CVE-2024-27301 CVE-2024-27822 - Discovering Hundreds of Vulnerable MacOS Installers
Learn how to use Trickest to discover hundreds of assets vulnerable to a newly discovered security flaw.
As a pentester, whenever you discover a new type of vulnerability, you're always curious about its real impact. This was the case with the vulnerability CVE-2024-27822 I discovered, which affected hundreds of macOS installers.
This vulnerability allowed abuse of third-party installers to escalate privileges to root without needing the user's password.
To understand how widespread this issue was, I used the Trickest to build workflows and automate the discovery of vulnerable installers.
Fingerprinting Vulnerable macOS Installers
First, I needed a way to identify vulnerable macOS installers. The process was straightforward:
- Identify pre and post-install scripts: macOS installers execute these scripts (e.g.,
preinstall.shandpostinstall.sh) with root privileges - Locate the scripts: These scripts are found in the installer package (
.pkg) inside theScriptsfolder - Identify the vulnerability: If these scripts used the shebang
#!/bin/zsh, they could execute$HOME/.zshenvas root, leading to arbitrary code execution
With this knowledge, I set out to find as many .pkg macOS installers as possible, decompress them, and check for scripts using the shebang #!/bin/zsh.
Method 1: Scraping GitHub
The first method involved scraping GitHub for macOS installers. Previously, I used Trickest to parse 10TB of GitHub logs and categorize millions of repositories.
Using these URLs, I created a Trickest workflow that utilized the GitHub GraphQL API to search for .pkg files in releases and return their URLs.
The workflow:
- Downloads the list of GitHub repositories
- Splits the list into chunks and process them in parallel
- Uses the GitHub GraphQL API to find
.pkgfiles and return their URLs
With 5 machines and the powerful scalable execution engine, it took only half an hour to gather URLs to .pkg files from millions of GitHub repositories, resulting in a few dozen URLs.
Method 2: Scraping itunes.apple.com
This idea came from Nenad, the CEO of Trickest. He suggested scraping itunes.apple.com for application URLs and then scraping these websites for .pkg files.
We created a Trickest workflow to:
- Get application URLs from
itunes.apple.com - Use tools like gau and katana to find paths
- Grep for
.pkgfiles

Using 10 machines, we obtained a few hundred URLs to .pkg files in 5 hours.
Searching for Vulnerable macOS Installers
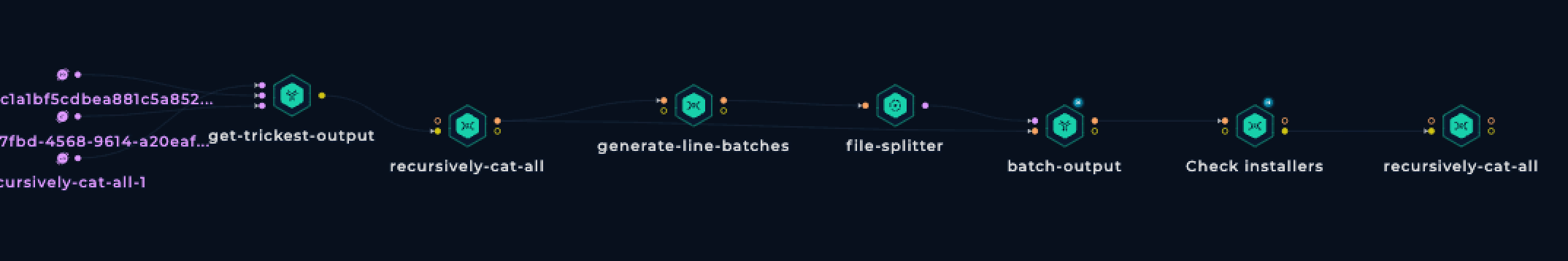
With hundreds of .pkg URLs, it was time to download, decompress, and search for scripts with the shebang #!/bin/zsh. If found, the installer was vulnerable.
We created a simple Trickest workflow:

This workflow:
- Separates URLs into chunks
- Process them in parallel
- Download, decompress, and search for the scripts
Running this workflow with 6 machines in parallel took only about 6 minutes.
Findings & Conclusions
After running these workflows, we discovered over a hundred installers vulnerable to privilege escalation. This exercise and results demonstrated how Trickest can effectively uncover vulnerable assets.
I reported the identified vulnerability to the relevant companies and Apple. Initially, I directly contacted the companies, presuming it to be a misconfiguration that they could rectify autonomously. However, subsequent discussions led me to report the issue to Apple, in consideration of a potential OS-level resolution.
Several CVEs and advisories were released:
- Microsoft advisory
- First reported vulnerability: CVE-2024-27301
- Apple CVE: CVE-2024-27822
After Apple clarified that they would fix the issue, no more advisories or CVEs were requested, and no more companies were contacted about the issue.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
