Full Subdomain Brute Force Discovery Using Automated Trickest Workflow - Part 2
Learn how to generate subdomain permutations from an initial list of subdomains and brute force them to discover more subdomains.
In the previous post about subdomain discovery, we explained what subdomain discovery is and the best techniques to start finding subdomains from a domain. We also created a workflow to search for subdomains given a domain name. We show we could find several subdomains from trickest.com and concluded the post by suggesting some improvements, so let's implement them now!
Several Domains as Input
Currently, if we want to use the previous workflow to search for subdomains of different domains, we would need to launch it several times, modifying the domain used as input.
To avoid this, the first improvement we will develop is to allow the workflow to search for subdomains of several domains running it just once.
To do this, the main change we have to make is to change the initial input string for an input file pointing to
https://gist.githubusercontent.com/carlospolop/5422bdc87a8bdb440b73b4b2e5bef794/raw/f38220dcf987875a36bdf6266405f34326d534c9/trickest_domains.txt
This is a .txt file with the domains:
trickest.com
trickest.io
Therefore, instead of using a "STRING-TO-FILE" to connect the initial subdomains to oneforall, for example, we can directly connect our file input:

But what happened with the tools that expect a domain string as input? We can use the special node "FILE-SPLITTER" to call the tools once per line in the input file:
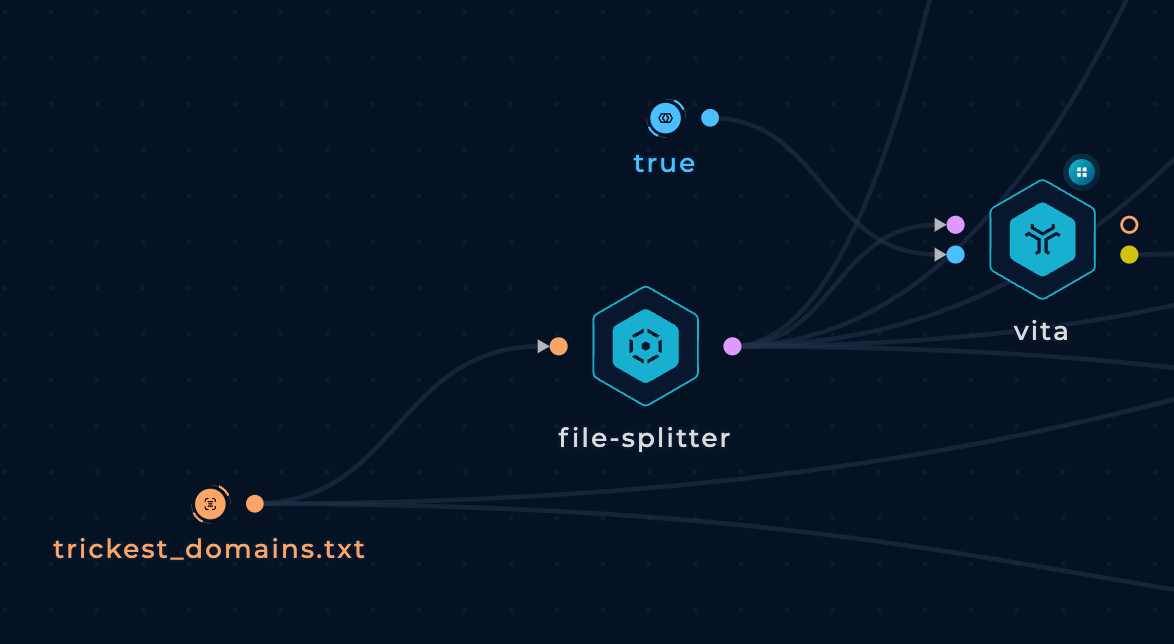
This way, we can control the domains we will enumerate in a gist and enumerate all of them in just 1 run of the workflow.
This is how the workflow looks like after these changes:
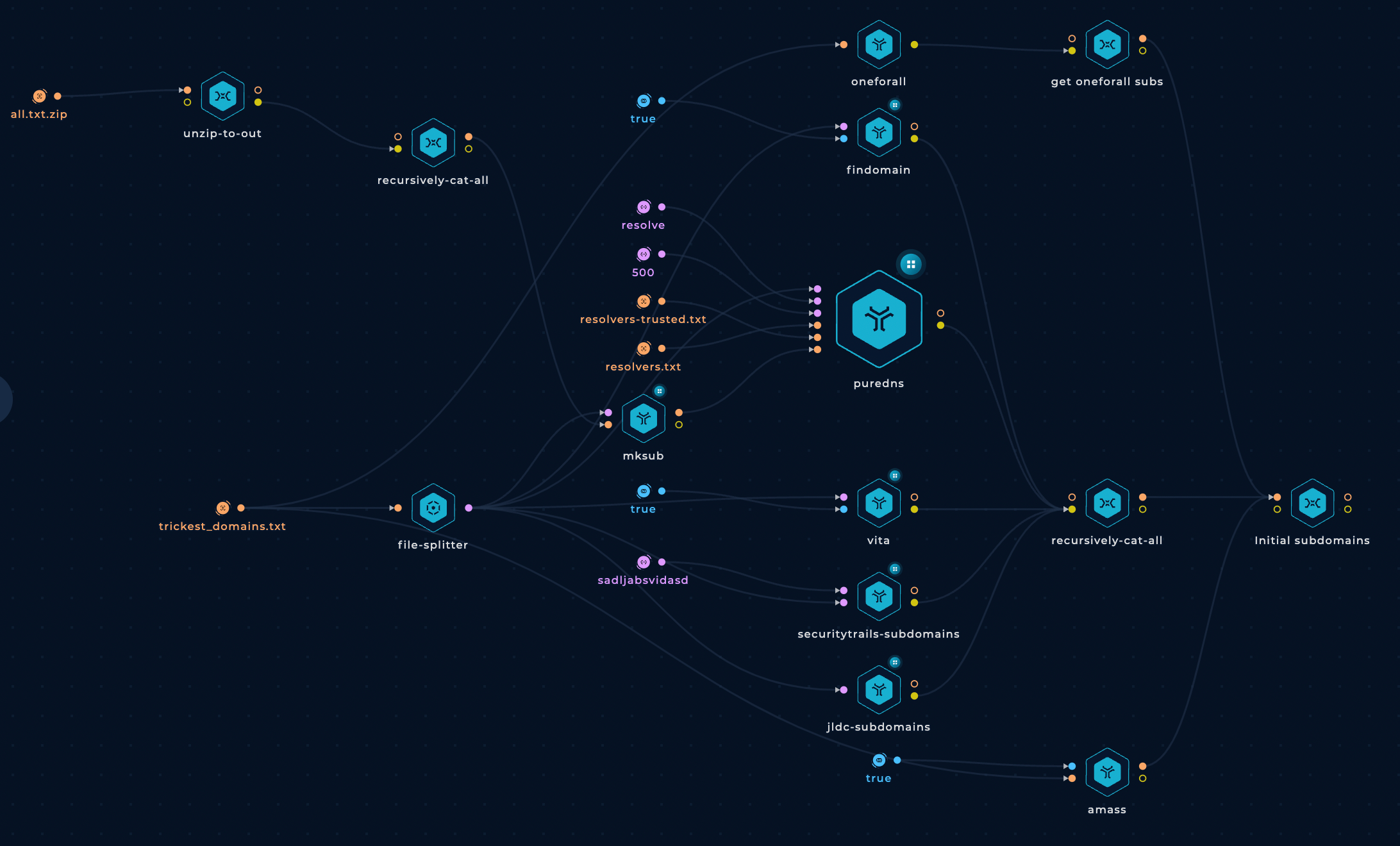
Generate Permutations to Brute Force
Having names of the already discovered subdomains, you could create permutations of those names and brute-force them to discover even more subdomains. For this technique, you need:
- Discovered subdomains: We already have this in our workflow
- Permutation wordlists: Wordlists with permutations to perform.
- Permutation tools: Tools that give names and a permutation wordlist, and the initial names will generate permutations.
Permutation Wordlists
These are the permutation wordlists I will combine into one to use in the workflow:
- https://raw.githubusercontent.com/bp0lr/dmut/main/words.txt
- https://raw.githubusercontent.com/infosec-au/altdns/master/words.txt
- https://raw.githubusercontent.com/cujanovic/goaltdns/master/words.txt
Permutation Tools
In this workflow, I will be using the following tools to generate permutations of the discovered subdomains' names:
Add Wordlists and Brute Force Tools to Trickest Workflow
These are the nodes we will be adding to our workflow to generate permutations of the discovered subdomains and then brute-force them with Puredns (using the same parameters as before):
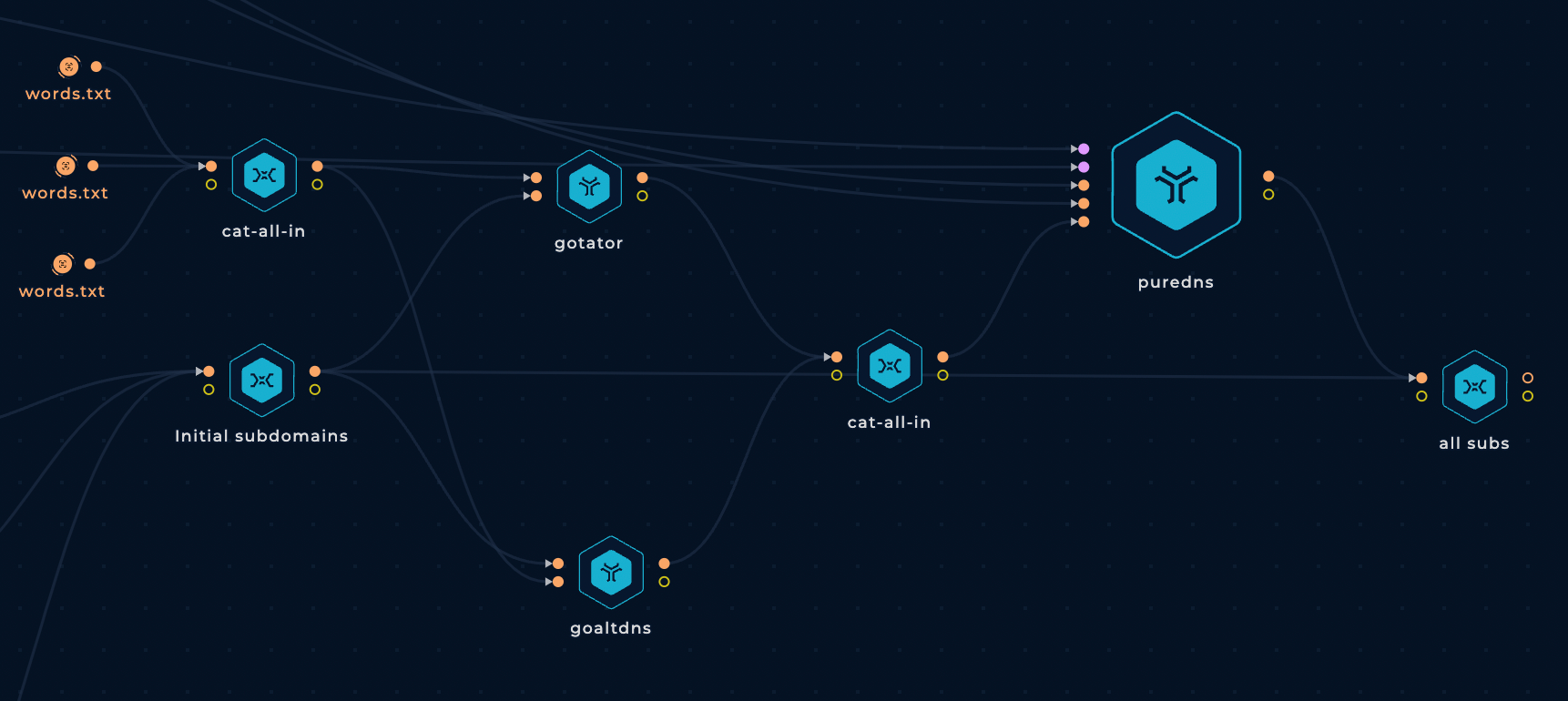
Grabbing All Subdomains
Finally, we will be combining the found subdomains from the first part of our workflow with the discovered brute forcing name permutations into one list.
Run it!
Let's give this workflow a try and see what it finds!
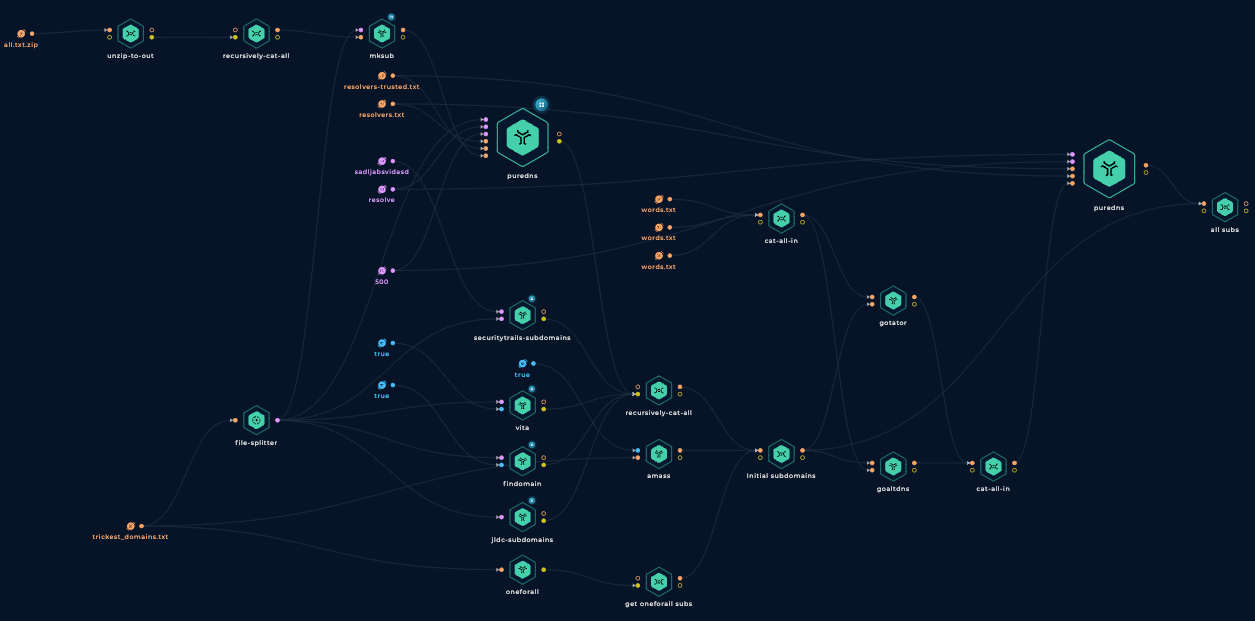
For the sake of brevity, I'm not going to list here all the discovered subdomains, but it discovered 63 subdomains:

Conclusion
We improved our previous subdomain's discovery workflow to try to find hidden subdomains with uncommon names. This will help us find those potentially forgotten subdomains exposing outdated webs.
However, could we improve even more this workflow? Yes, we can. You could dedicate tens of hours to improve this kind of workflow, and you will always find new ways to tune them better.
Here are some suggestions:
- Use more subdomain discovery tools such as SubDomanizer, subfinder and more already supported in Trickest Library/Tools.
- Use more DNS subdomains brute-force wordlists.
- Use platforms that require free or paid API keys to access their information.
- Check HackTricks subdomain's discovery techniques and implement them in Trickest
Furthermore, note that different tools will use the same OSINT platforms to find information and won't find new subdomains. Keep this in mind to optimize your workflow!
All these possibilities allow you to find new subdomains that other hunters or pentesters couldn't find.
Sign up on Trickest and have fun creating your unique workflow!
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
