Github Recon & Scanner
Complexity: advanced
Category: Attack Surface Management
Workflow
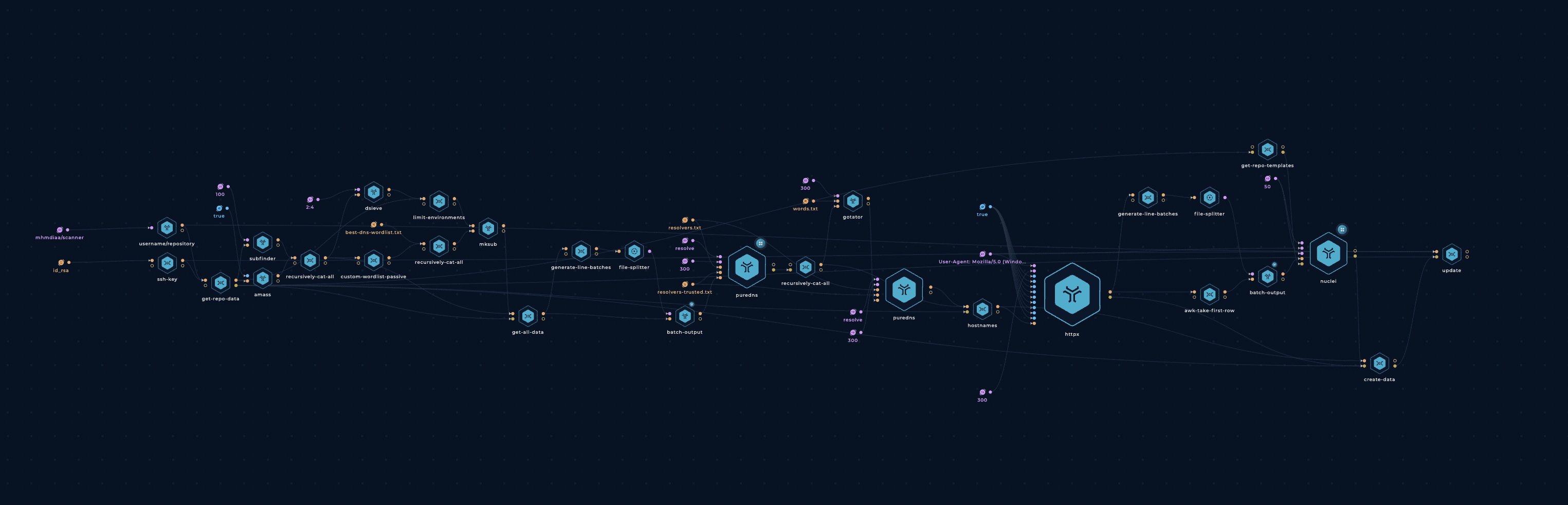
Github Recon & Scanner
Tools
Pre setup
As a pre-setup Trickest & GitHub Auth has to be provided:
- Create a new GitHub repository from the template, and find repository structure description.
- Open https://github.com/YOUR_USERNAME/YOUR_REPOSITORY/settings/secrets/actions.
- Add
TRICKEST_TOKENsecret with your Trickest token value. - Set up a GitHub deploy key with write access to your Bug Bounty Setup repository and add the private SSH key to the
SSH_KEYaction secret.
Setup and Execution
This workflow can be either set up and executed from the Platform or from the previously created GitHub repository:
Platform Setup and Execution
1. Inputs Setup
You can set up this workflow by changing following input values:
- id_rsa - provide your GitHub deploy key
- username/repository - provide your username/name of your repository previously copied from the template
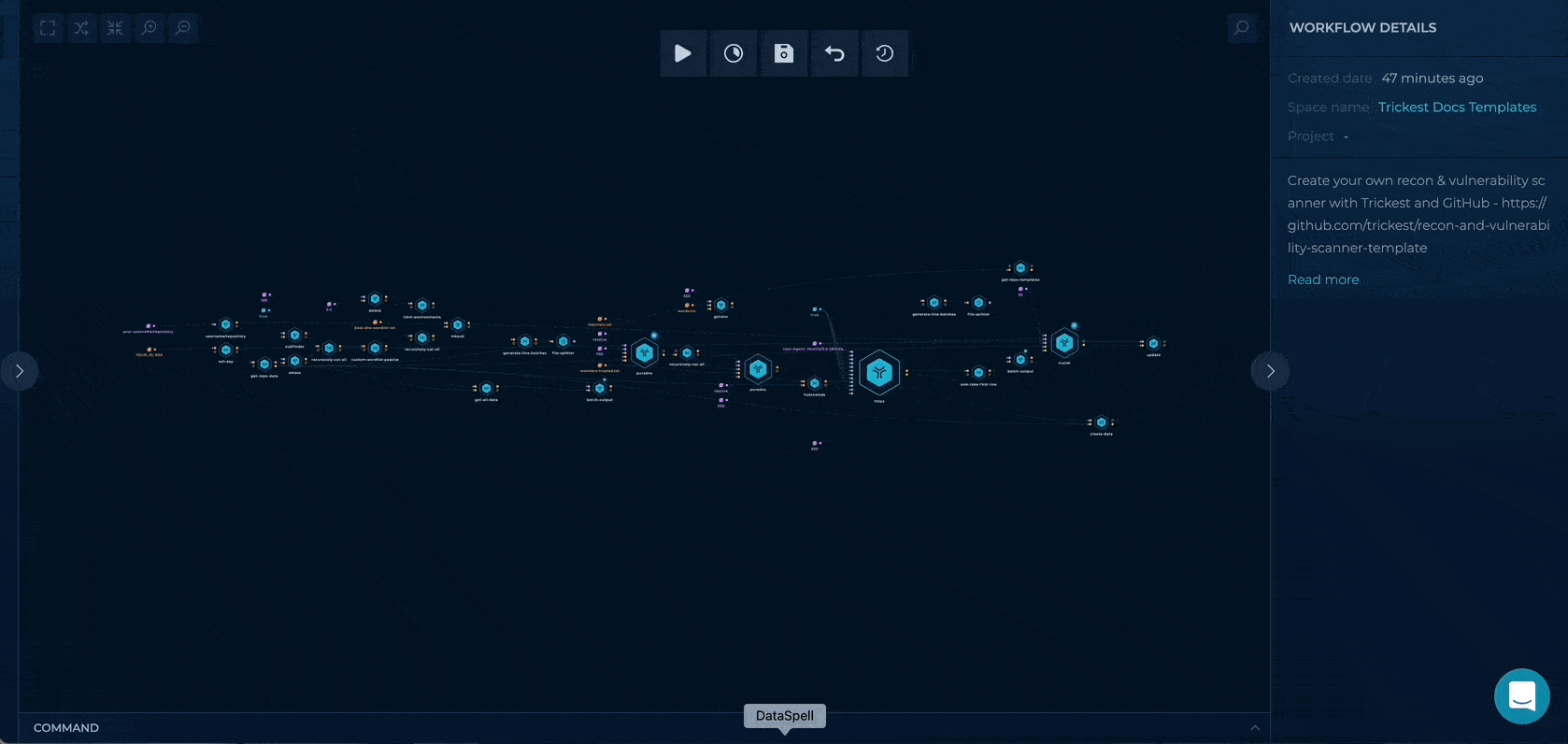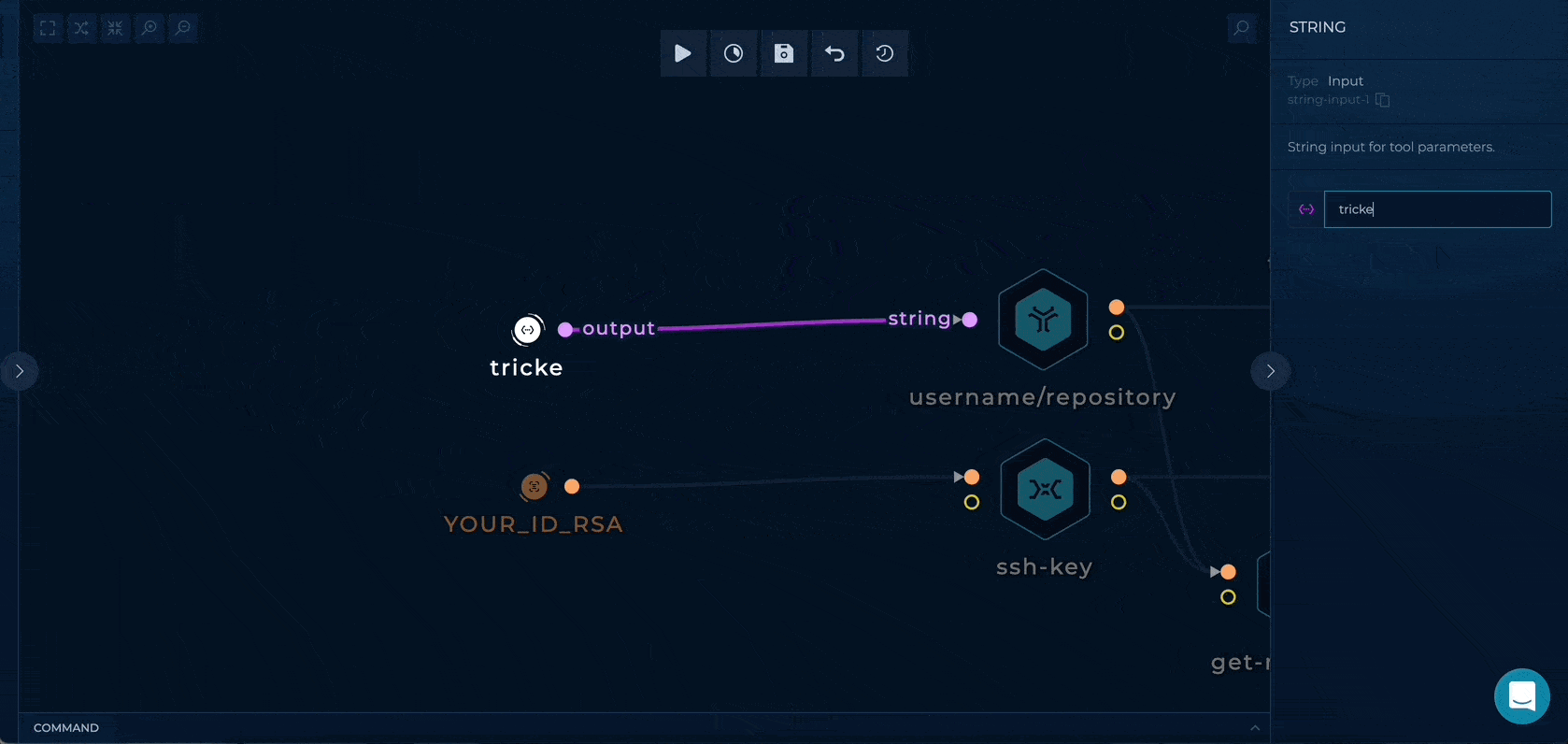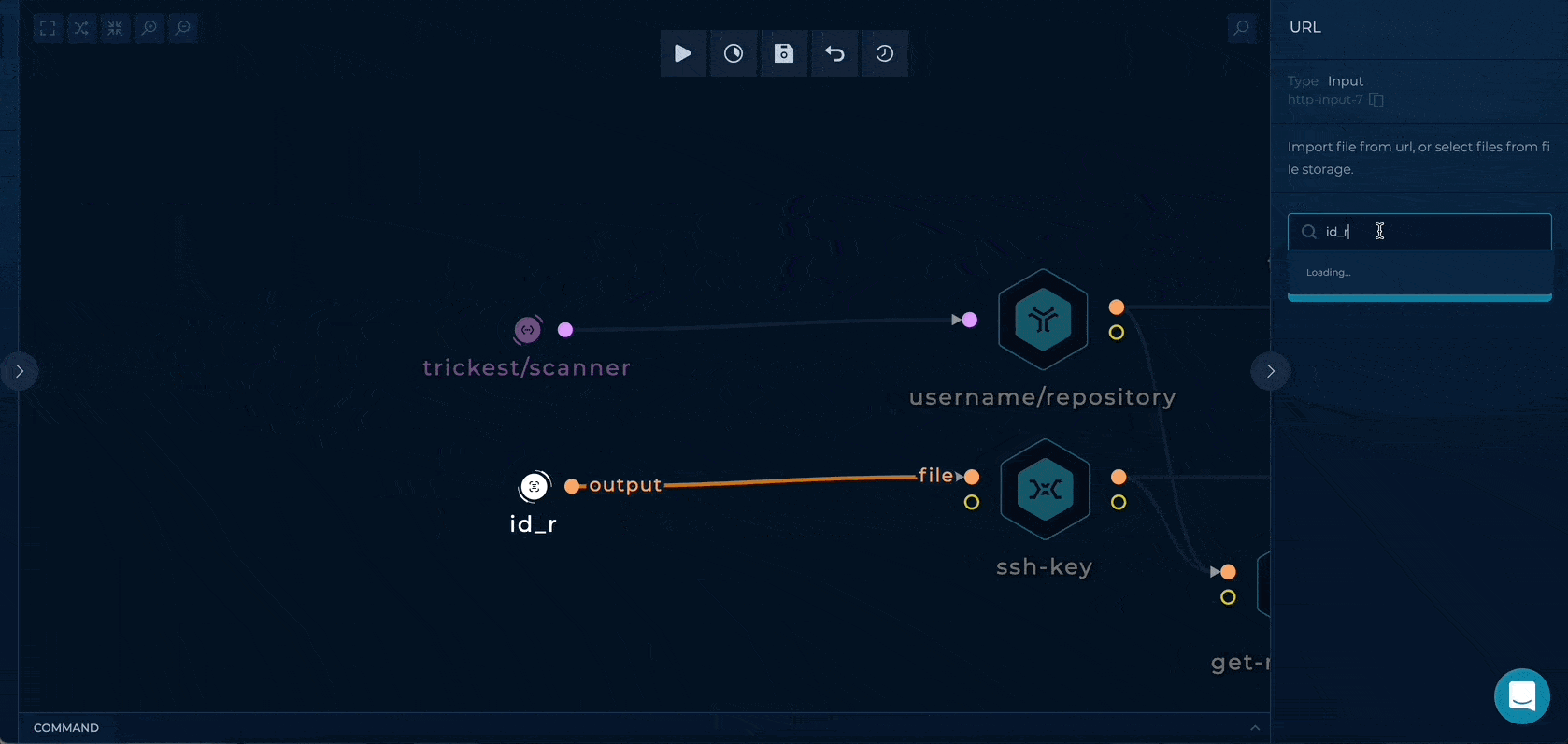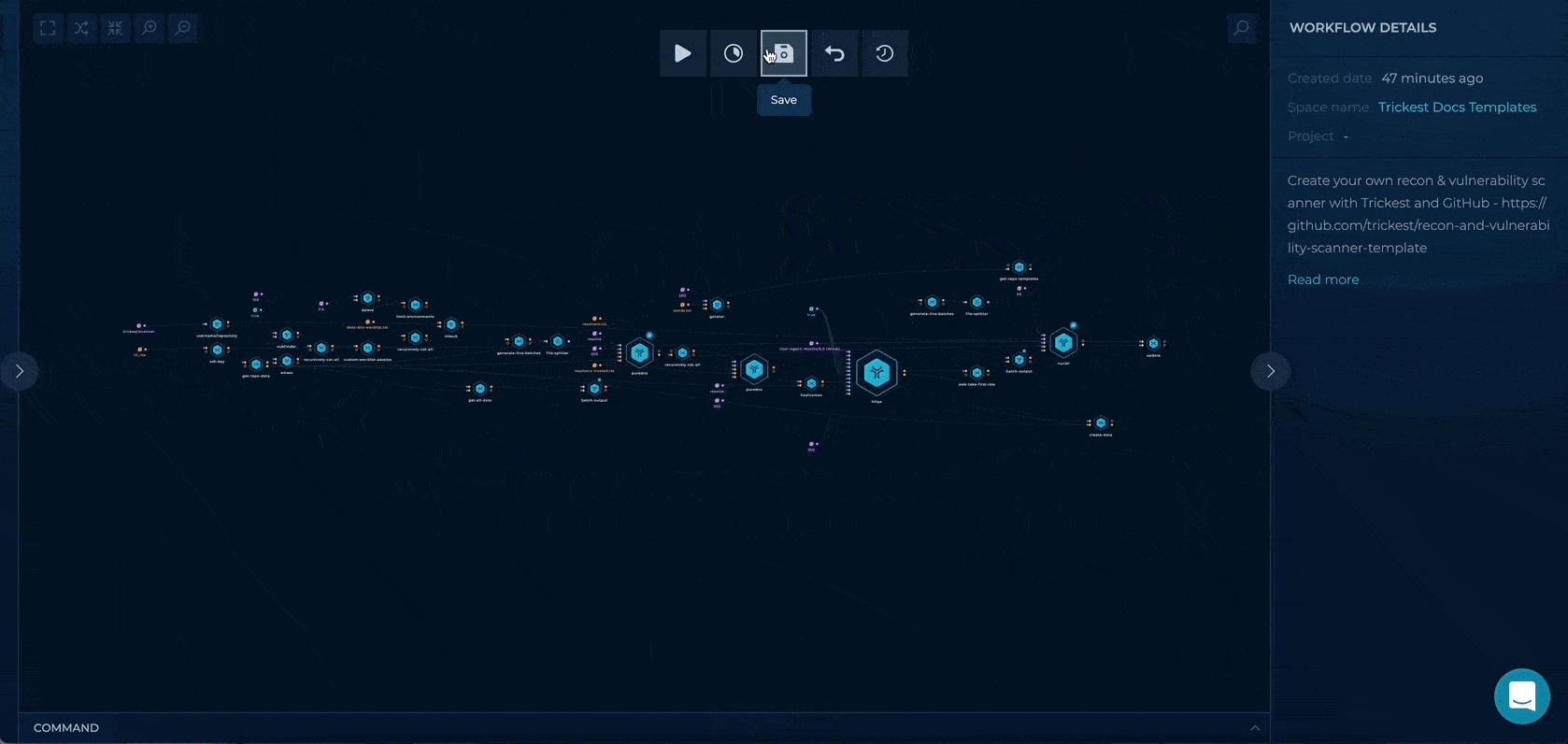
Workflow Targets Setup
2. Running the workflow
Trigger Execute action in Builder's top bar.
GitHub Setup and Execution
1. Config File Setup
Replace REPOSITORY_NAME with your GitHub repository name inside the config.yaml file.
inputs:
string-to-file-1.string: REPOSITORY_NAME
recursively-cat-all-5:
file:
- id_rsa
machines:
large: 1
2. Root Domains Setup
All of the domains will be picked up automatically by the workflow. You will need to push the new root domain names to the domains.txt file.
echo "trickest.com" > domains.txt
3. Nuclei Templates Setup
All of the nuclei templates will be picked up automatically by the workflow. Push the new nuclei templates to the templates folder.
cd templates
wget "https://raw.githubusercontent.com/projectdiscovery/nuclei-templates/master/cves/2022/CVE-2022-35416.yaml"
4. Pushing the data
When you're done adding your data/templates, commit and push
git add *
git commit -m "Add data"
git push
5. Running the workflow
The workflow is triggered on workflow_dispatch event; feel free to change the trigger the way it suits the best your use case (The push event might be suitable if you want to trigger the workflow automatically).
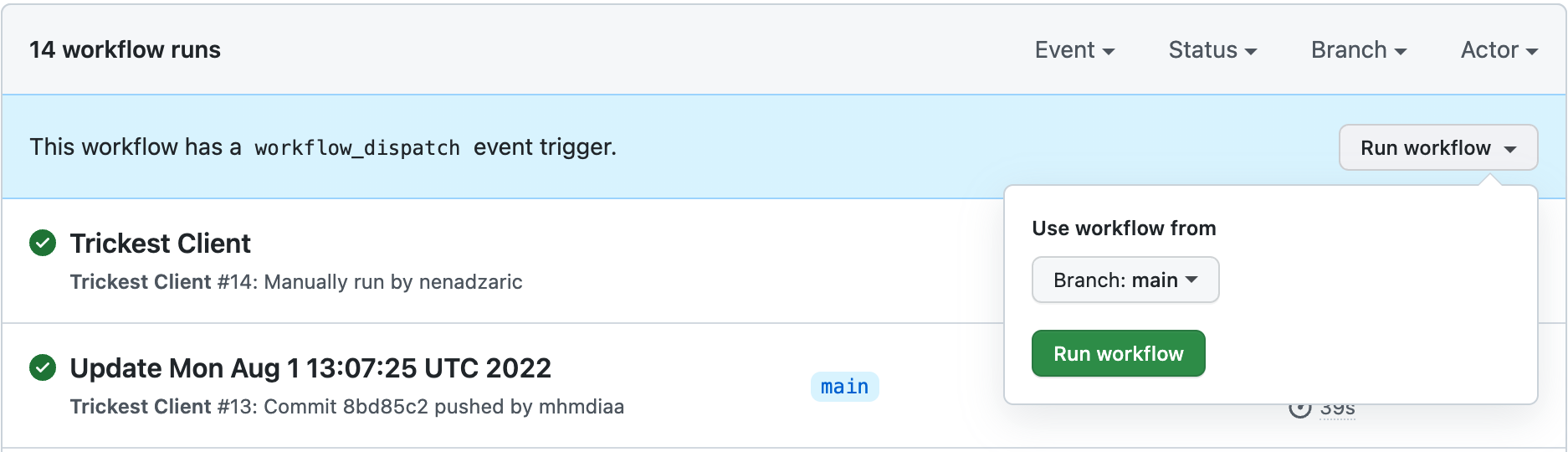
GitHub action for executing Github Recon & Scanner
Results
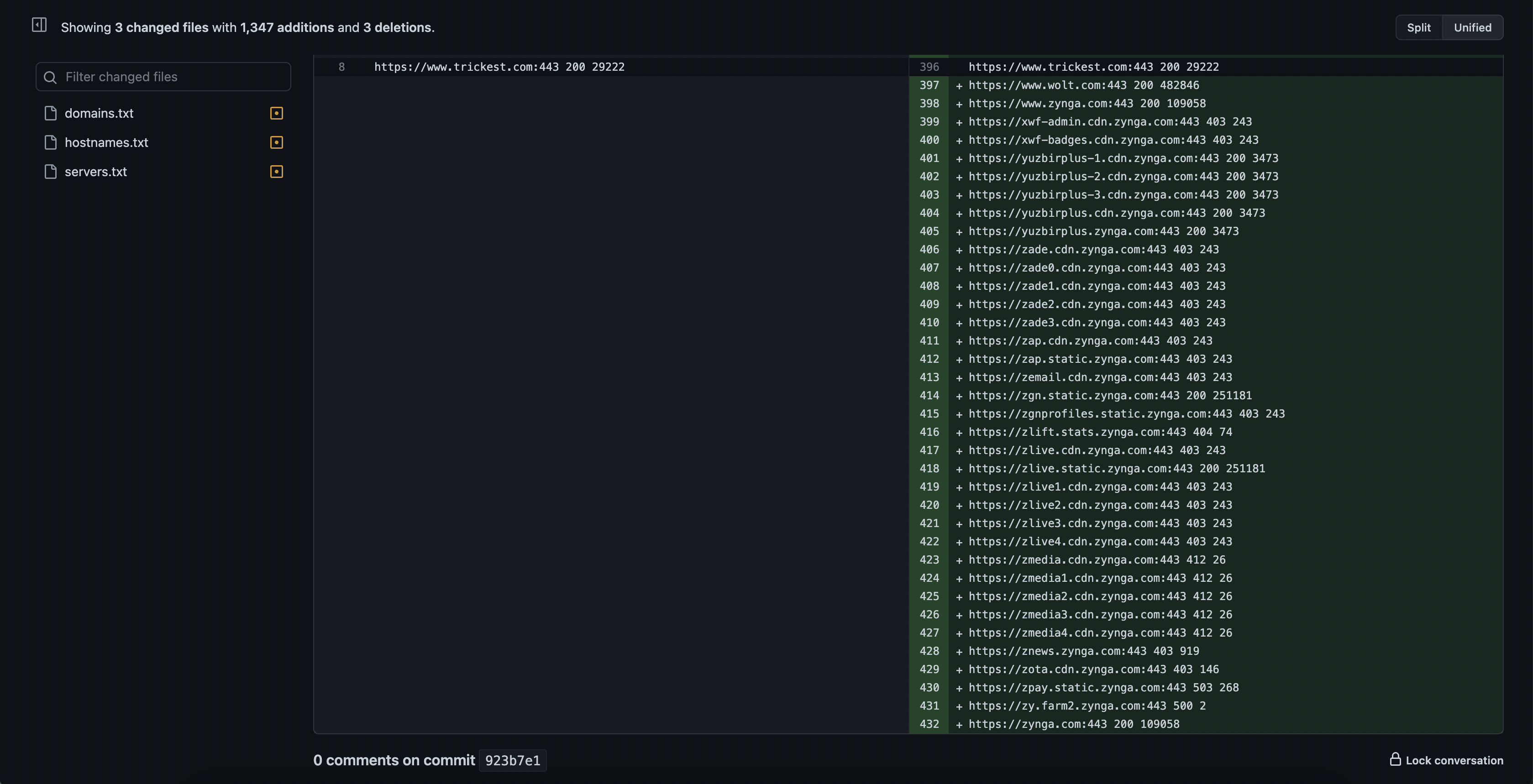
With this workflow, there is no need to download the outputs directly from the platform, all of the results will be pushed to the GitHub repository provided initially:
domains.txt- List of provided root domainshostnames.txt- List of hostnames found for root domains provided (Updated by the workflow, if updated manually, will be propagated through the entire workflow)servers.txt- List of available web servers for found hostnamesreports.txt- List of vulnerabilities found for found servers
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!