Enumerate Cloud Resources
After setup, workflow is ready to be executed. Once workflow's last node, `recursively-cat-all` script is finished, result can be viewed and downloaded.Exposed cloud resources like storage buckets might contain important information no one should see. If these resources aren't properly protected, someone who shouldn't have access could get their hands on sensitive data, like passwords or personal information. This could lead to problems like data breaches or identity theft. \
\
This workflow is finding your buckets based on the hostnames and company name used as a target.
Complexity: advanced
Category: Attack Surface Management
Workflow
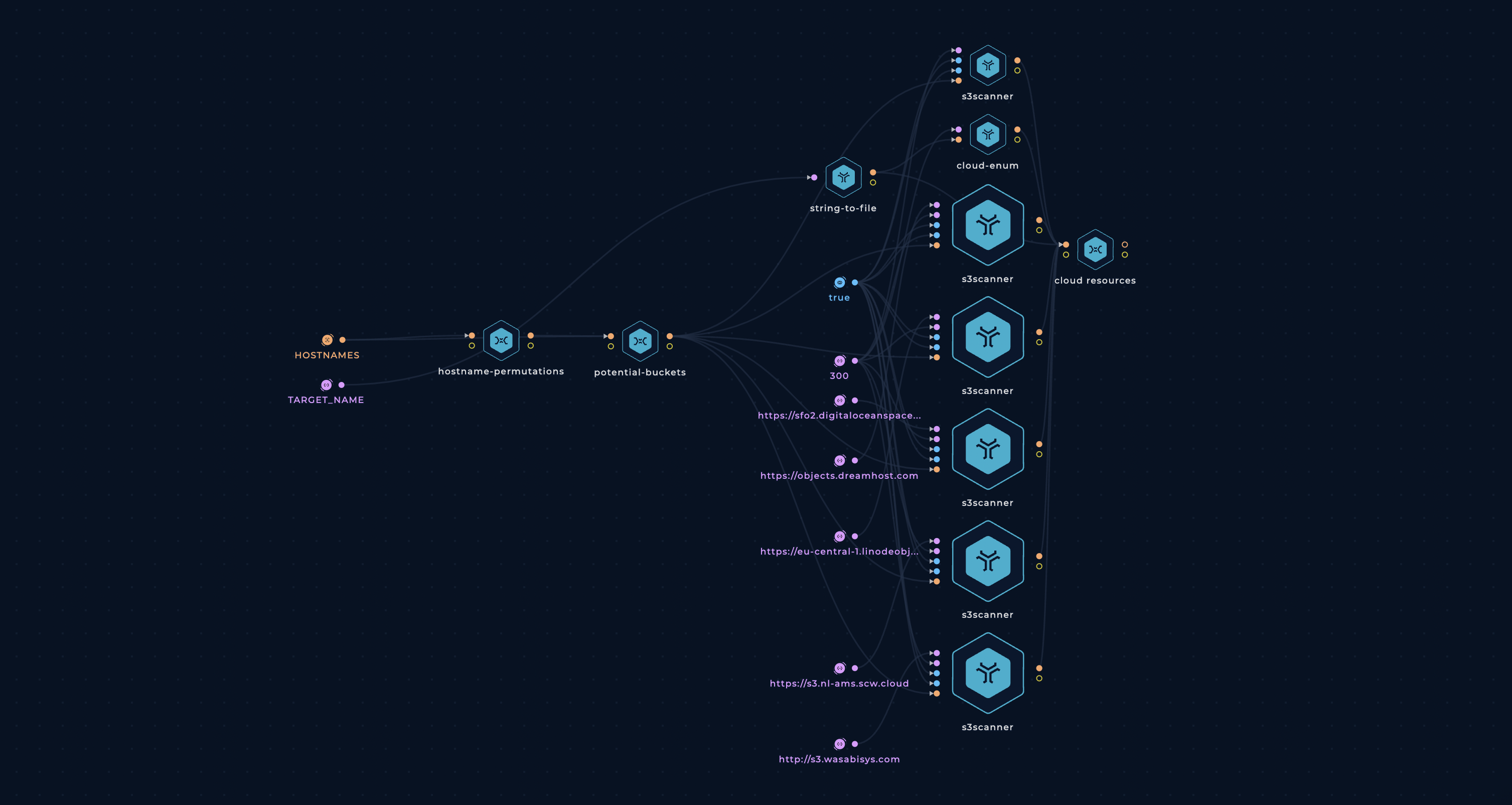
Enumerate Cloud Resources
Tools
Setup
You can set up this workflow by changing following input values:
- TARGET_NAME - provide a target name, e.g. trickest
- HOSTNAMES - provide a file containing hostnames list
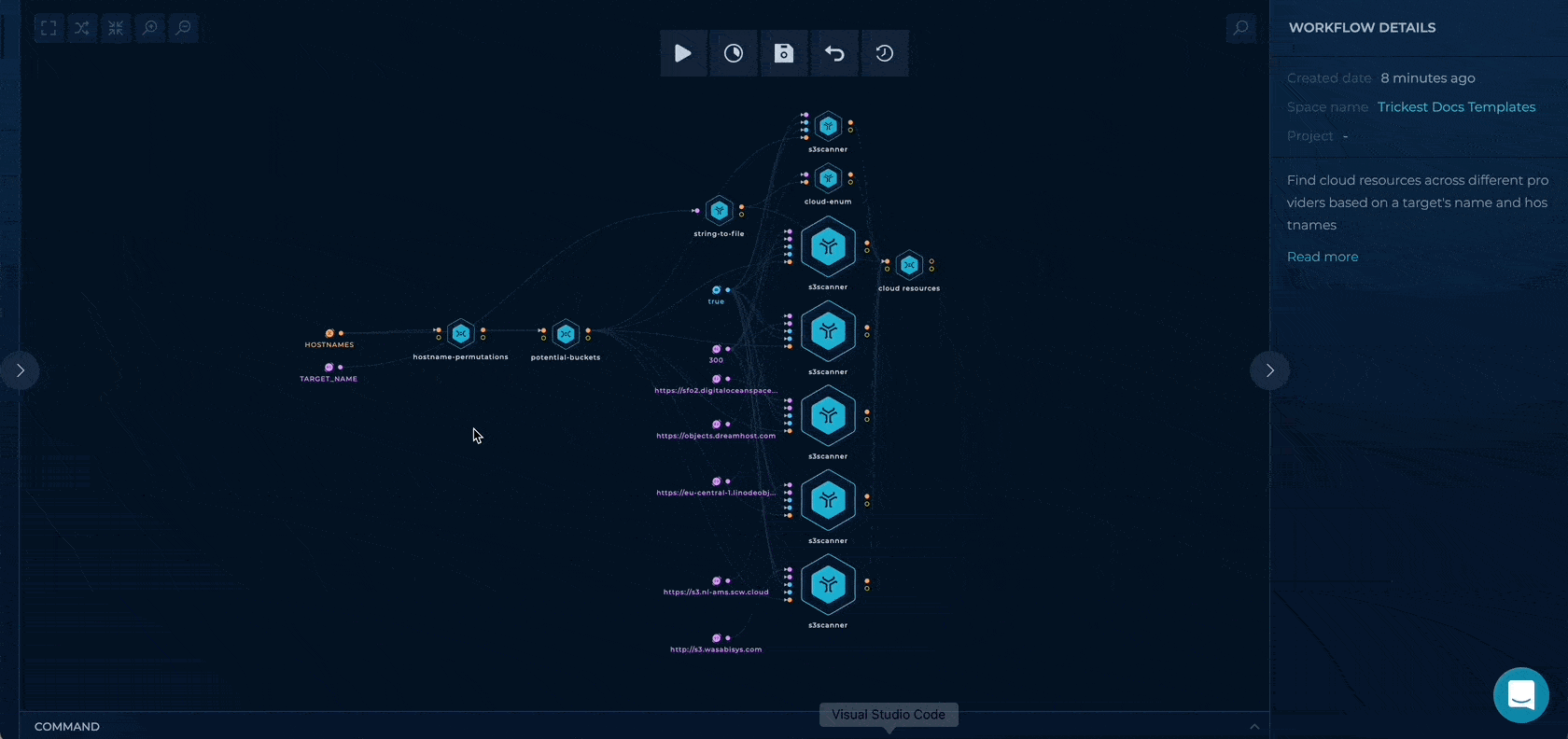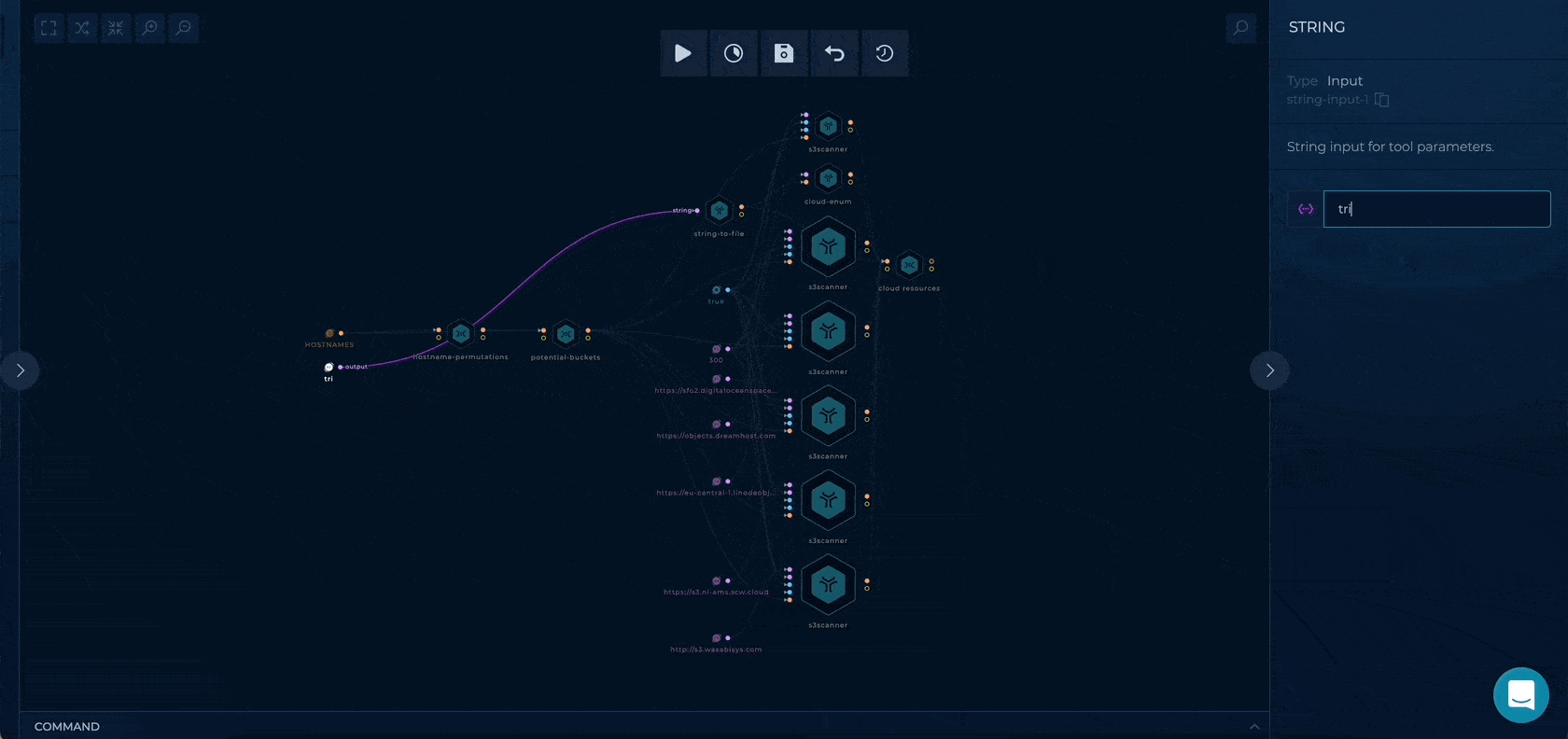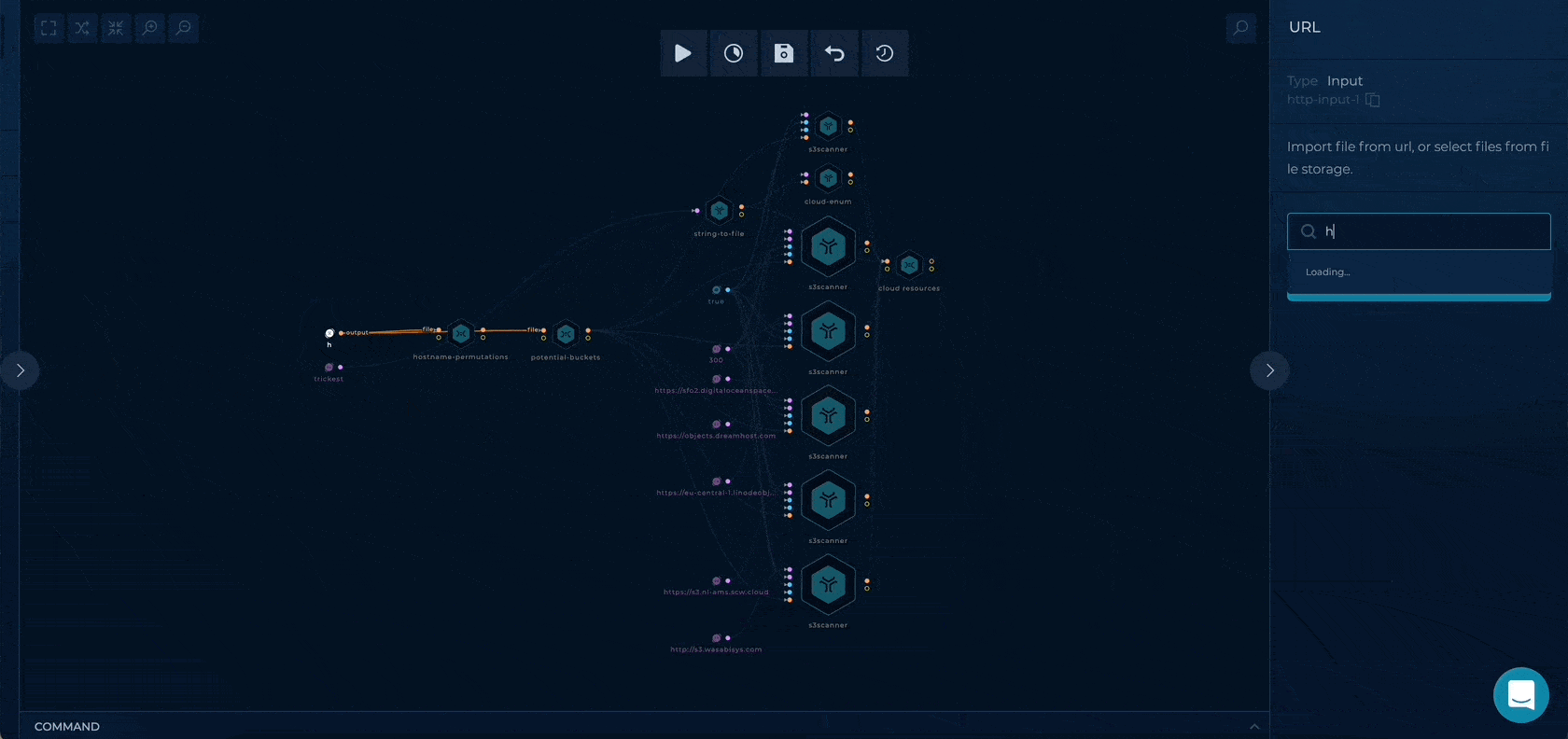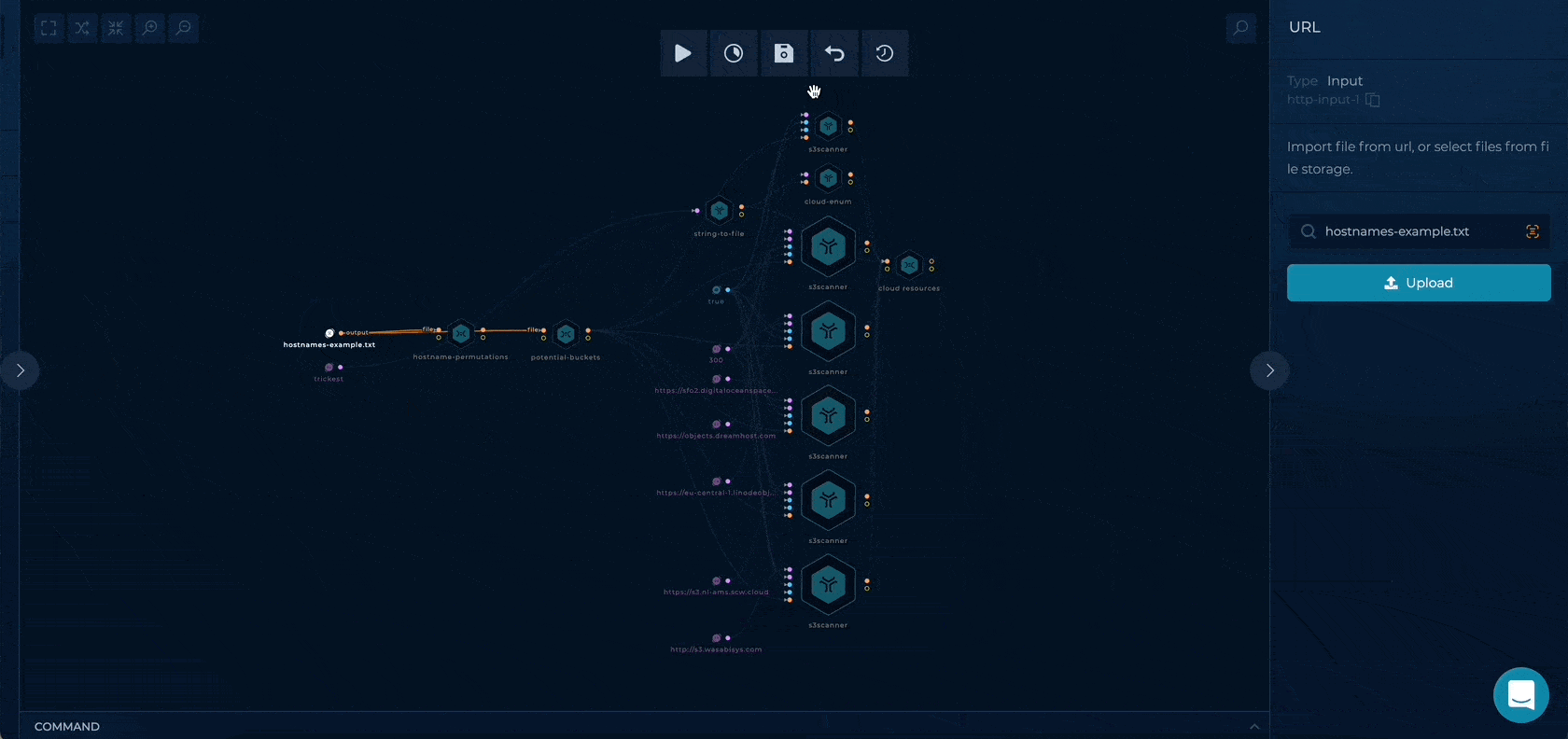
Workflow Targets Setup
Build this workflo in steps
Visit our blog for a more thorough explanation of how to build this workflow:
Execution and results
After setup workflow is ready to be executed. Once workflow's last node, cloud-resouces script, is finished result can be viewed and downloaded.
cloud-resouces script will have a list of files representing the found buckets from different cloud providers.
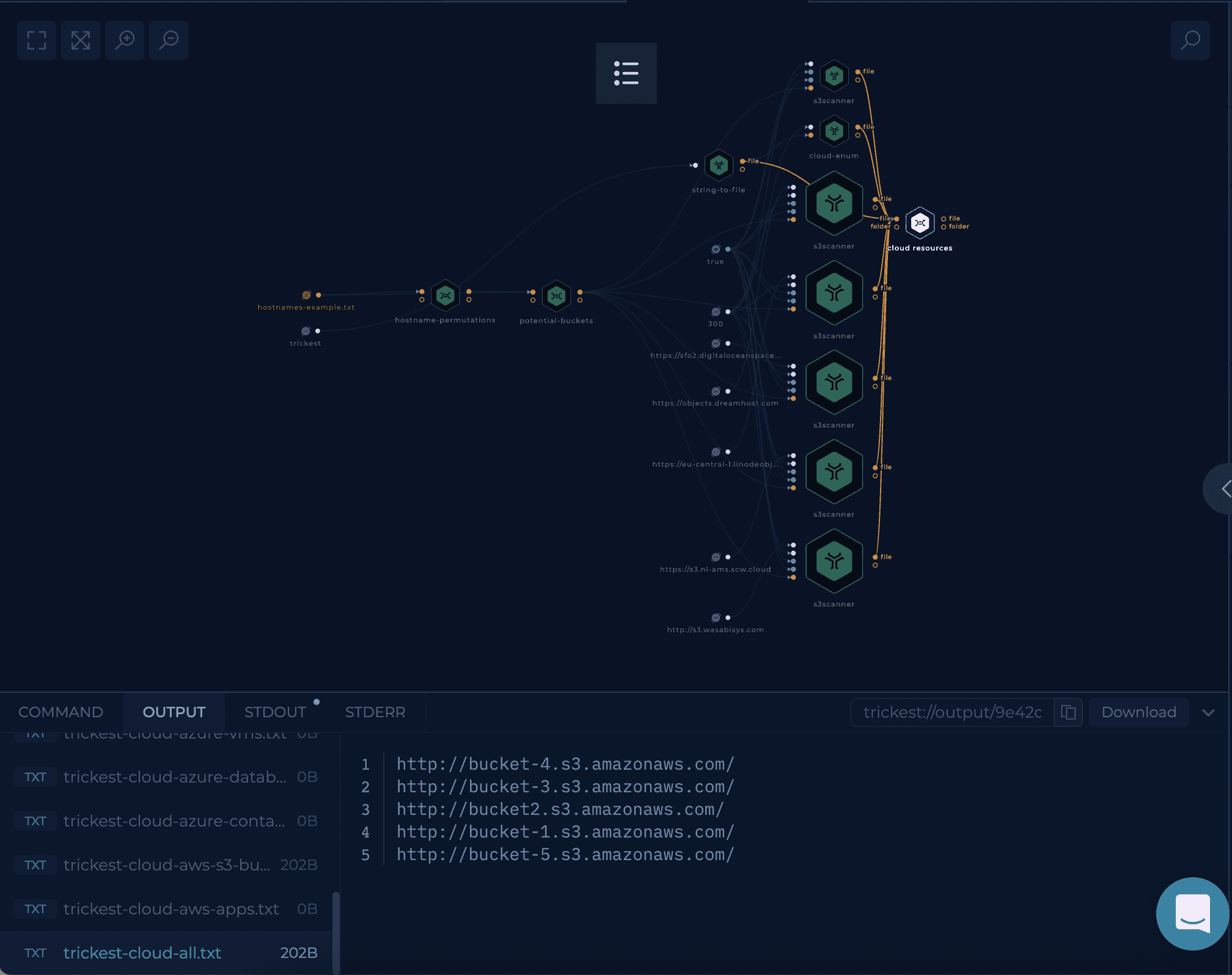
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Changing machine type of tools to speed up the execution
- Add more cloud bucket checks
- Verify the access denied for all found buckets by providing the API keys from different cloud providers
- Implement a mechanism to merge all of the previous results through scheduling and get-trickest-output