34 M Wordlist Subdomain Brute-Force
Complexity: basic
Category: Attack Surface Management
Workflow
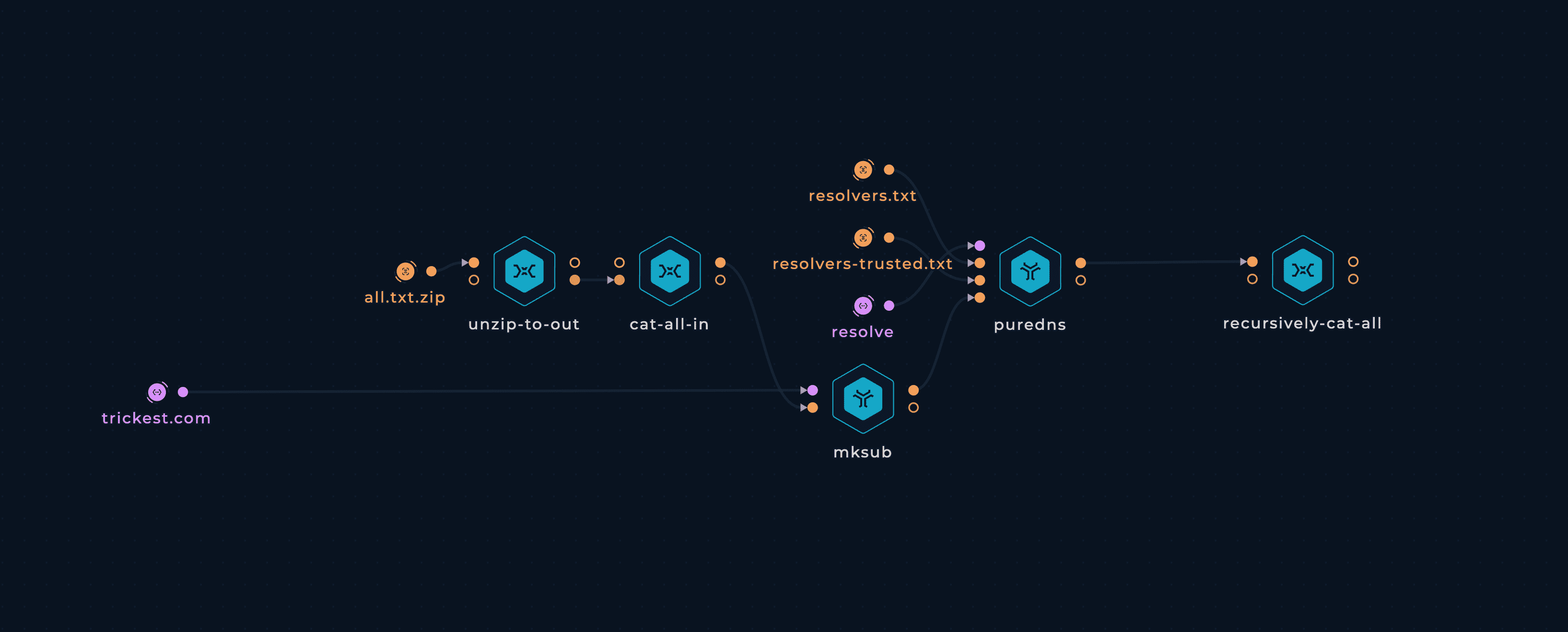
34 M Wordlist Subdomain Brute-Force
Tools
Setup
You can set up this workflow by changing following input value:
- ROOT DOMAIN - provide root domain, e.g. trickest.com, as a target

Workflow Targets Setup
Execution and results
After setup, workflow is ready to be executed. Once workflow's last node, recursively-cat-all script, is finished result can be viewed and downloaded.
recursively-cat-all script will contain all of the hostnames found.

Results
Build this workflow in steps
Unzipping wordlist with unzip-to-out
Firstly, we will download the zip wordlist from https://localdomain.pw/subdomain-bruteforce-list/all.txt.zip as it contains most comprehensive and all-around wordlist.
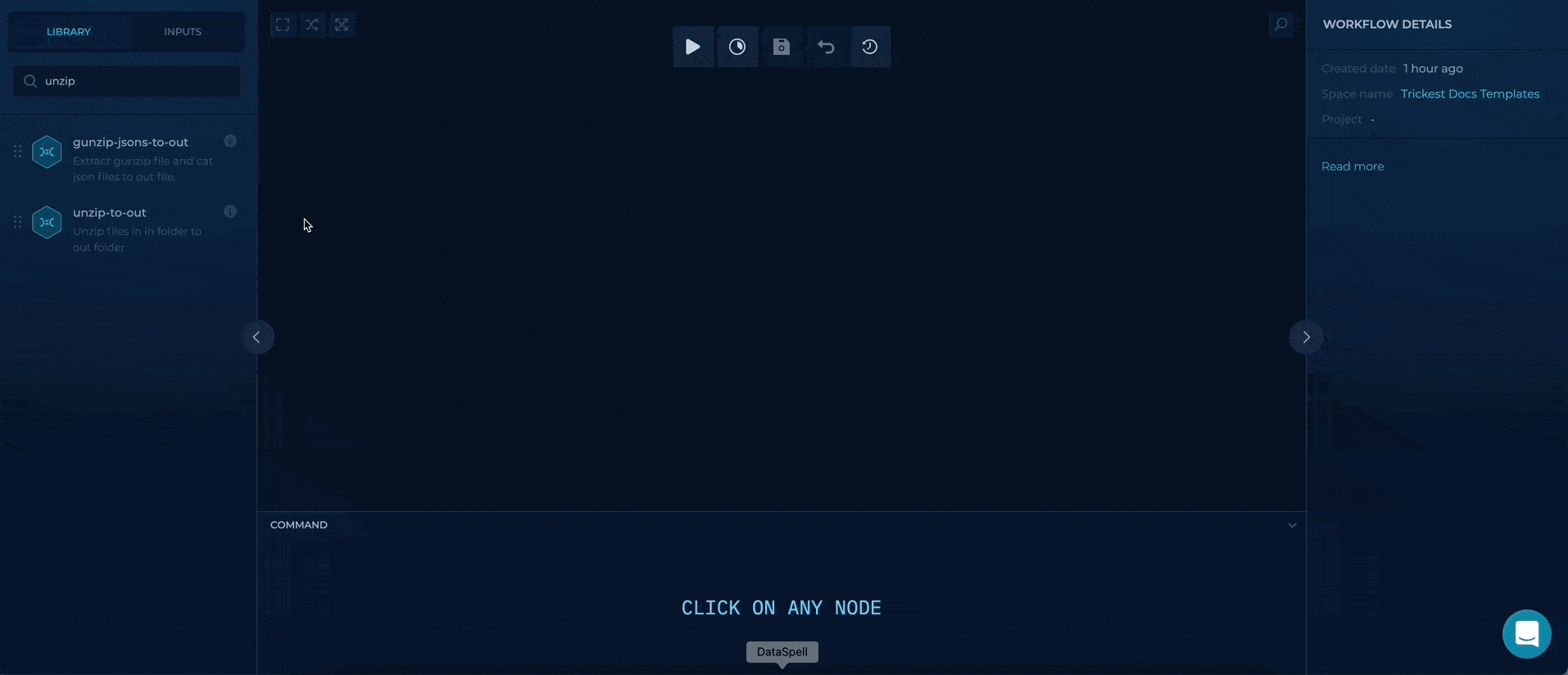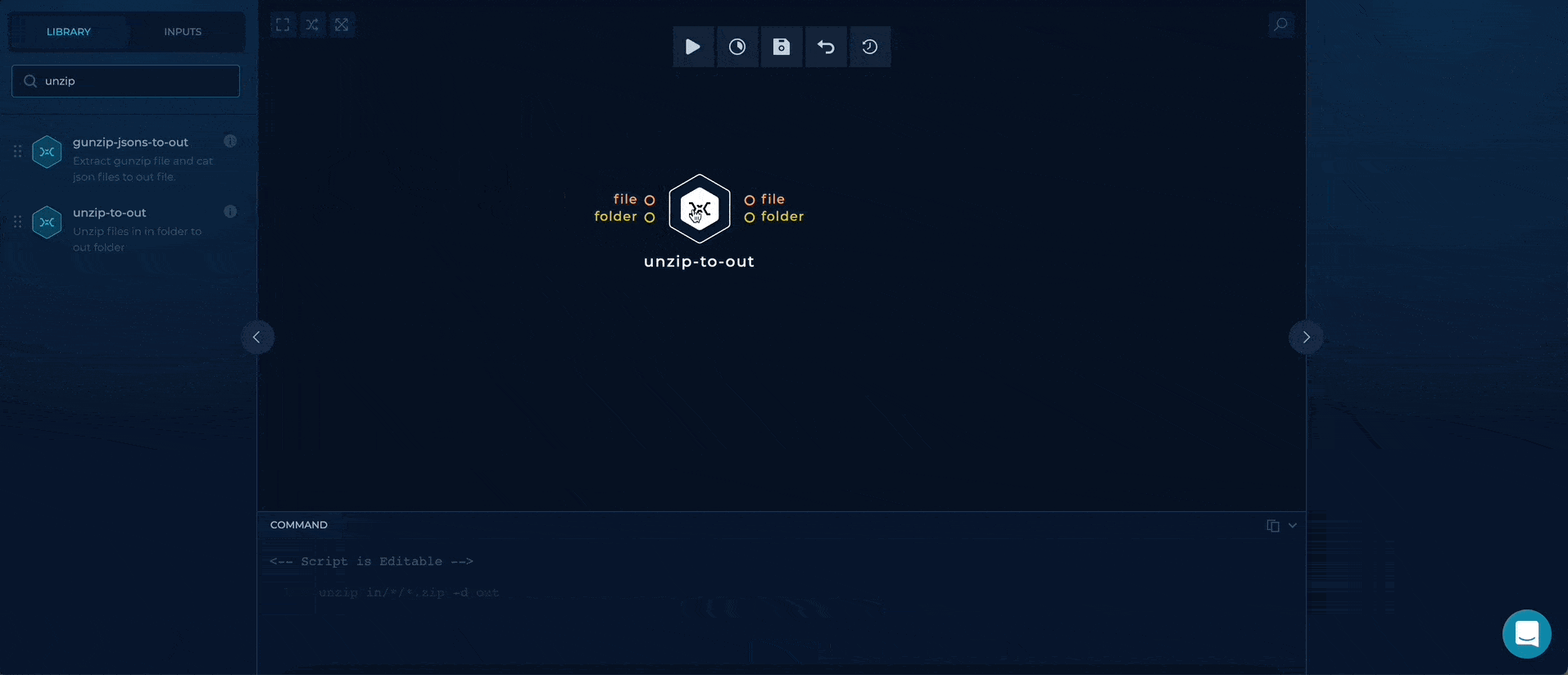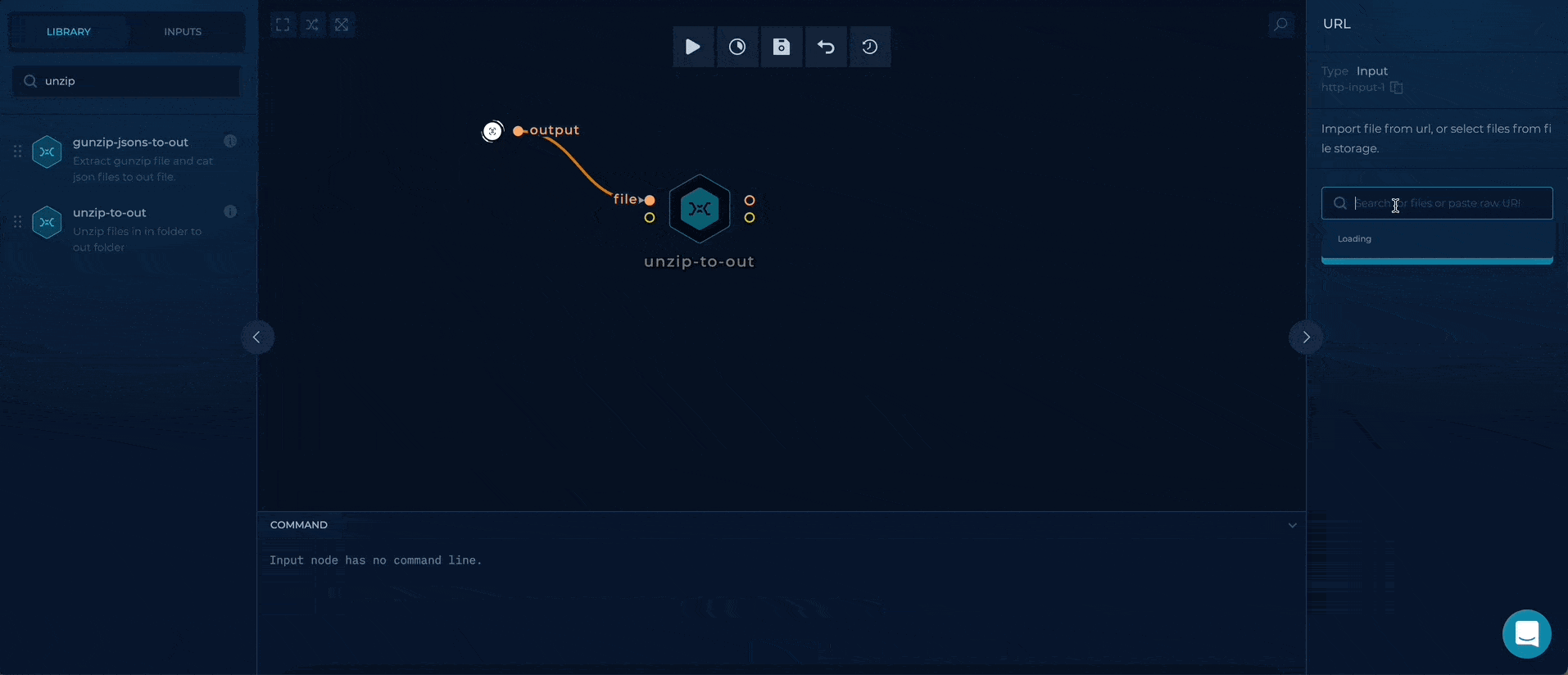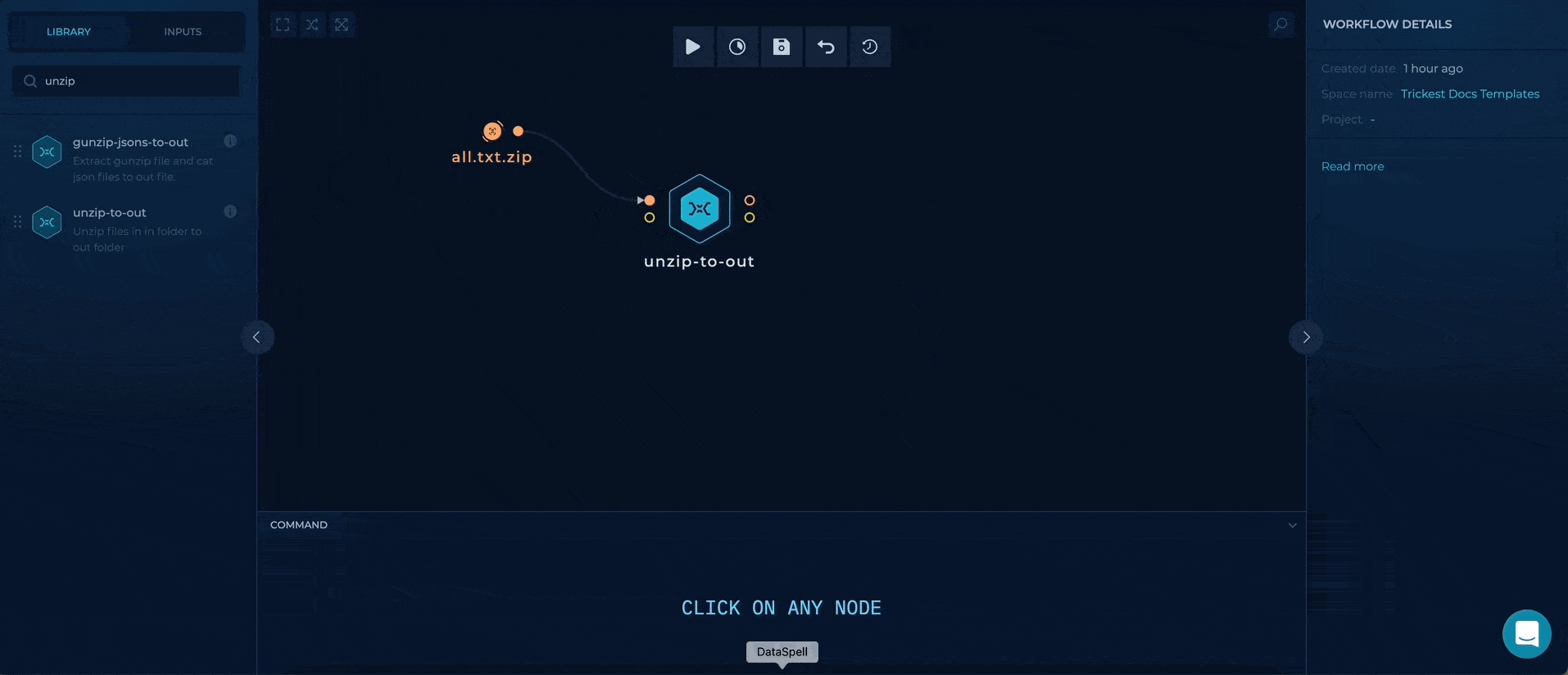
unziping external zip file using unzip-to-out
Getting wordlist with cat-all-in
As the output from unzip-to-out is folder with all of the files contained in zip used as an input, we will use cat-all-in to cat all of the files into one file. Output should be inside of out/output.txt which is being used by file output port.

cat-ing all of the files inside of zip
Create potential hostnames with mksub
Now that we have the wordlist, we can use mksub to merge the wordlist with our root domain.
Firstly, we will set the string to the mksub domain parameter. And connect the previously added cat-all-in output to mksub wordlist parameter.

creation of potential hostnames with mksub and root domains
With mksub we have all of our potential hostnames consisting of the root domain and potential wordlist, which we unzipped previously. Time to resolve!
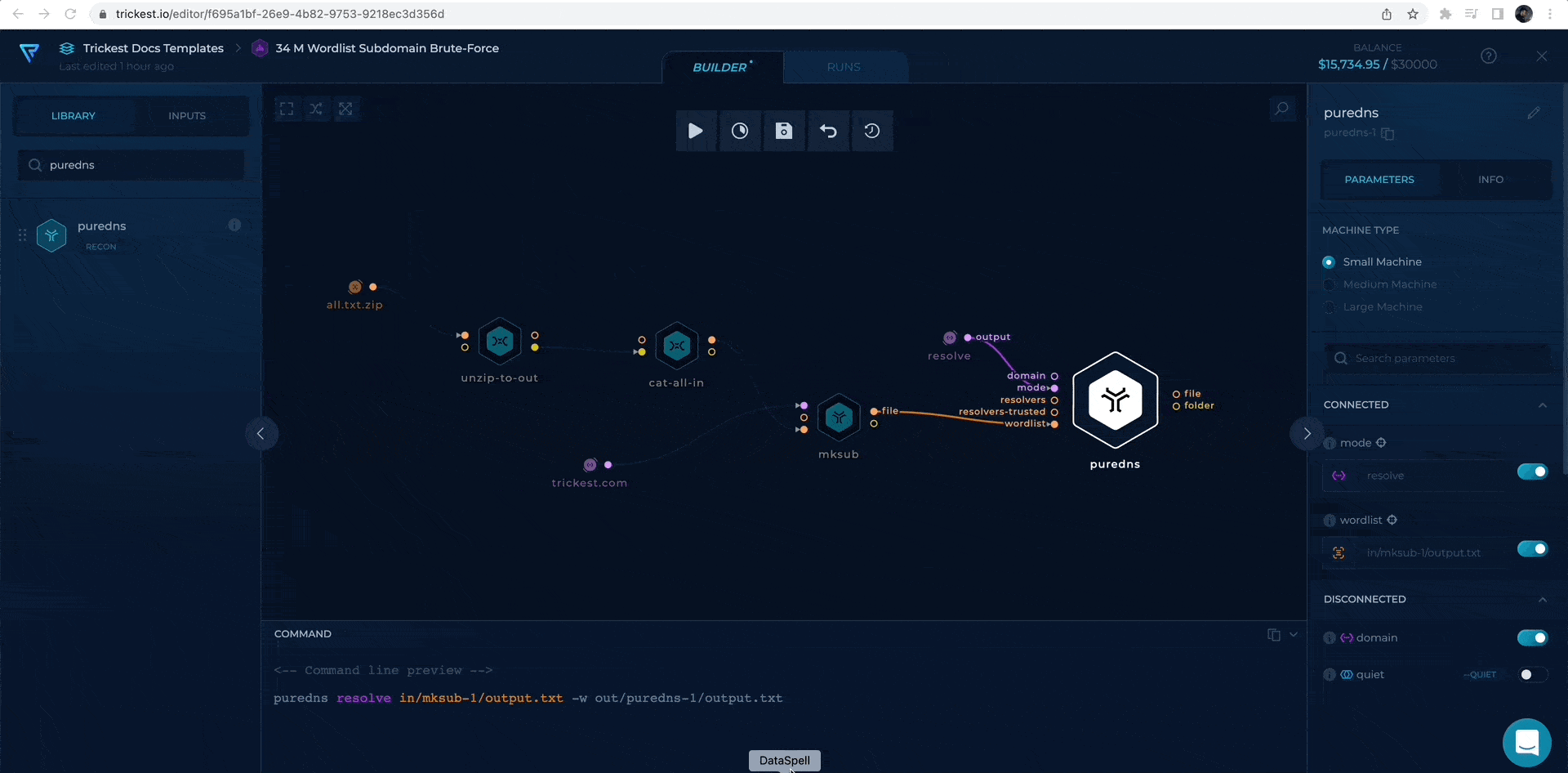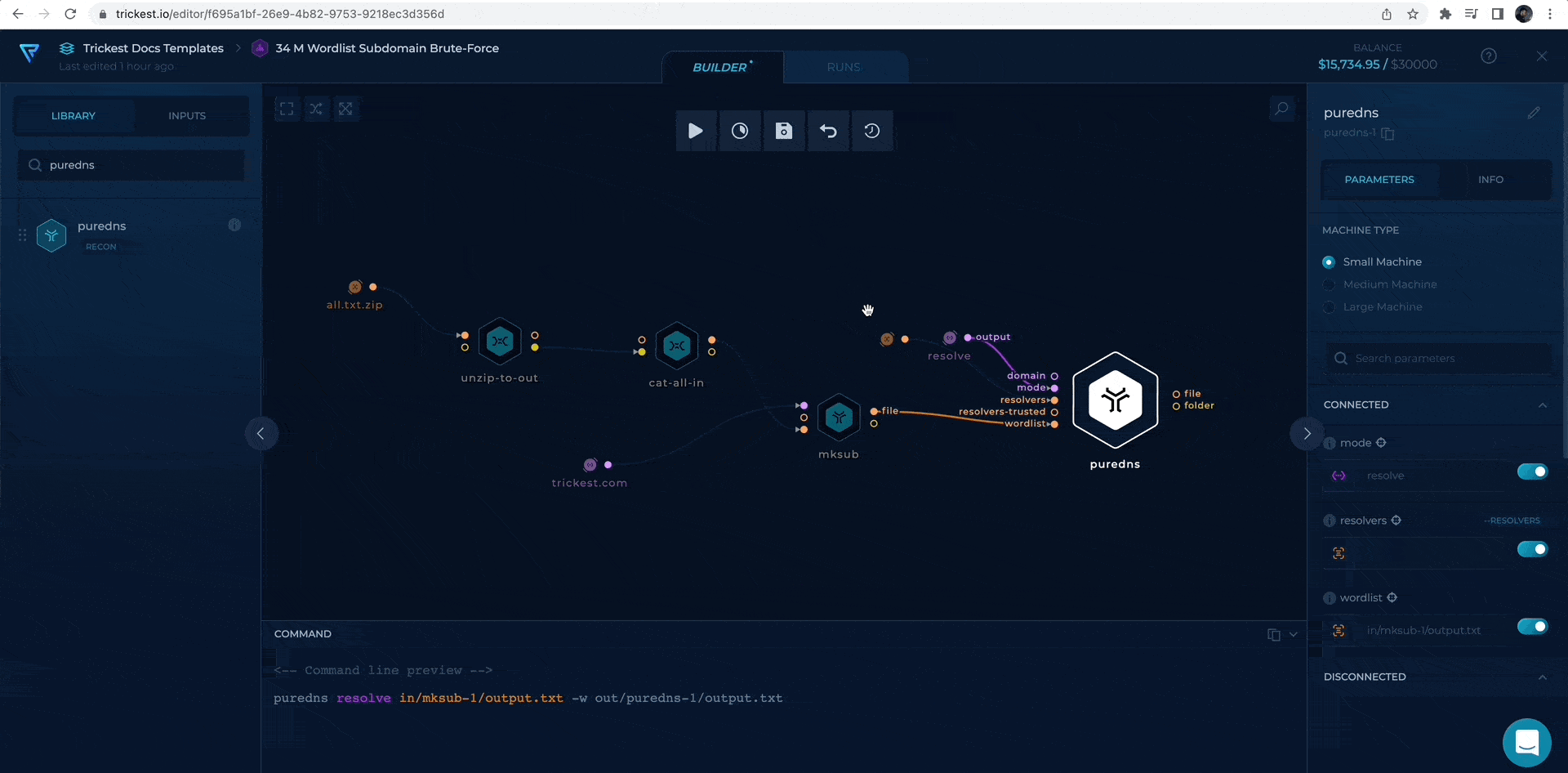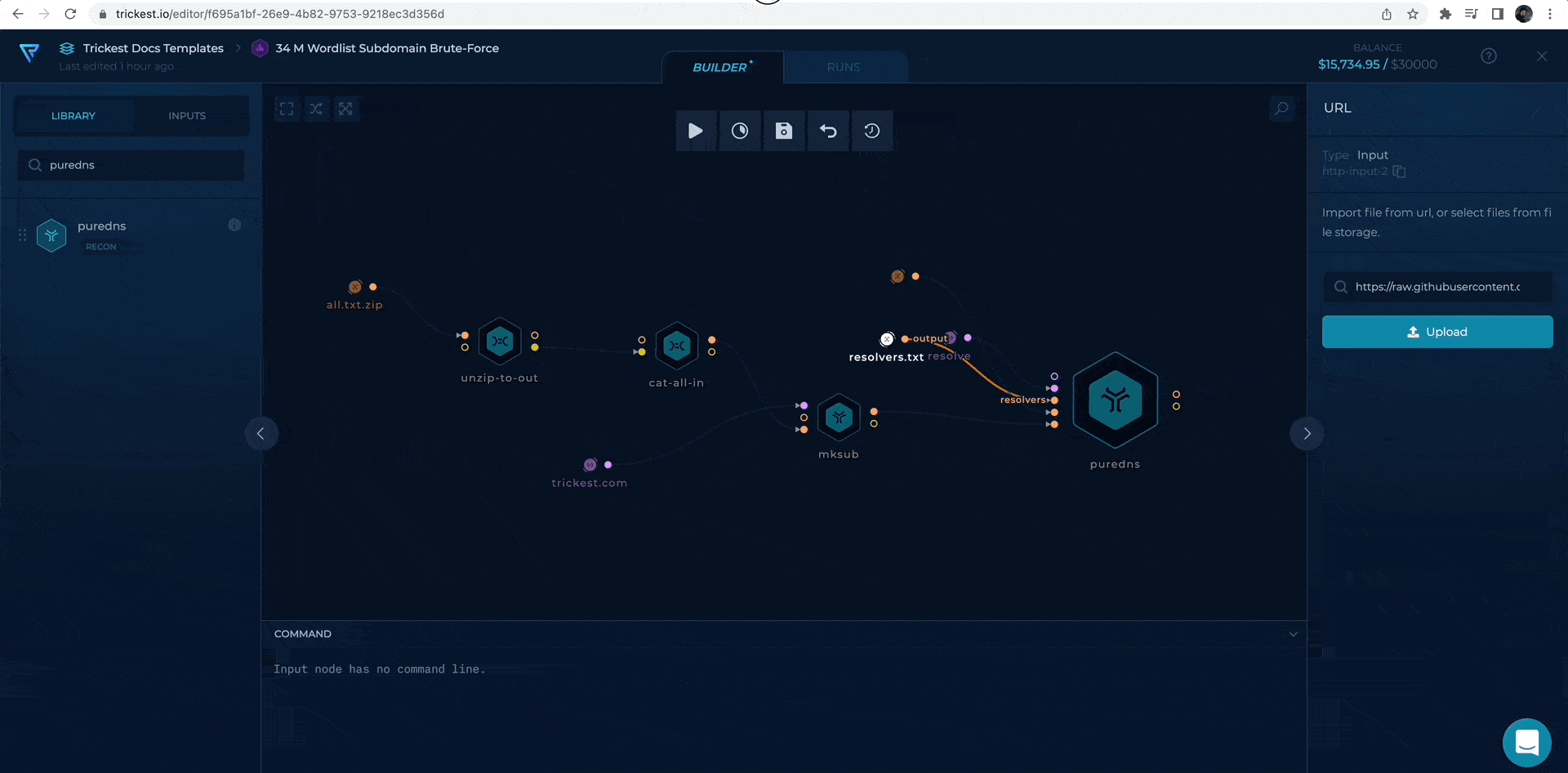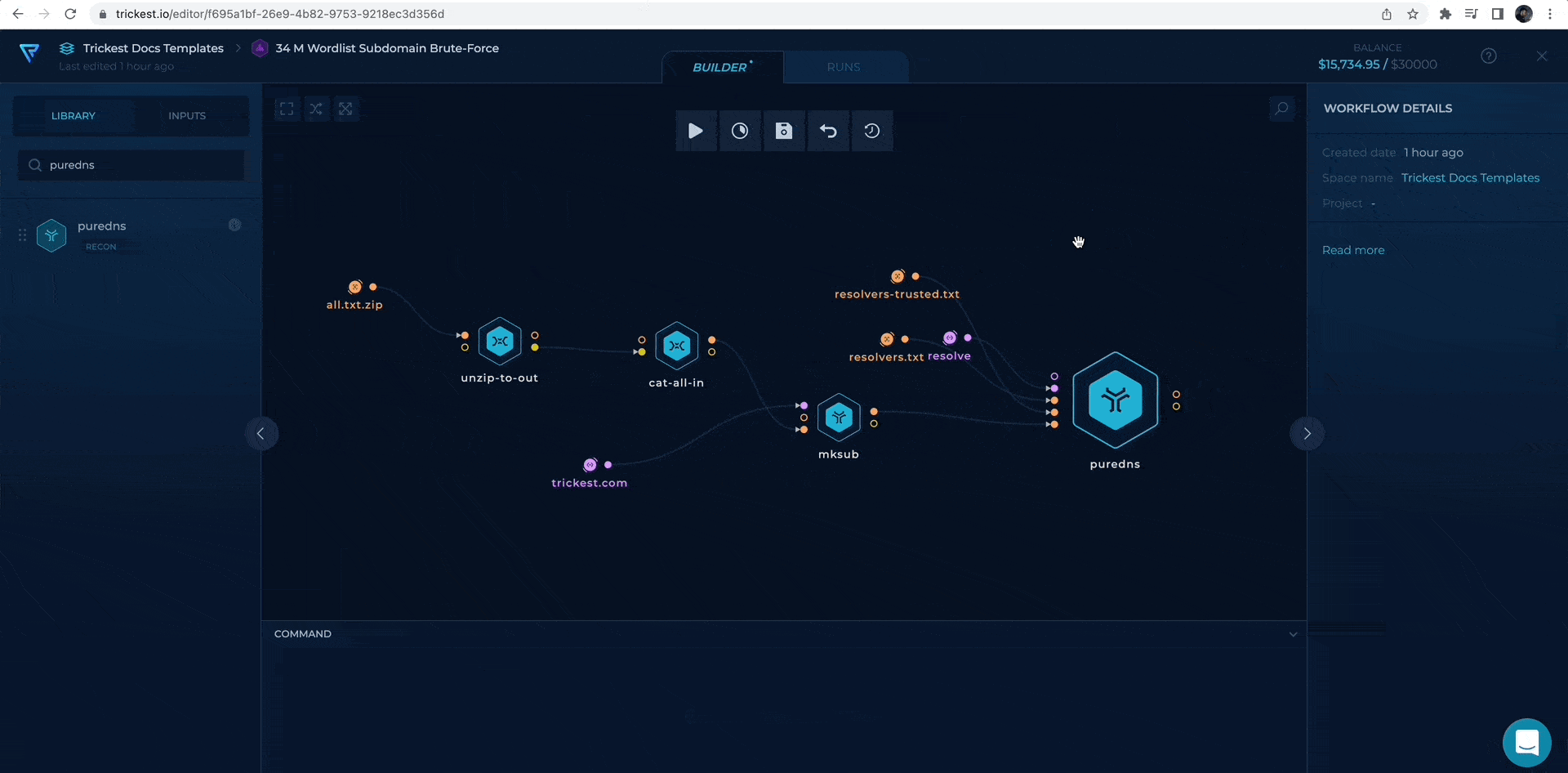
Resolve with puredns
It is time to resolve our potential hostnames. Puredns has two types of modes, and in this case, as we have already created hostnames, we will use the resolve mode. Additionally, puredns uses two resolver file inputs to resolve all of the hostnames used as input. One of our project's trickest/resolvers is focused on that, so we can use the URL inputs for puredns which will be downloaded and used in execution time.
Firstly, we will connect the wordlist from mksub and enable the resolve mode

enabiling resolve mode and wordlist to be resolved
Second, we will add resolvers and resolvers-trusted URLs from repository.
adding resolver file URLs to puredns
Additionally, as we are in resolve mode, the domain parameter is unnecessary, so we can disable it through the right sidebar.
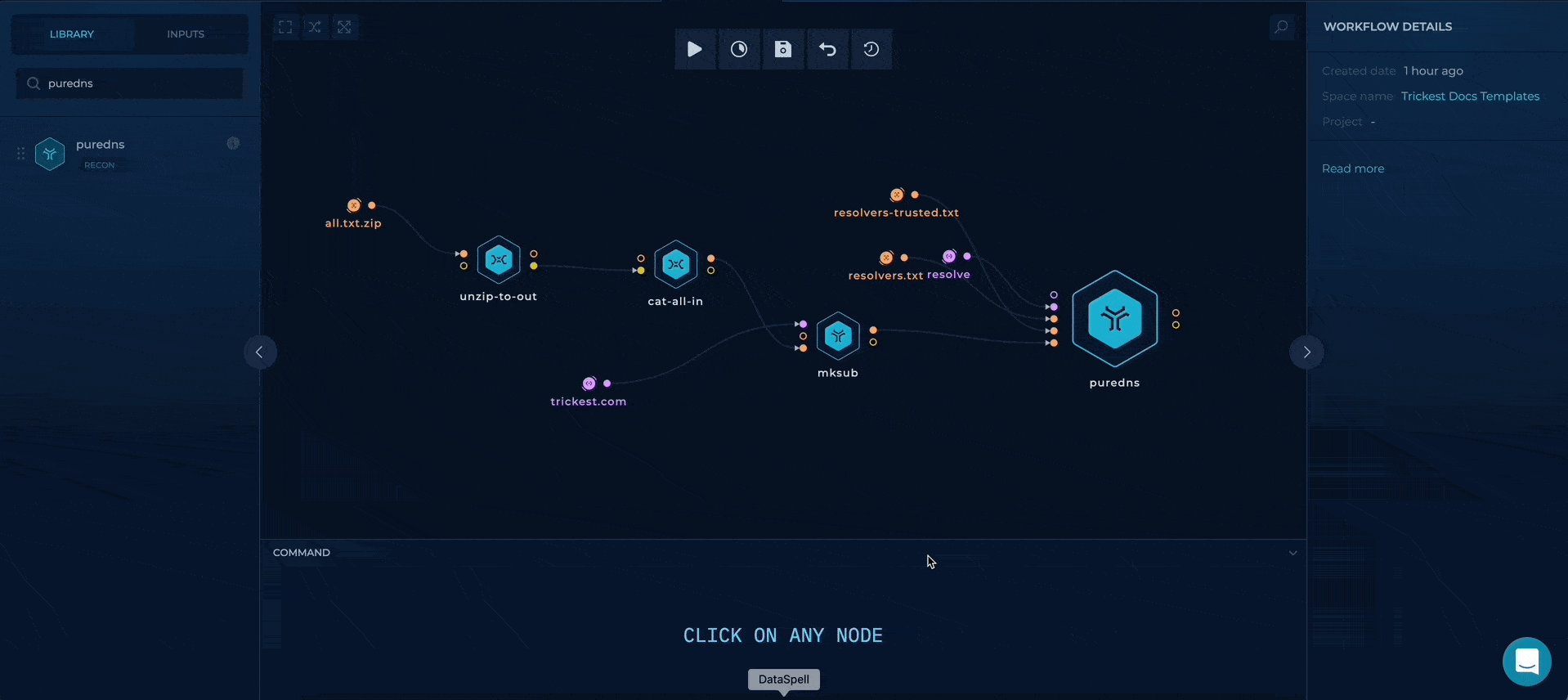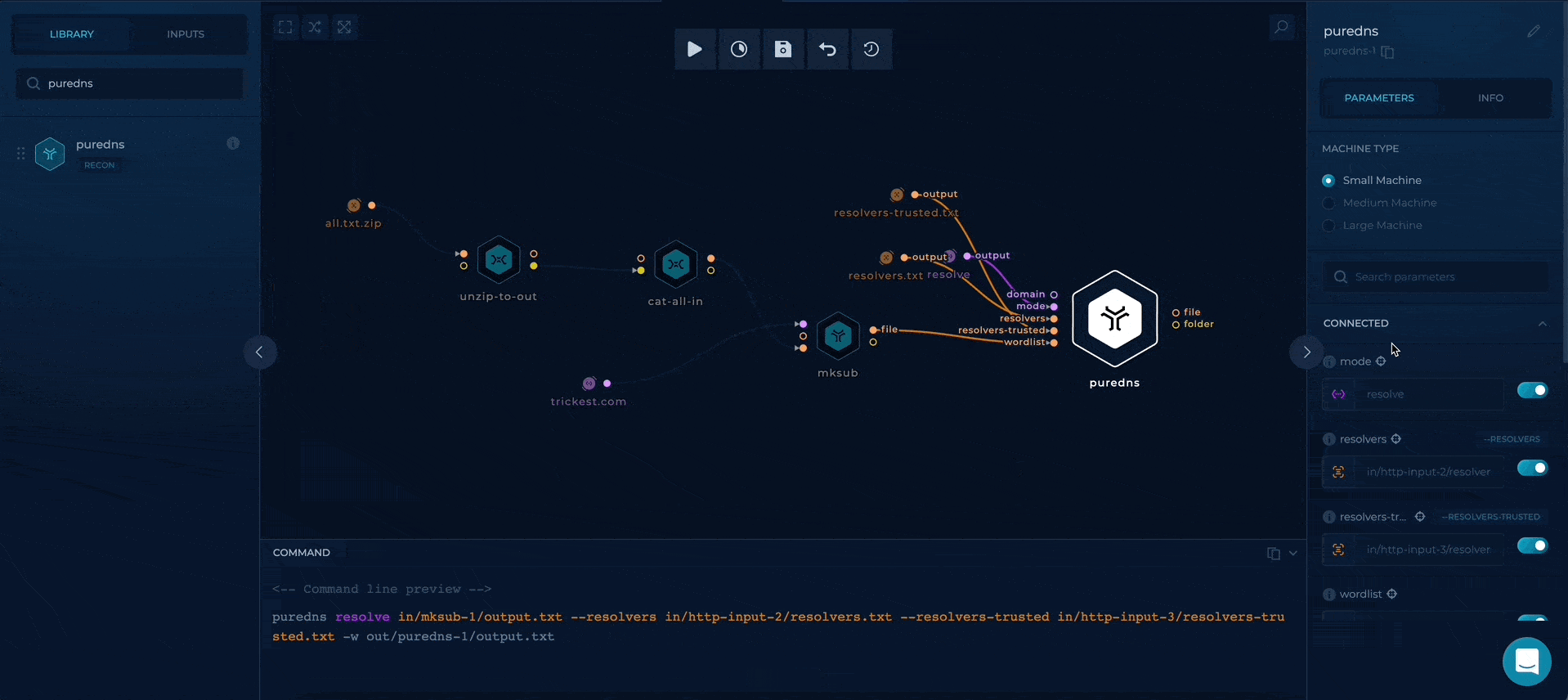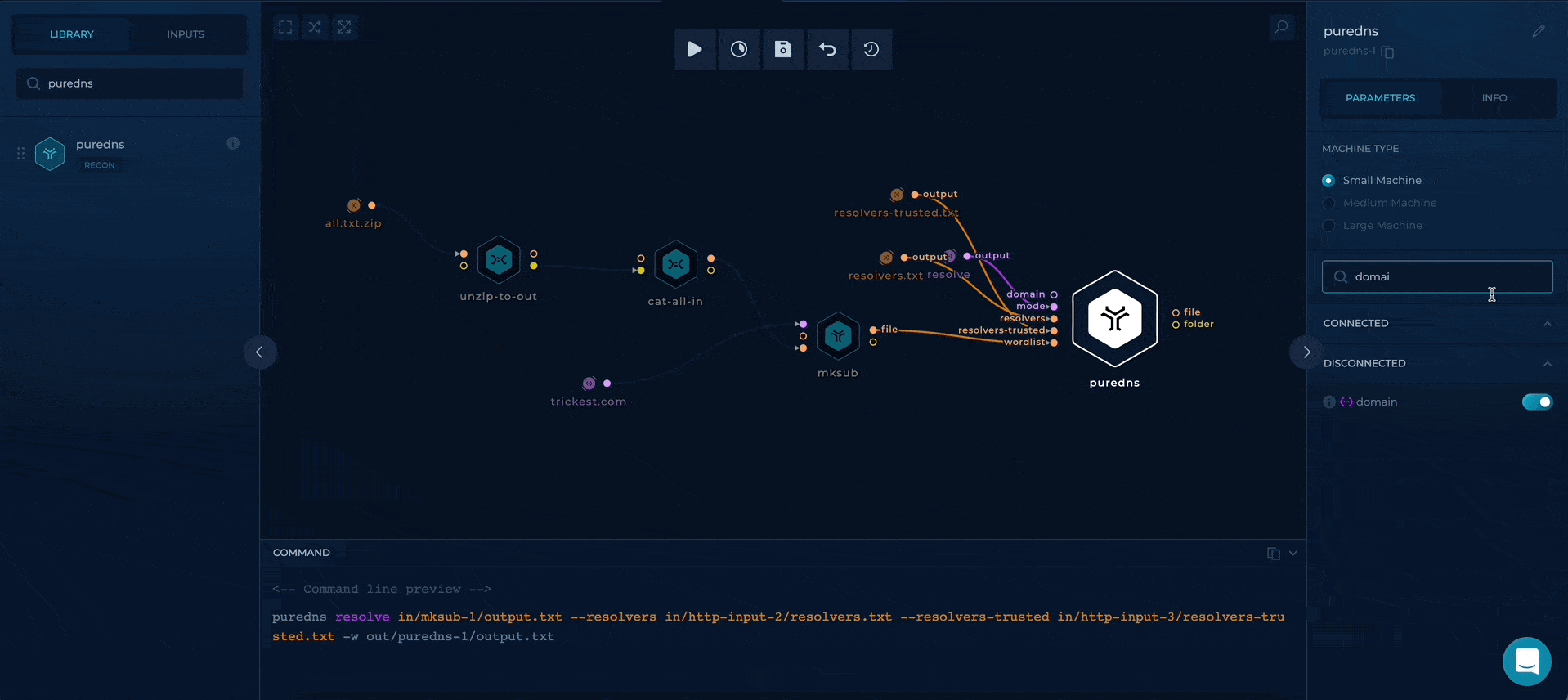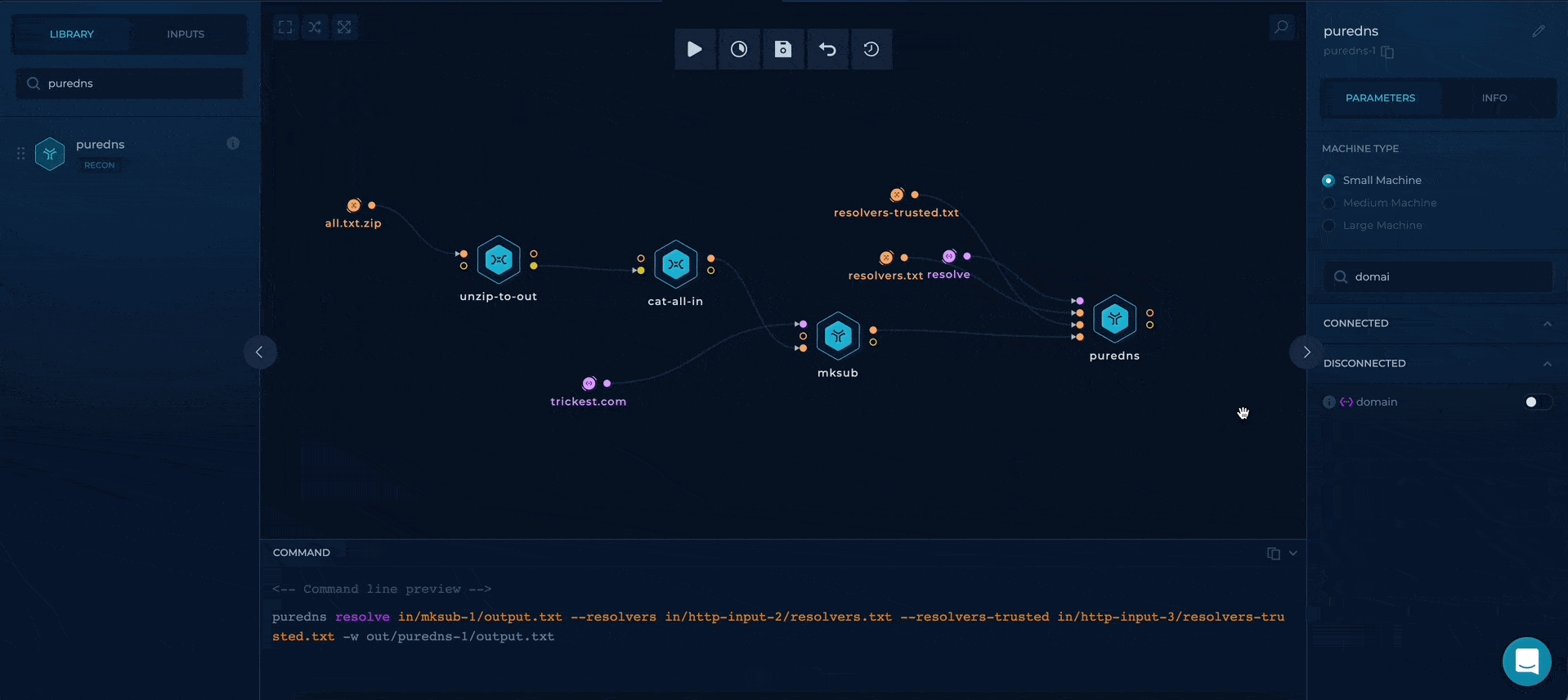
disabling domain parameter on puredns
Get results with recursively-cat-all
Finally, we will use the recursively-cat-all script, which will cat all of the files into one recursively.

cat-ing output recursively from puredns
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Changing machine type of tools to speed up the execution
- Adding more wordlist files and connecting them to the cat-all-in script node
- Enabling
threadsthe parameter in puredns for faster execution