ASN Based Network Scan
This workflow will provide you with the IP addresses and open ports for a given ASN.
Complexity: intermediate
Category: Attack Surface Management
Tools
Setup
You can set up this workflow by changing following input value:
- ASN_LIST - provide a file containing company ASNs list, as a target
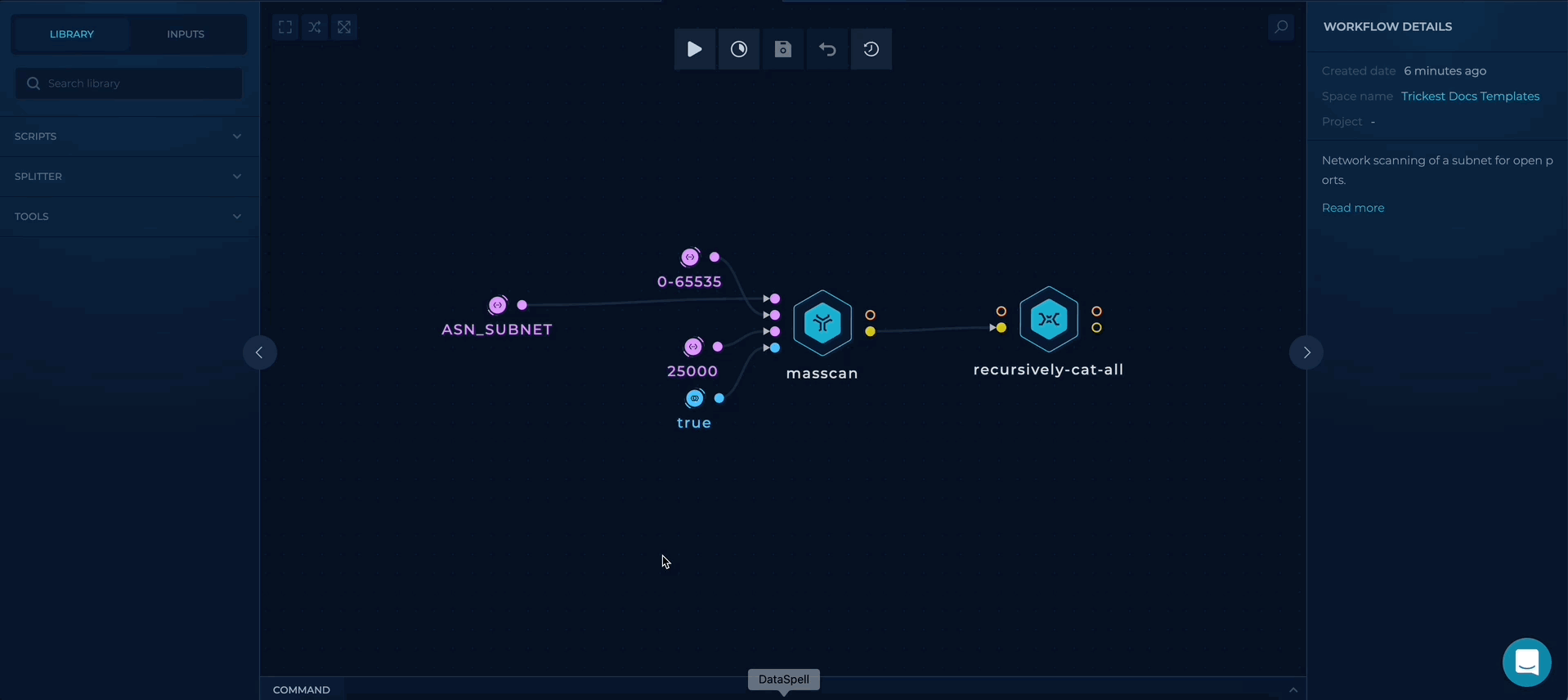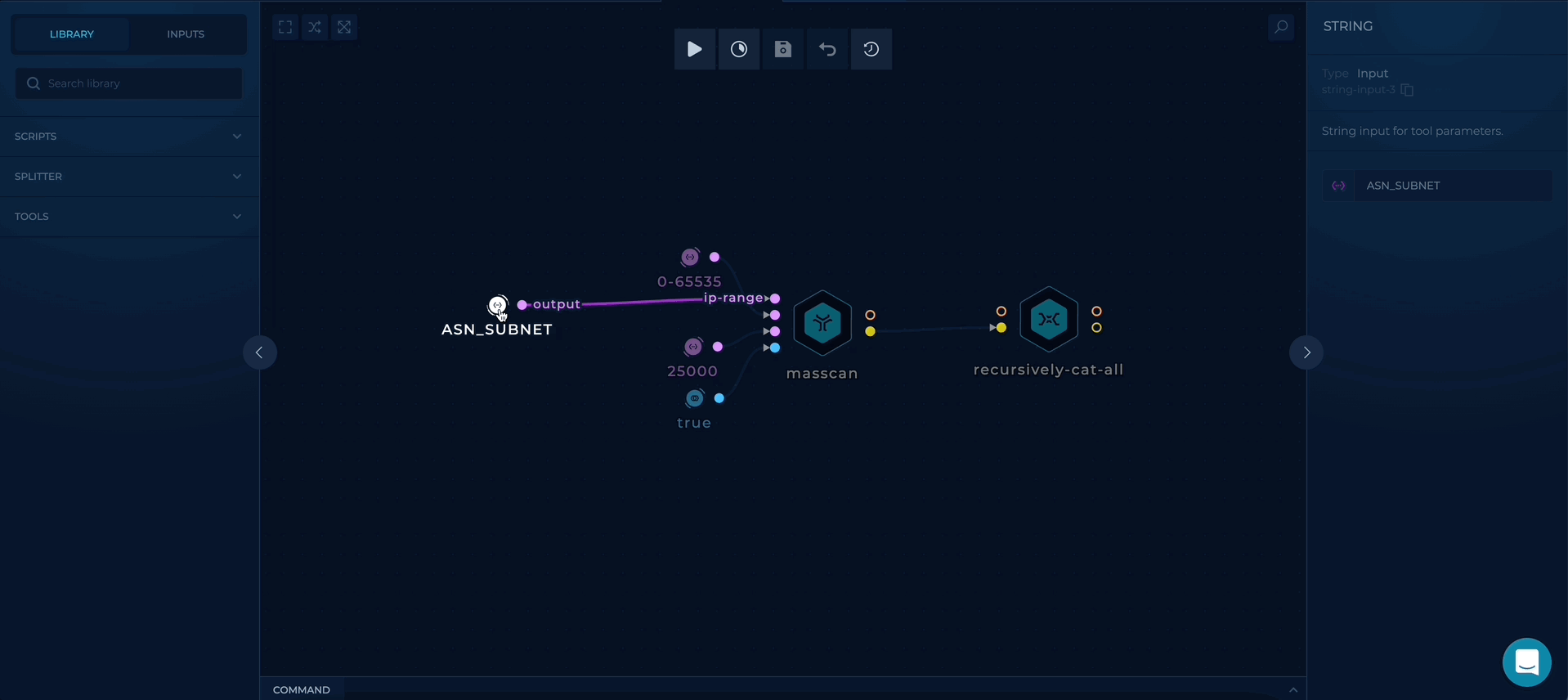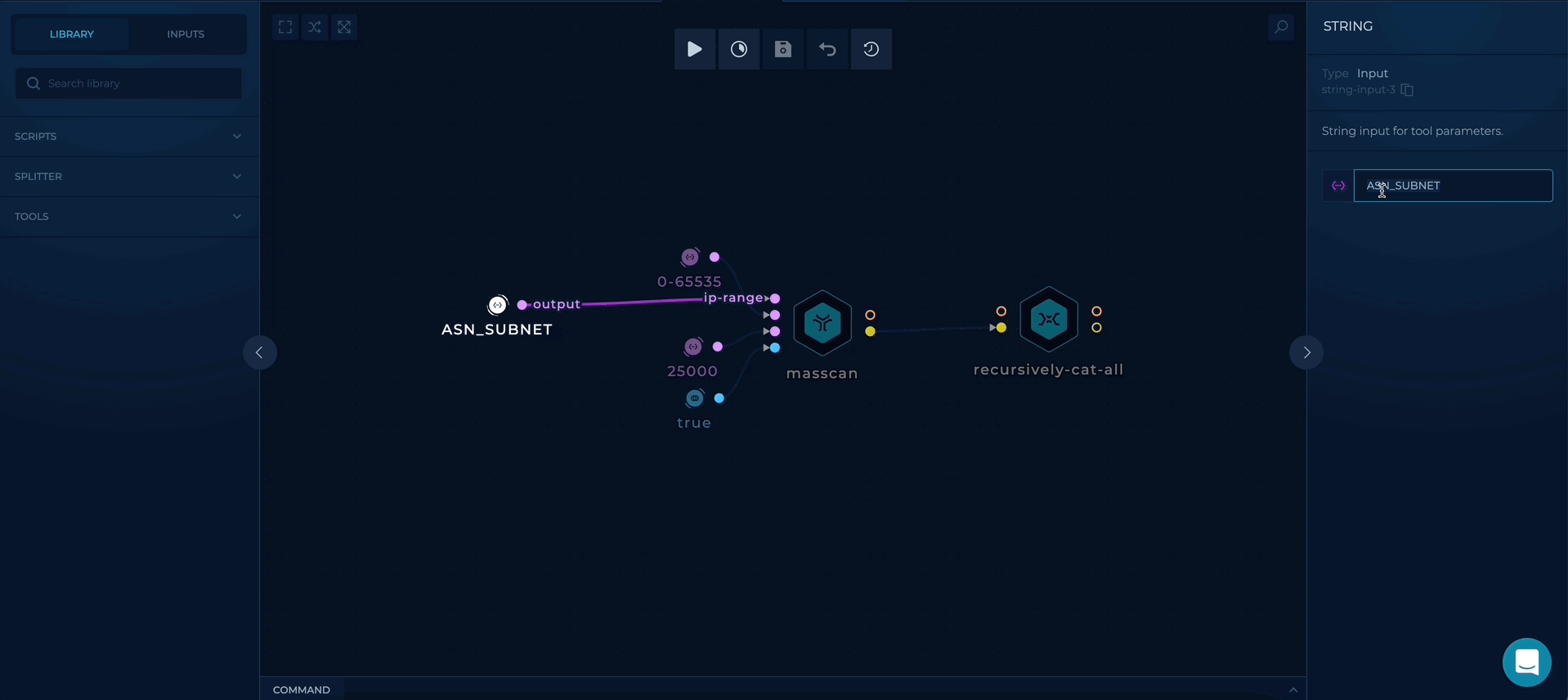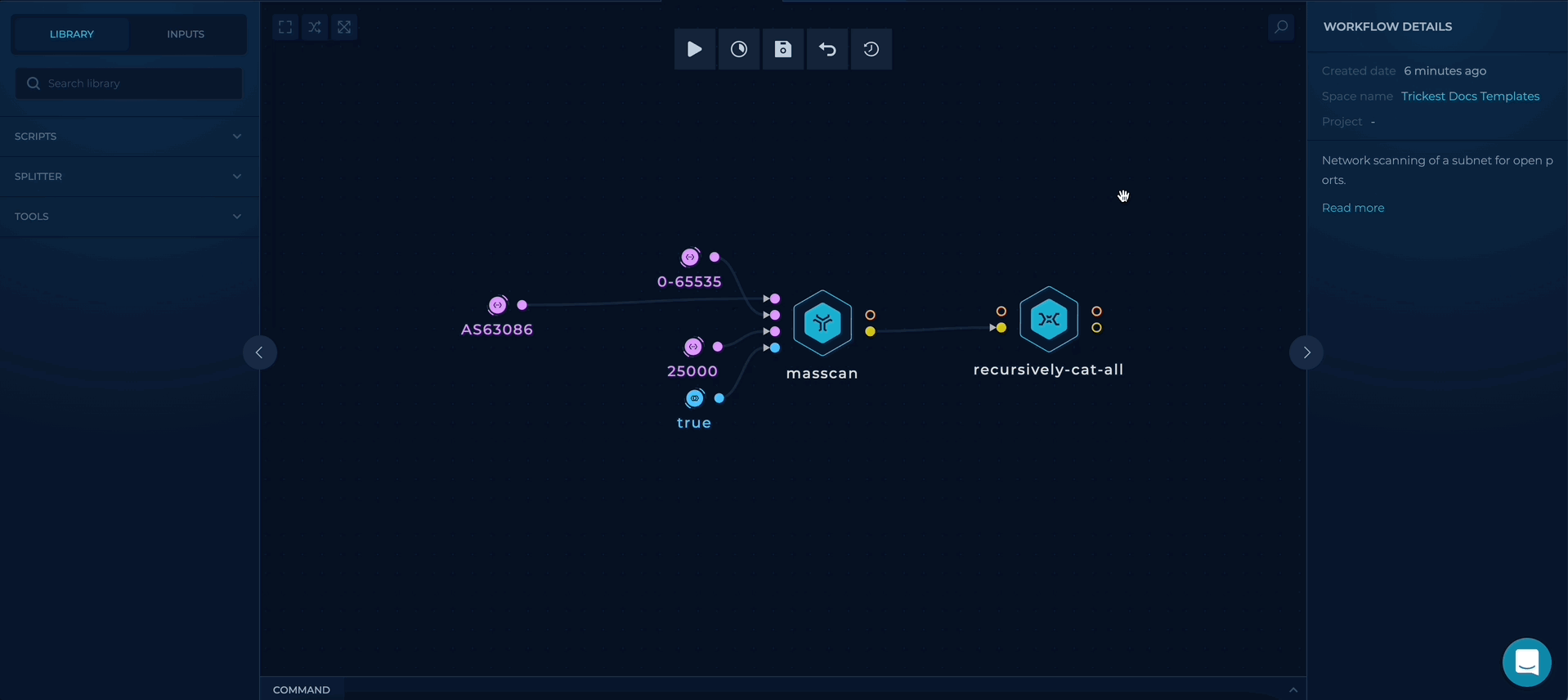
Workflow Targets Setup
Execution and results
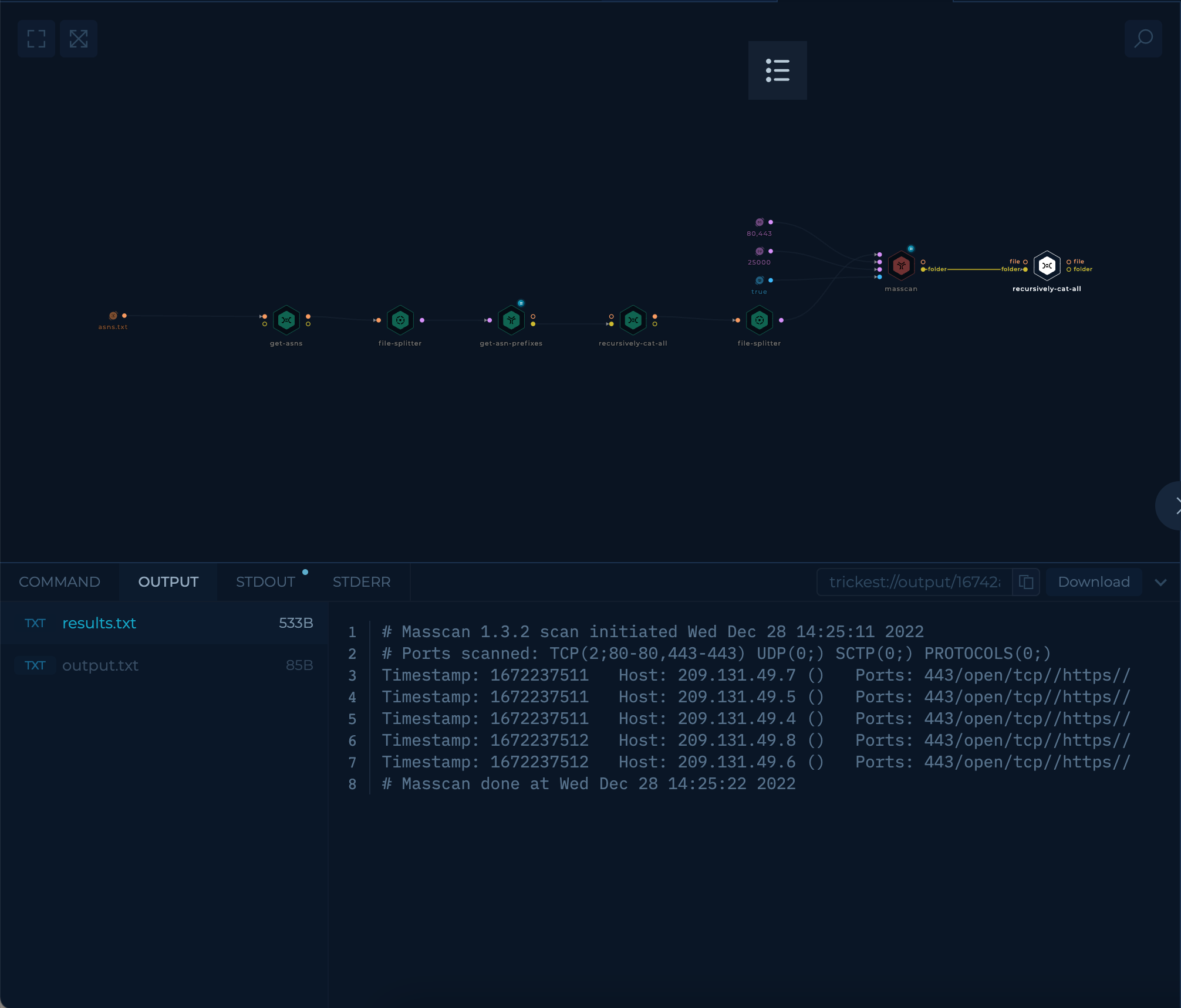
After setup workflow is ready to be executed. Once workflow's last node, recursively-cat-all script, is finished result can be viewed and downloaded.
recursively-cat-all script will contain raw masscan data, and output with ip:port structure.
Build this workflow in steps
Get ASNs file with recursively-cat-all and connecting file-splitter
We can use the recursively-cat-all script to get all of the ASNs provided in a file. As we want to get all of the prefixes per ASN we will also connect file-splitter to it.

splitting the list of ASNS to strings via file-splitter
Execute get-asn-prefixes in parallel and cat all results
File-splitter will convert all of the lines in input file to strings, that way, we can execute get-asn-prefixes in parallel for each ASN and that way get all of the prefixes (subnets) for specific ASN.
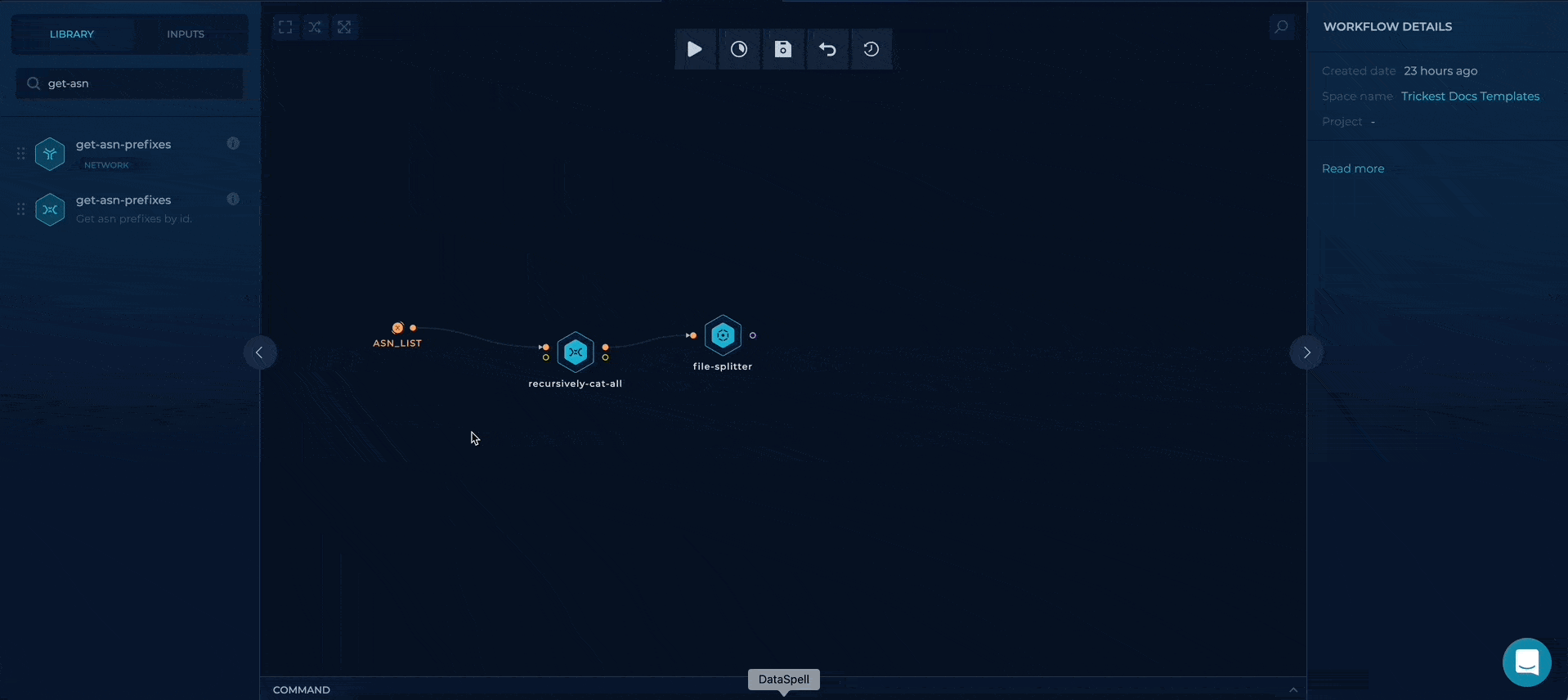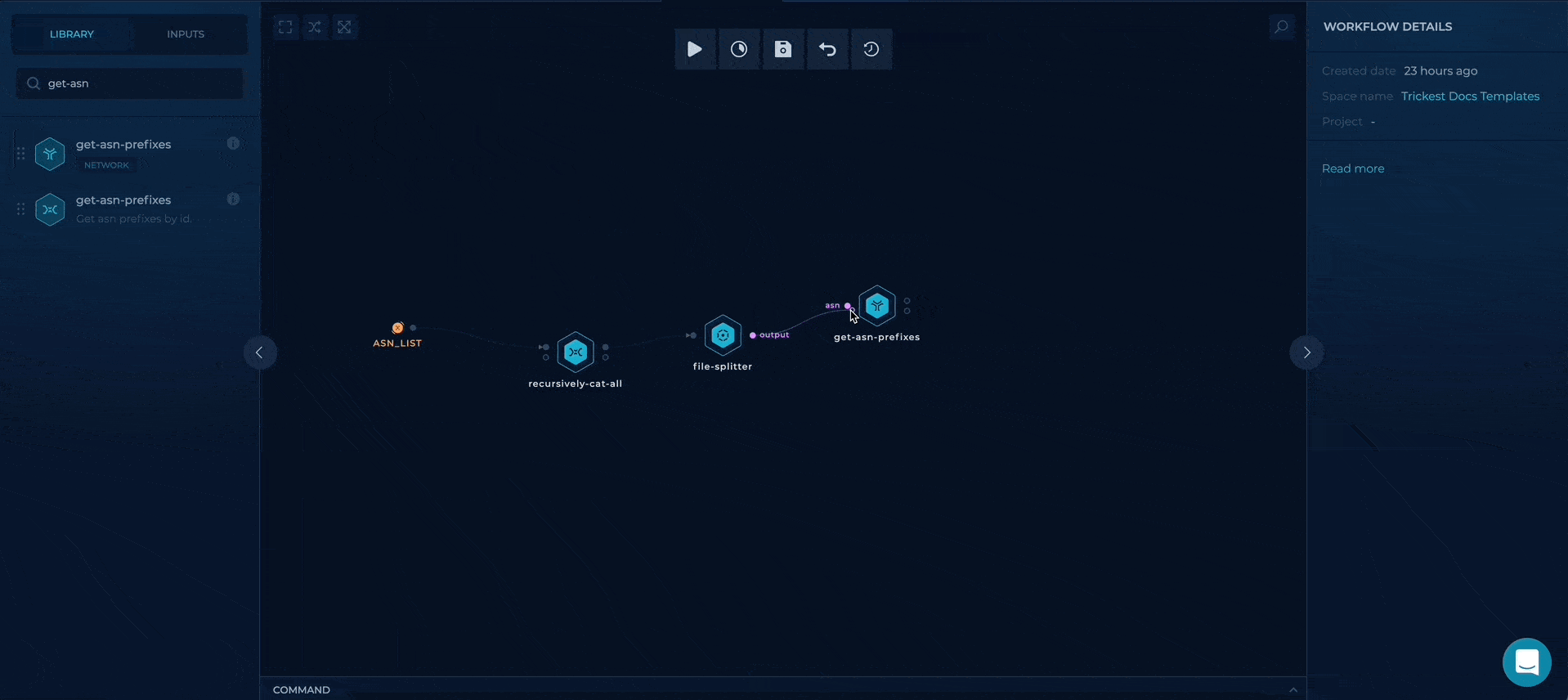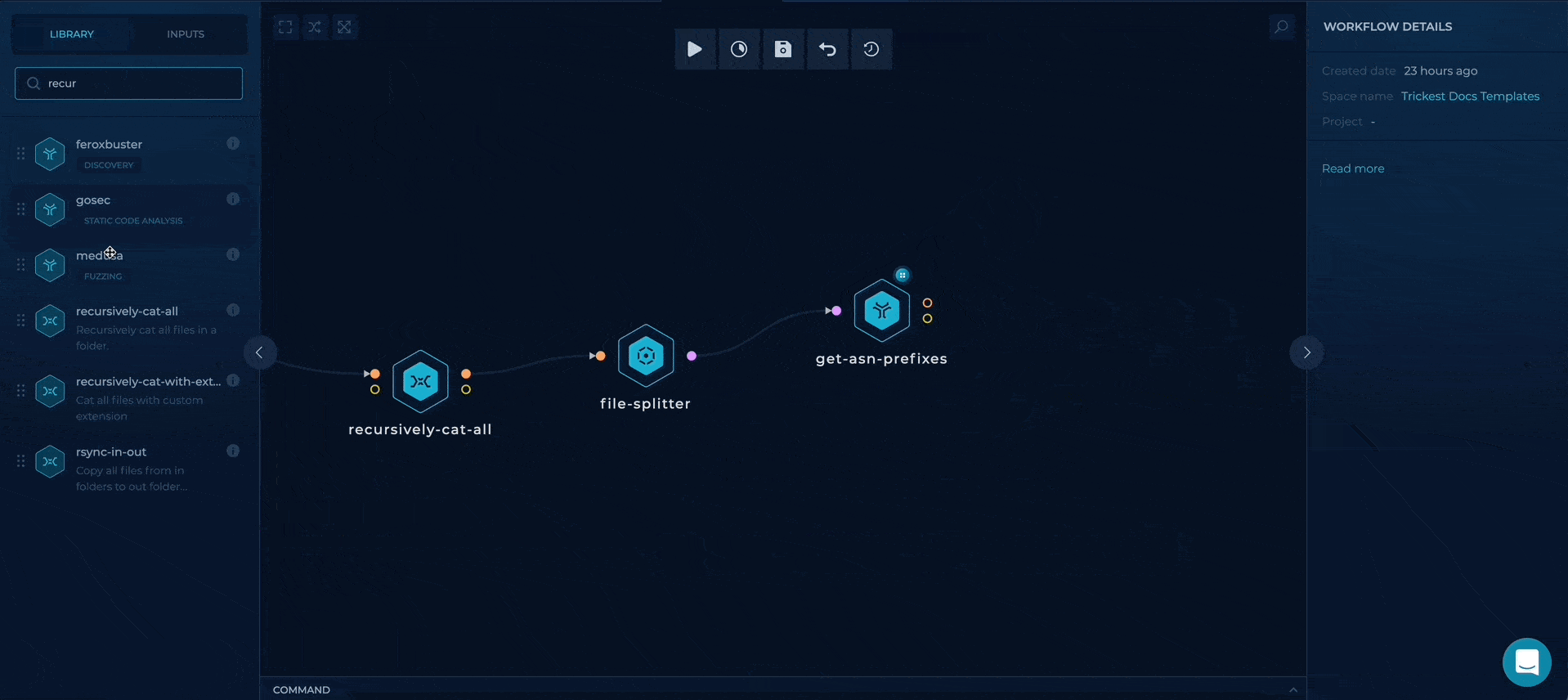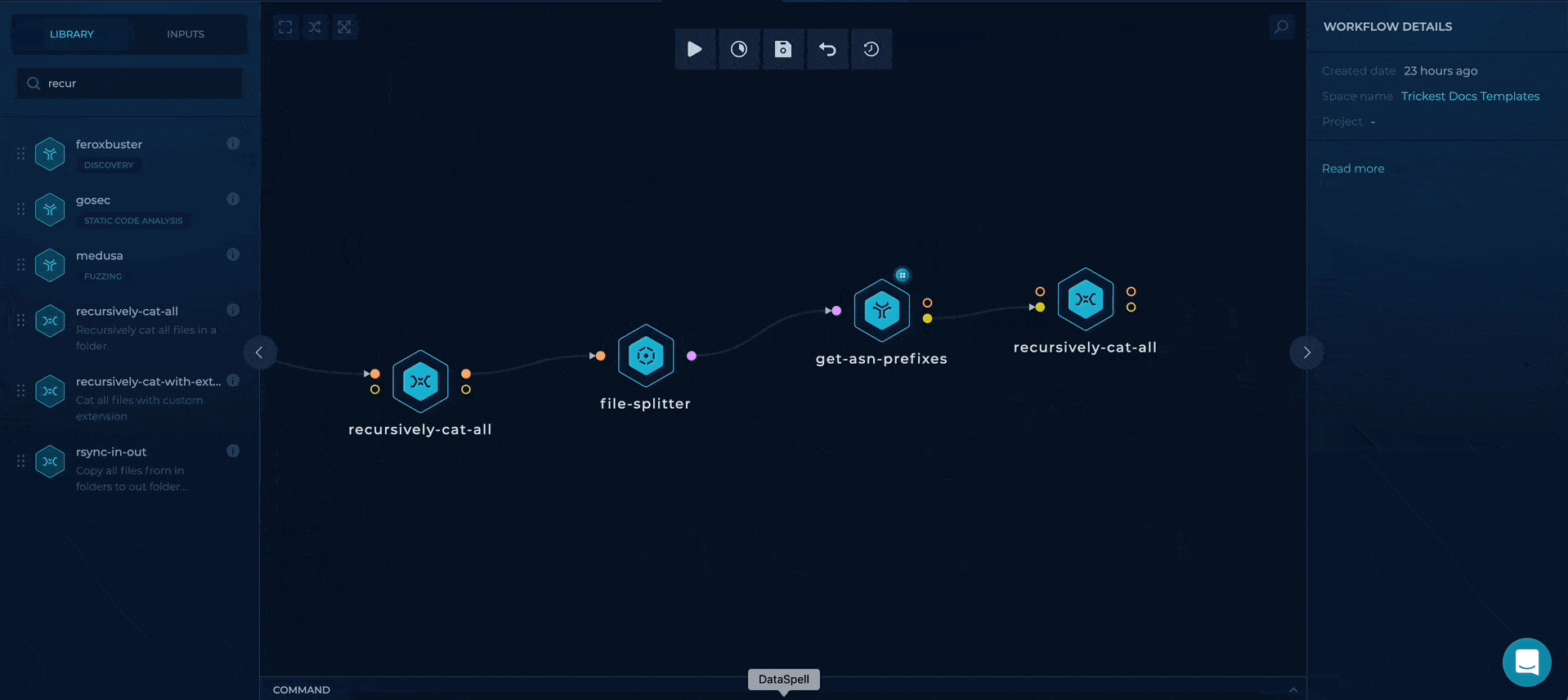
executing get-asn-prefixes in parallel and merging the results
Executing masscan for each subnet found
We will use file-splitter node again to execute masscan for each subnet found.
Masscan is a great and fast port scanner. By default, it accepts ip-range string parameter, ports where you describe which ports you want it to scan. We will additionally enable the rate parameter for it to be faster and enable banners boolean flag to gather more information about the services running on found open ports.

Execute masscan for each ASN prefix found
Getting and parsing masscan results
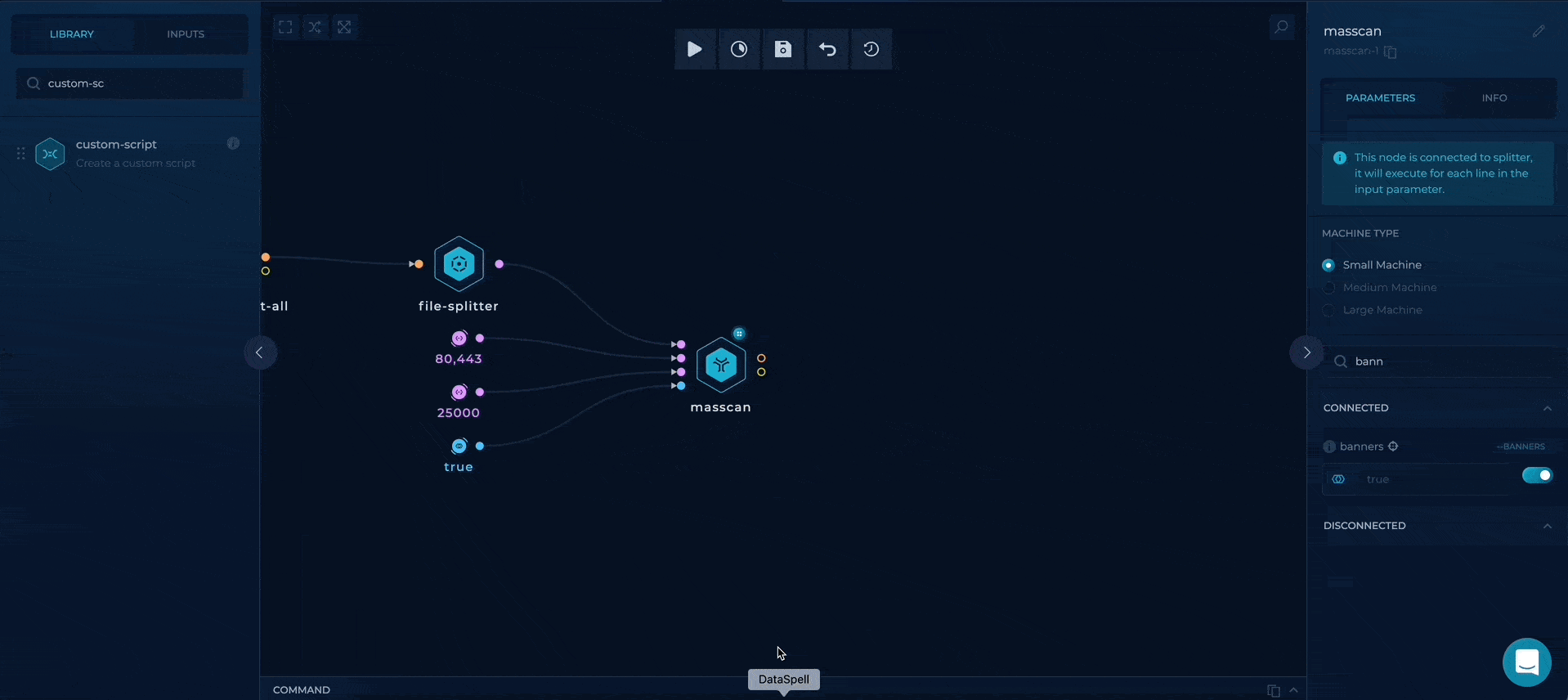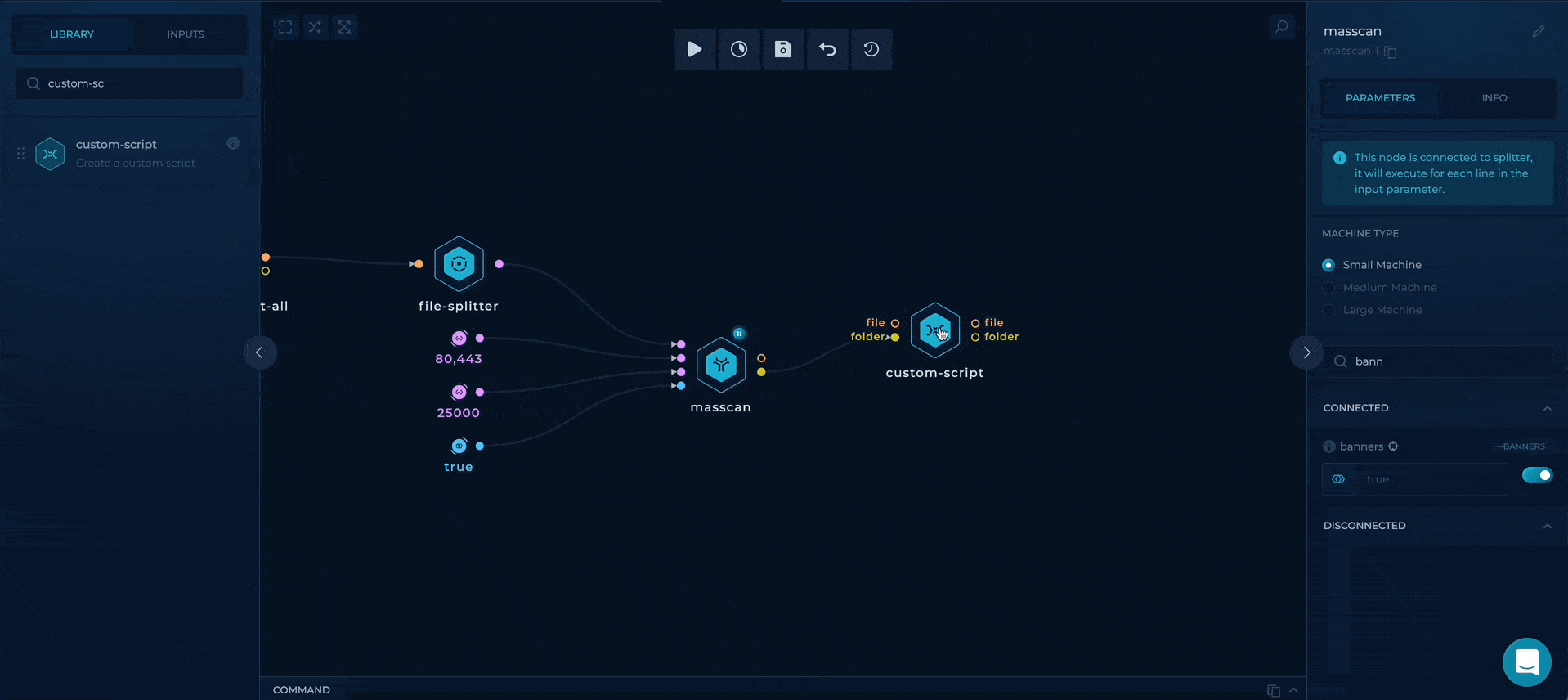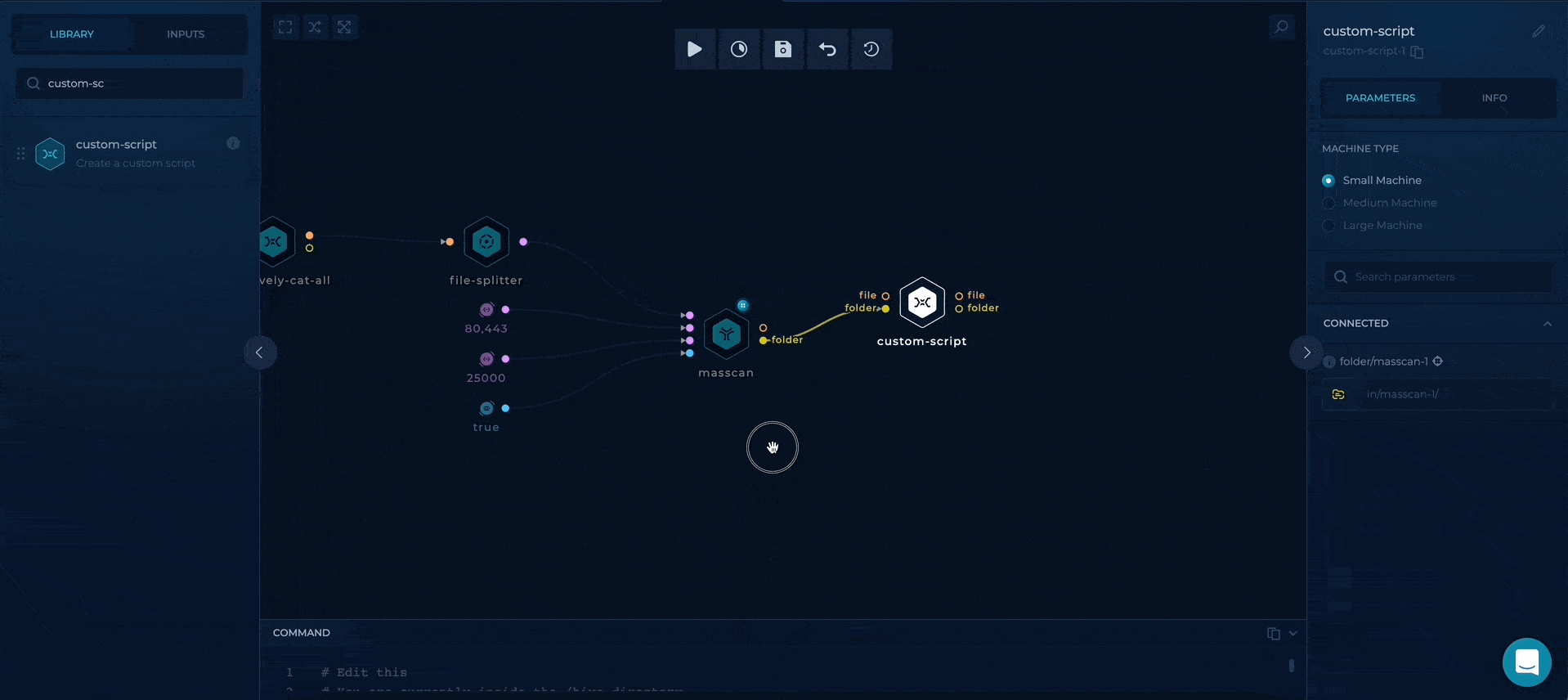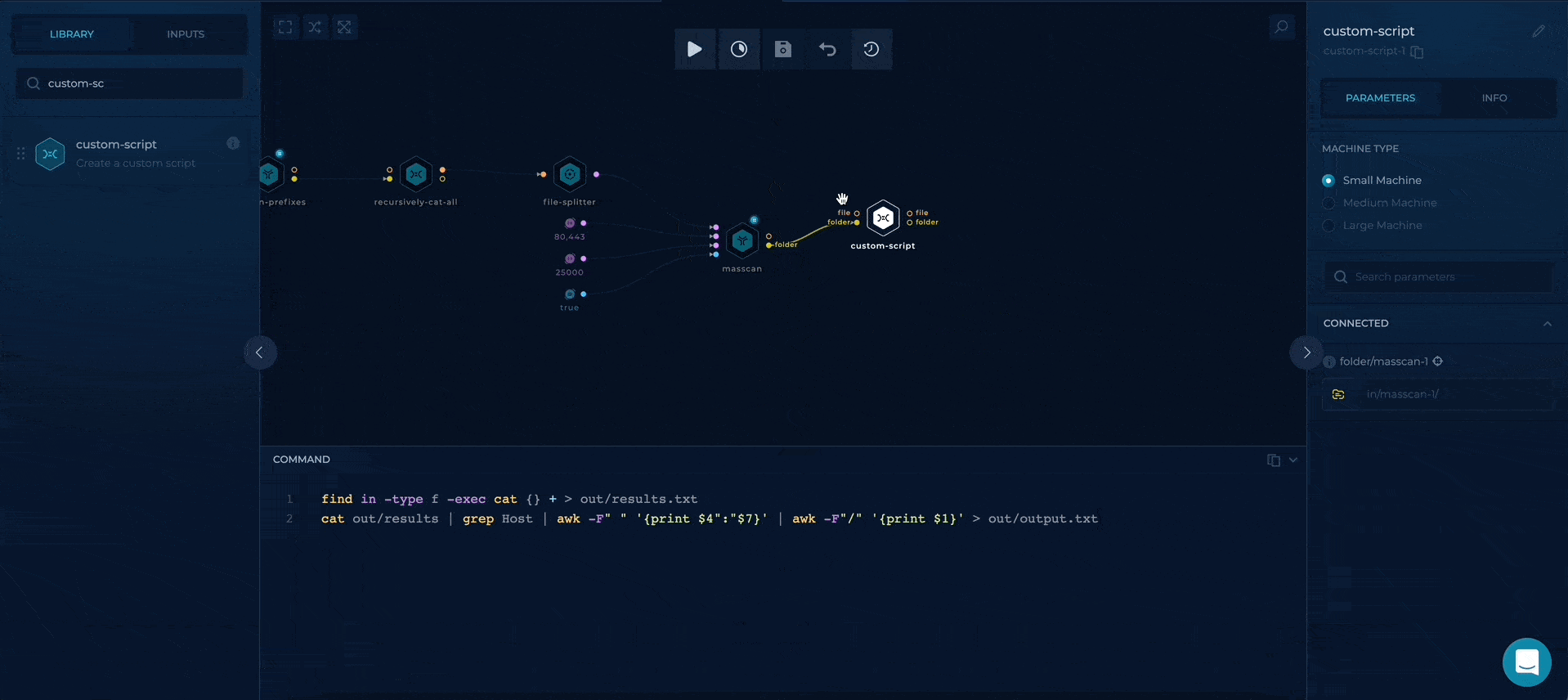
At the end, we will take advantage of custom-script to parse the masscan results and output the raw result, which will be available at out/results.txt and ip:port result which will be available on out/output.txt so we can develop this workflow further!
Here is the script that does it:
find in -type f -exec cat {} + > out/results.txt
cat out/results | grep Host | awk -F" " '{print $4":"$7}' | awk -F"/" '{print $1}' > out/output.txt
Execution and results
The last node, in this case, recursively-cat-all, will contain raw masscan data, and output with ip:port structure.
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Changing machine type of tools to speed up the execution
- Parsing the get-asn-prefixes output for IPv4 and IPv6 subnets
- Implement a mechanism to get the new ports through scheduling and get-trickest-output