Completely Transparent Attack Surface Management: Introducing Inventory 3.0 Workflow
CybersecurityAttack Surface ManagementBug BountyOn this page
Get Started with WorfklowsIn the world of bug bounty hunting and enterprise security, understanding and managing your attack surface can be the difference between finding a bug or missing it entirely. Keeping a constant eye on your assets ensures that no security vulnerabilities slip through the cracks. This is where Inventory 3.0 takes center stage. It's a straightforward, effective workflow > dataset for your bug hunting and red team arsenal, designed to simplify and enhance your approach to public bug bounty programs and your enterprise exposure.
Attack Surface Management available to everyone
The Inventory 3.0 workflow is designed to monitor over 800 companies for new assets and streamline the asset management of public bug bounty programs. Its primary purpose is to aid bug bounty hunters in getting up to speed with new programs while offering security teams enhanced visibility into their assets. By reducing the noise and load that automated tools often generate, this project aims to provide a holistic, efficient, and comprehensive approach to attack surface management.
The main parts of this dataset are the DNS Records and Web Servers of particular companies.
How it Works?
It consists of two primary workflows: Inventory 3.0 - Targets, and Inventory 3.0. These workflows are designed to offer an organized view of bug bounty program data and facilitate its efficient management. Let's dive deeper to better understand their unique components.
Inventory 3.0 - Targets
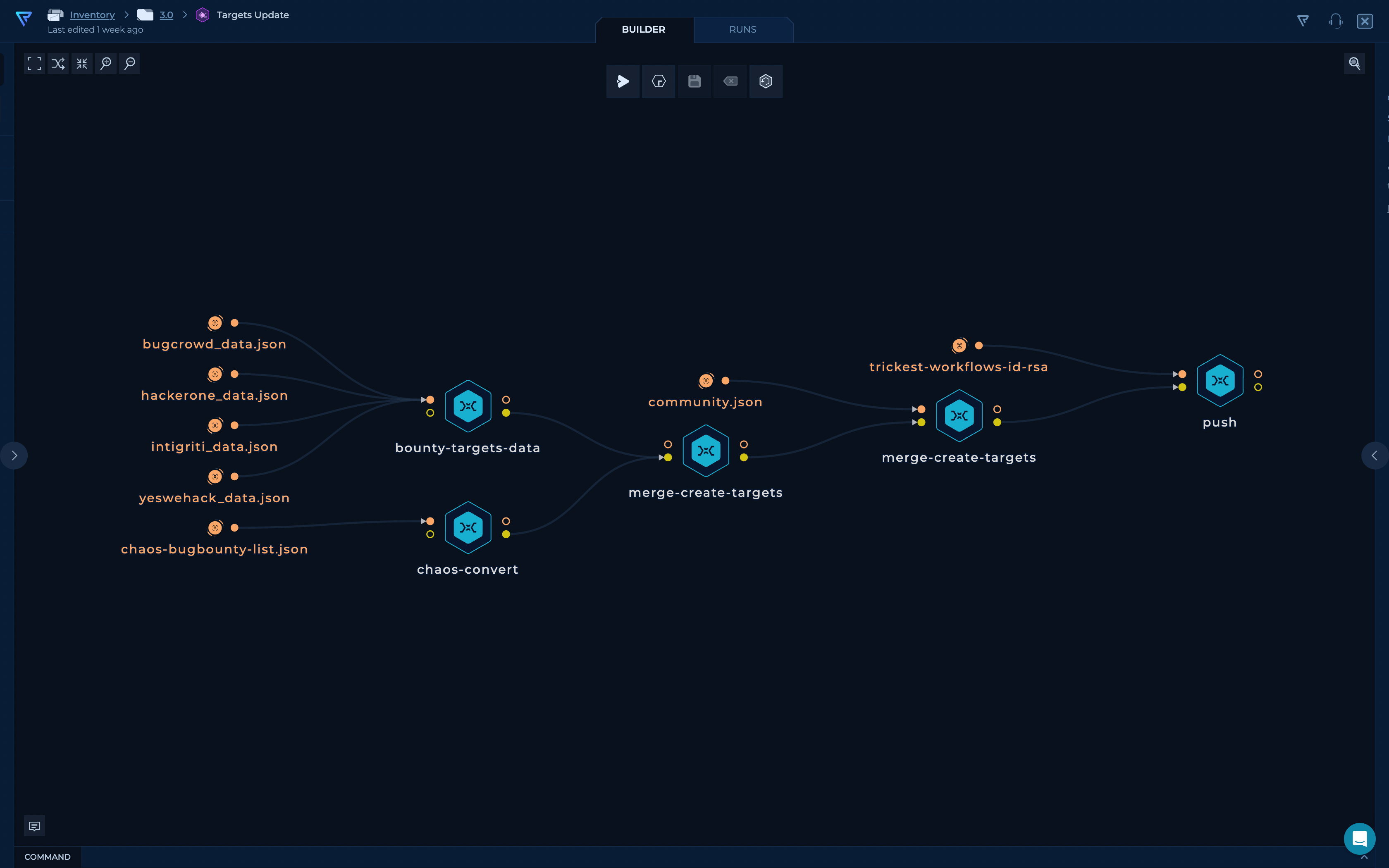
The first part of the workflow streamlines the collection and organization of bug bounty program data from multiple sources.
- Data Collection: The workflow begins by fetching data from two key sources: Bounty Targets Data Chaos Public Bug Bounty Programs. These repositories are treasure troves of bug bounty program information.
- Data Transformation: The collected data is then transformed using
pythonscripts. This ensures that the data is formatted consistently, facilitating easier analysis. - Program Merging: To avoid duplication, programs with identical URLs are merged, presenting a unified view of each bug bounty program and eliminating redundancy.
- Community Program Inclusion: Programs from the
community.jsonfile are incorporated into the workflow, enhancing the diversity and coverage of the dataset. - Final Output: The workflow culminates in the creation of a consolidated JSON file,
targets.json, containing all the merged bug bounty program data. This serves as a centralized resource for bug bounty researchers.
Inventory 3.0

Inventory 3.0 consists of several stages, each building on the data gathered from the previous stage, ultimately creating a thorough inventory of your target domains and subdomains.
1. Gathering the Targets
The first step in the workflow starts with identifying the domains that need to be tracked. These domains get extracted from a JSON file, named targets.json. The file contains the list of all companies with their respective domains that will be analyzed.

2. Full Distribution
The file-splitter node you saw in previous section is really important. That is the node that is being propagated to all of the tools in the workflow making it completely distributed and paralelized. This approach helps us to push the results to repository as soon as they are finished, and other machines picking up all of the jobs as they come.
This is also why we call our platform hyperscalable. More machines = faster execution.
2. Passive Enumeration
Following the identification of targets and domains, the workflow goes to passive enumeration. Data is gathered from a multitude of sources, which provide a wide range of potential subdomains. The tools employed in this process include the following:

3. Active Enumeration
In the next step, the passive enumeration data is used to create a new brute-force wordlist. And it consists in two parts:
- Active Enumeration: Using mksub to generate potential subdomains for root domain.

- Environments: Dsieve discovers environments per subdomain level. It also generates potential subdomains with mksub and the custom wordlist, along with an additional wordlist - level2.txt.

4. Permutations
The results of the active and passive enumeration are merged, and the workflow extracts environments per subdomain level. It uses alterx to generate permutations and resolve these with puredns.

5. Collecting Previous Results
In this step, the workflow utilizes a Python script to fetch all of the previous hostnames.txt. It then uses anew to extract the new hostnames found and zip active, passive, and permutation results per program for repository storage.

6. Reporting
In the last part of the workflow, the workflow uses dnsx to resolve the found hostnames and a python script to generate a dns-report.csv. The newly found domains are marked with [x]. It also uses httpx to gather information on web servers and generate a server-report.csv. These reports are then finally pushed to the repository.

Join us in the Inventory Project
We welcome contributions from the community, as in all our projects. Whether you have ideas, suggestions, or wish to add/edit a target/workflow, we encourage you to participate. You can help by sending a PR with new targets through the community.json file, tweeting at @trick3st, or joining the conversation on our Discord channel.
Customize your Workflows with Trickest
Inventory 3.0 is more than just a resource; it's a dynamic and evolving workflow for better attack surface management. With its emphasis on comprehensive monitoring and efficient handling of bug bounty programs, it represents a significant step forward in cybersecurity. By facilitating an in-depth understanding of your assets and providing actionable insights, this project is a must-have for any security team looking to bolster their cybersecurity defense.
At Trickest, we believe in the power of innovation and customization. We encourage you to sign up for free on Trickest and customize this workflow to your use case. Explore more pre-built workflows from the rich Library, or better yet, create your own from scratch!
Cybersecurity is not just about responding to threats—it's about proactive monitoring, understanding your attack surface, and taking steps to secure your assets before others can exploit them. This workflow with in-depth monitoring and wide-ranging insights, is the perfect tool to help you do just that. Whether you're a bug bounty hunter, a member of a security team, or just interested in cybersecurity, we offer tools, insights, and resources to help you step up your cybersecurity game.
This project stands as a testament to the power of community-driven development in cybersecurity. Its mission to streamline public bug bounty programs and improve attack surface management represents a forward-thinking approach to cybersecurity and one that will hopefully inspire similar initiatives in the future.
GET STARTED WITH TRICKEST TODAY
Complete our registration to elevate and automate your offensive security endeavors.
Get started