Custom subdomain brute-force wordlist from IP ranges
SSL certificates obtained from various hosts may contain valuable information that could be utilized to create a wordlist and then find additional hostnames belonging to a specific company's root domain
Complexity: basic
Category: Attack Surface Management
Workflow
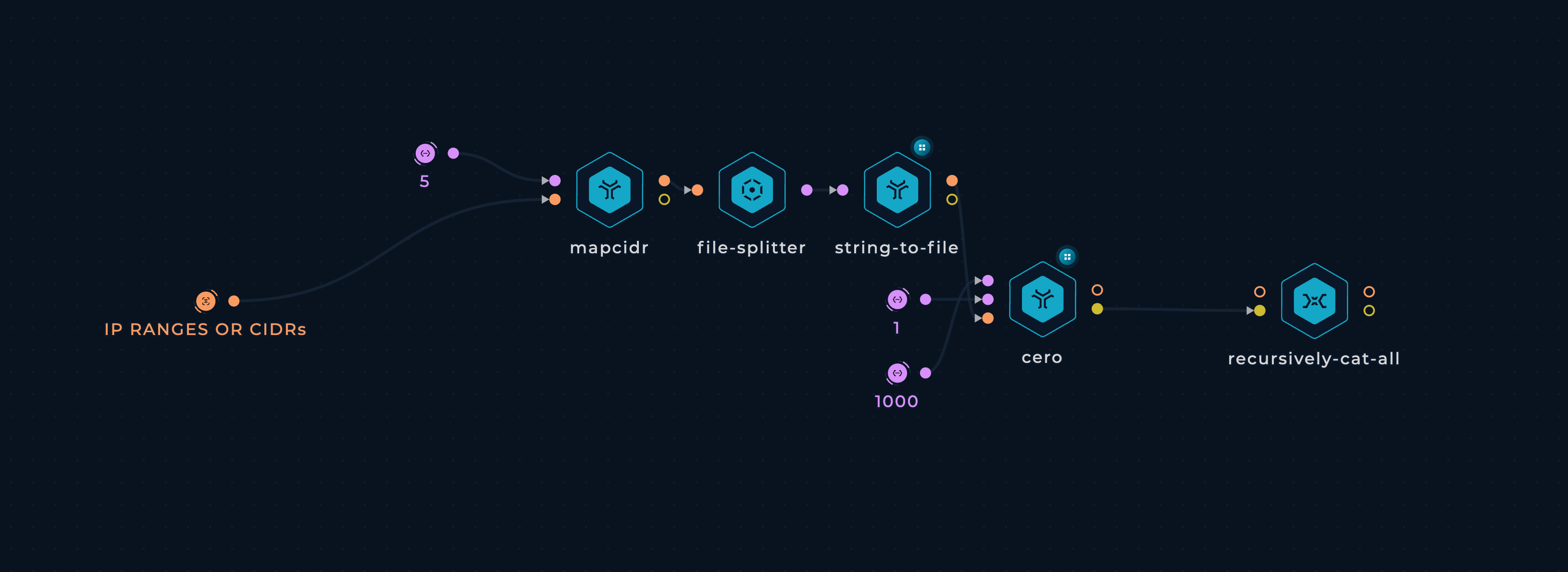
Custom subdomain brute-force wordlist from IP ranges
Tools
Setup
You can set up this workflow by changing following input value:
- TARGET - provide file containing company's CIDR or IP-range, as a target
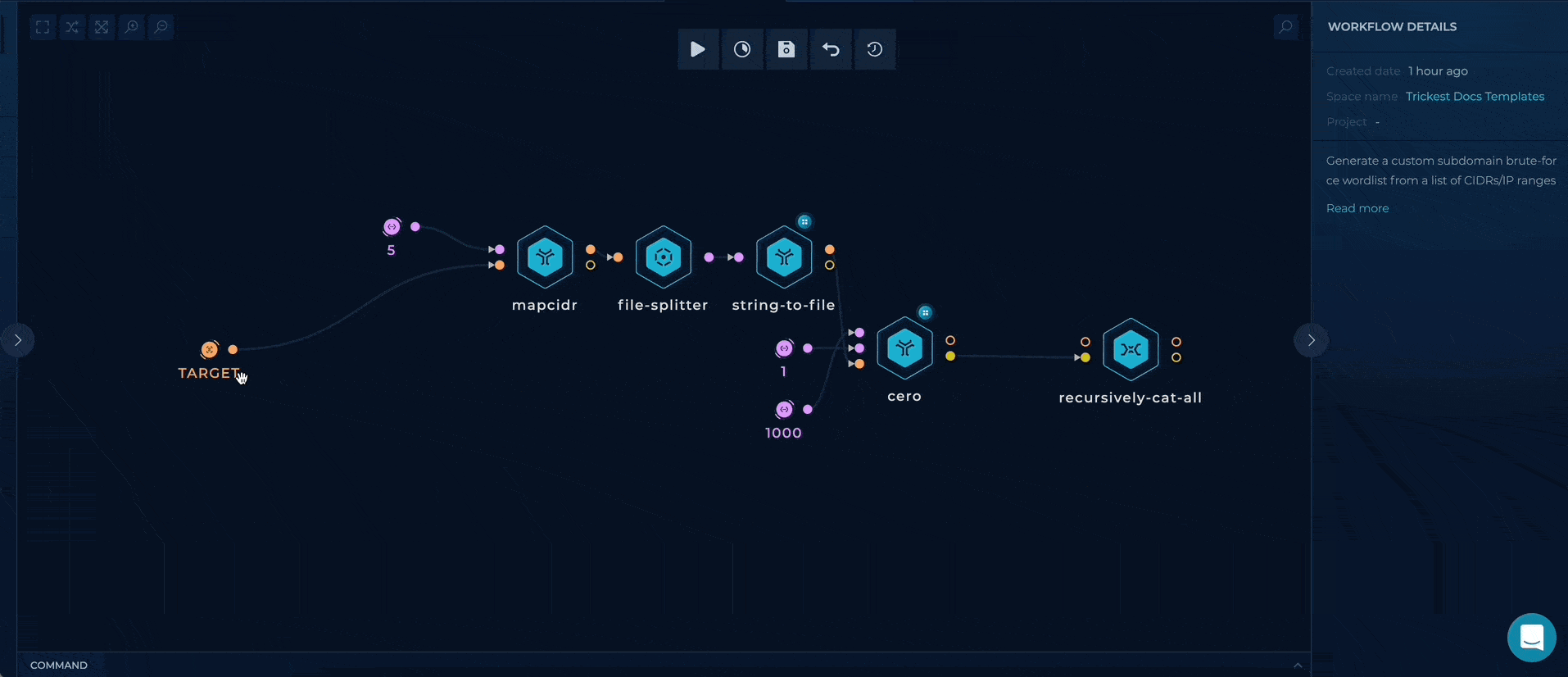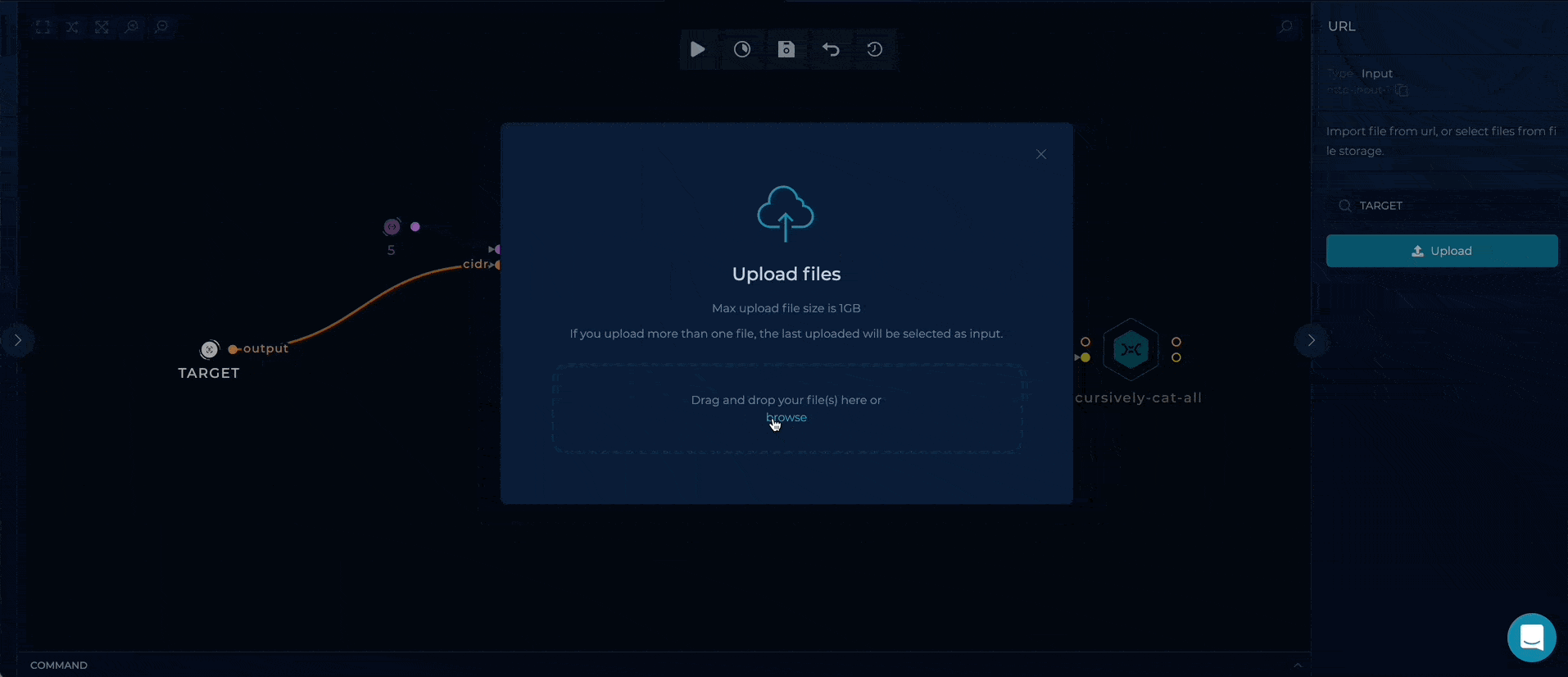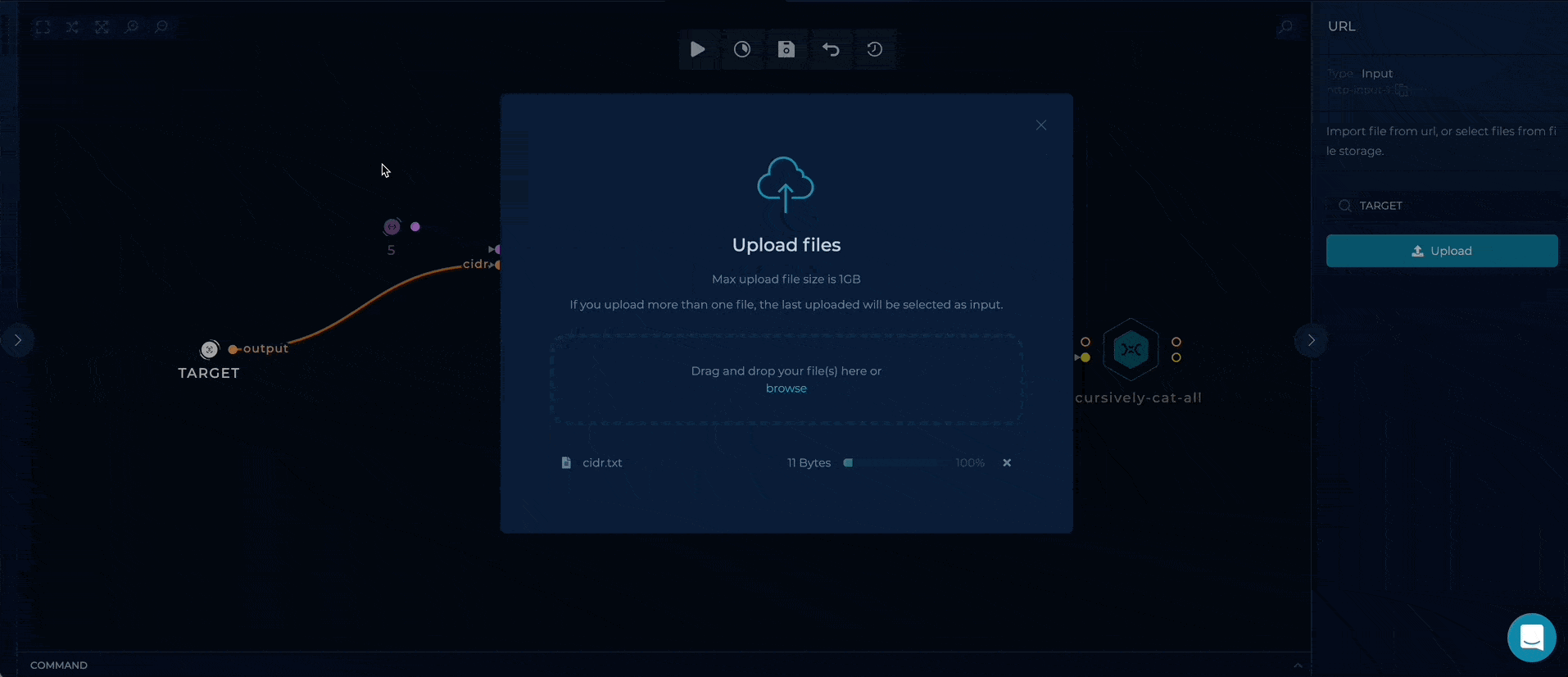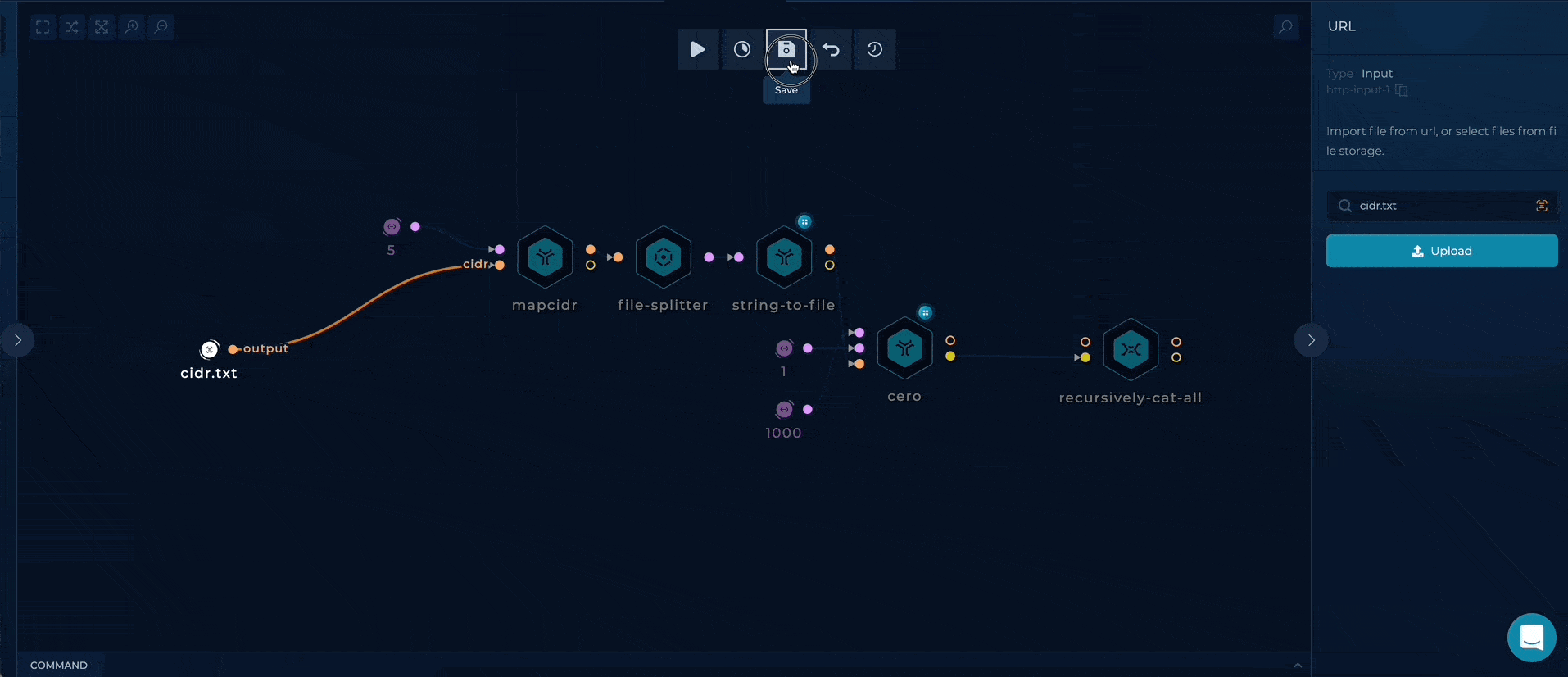
Workflow Targets Setup
Execution and results
After setup workflow is ready to be executed. Once workflow's last node, recursively-cat-all script, is finished result can be viewed and downloaded.
recursively-cat-all script will contain the wordlists gathered from cero parallel execution for each cidr-list.
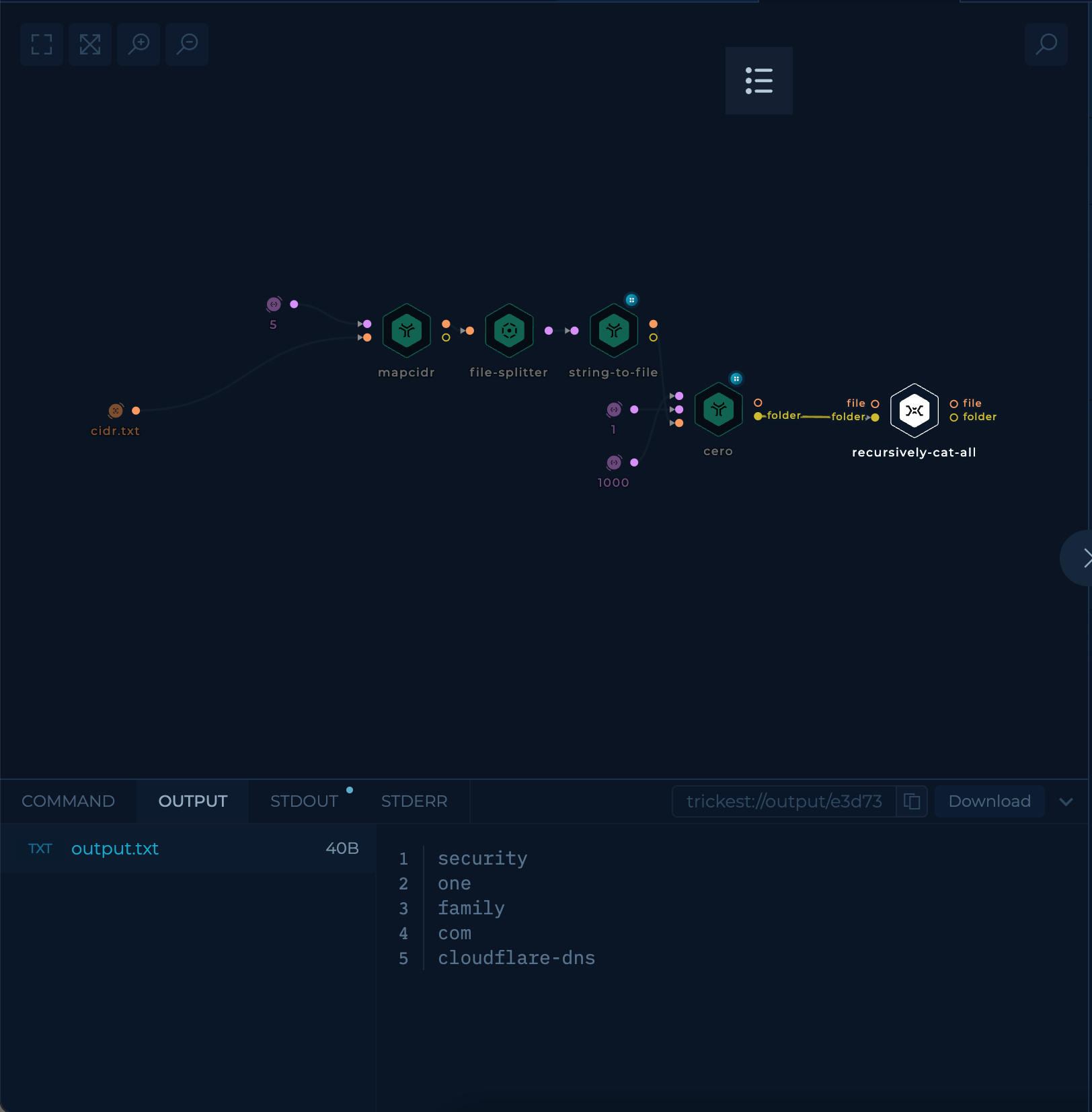
Try it out!
This workflow is available in the Library, you can copy it and execute it immediately!
Improve this workflow
- Changing machine type of tools to speed up the execution
- Change input to ASNs and use get-asn-prefixes to get all of the prefixes used in mapcidr
- Implement a mechanism to merge all of the previous results through scheduling and get-trickest-output