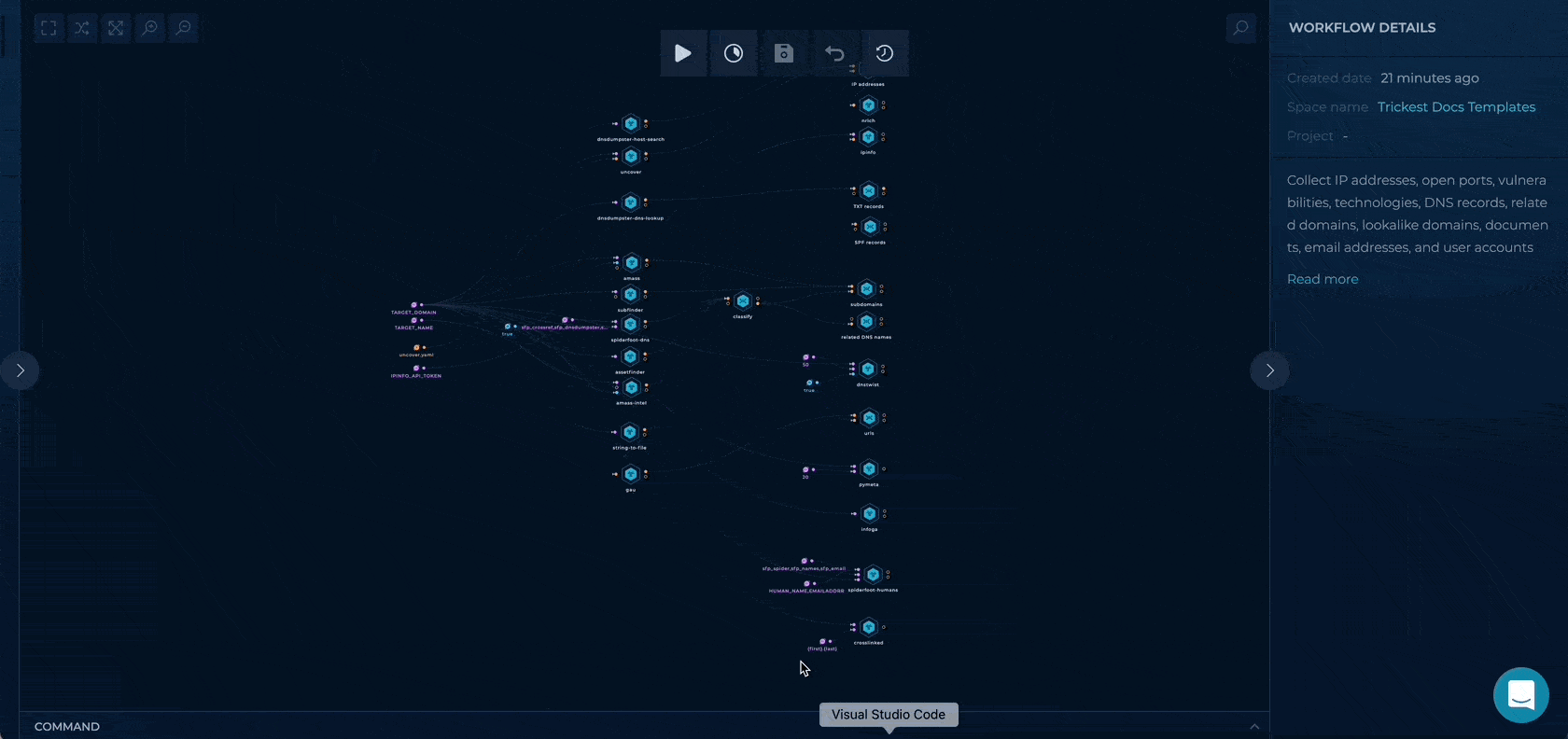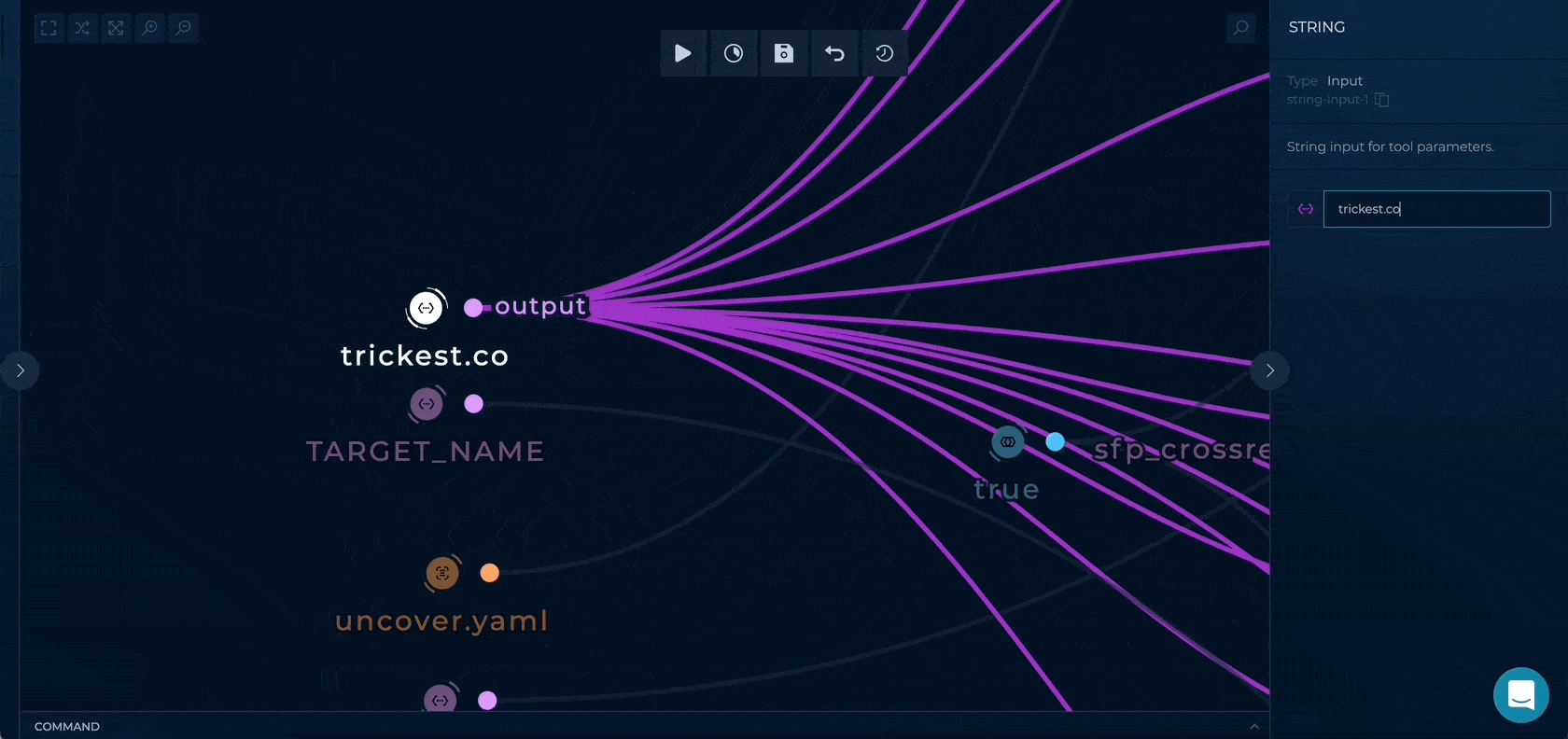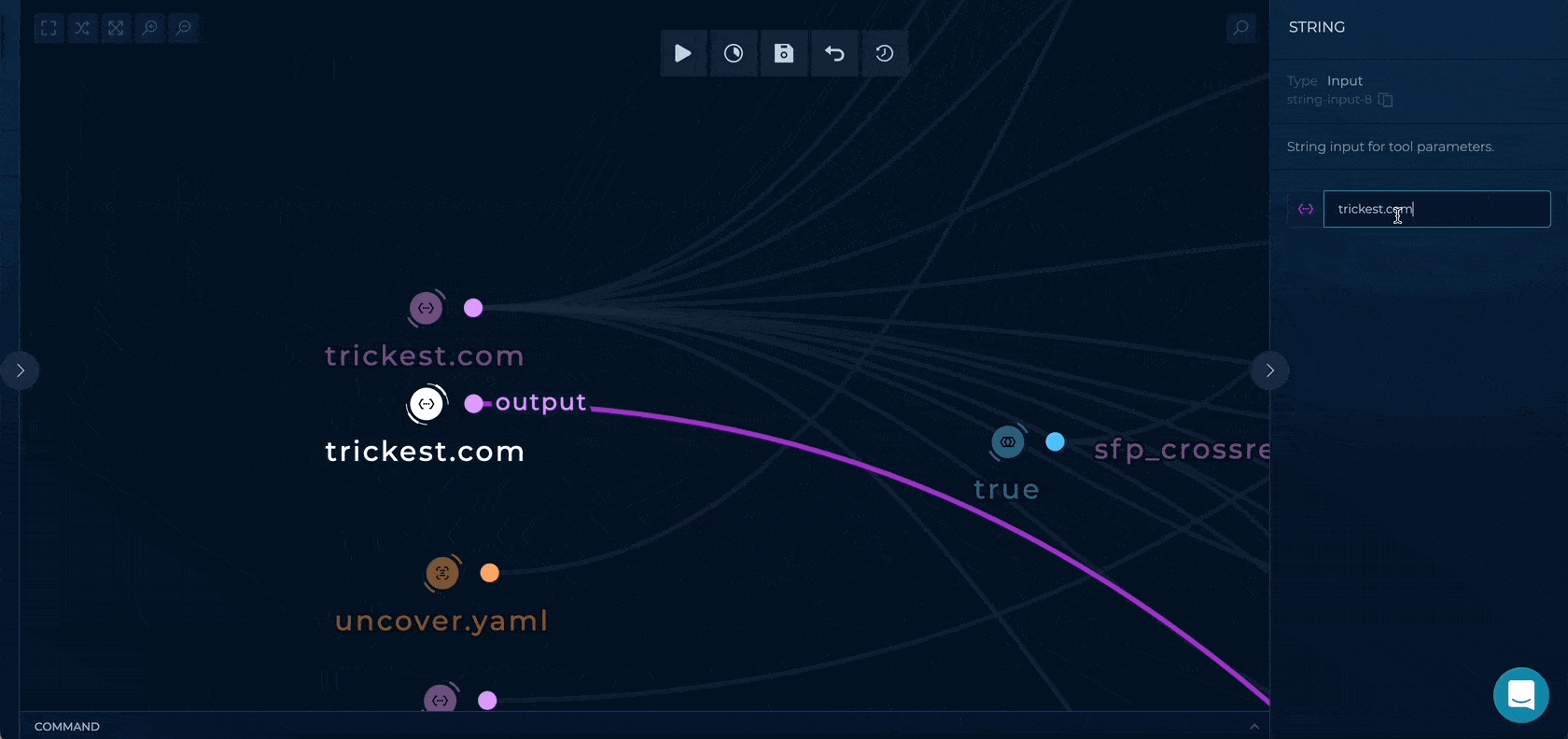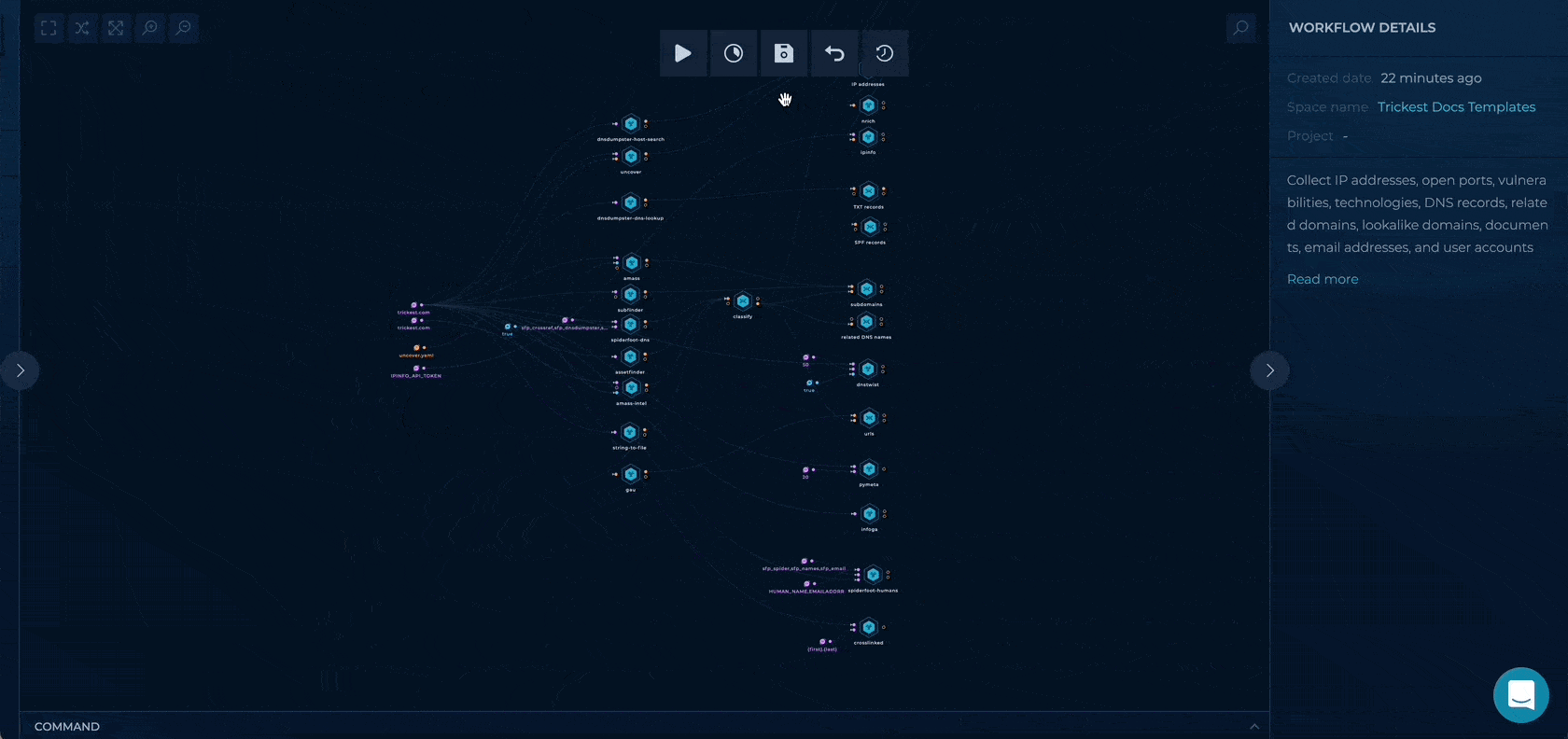
Extensive OSINT
This workflow can help threat analysts track the movements and actions of malicious actors, identify potential vulnerabilities in an organization's systems, and gain insights into the tactics, techniques, and procedures (TTPs) used by adversaries. By analyzing this data, analysts can better understand the threat landscape and develop strategies for defending against potential attacks.
Complexity: advanced
Category: Threat Intelligence
Tools
- dnsdumpster-host-search
- dnsdumpster-dns-lookup
- amass
- subfinder
- uncover
- assetfinder
- gau
- ipinfo
- nrich
- dnstwist
- pymeta
- infoga
- crosslinked
Setup
You can set up this workflow by providing a root domain name, company name, and, optionally, ipinfo API key and uncover YAML config file.
Execution and results
As mentioned in the workflow description, it generates a lot of data, and you can see the outputs at all of the end nodes.
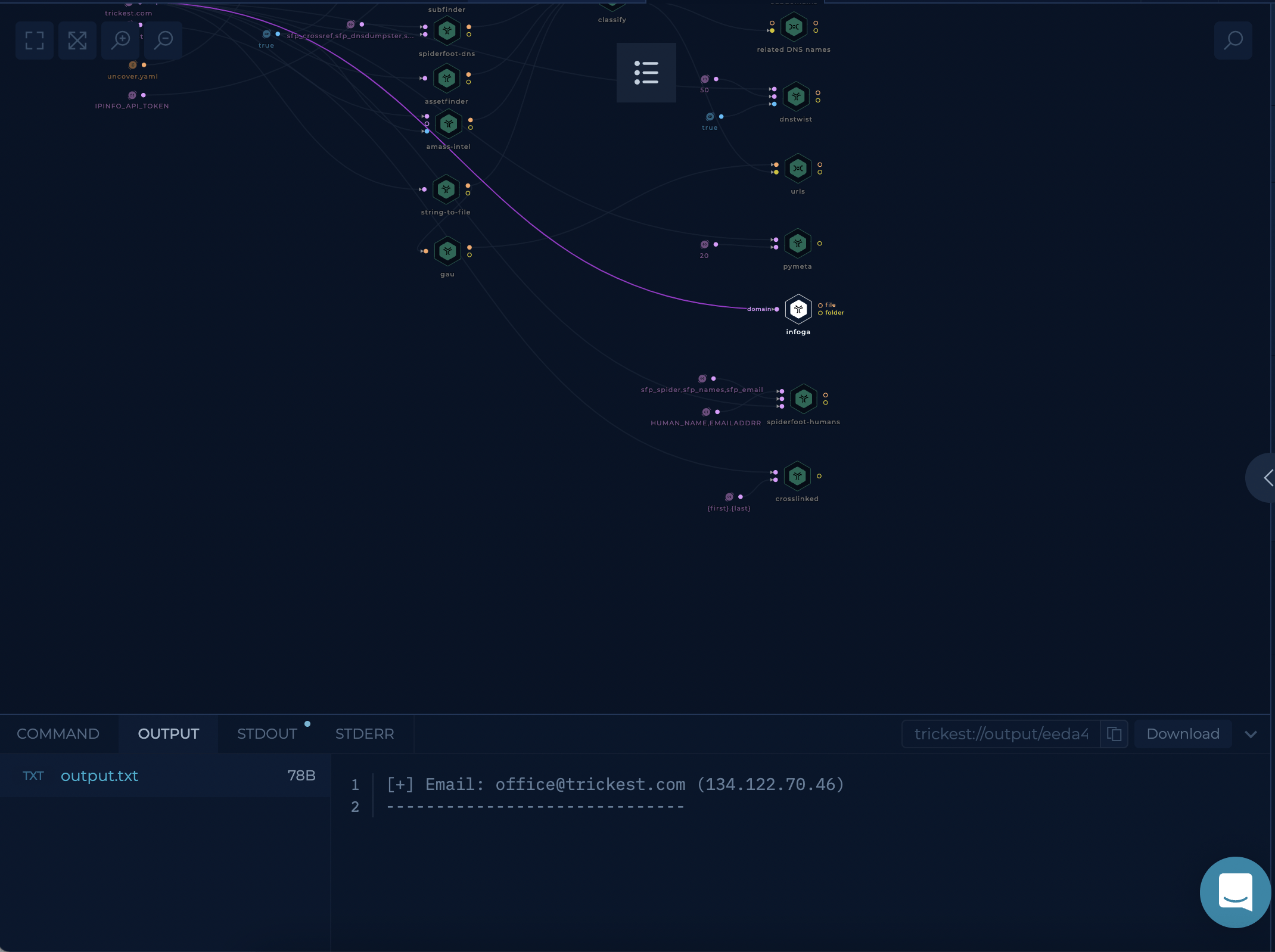
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Changing machine type of tools to speed up the execution
- Add more tools and checks
- Generate a unified report from the outputs