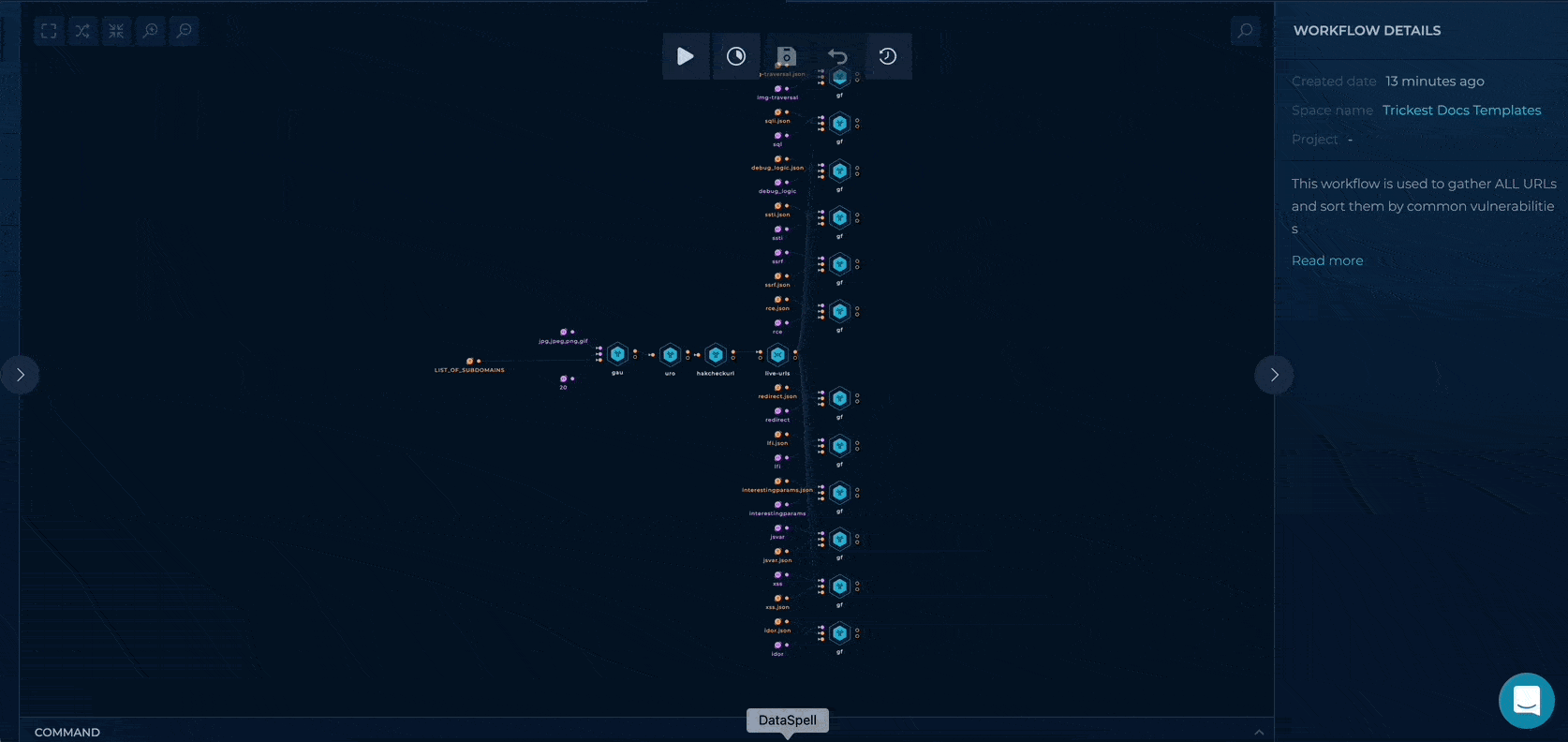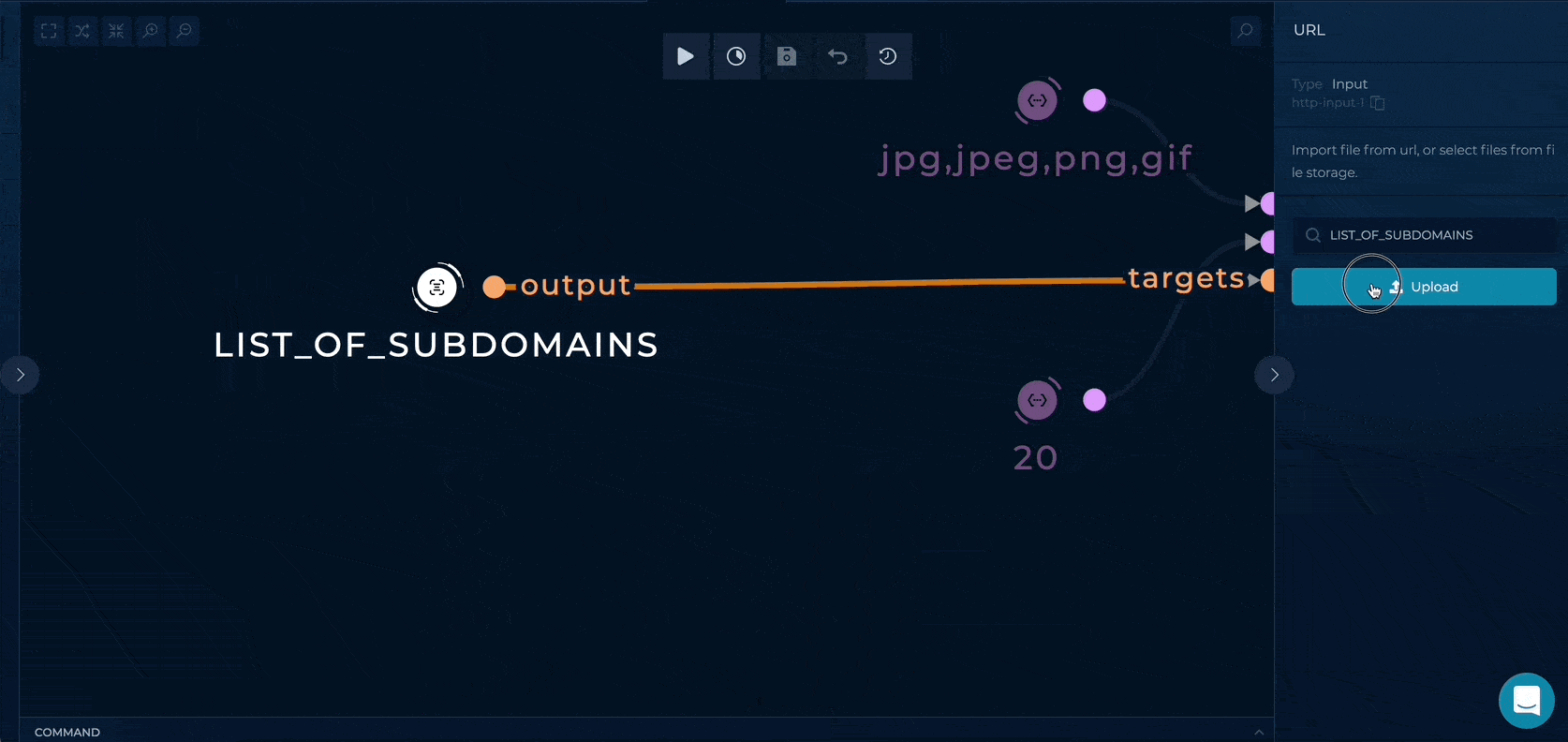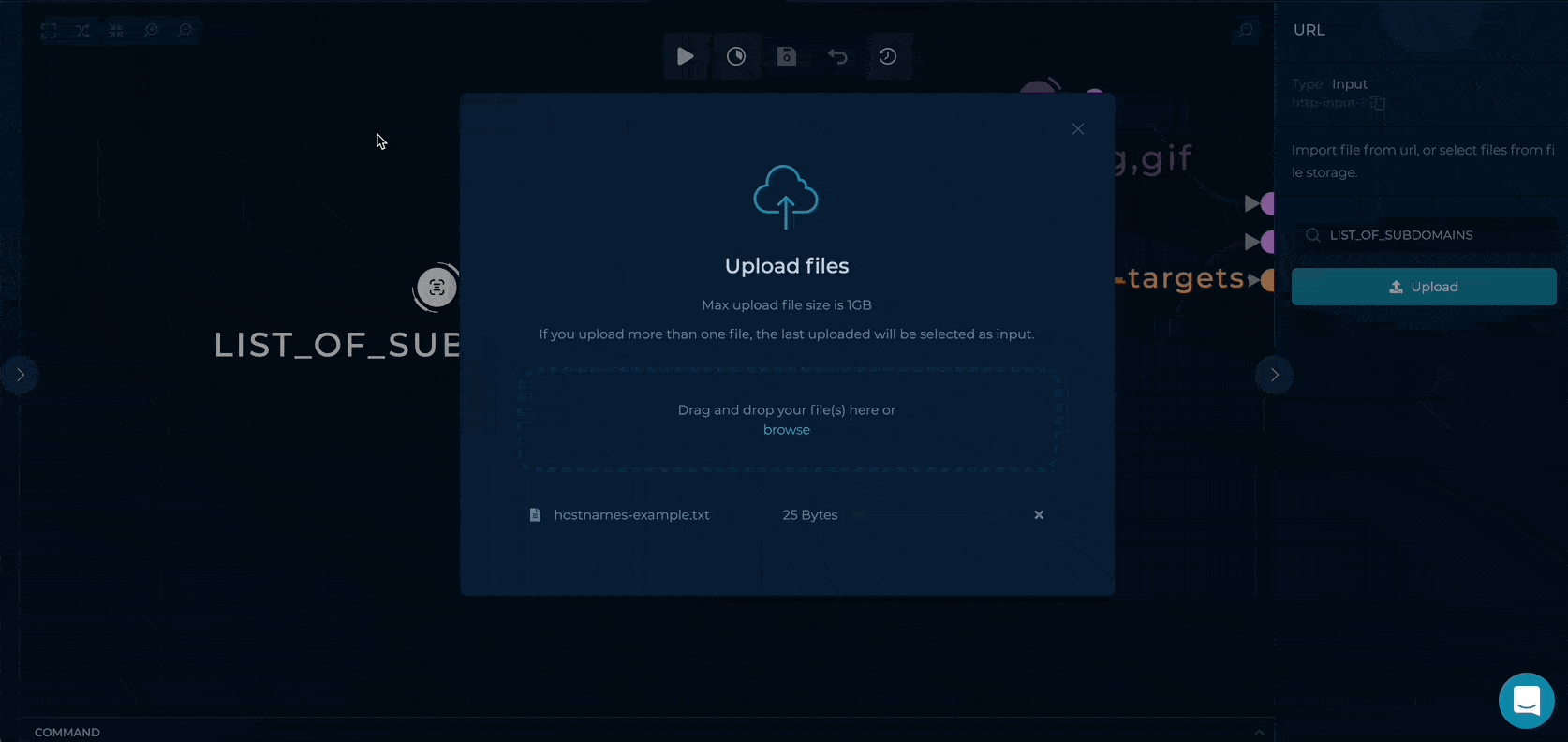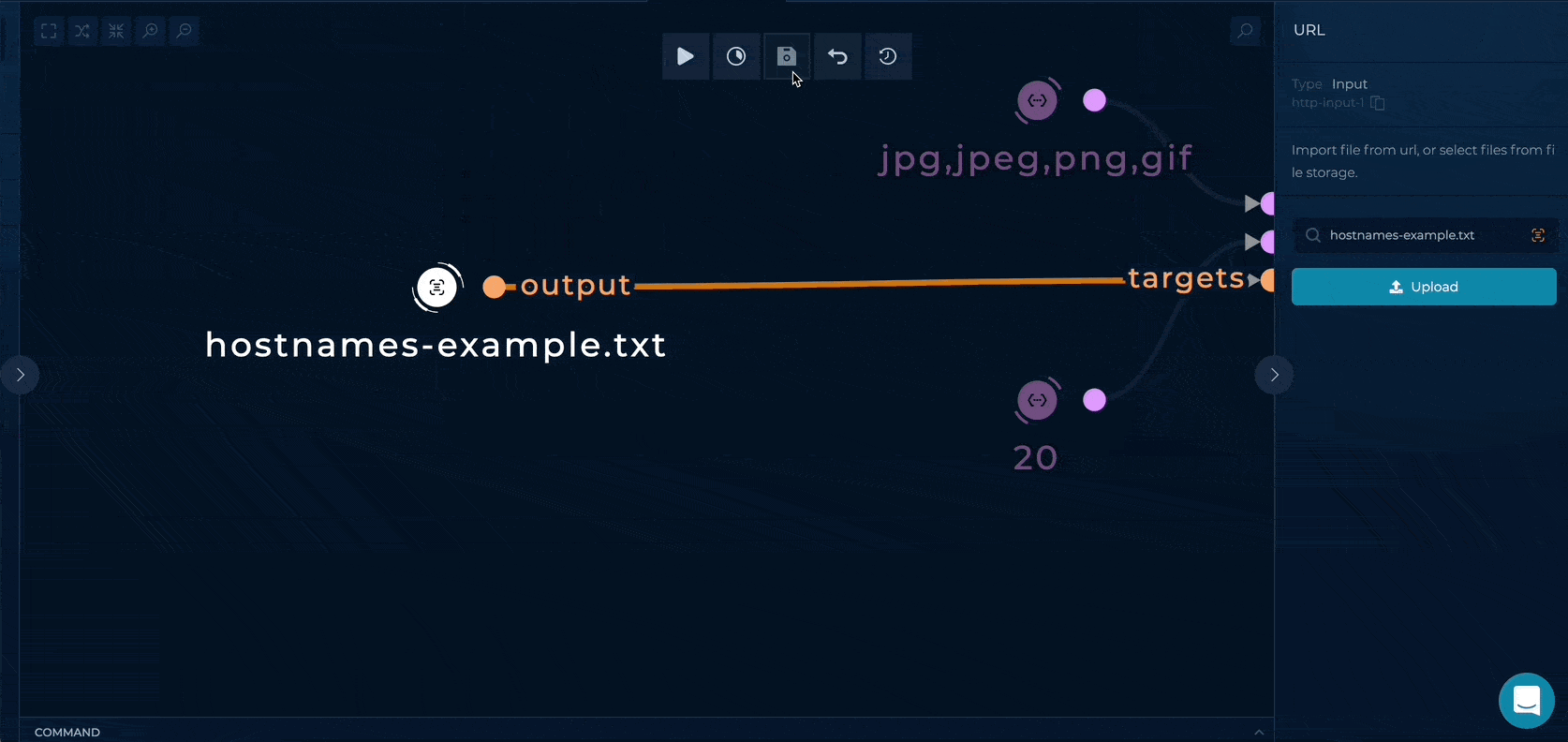
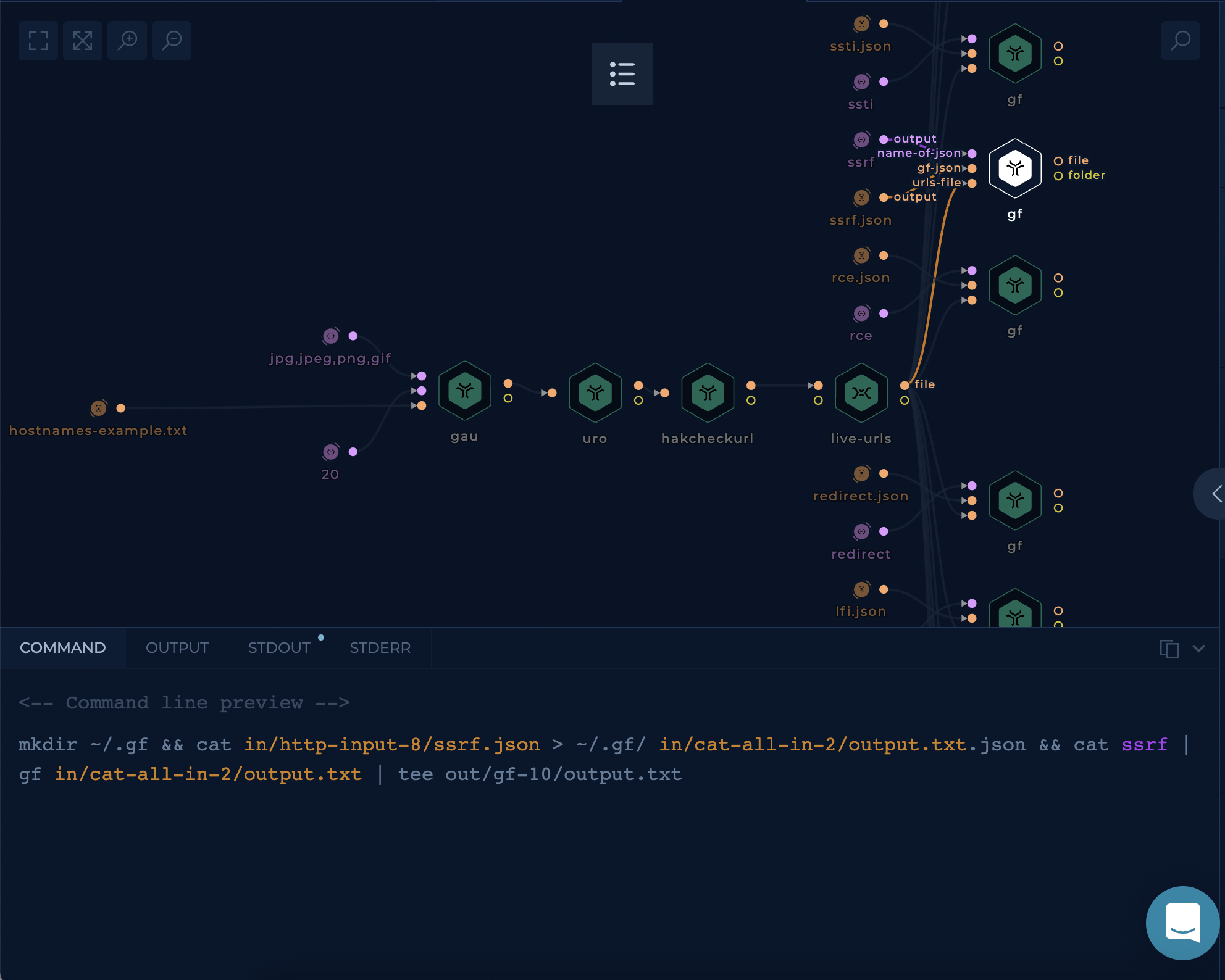
Get all URLs and classify by vulnerability type
While "Get-all-public-urls" workflow will give us only the URL results, this workflow will sort out all of the found URLs into appropriate categories. You can check out the vulnerability categories that are supported below.
Complexity: advanced
Category: Web Discovery
Repository: https://github.com/trickest/inventory
Tools
Setup
The input is a list of webservers or hostnames, this workflow will gather all of the URLs archived by different providers and classify them by vulnerability type:
- Image Traversal
- SQL Injection
- Debug Logic
- Server Side Template Injection
- Server-Side Request Forgery
- Remote Code Execution
- Open Redirect
- Local File Inclusion
- Interesting Parameters
- JS Variables
- Cross-Site Scripting
- Insecure Direct Object Reference
Workflow Targets Setup
Execution and results
After setup workflow is ready to be executed. Once workflow last nodes, gf tools, are finished results can be viewed and downloaded.
Each of gf tool nodes will contain URLs for a particular vulnerability category.
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Execute vulnerability scanners like nuclei on particular vulnerability findings per tag
- Add more vulnerability categories and improve gf patterns
Check out also this Web Discovery workflow - Get All Public URLs!