Brute-Force Files & Directories on a List of Hosts
Getting as much information about web application structure is sometimes crucial for any penetration testing & bug bounty engagement. Exposed files and directories could contain secrets (../.env or dockercompose.yaml files for example), be vulnerable to specific exploits, give unprivileged access on new endpoint, etc.
Complexity: intermediate
Category: Web Discovery
Tools
Setup
You can set up this workflow by changing initial input value:
- URL_LIST - provide a file containing a list of web servers, as a target
In the example below, we're providing a sample as a target:
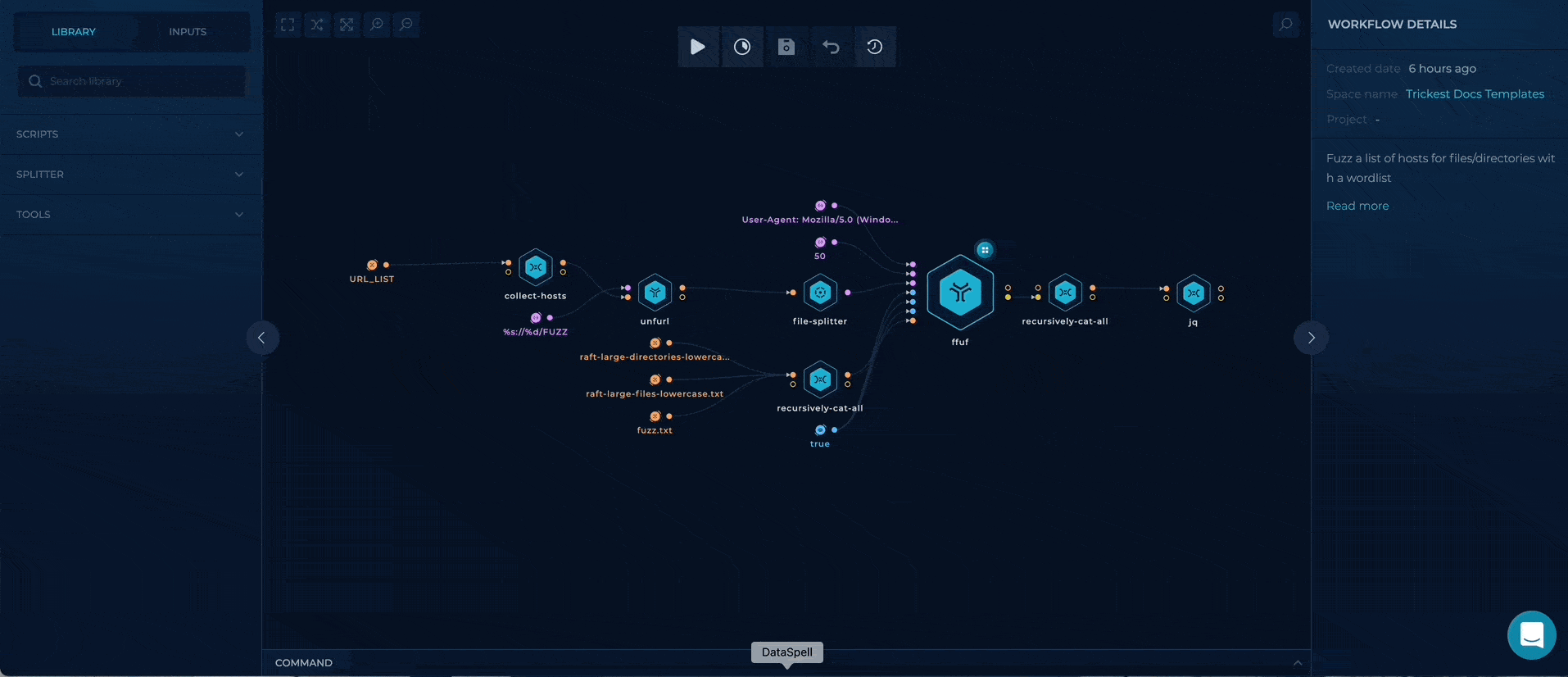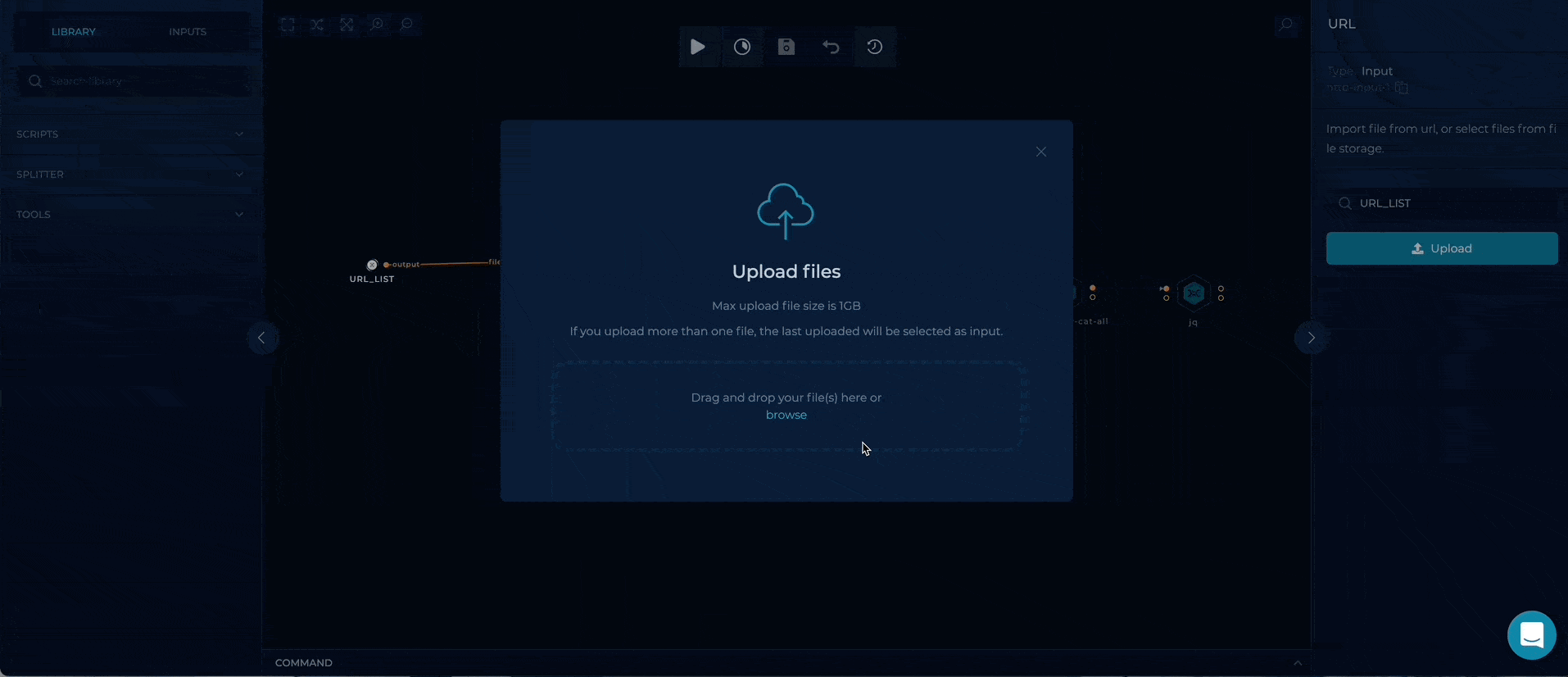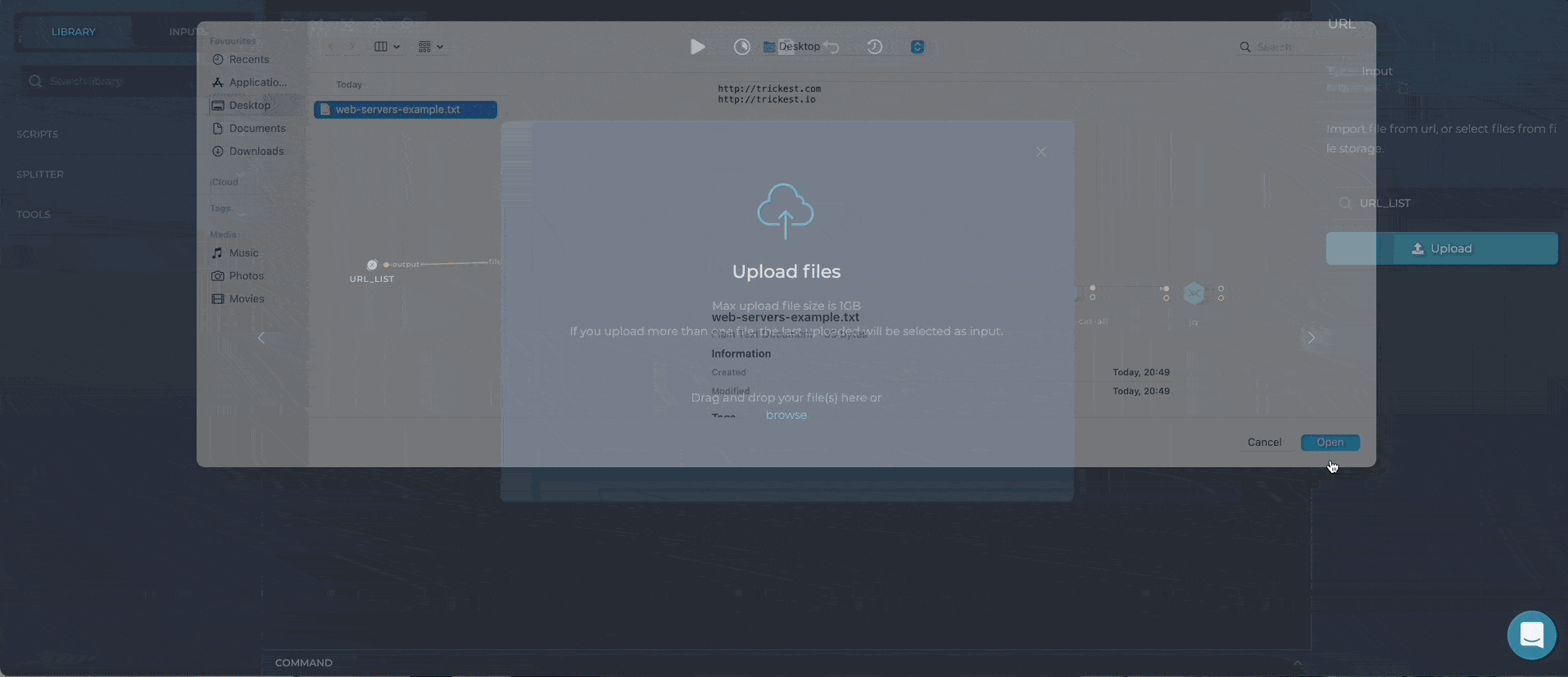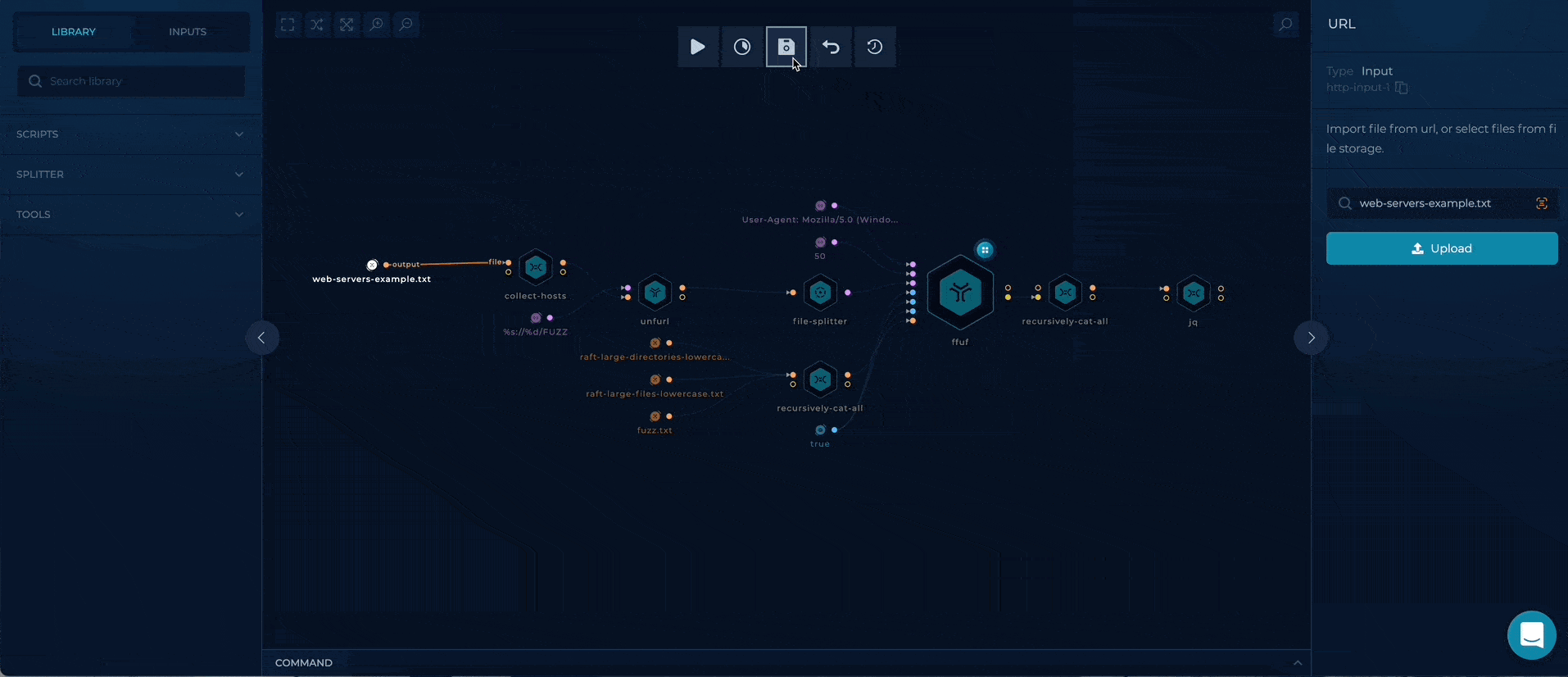
Workflow Targets Setup
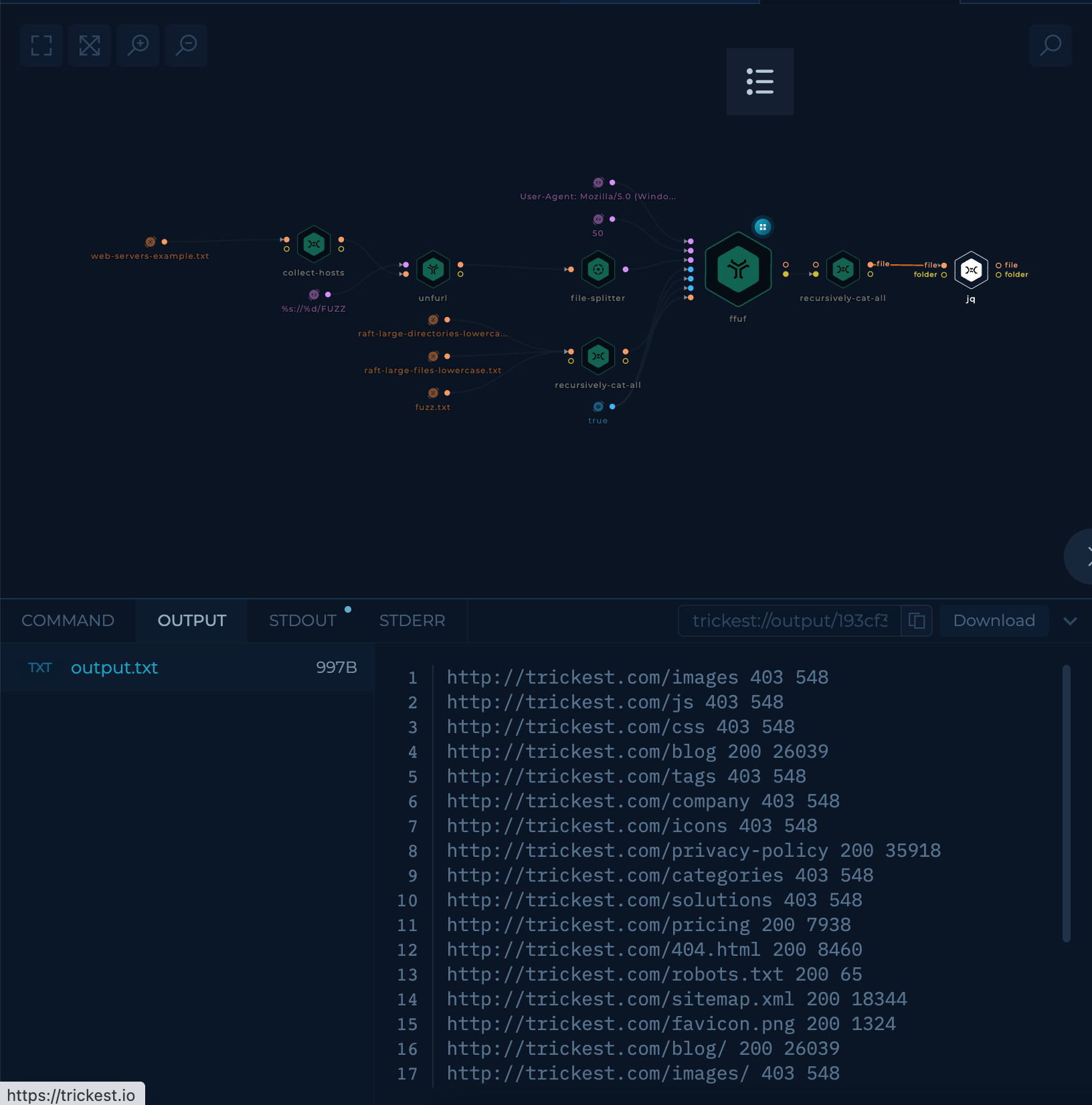
Execution and results
After setup workflow is ready to be executed. Once workflow's last node, jq script, is finished result can be viewed and downloaded.
jq node will contain parsed output of ffuf.
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Changing machine type of tools to speed up the execution
- Executing the workflow on multiple instances
grepdifferent status-codes and sort them- bypass 403 status codes
- use notify and anew to send newly found files and directories as notification messages
Check out also this Web Discovery workflow - Brute Force Parameters Single URL!