CVE-2023-3519: Citrix ADC and NetScaler Gateway Detection Workflow At Scale
CitrixVulnerabilityExploitCVE-2023-3519On this page
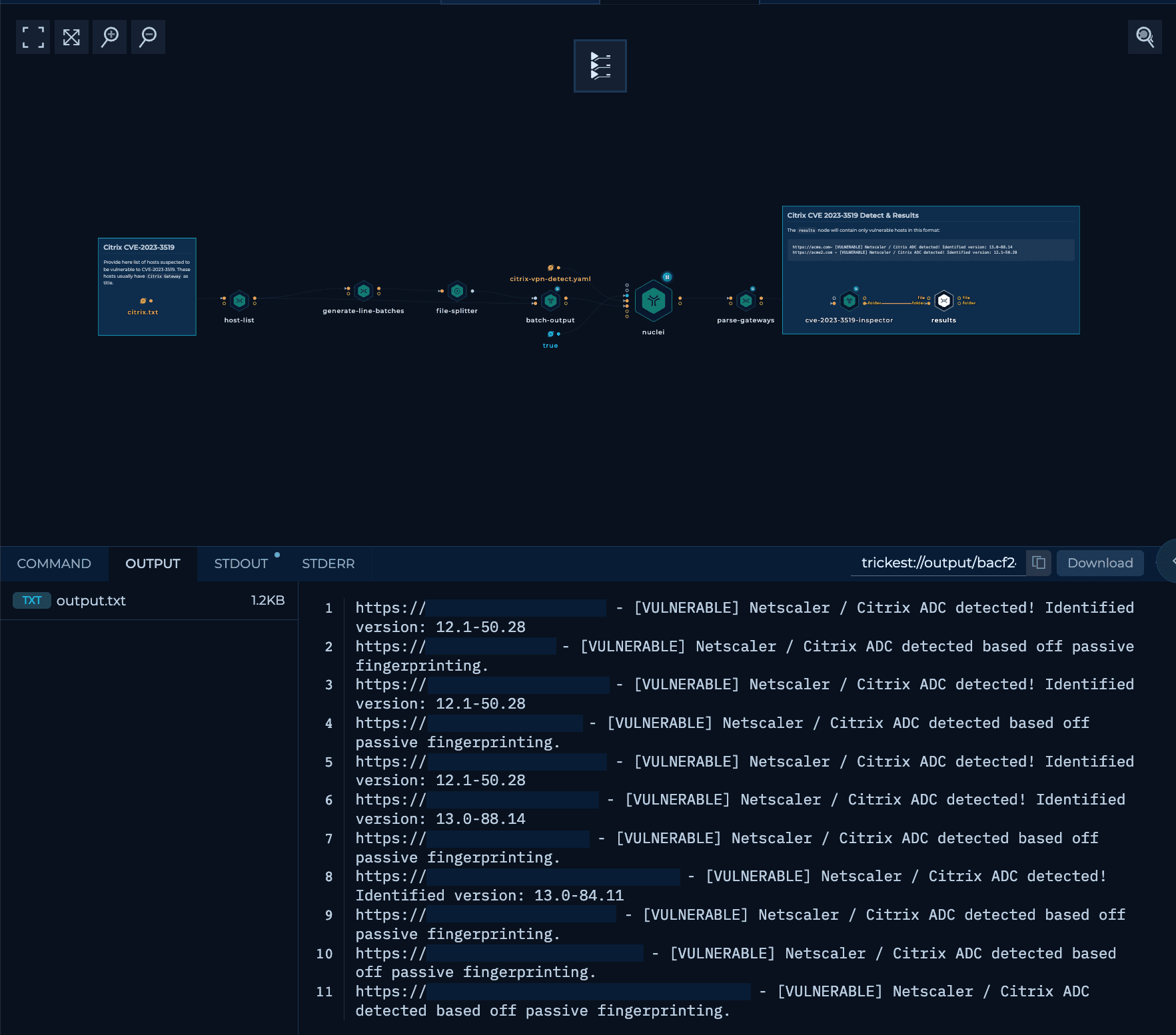
Get Started with WorfklowsThe recently disclosed CVE-2023-3519 vulnerability in Citrix ADC and NetScaler Gateway presents a critical threat to organizations using these products. This remote code execution bug allows attackers to take full control of the gateway appliance if successfully exploited.
To help enterprises quickly check their software versions, we have built a workflow that detects the hostnames provided at the beginning, indicating where security teams should look first.
The Workflow
Input
The input for the workflow consists of a list of hosts. These hosts can be subdomains or IP addresses.

Citrix Detection
We should check firstly if the hostnames provided actually host Citrix Gateway. Spraying the detection across many hosts would overwhelm the networks without need. For this, we are using nuclei with citrix-vpn-detect.yaml template.
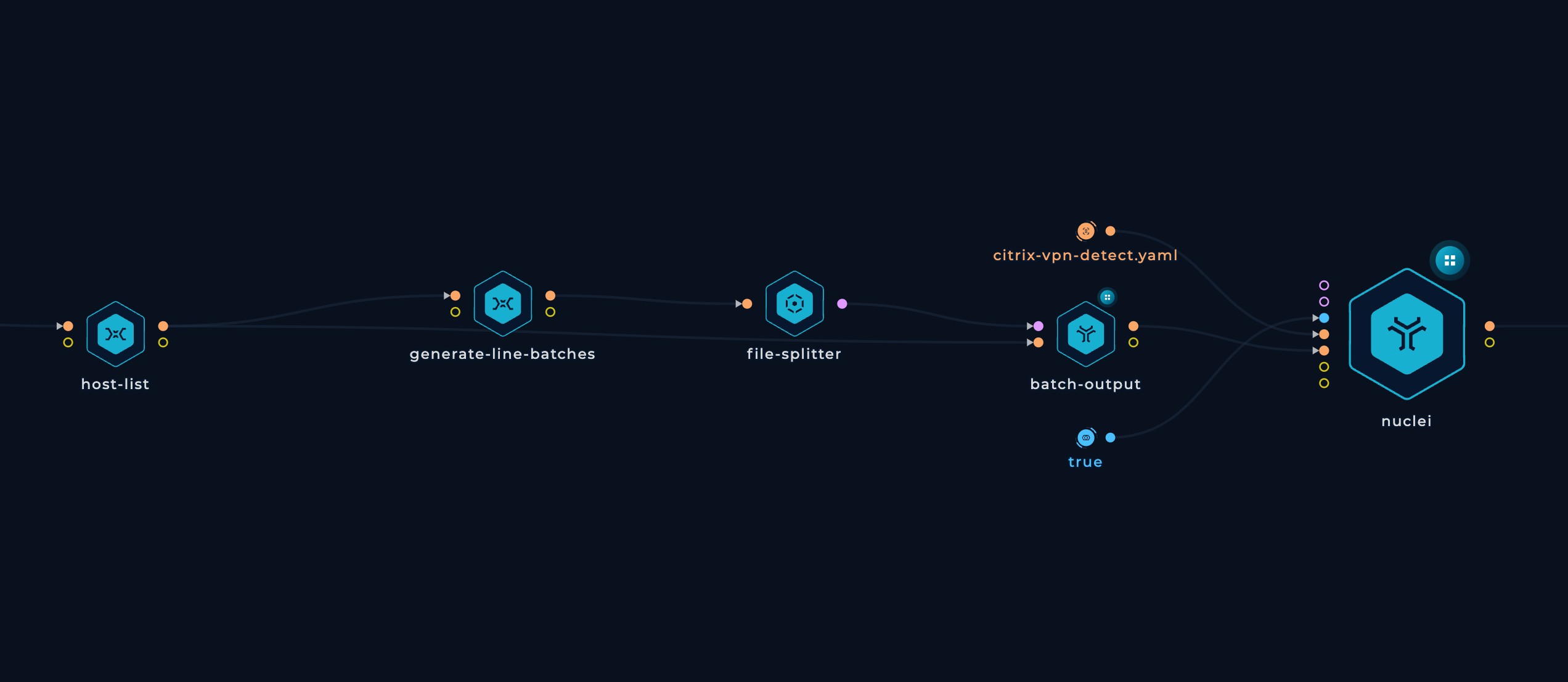
nuclei -no-color -stats -templates in/http-input-1/citrix-vpn-detect.yaml -list in/batch-output-1/output.txt -output out/nuclei-1/item/output.txt
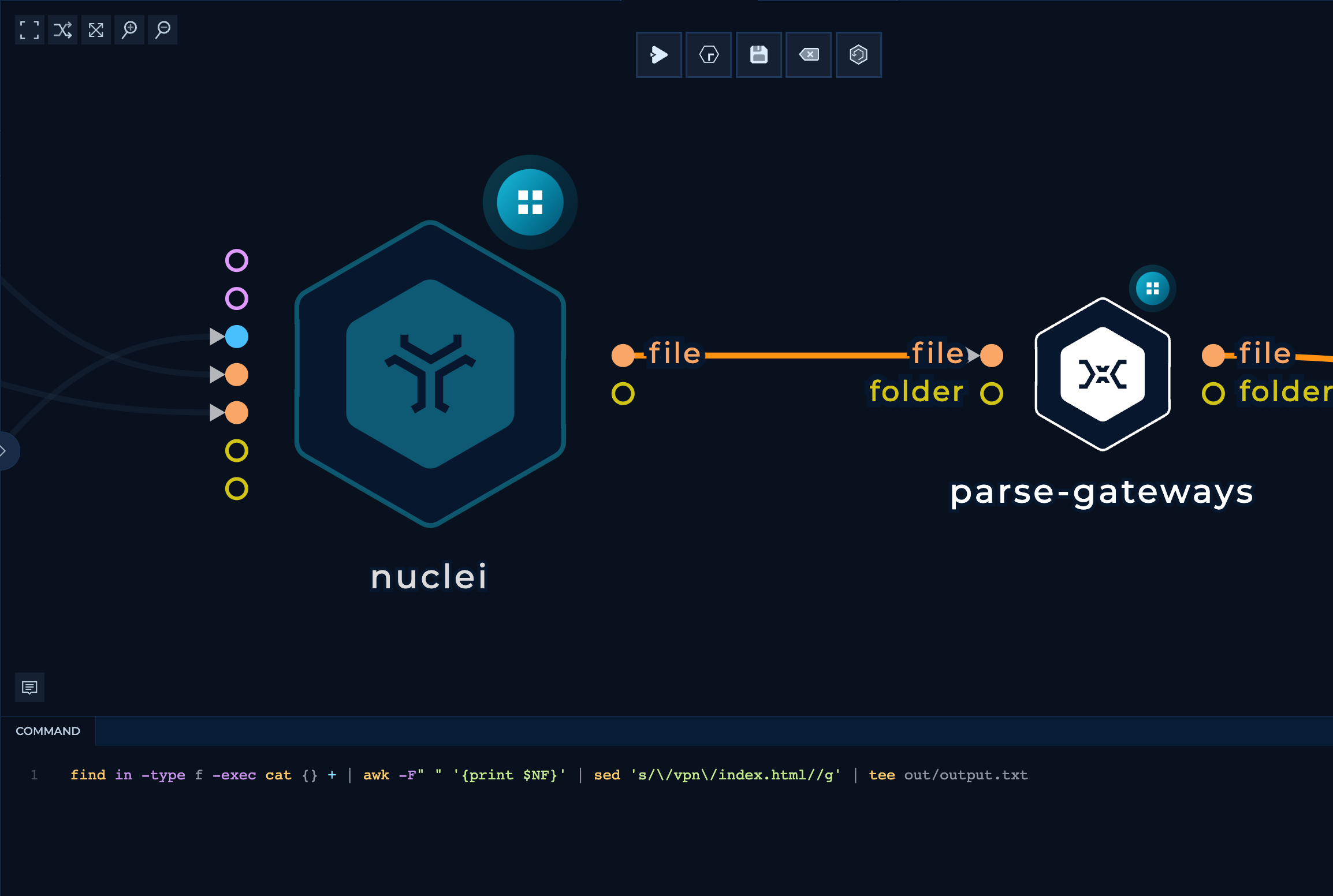
Parsing the Gateways
After getting the nuclei output, the bash script will parse all of the detected Citrix Gateways and delete all unecesarrly URL strings. Simply, it will just delete vpn/index.html at the end of each URL.
Nuclei output...
[citrix-vpn-detect] [http] [info] https://acme1.com/vpn/index.html
[citrix-vpn-detect] [http] [info] https://acme2.com/vpn/index.html
... will become list of web servers again
https://acme1.com
https://acme2.com
CVE-2023-3519 Inspector
After we've verified the Citrix Gateway servers, we are using an citrixInspector build by securekomodo that is detecting the versions of Gateway and printing out if they potentially vulnerable. The input to the script are parsed Gateways from previous step.

Finally, another bash script will grep for VULNERABLE hosts.

Conclusion
Given the critical nature of the CVE-2023-3519 vulnerability in Citrix ADC and NetScaler Gateway, rapid detection and remediation are of paramount importance. The workflow we've presented provides a fast, reliable method for organizations to identify potentially vulnerable systems.
Although this workflow is just used to detect potentially vulnerable versions of Citrix Gateway, we will keep an eye of the exploits and improve this workflow to provide our users with deeper analysis and detection.
This workflow has just been published in the Trickest Library of free pre-built workflows! Sign up for free to try this workflow and test your infrastructure to CVE-2023-3519.
GET STARTED WITH TRICKEST TODAY
Complete our registration to elevate and automate your offensive security endeavors.
Get started