
Discovering Adobe Experience Manager (AEM) Vulnerabilities at Scale
aem vulnerabilitiesaem securityautomationOn this page
Get Started with WorfklowsAEM Security potential with Trickest
In the world of web security and bug bounty hunting, Adobe Experience Manager is a goldmine for vulnerabilities. This post highlights the importance of finding these vulnerabilities with Trickest as a framework for automation. Here's a quick breakdown:
-
Discovering Vulnerability Goldmine: AEM has many vulnerabilities, which makes it an attractive target for ethical hackers.
-
Automation and Scaling with Trickest: With Trickest, the task of pinpointing AEM vulnerabilities becomes an automated and expansive endeavor.
-
System Security Enhancements: Companies can enhance their system security by proactively identifying and patching vulnerabilities using AEM.
-
Benefits for your Bug Hunting: Bug bounty programs offer higher rewards for ethical hackers who discover more bugs.
Dive into learning about vulnerabilities in Adobe Experience Manager (AEM) and how Trickest can supercharge your offensive security measures.
In this blog post, we aim to identify vulnerabilities in AEM deployments across the web for bug bounty reporting, research, and security of companies.
The Scope
We direct our scanning efforts towards entities deploying Adobe Experience Manager (AEM). This robust CMS powers countless websites, intranets, and immersive digital platforms. Yet, its intricate nature can lead to vulnerabilities, many of which are detectable using simple nuclei templates.
Scanning focus is:
-
Adobe Experience Manager (AEM) Instances: We scan the internet for publicly accessible AEM instances, identifying their versions and configurations.
-
Integration with Shodan API: To enhance our scanning capabilities, we integrate the Shodan API into our workflow. This integration allows us to gather valuable intelligence about AEM instances and their exposure to the internet.
Guiding Principles
When scanning Adobe Experience Manager, we follow these primary principles:
-
Vulnerability Discovery: Our goal is to detect specific vulnerabilities in AEM instances and configurations. This includes identifying potential entry points for cyber threats, misconfigurations, and known security issues.
-
Insights from Shodan: By integrating the Shodan API, we get a wealth of data about AEM instances online exposure and potential security gaps, enhancing our scanning precision.
-
Ethical Disclosure: We follow ethical practices by partnering with organizations that host vulnerable AEM instances. We collaborate responsibly to address and resolve identified security issues.
Let's explore how Trickest, using Shodan API and Nuclei, can scan and assess Adobe Experience Manager instances at scale and assure the organization's AEM security.
Overview of the Workflow

Our approach to discovering vulnerabilities in Adobe Experience Manager (AEM) deployments is guided by a carefully designed workflow. This workflow utilizes expert technologies and open-source tools and connects them to scan and assess AEM instances on a large scale. Take a peek inside our workflow building:
-
Defining the Scope: The journey starts with clearly defining the scope of our scanning operation which includes specifying the target application and title of the web pages we will search for to make sure we are scanning AEM.
-
Shodan Integration: Our secret weapon here is the Shodan API. Shodan, often referred to as the "search engine for IoT," provides a wealth of information about internet-connected devices and services. By integrating Shodan, we gain insights into AEM instances' exposure and potential vulnerabilities.
-
Mass Scanning with Shodan: Leveraging the Shodan API, we initiate a mass scan at the beginning of our Trickest workflow across the internet to identify AEM instances that match our predefined criteria. This scan helps us compile a comprehensive list of potential targets. We do this by using the shodan dork "http.title:"AEM Sign In""
-
Customized Vulnerability Checks with Nuclei: Armed with a list of AEM instances, we add custom vulnerability checks from Nuclei, a security testing tool tailored to AEM-specific security issues. On top of vulnerability checks we employ additional nuclei scan to discover SSL data on each IP that contains a vulnerability.
-
Merging the IPs, Hostnames and Vulnerabilities: After the AEM and SSL scans, we use a simple
pythonscript to merge the data by using outputs of both nuclei scans.
By utilizing python, we are going to merge the IP, Hostname and Vulnerability data into one file.
import json
with open('in/nuclei-2/output.txt') as f:
hosts = [json.loads(line) for line in f]
with open('in/nuclei-1/output.txt') as f:
vulnerabilities = [json.loads(line) for line in f]
results = []
for host in hosts:
host_ip = host["ip"]
matched_vulns = []
for vuln in vulnerabilities:
if vuln["ip"] == host_ip:
matched_vulns.append({
"name": vuln["info"]["name"],
"matched_at": vuln["matched-at"],
"request": vuln["request"],
"ip": vuln["ip"],
"curl-command": vuln["curl-command"]
})
if matched_vulns:
results.append({
"host": host_ip,
"ssl": host["extracted-results"],
"vulnerabilities": matched_vulns
})
with open('out/output.txt', 'w') as f:
json.dump(results, f, indent=4)
The output of this script looks like this:
[
{
"host": "REDACTED",
"ssl": [
"www.offers.redacted.com",
"www.unlimited.redacted.com",
"redacted.com",
"www.redacted.redacted.com",
"*.redacted.com",
],
"vulnerabilities": [
{
"name": "Adobe AEM Default Login",
"matched_at": "https://REDACTED/libs/granite/core/content/login.html/j_security_check",
},
{
"name": "Adobe Experience Manager Felix Console - Default Login",
"matched_at": "https://REDACTED/system/console/bundles",
}
]
}
]
-
Assessing Risks: Every discovered vulnerability is carefully assessed for its impact and potential risk. We prioritize vulnerabilities based on their severity, potential for exploitation, and the sensitivity of the affected systems.
-
Reporting and Responsible Disclosure: Our responsible disclosure process involves notifying organizations hosting vulnerable AEM instances and providing them with details and remediation guidance.
Tools and Technologies
The workflow is powered by an arsenal of tools and technologies, including:
-
Shodan API: It's the cornerstone of our scans, as it offers real-time data on internet-exposed devices and services.
-
Vulnerability Scanners We use Nuclei templates to match AEM-specific vulnerabilities.
-
Automation: It's the key to scalability. The workflow uses scripts and open-source tools, making building, customization, and running super easy!
-
Reporting and Collaboration Tools: To ensure responsible disclosure and collaboration with organizations, we utilize secure communication channels and reporting platforms such as HackerOne, Bugcrowd, and Intigriti.
Discoveries
Our scanning journey through the digital landscape focused on Adobe Experience Manager (AEM) deployments has provided a lot of valuable insights. Here are some of the notable discoveries and vulnerabilities:
-
Critical Security Patches Missing: Surprisingly, a significant number of AEM instances were found to be running without critical security patches. This exposes organizations to well-known vulnerabilities that could be exploited by malicious actors.
-
Misconfigured Access Controls: Access controls are a fundamental aspect of AEM security. Yet, we discovered instances with misconfigured access controls, potentially granting unauthorized users access to sensitive content and functionality.
-
Exposed Debugging Endpoints: In some cases, debugging endpoints were left exposed, providing a potential entry point for attackers to gather information about the AEM environment or execute arbitrary code.
-
Outdated AEM Versions: The workflow identified Outdated AEM versions, often missing important security updates and bug fixes. Those instances are at a higher risk of exploitation.
Impact Assessment
The vulnerabilities we uncovered within AEM deployments can have wide-ranging impacts on organizations:
-
Data Breach: Misconfigured access controls and missing security patches can lead to data breaches, compromising sensitive information.
-
Business Disruption: Exploitable vulnerabilities can disrupt business operations, leading to downtime and financial losses.
-
Reputation Damage: A security breach can tarnish an organization's reputation, eroding trust among customers and partners.
Bug Bounty Programs
We are committed to responsible disclosure practices and have reached out to organizations that have vulnerable AEM instances. In cases where they have bug bounty programs, we have reported our AEM vulnerabilities and worked together with their security teams to fix these security issues. By collaborating in this way, organizations can address these issues quickly and recognize the efforts of security researchers.
We were able to report and disclose two vulnerabilities in a public program through HackerOne and can provide their titles:
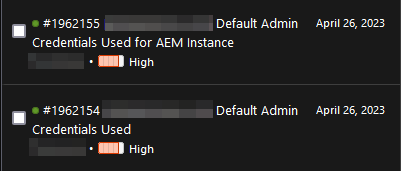
Wrapping Up
In conclusion, it's crucial to remain vigilant and take proactive steps to ensure the security of the entire organization. This includes securing Adobe Experience Manager deployments, scheduling continuous security assessments, and collaborating to strengthen your digital infrastructure. With Trickest, you can easily ensure AEM security by scaling your scanning operations, identifying vulnerabilities, and promoting offensive cybersecurity automation as a foundation for a safer digital environment. If you are interested in enhancing AEM security and scheduling automation of all sorts of use cases, sign up for free to get access to Trickest.
GET STARTED WITH TRICKEST TODAY
Complete our registration to elevate and automate your offensive security endeavors.
Get started