The significance of early and accurate threat detection cannot be overstated. Automated vulnerability scanning emerges as a cornerstone in this strategy, offering a methodical and continuous approach to identifying potential threats. It is here that Trickest, an Offensive Security Orchestration Platform, transforms the landscape. Trickest facilitates effective and efficient automated vulnerability scanning, equipping security teams with the advanced open-source tools and capabilities necessary to preventively identify and mitigate potential threats to their environments.
This guide dives into how Trickest amplifies the power of automated vulnerability scanning. With an array of pre-built workflows designed for a diverse range of security needs, Trickest enables both novice and senior security professionals to safeguard their systems. From automated vulnerability detection to continuous attack surface management, Trickest’s platform offers a visual orchestration framework with hyperscalable execution engine and managed cloud infrastructure that empowers users to execute sophisticated security measures with precision and ease. Read on to explore how Trickest's platform can revolutionize your approach to offensive cybersecurity.
What is Automated Vulnerability Scanning?
Automated Vulnerability Scanning is an essential process in cybersecurity, where software tools are deployed to scan systems, networks, and applications for known security weaknesses. This function allows organizations to quickly address vulnerabilities, significantly mitigating the risk of exploitation and enhancing their overall security posture.
Automated scanning provides regular, thorough checks of digital infrastructure, identifying vulnerabilities with precision and consistency. By automating this process, companies can focus their manual efforts on strategic analysis and remediation, ensuring that their defenses evolve in tandem with arising threats.
Understanding the Automated Vulnerability Scanning Process
Automated Vulnerability Scanning simplifies the daunting task of continuous security monitoring. It systematically evaluates your digital infrastructure for known weaknesses by following a multi-step process:
1. Identifying the Vulnerabilities
In this initial phase, automated tools, such as Trickest, perform thorough scans across your network and systems, comparing findings against extensive databases of known vulnerabilities. This includes not only cataloged weaknesses but also common misconfigurations and potential security oversights. The goal is to create a complete inventory of areas that may be prone to cyber threats, ensuring that even the smallest gaps in security are brought to light.
2. Analyzing the Risk
Once a vulnerability is identified, its level of risk is carefully evaluated. Tools assess the severity based on criteria such as the potential for data loss, ease of exploitation, and the affected system's role within the broader network. The Common Vulnerability Scoring System (CVSS) enables a standardized framework for this assessment, assigning each vulnerability a score from 0 to 10, enabling security teams to understand the relative importance and urgency of each identified risk.
3. Prioritizing for Action
With a list of vulnerabilities at hand, they are then prioritized to ensure that resources are allocated effectively. Trickest's automated system assists in this process by ranking vulnerabilities based on their severity, potential impact, and the complexity of remediation. This enables security teams to tackle the most critical issues swiftly, arranging them in a remediation queue that aligns with the organization's security policy and operational requirements.
4. Remediating the Risks
In the remediation stage, the identified vulnerabilities are systematically addressed. This may involve applying patches, updating software, reconfiguring systems, or even removing compromised elements from the network. Automated workflows within the Trickest platform can streamline this process, providing guidance on remediation actions and, in some cases, applying fixes directly through integration with patch management systems.
5. Reporting for Insight
The final step is about transforming the raw data from scans and remediation activities into actionable intelligence. Exhaustive reports are generated that not only detail the vulnerabilities and actions taken but also provide insights for enhancing future security measures. These reports can include trend analyses, recommendations for policy adjustments, and even predictive assessments to anticipate where vulnerabilities may appear next. With Trickest, this information becomes a pivotal part of a continuous feedback loop, fueling smarter, more proactive security strategies.
By enriching each step in the vulnerability scanning process, organizations can ensure that their cybersecurity practices are not only reactive but also strategic and informed, paving the way for a more secure operational environment.
Types of Automated Vulnerability Scanning
When it comes to effectively saving your digital infrastructures, there are different types of vulnerability scans that can be employed to safeguard digital infrastructures. Two important distinctions are internal vs external and authenticated vs unauthenticated scans. It's imperative to use the appropriate type of scan based on the needs and environment. Luckily, Trickest’s versatile platform is adept at facilitating these diverse scanning methodologies, assuring careful examination of digital assets.
Internal Scanning
Diving deep into the heart of your network, internal scanning meticulously examines the devices and systems within the secure perimeter of your firewall. This thorough examination detects vulnerabilities that might be exploited by internal threats or those that have bypassed external defenses, offering a granular view of the security configuration from the inside out.
External Scanning
In contrast, external scanning casts an analytical look beyond your network boundaries, mirroring the perspective of a potential intruder. It methodically probes your externally facing infrastructure—servers, web applications, and network interfaces—to identify vulnerabilities exposed to external attacks, ensuring defenses are shielded where they are most visible to the cyber world.
Authenticated Scans
Authenticated scans, conducted with proper credentials, grant a privileged perspective akin to that of a trusted user, allowing for a deep examination of the system’s integrity. During the scanning process, a thorough analysis is conducted to identify any potential vulnerabilities in the system. Once access is gained, the scan dives into intricate details, exposing any weaknesses that can be exploited. Additionally, the report offers a detailed assessment of the internal security landscape, giving you a better understanding of the potential risks and threats that may exist.
Unauthenticated Scans
Conversely, unauthenticated scans, also known as non-credentialed scans, operate without insider credentials, presenting a view from the perspective of an unauthorized entity. This type of scan is necessary for identifying the initial weaknesses an attacker may target and evaluating the stability of the outer layers of your cybersecurity infrastructure.
By incorporating these varied scanning approaches with Trickest, you empower your team and organization to construct a nuanced, multilayered defensive strategy. Each scanning type complements the others, resulting in a well-rounded vulnerability assessment protocol that leaves no stone unturned in the quest to secure critical digital resources.
Automate Your Vulnerability Scanning with Trickest
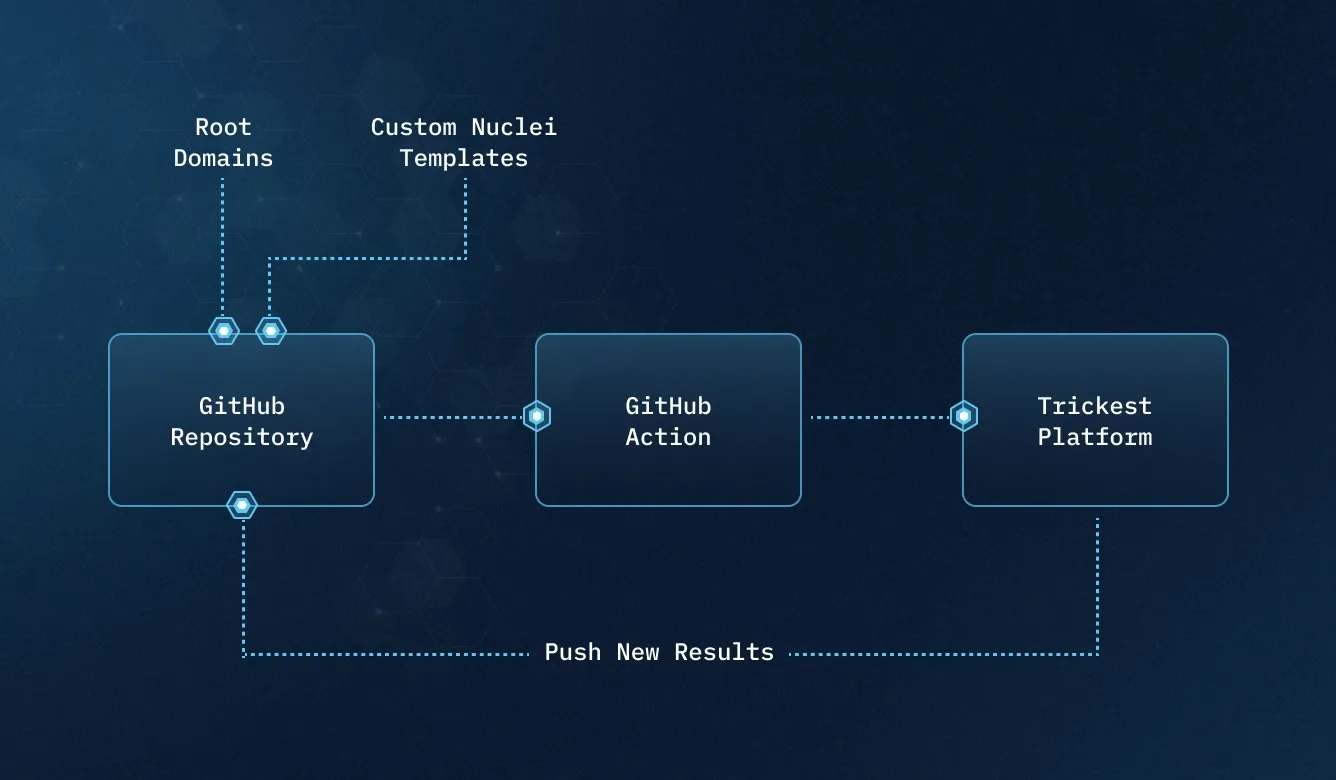
Trickest revolutionizes the field of offensive cybersecurity, bringing a new dimension of automation for diverse security teams. Our platform is specifically designed for Red and Purple Teams, MSSPs, SecOps teams, pentesters, and bug bounty hunters, enabling them to build and manage custom vulnerability scanning workflows with ease. This shift from traditional, heavy methods to a fast, automated approach marks a significant leap in cybersecurity efficiency.
Our platform removes the barriers of complex coding and manual set-up, allowing security professionals to focus on building precise, infrastructure-specific solutions. The Visual Workflow Builder in Trickest transforms complicated scripting into manageable tasks, making the vulnerability scanning process both thorough and effective.
Diving deeper into Trickest's offerings, we offer a variety of pre-built workflows that highlight the platform's mastery in automated vulnerability scanning. These ready-made, customizable templates cater to a wide range of security scenarios, enabling quick and reliable automation of your vulnerability scanning needs. Next, we will look at some of these key workflows, demonstrating the depth and adaptability of Trickest's capabilities.
Vulnerability Scanning Workflows
Take proactive control of your security setup by identifying hidden vulnerabilities within your digital assets automatically with the following workflows:
Scan hosts with Nuclei & Cent
Run a thorough scan across your host list using an extensive collection of open-source templates specifically designed for Nuclei integrated with Cent capabilities:

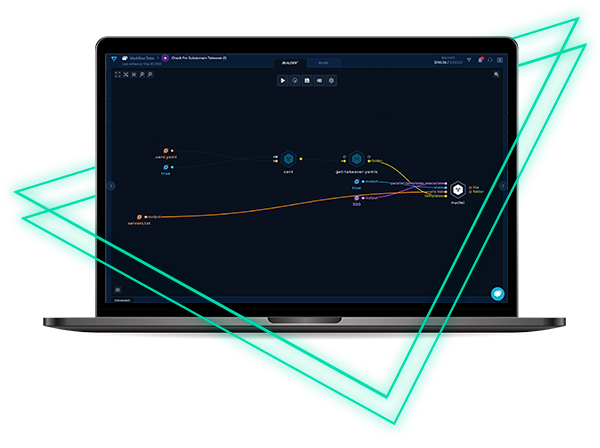
Check for Subdomain Takeover
Detect and secure unused or misconfigured subdomains to prevent takeover attacks with this workflow, utilizing Cent and Nuclei for targeted scanning and immediate threat identification.

Dynamic Web App Scanner
Uncover and test the strength of web application paths and parameters against a range of security threats, including XSS, SQLi, and SSRF, by dynamically generating and applying Nuclei templates with customizable payloads within this workflow.

Best Open-Source Automated Vulnerability Scanning Tools
In the domain of cybersecurity, open-source tools have become fundamental. Trickest seamlessly incorporates these into its workflows, giving users the ability to tune their security processes finely. Whether you're sweeping entire networks or probing deep into application layers, these tools provide the insights needed for strong vulnerability management.
ZAP
Zed Attack Proxy (ZAP) is renowned for being one of the world's foremost open-source security tools, bolstered by an enthusiastic global community. It excels at uncovering security vulnerabilities in web applications during the development and testing stages. Its capabilities also extend to providing a reliable platform for experienced penetration testers to conduct manual security assessments.
Nuclei
Nuclei stands out as a versatile scanning tool, adept at issuing tailored requests to various targets, ensuring precise results with no false positives. Its multi-protocol support, ranging from TCP to Websockets, and a strong templating system, makes it adept at crafting a diverse array of security checks, allowing for efficient scans over extensive networks.
Sqlmap
Sqlmap is a renowned tool in the penetration testing community, designed to automate the detection and exploitation of SQL injection flaws, facilitating the compromise of database servers. It is equipped with a potent detection engine, a suite of features tailored for penetration testing, and a multitude of options for in-depth database analysis, file system access, and command execution through out-of-band connections.
Commix
Commix is an open-source penetration testing utility focused on streamlining the detection and exploitation of command injection vulnerabilities. Developed by Anastasios Stasinopoulos, Commix serves as a specialized tool in the penetration tester's toolkit, automating complex sequences to reveal and exploit command injection weaknesses.
Nikto
Nikto is a sophisticated web server scanner that conducts exhaustive audits against web servers. It tests for a plethora of potential risks, including thousands of hazardous files and programs. Additionally, Nikto checks for outdated software across an array of server types, identifying specific version-related vulnerabilities that could compromise server security.
All of these powerful tools can be used as building nodes in Trickest workflows, empowering users to automate and orchestrate their security operations with ease. With Trickest, you can harness the full potential of each tool, customizing your approach to automated vulnerability scanning and ensuring complete coverage across your digital assets.
The Role of Automated Vulnerability Scanning in Security Strategy
Incorporating automated scanning into your security strategy is necessary for a proactive approach. It simplifies and accelerates the detection and remediation process, ultimately strengthening your security measures.
Continuous and In-depth Scanning
With Trickest, continuous scanning isn't just about vigilance—it's about creating a sustainable, repeatable process that consistently protects your systems. By covering both internal and external aspects of your digital environment, Trickest ensures no vulnerability goes unnoticed.
Using Open-Source Tools for Enhanced Scanning
The rich suite of over 300 open-source offensive security tools in Trickest's Library enables the simultaneous utilization and integration of tools' findings for your vulnerability scanning. This approach delivers a depth of results that proprietary, black-box tools can't match. Open-source tools are integrated and available within Trickest's workflow editor, ensuring that your vulnerability workflows benefit from the team's creativity and ongoing enhancements from the cybersecurity community.
Adapting to Emerging Threats with HyperScalable Execution
Trickest's hyperscalable capabilities and managed infrastructure eliminate the boring tasks of manual setup, configuration, and scripting, providing you with the power to face new challenges head-on. Our platform evolves with you, ensuring that your security measures remain as dynamic as the threats you aim to prevent.
FAQ
What is Vulnerability Scanning?
Vulnerability scanning identifies potential security threats across networks and systems. It is a pillar of any effective cybersecurity strategy, shedding light on areas that need reinforcement to better protect against cyber threats.
What are The Benefits of Vulnerability Scanning?
The advantages of vulnerability scanning are multifold: it strengthens defenses against cyber threats, ensures compliance with various standards, and maximizes the impact of security resources.
Which vulnerabilities do automated scanners detect?
Automated scanners detect an extensive range of vulnerabilities, including but not limited to software flaws, configuration errors, and outdated security measures.
How does Trickest Automate Vulnerability Scanning?
Trickest streamlines the complex process of vulnerability scanning by providing dozens of pre-built workflows that users can execute with a few clicks on a hyperscalable, visual framework. It is for companies of all sizes with specialized teams like Red and Purple Teams, SecOps, and MSSPs, and it also serves bug bounty hunters and penetration testers, enabling them to build, manage, orchestrate, and run custom offensive security automation workflows with over 300 open-source tools and scripts already integrated.