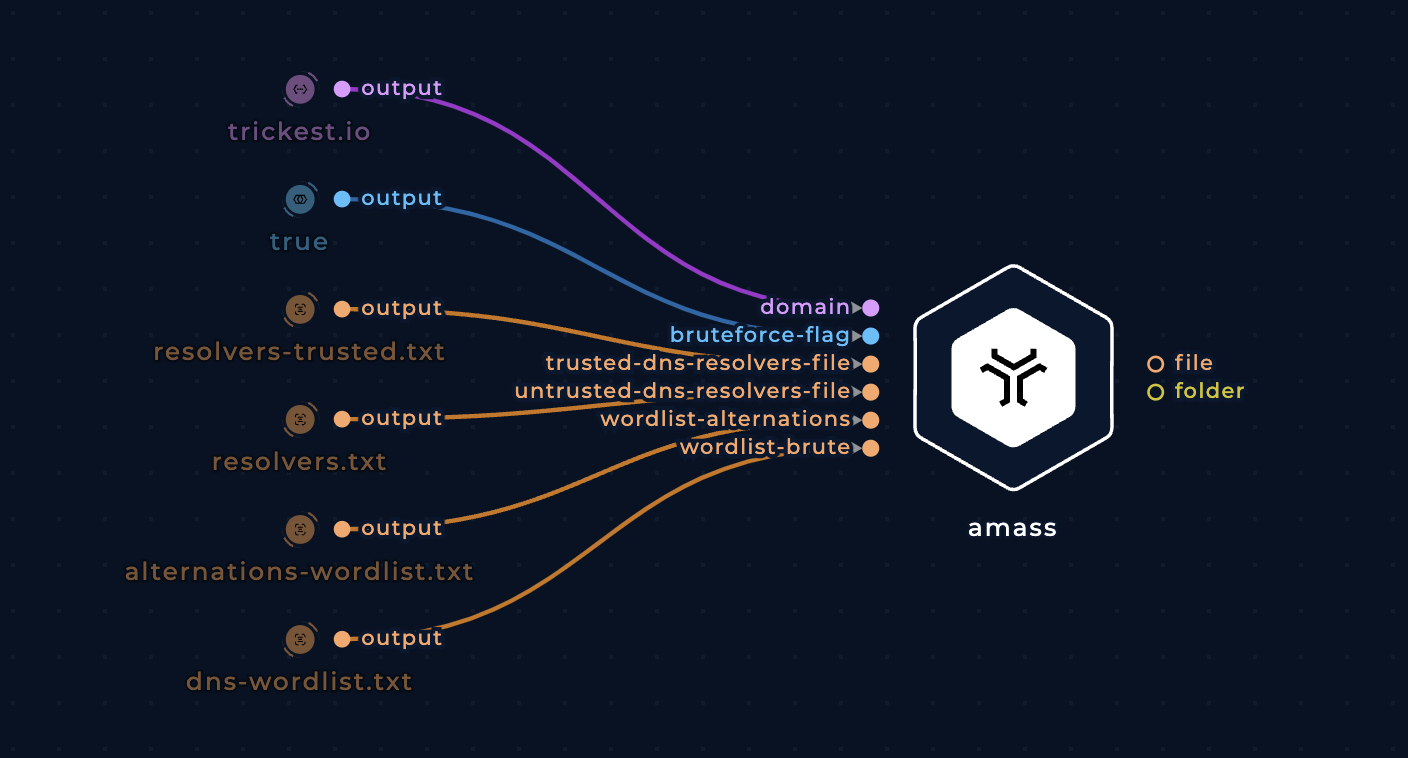
Brute force subdomains with amass
Print data sources
Use the print-data-sources to learn which data sources were used to find each subdomain.
[DNS] trickest.io
[CertSpotter] docs.trickest.io
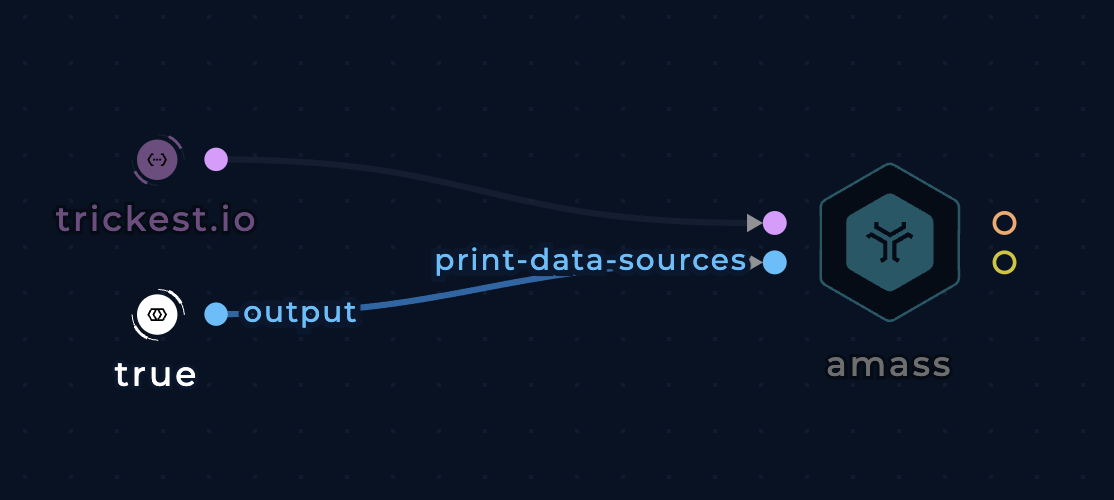
Print which data sources amass used to find each subdomain
amass-json
This version is identical to the base amass with the sole exception that it write its output to a JSON file. Every use case and improvement that applies to amass, applies to amass-json.
amass-intel
This version uses the amass intel command to discover additional root domain names associated with the organization or domain you are investigating.
Here you can find details on how to execute intel command with amass.
Warning: Before carrying out any scans on the results of this tool, we recommend that you double check the results to make sure they are in-scope and belong to your target organization.
Basic Usage Examples
Root domain enumeration with one domain as input
Use the domains string input to input one domain or multiple domains separated by spaces. Keep in mind that, in most cases, you need to specify at least one enumeration technique such as whois to get useful output.
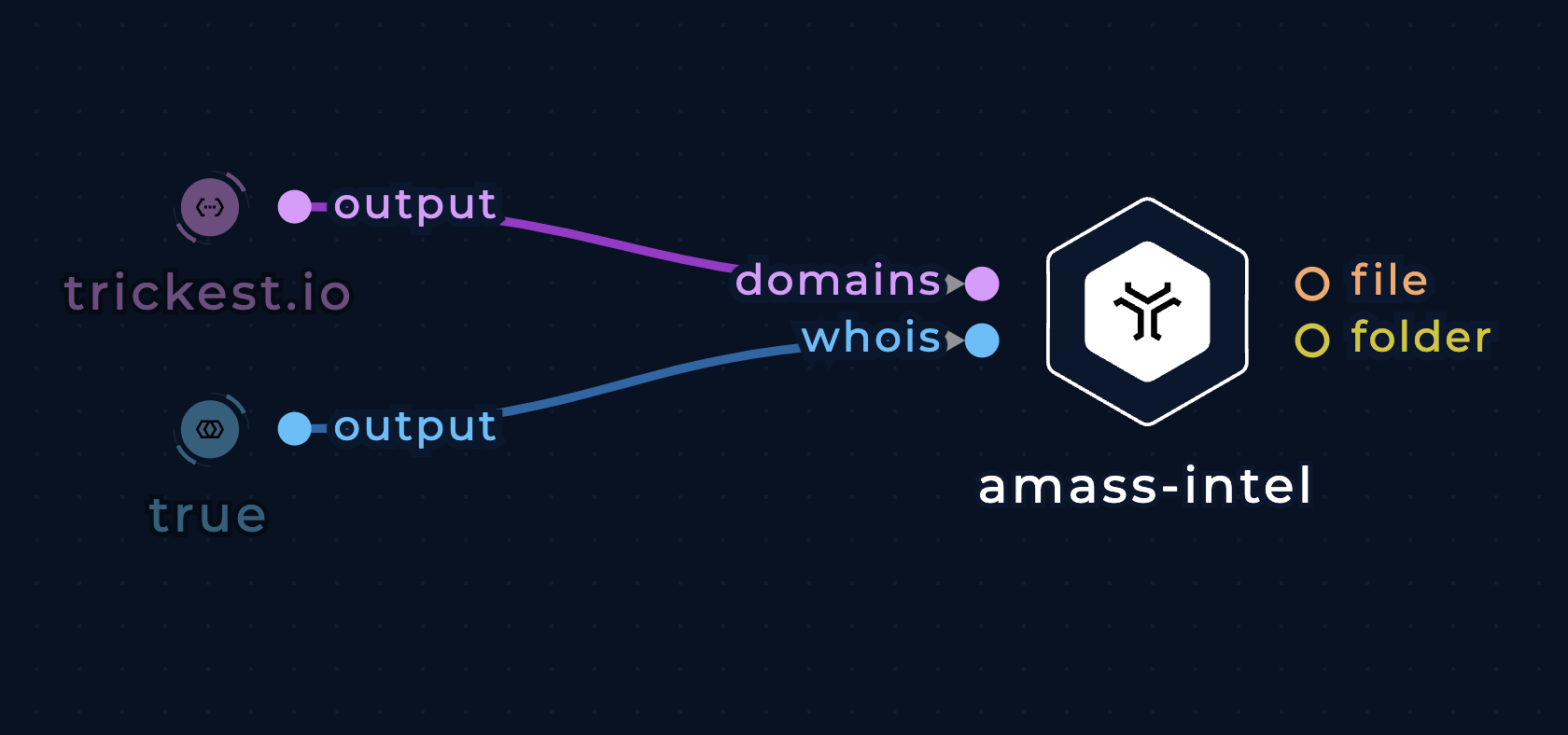
Enumerate other root domains using domain input with amass-intel
Root domain enumeration with a list of domains as input
Pass a list of domains to the df (i.e. domains file) file input.
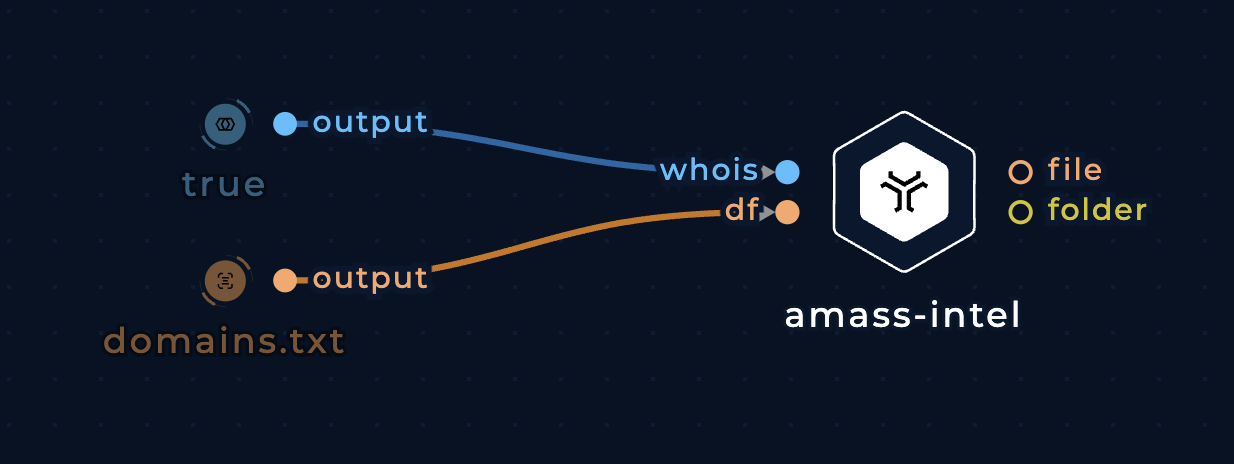
Enumerate other root domains using a list of domains with amass-intel
ASN, and IP range, and alternative organization name enumeration for an organization
Pass an organization name (e.g. Trickest) to the org string input.
ASN: 123123 - Acme Corp Limited.
127.0.0.1/24
ASN: 321321 - AS134981 - Acme Technologies LTD
192.168.0.1/8
0000:0000:000::/44
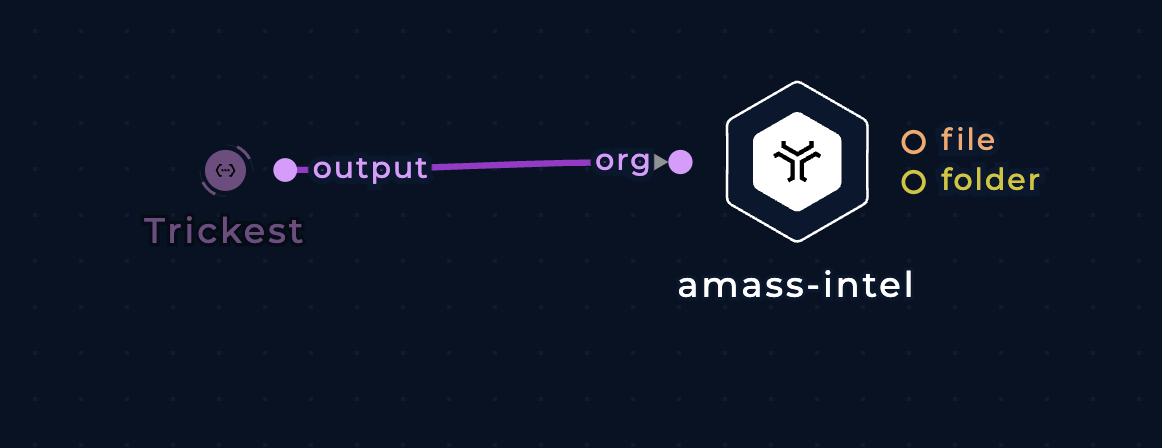
Enumerate ASNs, IP ranges, and alternative organization names with amass-intel
Root domain enumeration for a CIDR/IP range
Pass a CIDR to the cidr input or an ASN to the ASN input to discover root domains that resolve to an IP address within that range.
127.0.0.1 foo.com
127.0.0.2 bar.com
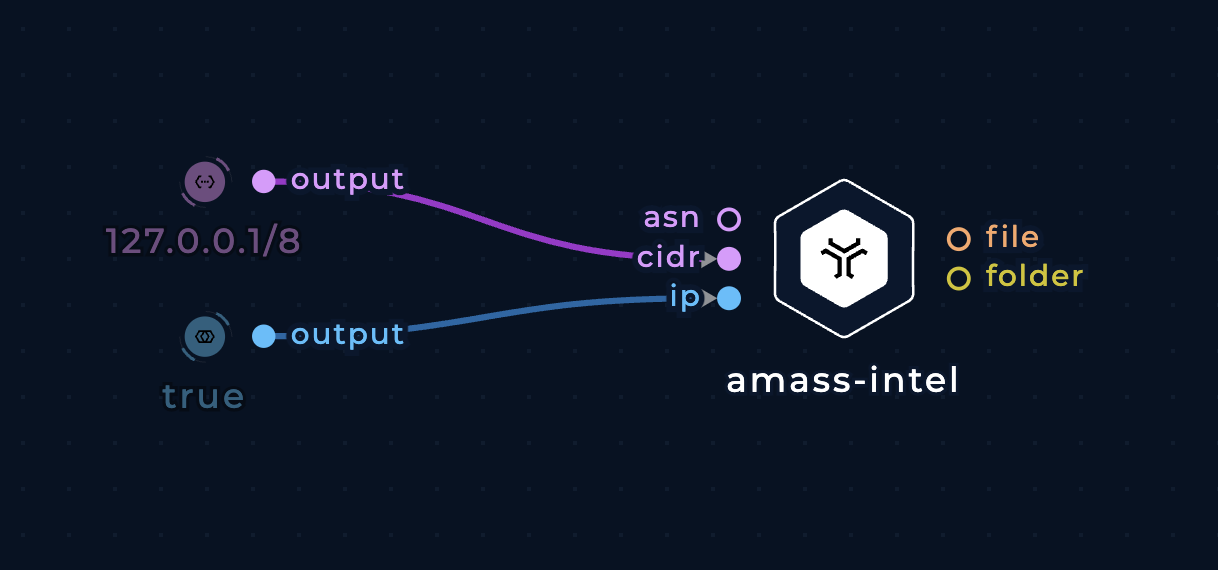
Enumerate root domains from a CIDR/IP range with amass-intel
Improvements
Most of the improvements listed under the base amass integration will apply here.