tlsx
tlsx in the Trickest library - GitHub repo
Basic Usage Examples
Making A TLS Connection to an IP Address
Pass an IP address (e.g. 52.59.15.118) to the host string input.
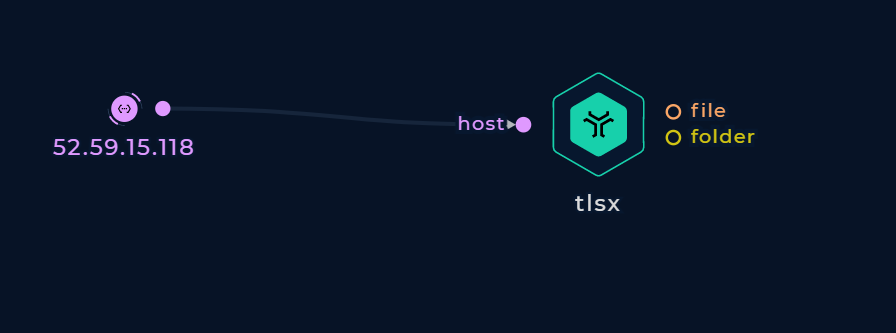
Connect to an IP address
Enumerating `Common Names` from a TLS Certificate
Turn on the common-names boolean input.
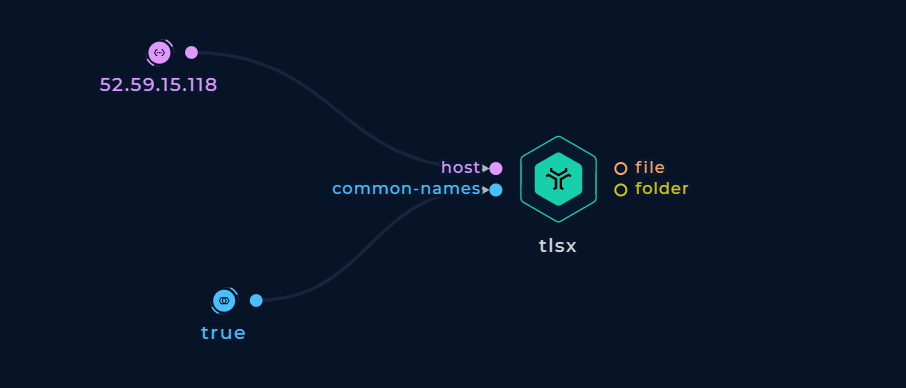
Enumerate Common Names
Enumerating `Subject Alternative Names` From a TLS Certificate
Turn on the subject-alternative-names boolean input.

Enumerate Subject Alternative Names
Enumerating Hostnames from a List of Hosts
You can combine the 2 techniques above to enumerate possible hostnames from a target's TLS certificates and expand the attack surface.
Pass a list of IP addresses and/or hostnames to the list file input value and turn on the common-names and subject-alternative-names boolean inputs.
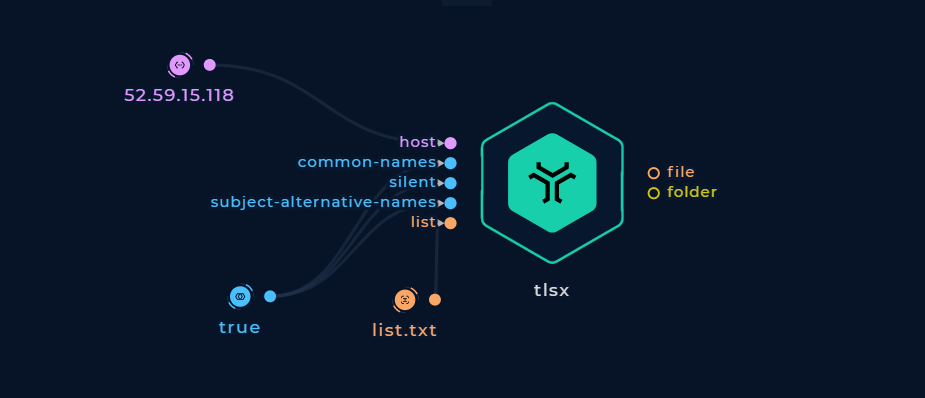
Enumerate hostnames from a list of hosts
Enumerating Hostnames from an IP range
Pass an IP range in CIDR notation to the host string input and turn on the common-names and subject-alternative-names boolean inputs.
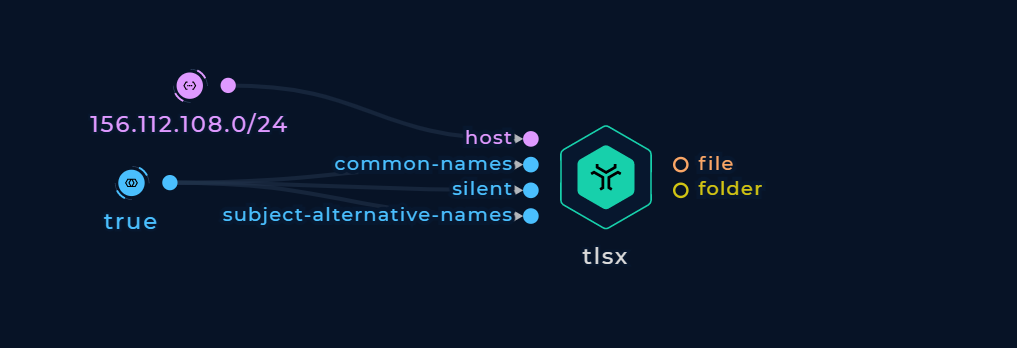
Enumerate hostnames from an IP range
Scanning for TLS Misconfigurations
Pass your input host or list and turn on the expired, mismatched revoked, and self-signed boolean inputs.
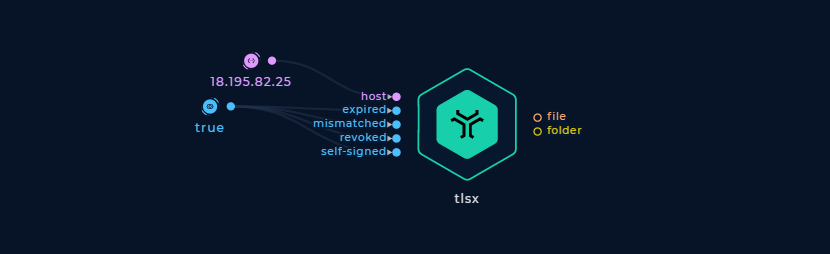
Scan for TLS Misconfigurations
Scanning Specific Ports
Port 443 is used by default but you can change it or add more ports using the port string input (comma-separated)
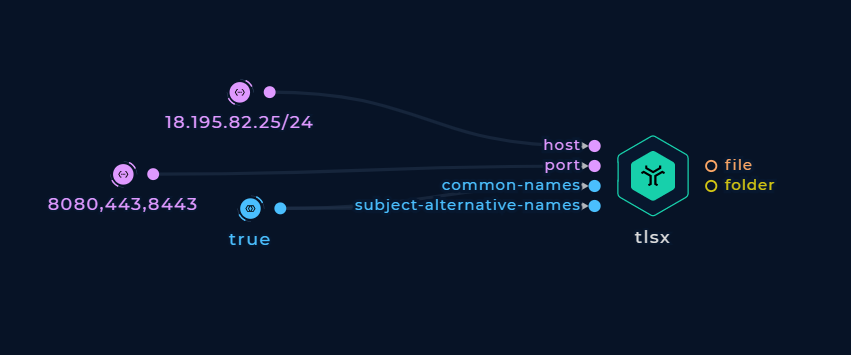
Scan specific ports
Filtering/parsing Results
JSON Output
To write the output in JSON format, turn on the json boolean input.
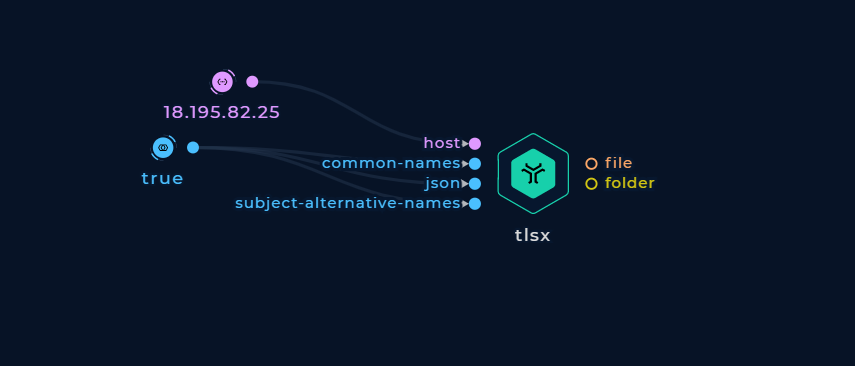
JSON output
Extract Only The Hostnames
Turn on the resp-only boolean flag to display the TLS response only without the input.
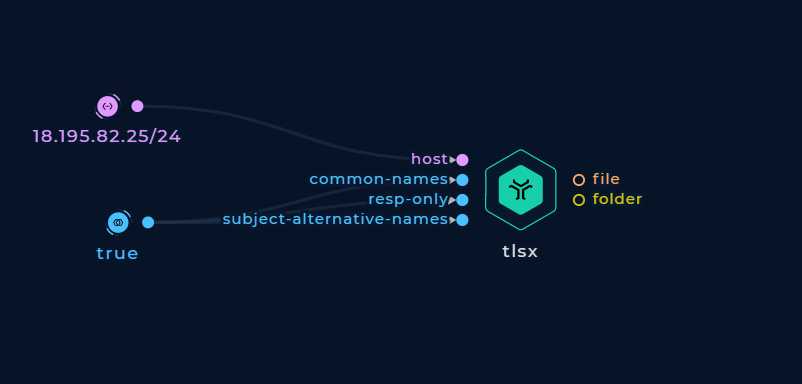
Response only
Performance Improvements
Increase / Decrease the Number of Concurrent Threads
The default number of concurrent threads is 300, but you have the option to modify this using the concurrency string input. Adjusting this input can either speed up the execution or decrease the aggressiveness of the scan.
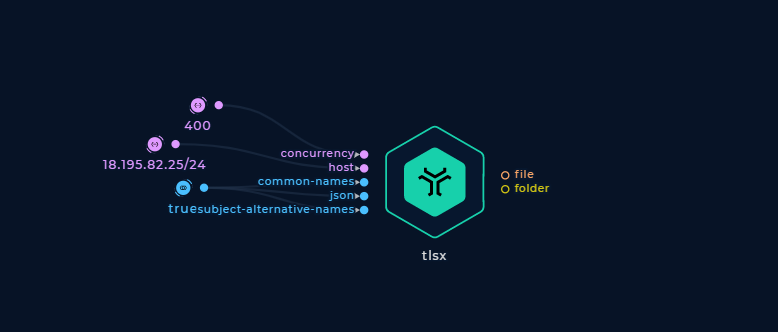
Change the number of concurrent threads
Adjusting the Delay
Use the delay string input to set a specific duration to wait between each connection per thread (number + time unit, e.g. 200ms, 1s, etc)
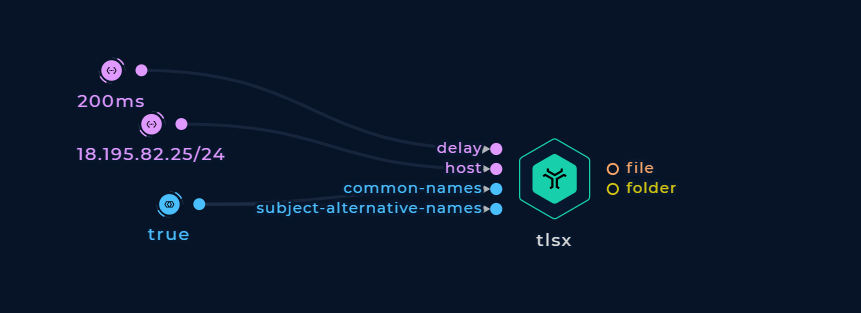
Adjust the delay
Adjusting the Timeout
The default TLS connection timeout is 5 seconds. Enter the number of seconds into the timeout string input to adjust it.
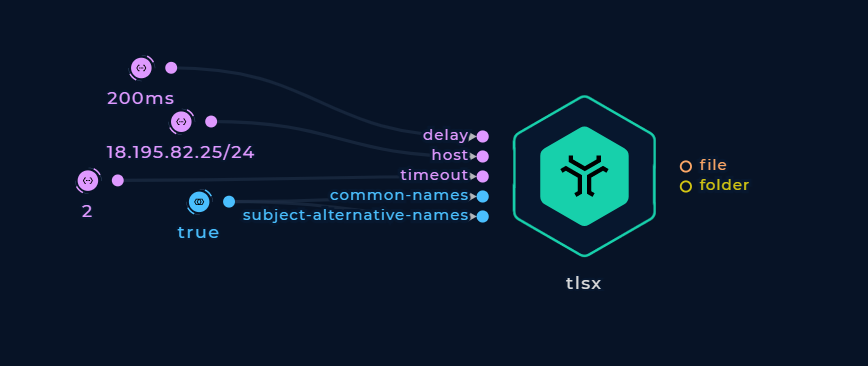
Adjust the timeout