Trickest Introduces Community Edition, Welcomes NahamSec as Advisor
Discover Trickest's Community Edition for advanced cybersecurity orchestration. Platform Access is now open round-the-clock for all users. Join us in welcoming NahamSec to our advisory team.
Today, we are proud to announce the launch of Trickest Community Edition. This release marks a new era in cybersecurity, democratizing access to advanced security tools and workflow orchestration. Designed to empower a diverse spectrum of users - from academia and individual researchers to educators and bug bounty hunters - the Community Edition is a testament to our commitment of making elite cybersecurity resources accessible to all.
In conjunction with the launch, we are excited to welcome Ben Sadeghipour, also known as NahamSec, a renowned figure in the ethical hacking and bug bounty hunting world, to our advisory team. His expertise and insights in offensive security and bug bounty hunting are set to strengthen the capabilities of our platform, supporting our dedication to innovation and community empowerment.
A key highlight of the Community Edition is the introduction of Self-Hosted Execution, enabling users to connect their machines in order to achieve a highly customizable and controlled execution environment. This feature enhances the flexibility and scalability of security operations as a response to the unique needs of our users.
Furthermore, our shift to Open Access signifies a revolutionary step in inclusivity, allowing ethical hackers, educators, researchers, and bug bounty hunters to sign up on the platform at any time.
Join us and NahamSec in welcoming this new chapter at Trickest!
The Community Edition: Democratizing Offensive Cybersecurity
The Community Edition of Trickest Offensive Security Orchestration Platform offers an exceptional opportunity for users to use open-source tools and custom-made scripts to build and run workflows. It aligns with Trickest's mission to democratize access to state-of-the-art security orchestration capabilities, ensuring that even individual researchers and bug bounty hunters can utilize high-level security workflows and methodologies.
Key features of the Community Edition include:
Run Units (RU)
- We have introduced a new execution metric called Run Units (RU).

- All users will receive 12,000 FREE RUs on Trickest Managed infrastructure with unlimited validity, allowing you to have greater flexibility and control.
- Usage calculation: For every minute that a managed default machine is used in workflow execution, 2 RU are consumed from the user's available RU. See below about default managed machines.
Run Units with Trickest Managed Infrastructure (Machines)
We are excited to announce that we now offer Pre-Paid Run Units for our Trickest managed infrastructure. This new option is specifically designed explicitly for bug bounty hunters, researchers, and educators who need to run machines efficiently while taking full advantage of the Trickest feature. With the Pre-Paid Run Units, you can now enjoy a smoother and more seamless experience when running machines on Trickest managed infrastructure. All purchased RUs have unlimited validity, offering you greater flexibility and control over your usage.

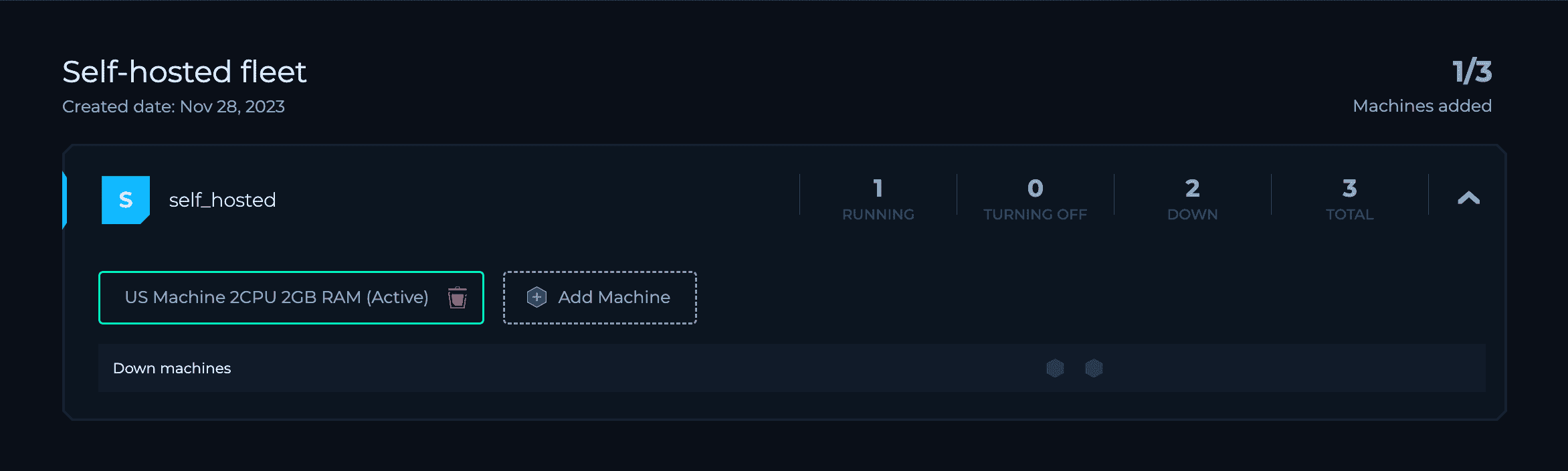
FREE Self-Hosted Execution for Community Users
Attach and use up to 3 of your own self-hosted machines for unlimited FREE execution with the Community Edition. You can refer to our documentation for detailed guidelines on how to do this.
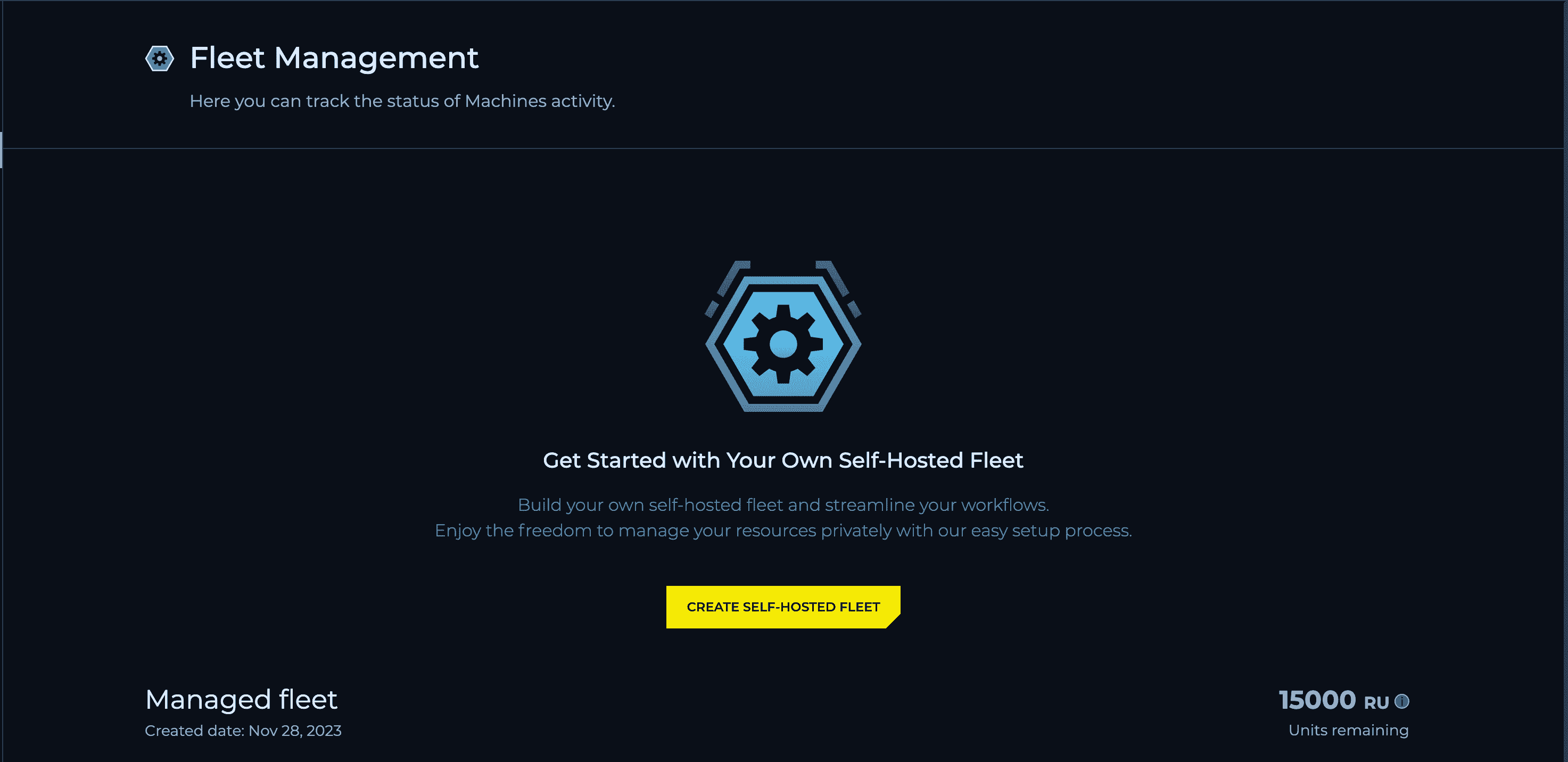
New Default Machine Type
We are excited to announce that we have optimized our specs and introduced a new, default machine type with improved performance (CPU 2, MEM 4). This change optimizes the execution process and significantly enhances the speed of Runs for our users.

Commercial vs. Non-commercial Usage
With the Community edition, you are allowed to use the Trickest Community edition for non-commercial purposes only; however, individuals can use the Community edition for bug bounty purposes. We updated our Terms and Conditions and will notify you of the detailed terms. To use Trickest commercially, please contact our sales team.
Ben Sadeghipour aka NahamSec Joins as Trickest Advisor
In conjunction with the launch, Trickest is excited to welcome a renowned figure in the cybersecurity realm, Ben Sadeghipour, also known as NahamSec as an advisor. With a rich background across various facets of ethical hacking, NahamSec brings a wealth of expertise to Trickest. Known for his significant contributions as the former head of Hacker Education at HackerOne, he has been an ethical hacking enthusiast since his teenage years, transitioning into a professional career in 2014. His work has led to the discovery and exploitation of thousands of vulnerabilities in high-profile web and mobile applications for giants such as Amazon, Apple, Google, Airbnb, Snapchat, the US Department of Defense, Zoom, and more.
NahamSec is not just a highly skilled ethical hacker and bug bounty hunter; he's also a celebrated content creator and keynote speaker. His presence on platforms like YouTube and Twitch has been instrumental in inspiring and educating a new generation of ethical hackers, sharing insights into bug bounty hunting and reconnaissance. His love for gaming, with favorites like Watchdogs, GTA V, PUBG, R6 Siege, and Call of Duty Warzone, resonates with his dynamic approach to cybersecurity. At Trickest, NahamSec's unique blend of hands-on hacking experience, educational leadership, and community engagement is set to drive innovative developments in security solutions, reinforcing our dedication to empowering the cybersecurity community with advanced, automated workflows for offensive security and orchestration.

Open Access: Registration Open 24/7
Trickest has removed the “request an invitation” barrier, making the platform accessible for registration at any time. This open access marks a new era in offensive cybersecurity, inviting a global community of ethical hackers, bug bounty hunters, researchers, and educators to explore and utilize the platform's extensive capabilities.
Core Offerings of Trickest's Platform:
- Custom Offensive Security Workflows: Build, manage, orchestrate, and execute specialized security workflows, including Vulnerability Scanning, Attack Surface Management, and Dynamic Application Security Testing.
- Hyper-Scalable Managed Infrastructure: Designed for large-scale operations, covering vast digital landscapes.
- Collaborative Security Environment: Facilitates teamwork and knowledge sharing within the cybersecurity community.
- Extensive Open-Source Tools Library: Access to over 300 security tools and 80 workflow templates, enabling users to deploy and customize security scans efficiently.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
