masscan
Masscan supports widespread scanning of many machines. It's fast with possibility to scan the entire Internet in under 5 minutes, transmitting 10 million packets per second, from a single machine. Internally it uses asynchronous transmission, and it's flexible allowing arbitrary port and address ranges.
Basic Usage Examples
Trickest takes care of masscan's installation. All you have to do is to provide desired parameters - port or port range, address range(s), and optionally other feature parameters.
Port Scanning Of One Address Range
To scan a network segment for some port(s):
- Pass a port or port range to the
portsinput (typestring), - Pass an address range to the
ip-rangeinput (typestring).

Port Scanning Of Multiple Address Ranges
To scan multiple network segments for some port(s):
- Pass a port or port range to the
portsinput (typestring), - Pass as a list of address ranges, contained within a file, to the
targetsinput (typefile):
103.36.0.0./24
104.36.0.0./24
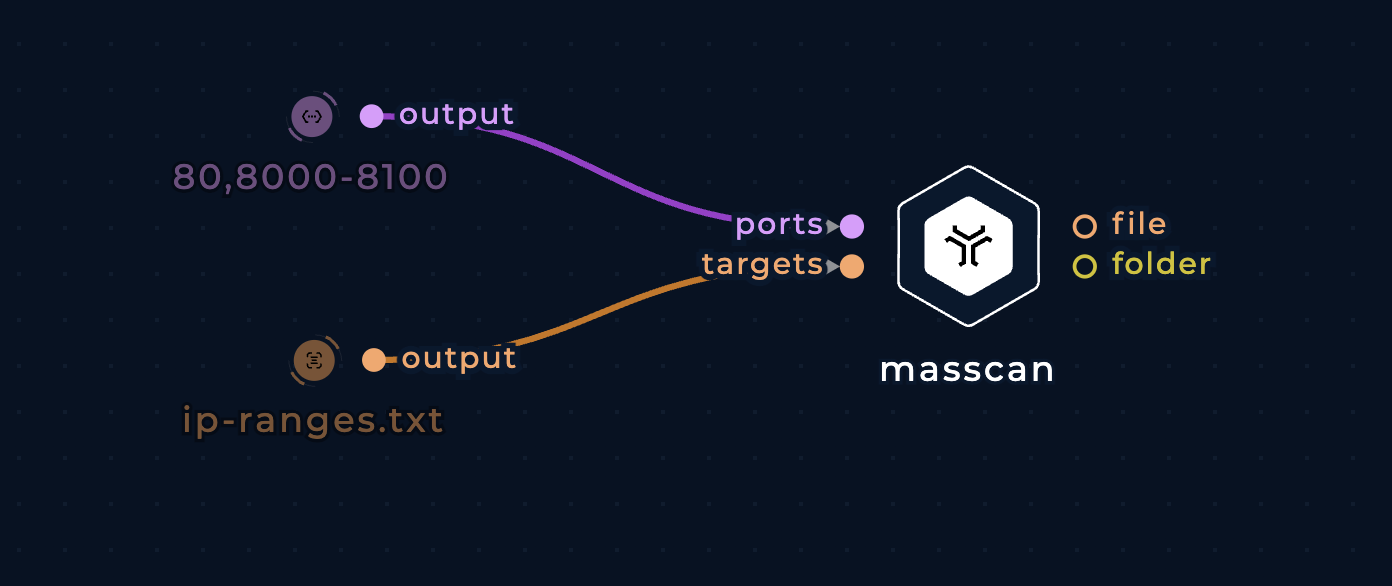
Scan port 80 and the range 8000 to 8100 on given subnets with masscan
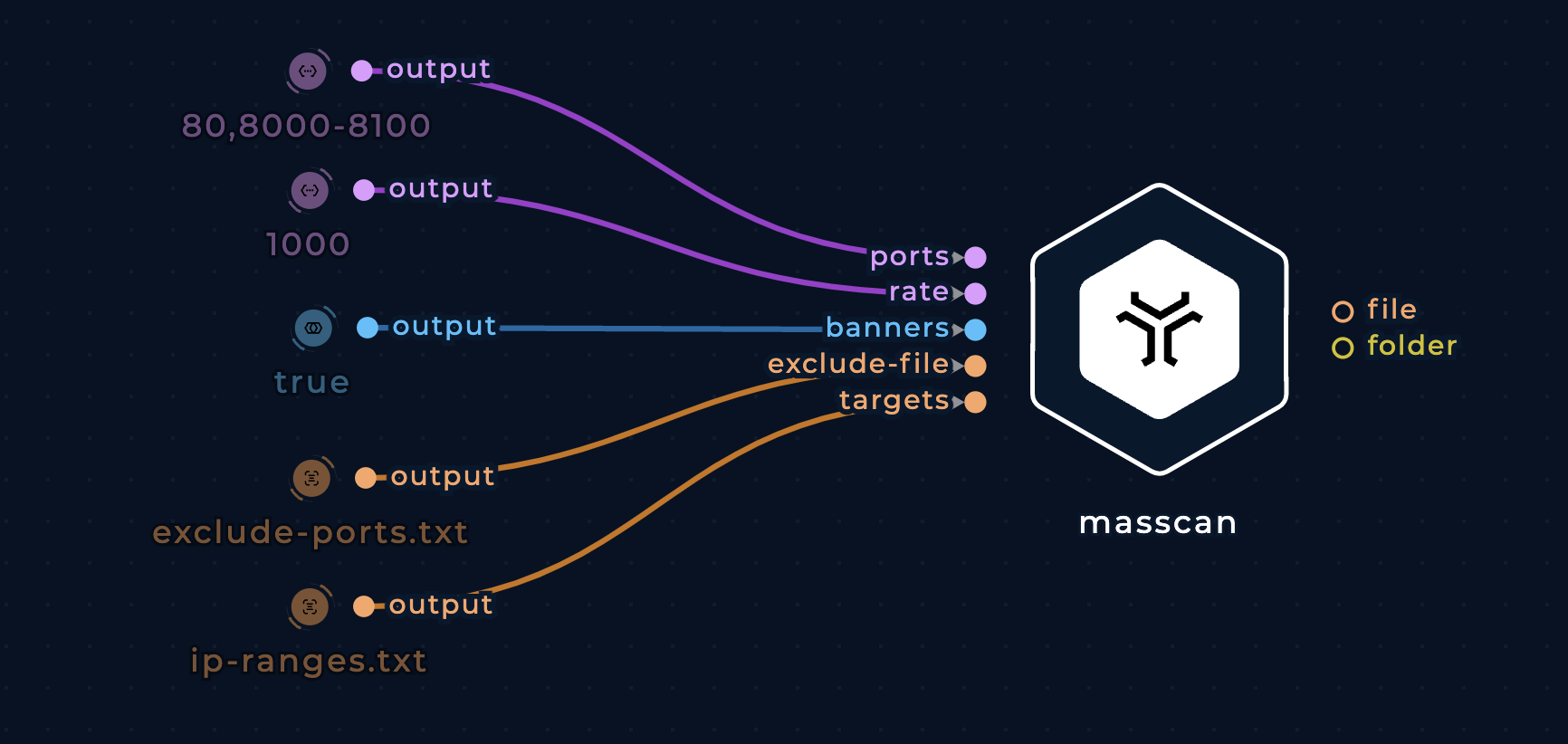
Improvements
Grab banner information
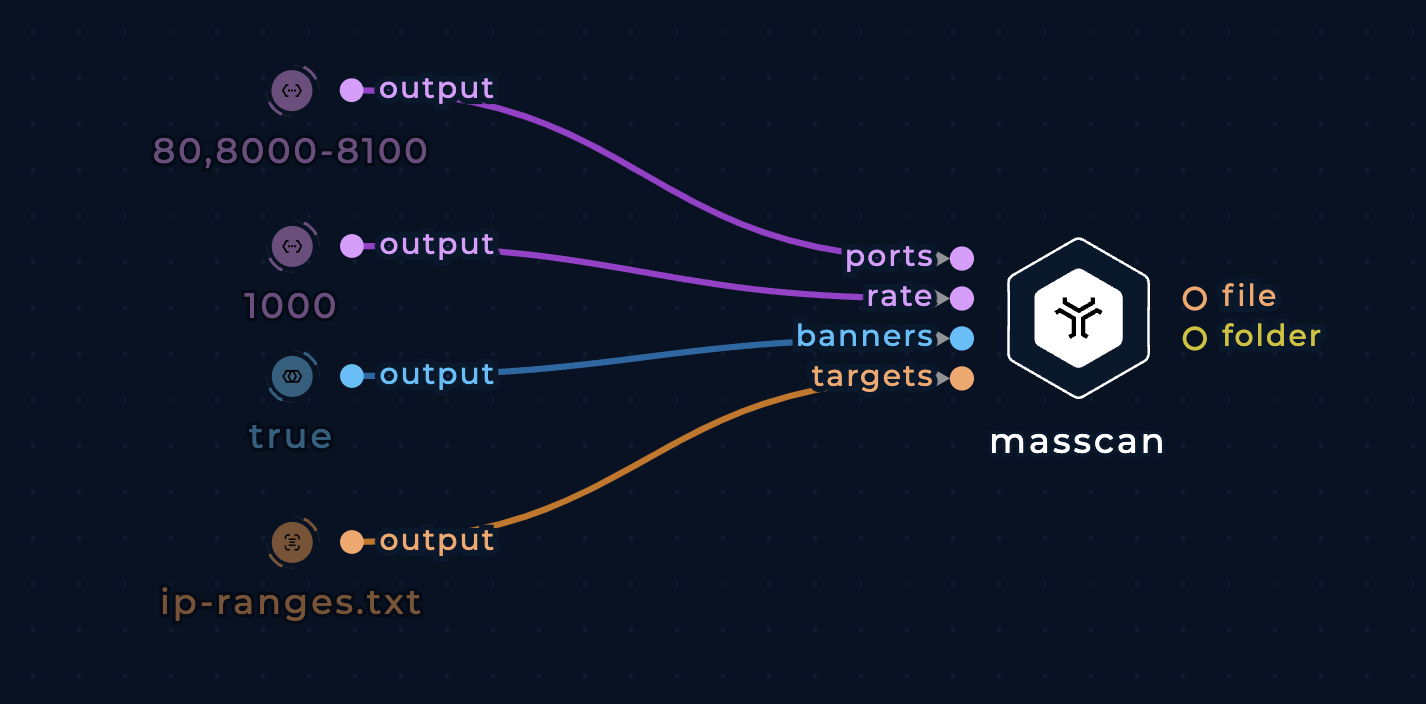
Masscan can do more than just detect whether ports are open. It can also complete the TCP connection and interaction with the application at that port in order to grab simple "banner" information.
To support banner checking, use banners boolean input.

Speed up scanning
Default scanning rate is 100 packets/second. To speed it up to 1000 packets/second, pass desired value to the rate input (type string).
Exclude a range of ports
Sometimes there is a need to blacklist or exclude some of port ranges from scanning.
Just think about scanning the entire Internet - parts of the Internet react badly to being scanned, some sites track scans and add you to a ban list etc. Excluding ranges will solve potential issues.
To blacklist or exclude specific port ranges, pass a list of desired port ranges, contained within a file, to the exclude-file input (type file).