Check For Subdomain Takeover
A subdomain takeover is a type of cyber attack in which an attacker is able to gain control of a subdomain that is no longer in use or has not been properly configured. This can allow the attacker to use the subdomain to host malicious content, phish for sensitive information, or perform other malicious activities.
Complexity: basic
Category: Vulnerability Scan & Management
Tools
Setup
You can set up this workflow by changing nuclei url-list input value:
- TARGETS - provide a file containing subdomains/hostnames list, as a target
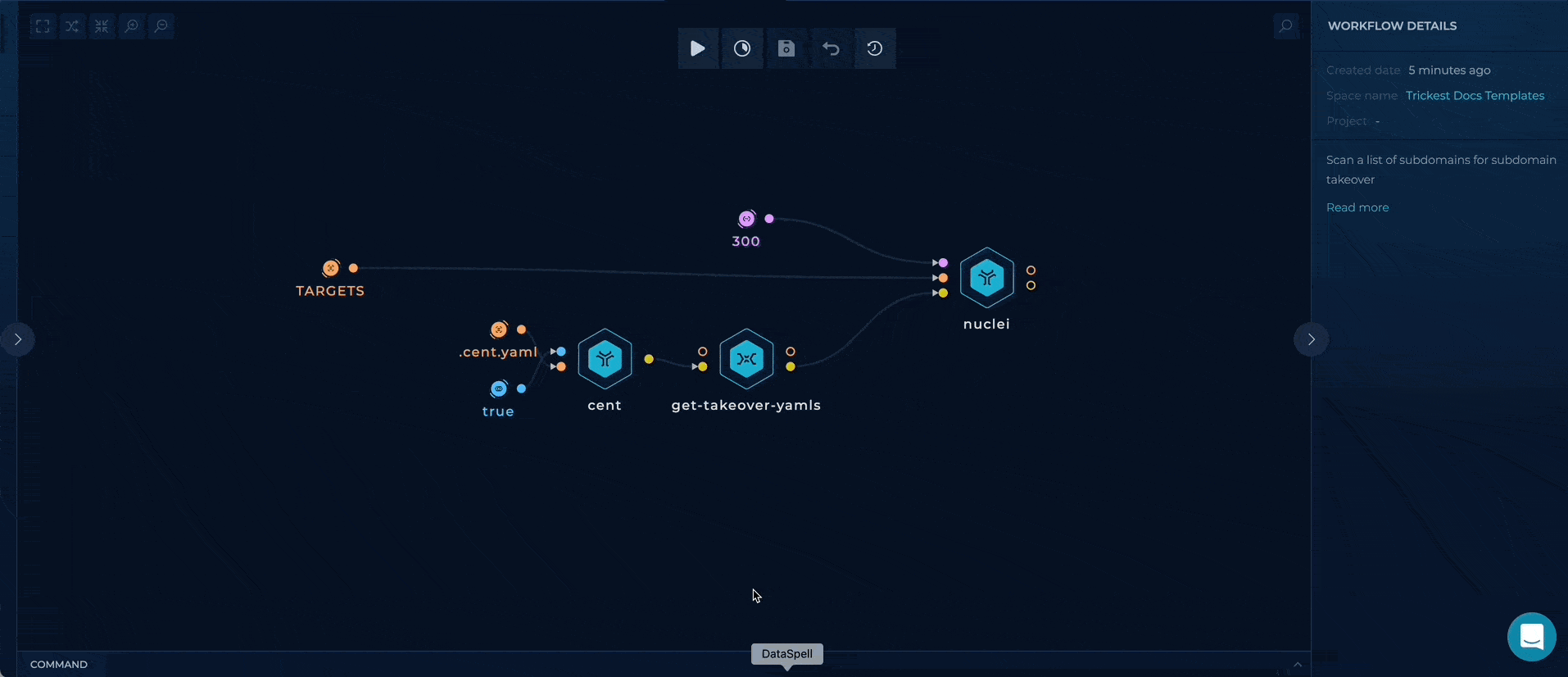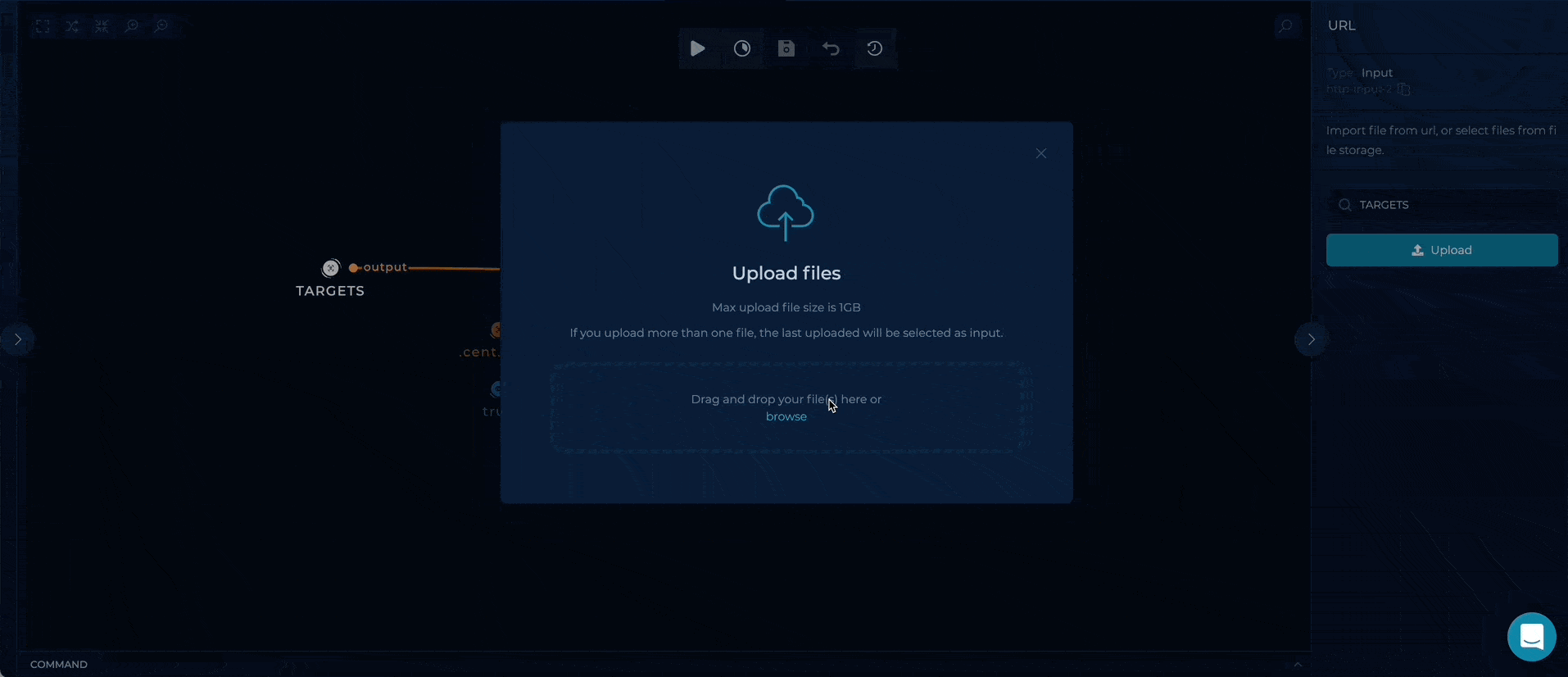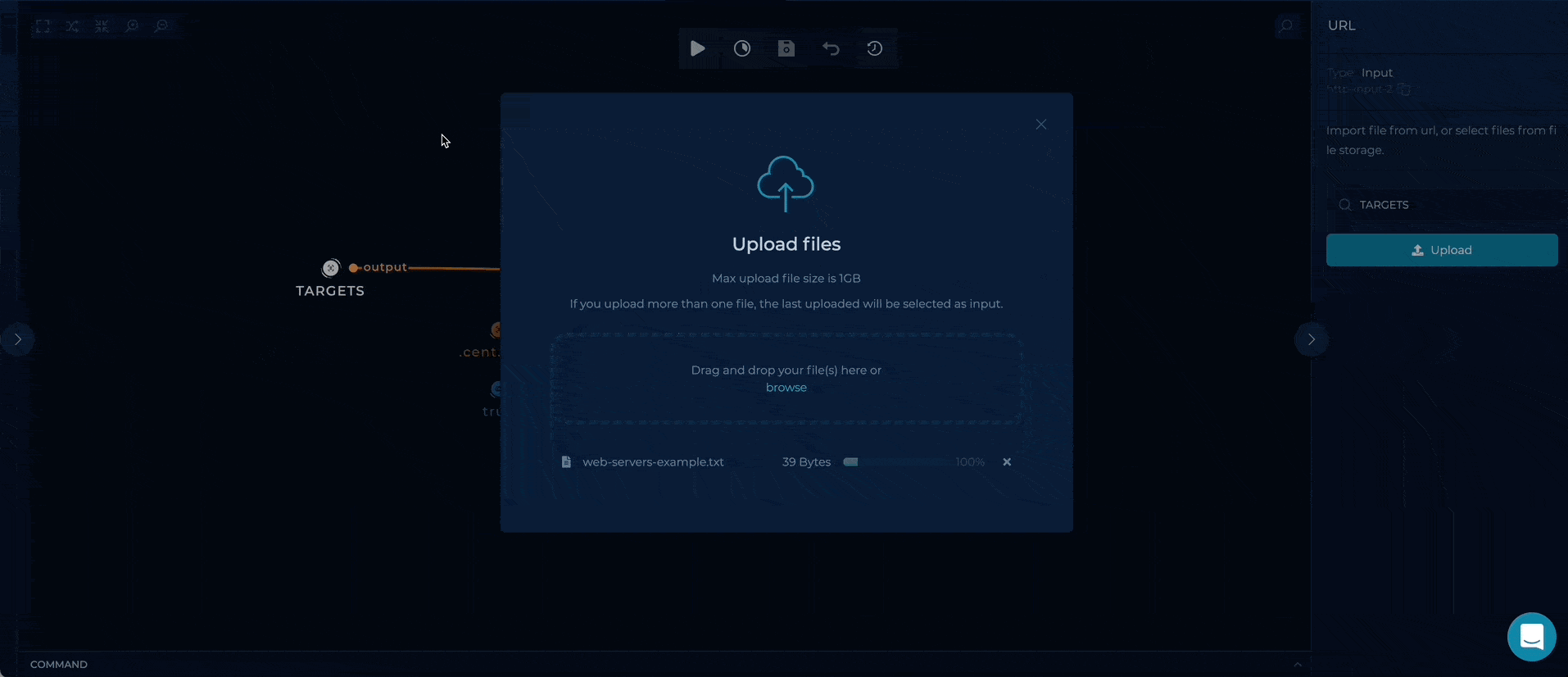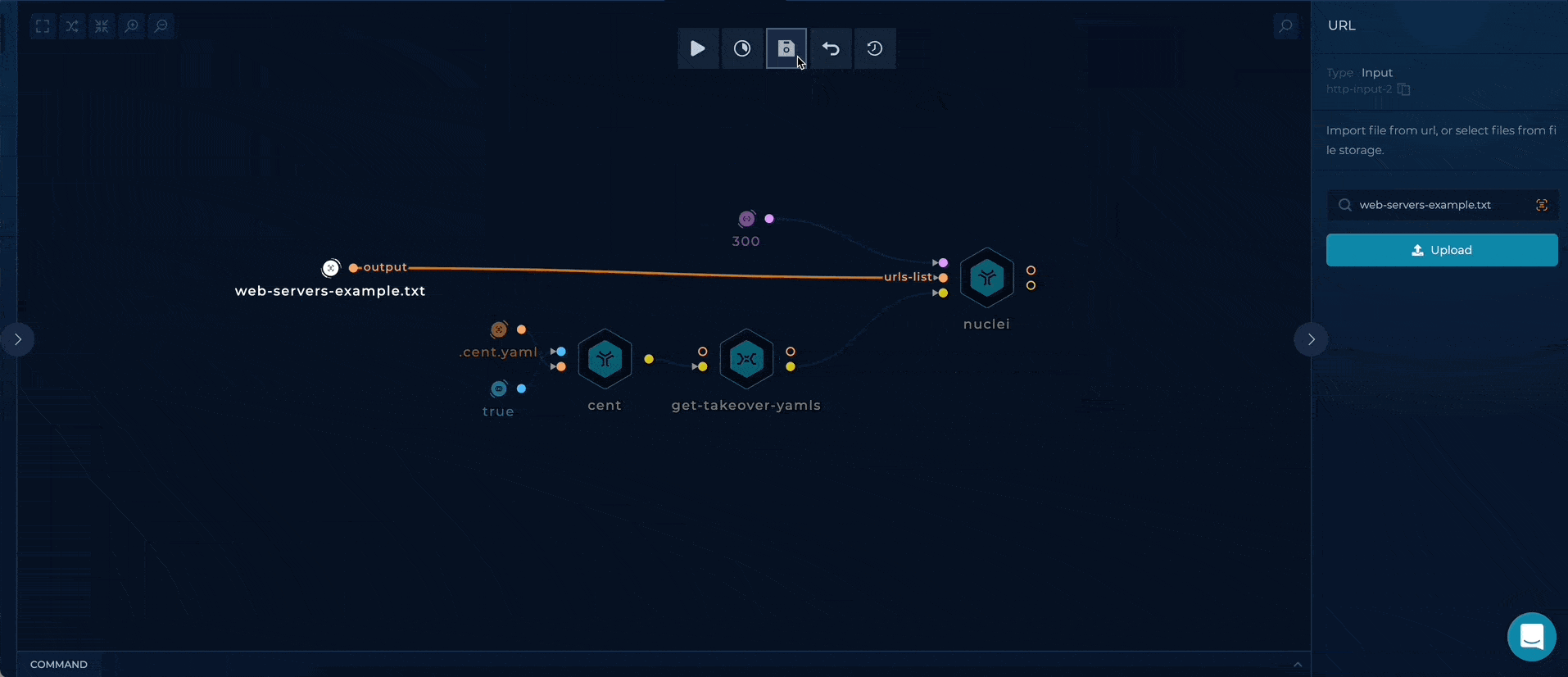
Workflow Targets Setup
Execution and results
After setup workflow is ready to be executed. Once workflow's last node, nuclei tool, is finished result can be viewed and downloaded.
nuclei tool will contain all of the possible subdomain takeovers.
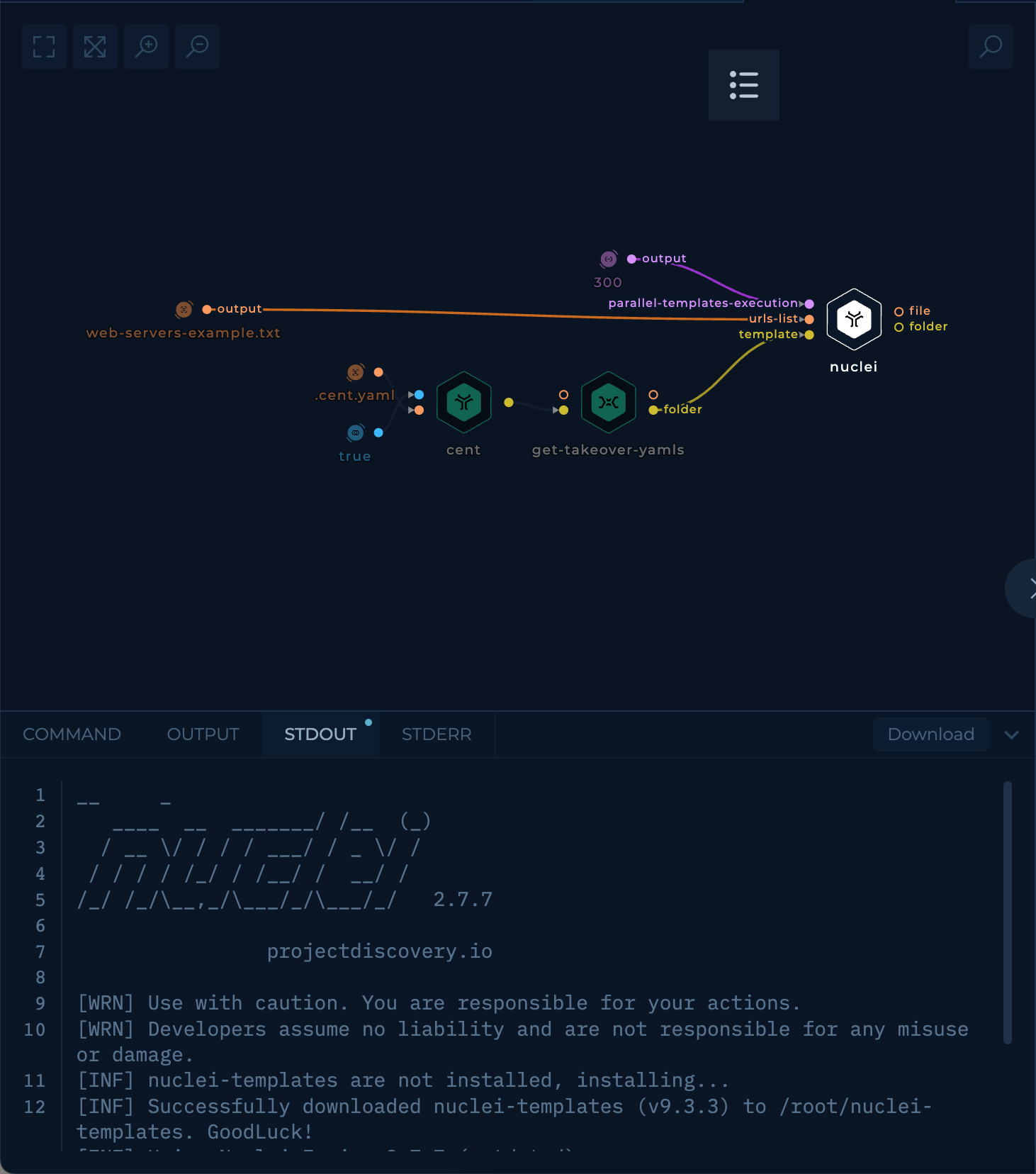
nuclei stdout of subdomain takeover workflow
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Add more nuclei takeover templates
- Get all DNS records and filter them in search for more attack vectors
- Execute nuclei through batch-output
- use notify to send newly found results via anew