
On this page
Get Started with WorfklowsThe sanctity and security of container orchestration systems like Kubernetes have become paramount. As they become integral to the infrastructure of numerous organizations, the incidents of breaches and vulnerabilities in these systems have surged. Notable breaches in recent years have laid bare the potential risks and consequences of insufficient security practices in Kubernetes environments:
-
Argo CD Supply Chain Attack (2022): This attack targeted the open-source Argo CD tool, compromising multiple Kubernetes clusters. Attackers injected malicious code into the Argo CD repository, highlighting the risks of supply chain attacks in Kubernetes environments.
-
Codecov Breach (2021): A compromised Codecov Bash Uploader script led to the exposure of thousands of customer credentials and source code. This incident highlighted the risks associated with supply chain attacks in Kubernetes environments.
-
Capital One Breach (2019): A misconfigured Kubernetes cluster allowed a hacker to gain access to sensitive customer data, including credit card applications and social security numbers. This breach emphasized the need for proper configuration and access control measures in Kubernetes deployments.
In cloud technology today, Kubernetes is a crucial tool for managing containers. As businesses increasingly rely on Kubernetes to run their applications efficiently, ensuring that these systems are safe from digital threats is vital.
Welcome to our thorough guide on making your Kubernetes environment more secure. We've gathered practical insights from security practices and workflows in Trickest to give you the knowledge and tools to secure your Kubernetes setup, ensuring it's well-protected against potential threats. Trickest is an all-in-one offensive cybersecurity platform that helps automate the end-to-end security and monitoring of your Kubernetes clusters.
What Is Kubernetes?
Kubernetes, commonly called K8s, is an open-source platform designed to automate the deployment, scaling, and operation of application containers. Developed by Google and now maintained by the Cloud Native Computing Foundation, it aims to provide a framework for running distributed systems resiliently, taking care of scaling and failover for applications, providing deployment patterns, and facilitating both declarative configuration and automation. It groups containers that make up an application into logical units for easy management and discovery.
At its core, Kubernetes manages clusters of virtual machines and schedules containers to run on those VMs based on the available compute resources and the resource requirements of each container. Containers are isolated from one another and bundled with their software, libraries, and configuration files; they can communicate with each other through well-defined channels. Kubernetes is highly modular, giving users the flexibility to deliver services built on a microservices architecture, and it is designed to run on a variety of infrastructure choices, including on-premises, public clouds, and hybrid clouds.
Why is Kubernetes Security important?
Protection Against Unauthorized Access
Securing your Kubernetes environment is necessary to prevent unauthorized individuals or entities from gaining access. Without proper security measures, malicious actors could infiltrate your cluster, compromising sensitive data and potentially disrupting your applications. Effective access control ensures only trusted users can interact with your Kubernetes resources, reducing the risk of unauthorized intrusions.
Avoiding Configuration Mistakes
Mistakes in your Kubernetes configurations can have serious consequences. Improperly configured settings might accidentally expose sensitive data or introduce vulnerabilities. Security practices help identify and fix configuration errors before attackers can exploit them. This proactive approach minimizes the chances of unintentional data exposure and system vulnerabilities.
Dealing with Ongoing Threats
Without adequate security measures, your system remains vulnerable to evolving attack techniques. Effective security practices offer continuous monitoring, threat detection, and fast responses to counteract these persistent threats. This proactive stance keeps your cluster secure against evolving security risks.
Meeting Compliance Standards
Many industries and organizations are subject to regulatory requirements and compliance standards that mandate robust security practices. Failing to meet these standards can lead to legal consequences and reputational damage. Kubernetes security practices play an important role in maintaining compliance with data protection regulations and industry-specific security requirements, ensuring your organization operates within the bounds of the law.
Ensuring Business Continuity
Kubernetes clusters are fundamental for the uninterrupted operation of many applications and services. Any unplanned disruptions within your cluster can significantly impact business operations, leading to revenue loss and customer dissatisfaction. Strong security practices, including backup and disaster recovery plans, ensure that your applications can continue running despite unexpected incidents. Ensuring this safeguards your business and its critical functions, reducing the financial and operational impact of disruptions.
Kubernetes OWASP Top 10
The OWASP (Open Web Application Security Project) Top 10 for Kubernetes outlines the most critical security risks facing Kubernetes environments. It includes risks such as:
- Inadequate Access Control
- Excessive Permissions
- Insecure Images
- Vulnerabilities in Cluster Configuration
- Unprotected Secrets and Configurations
- Lack of Network Policies
- Inadequate Logging and Monitoring
- Excessive Trust in External Resources
- Inadequate Resource Management
- Security Risks in Application Code
Understanding and addressing these risks is crucial for securing your Kubernetes environment.
Enumerating Kubernetes with Trickest
Trickest is a new ally in enhancing the security of Kubernetes environments against sophisticated threats. Our aim is to equip organizations with the most effective open-source tools and methods that can detect vulnerabilities automatically. By utilizing Trickest's platform, you can shift Kubernetes security from a reactive approach to a proactive one and ensure that your clusters are resilient.

We’ll primarily use two powerful tools, Nuclei and Naabu, to enumerate the Clusters or Pods. This workflow will also encompass identifying and assessing common vulnerabilities that could potentially compromise these servers:
-
Workflow input node will be a list of Domains or Hosts
-
From the Input file, we create Line Batches, i.e., splitting the input file into small batches and performing the execution in batches.
-
We pass those batches to DnsX to filter out the Live Domains using the following flags:
-a- To query A records-r- Providing a resolvers file
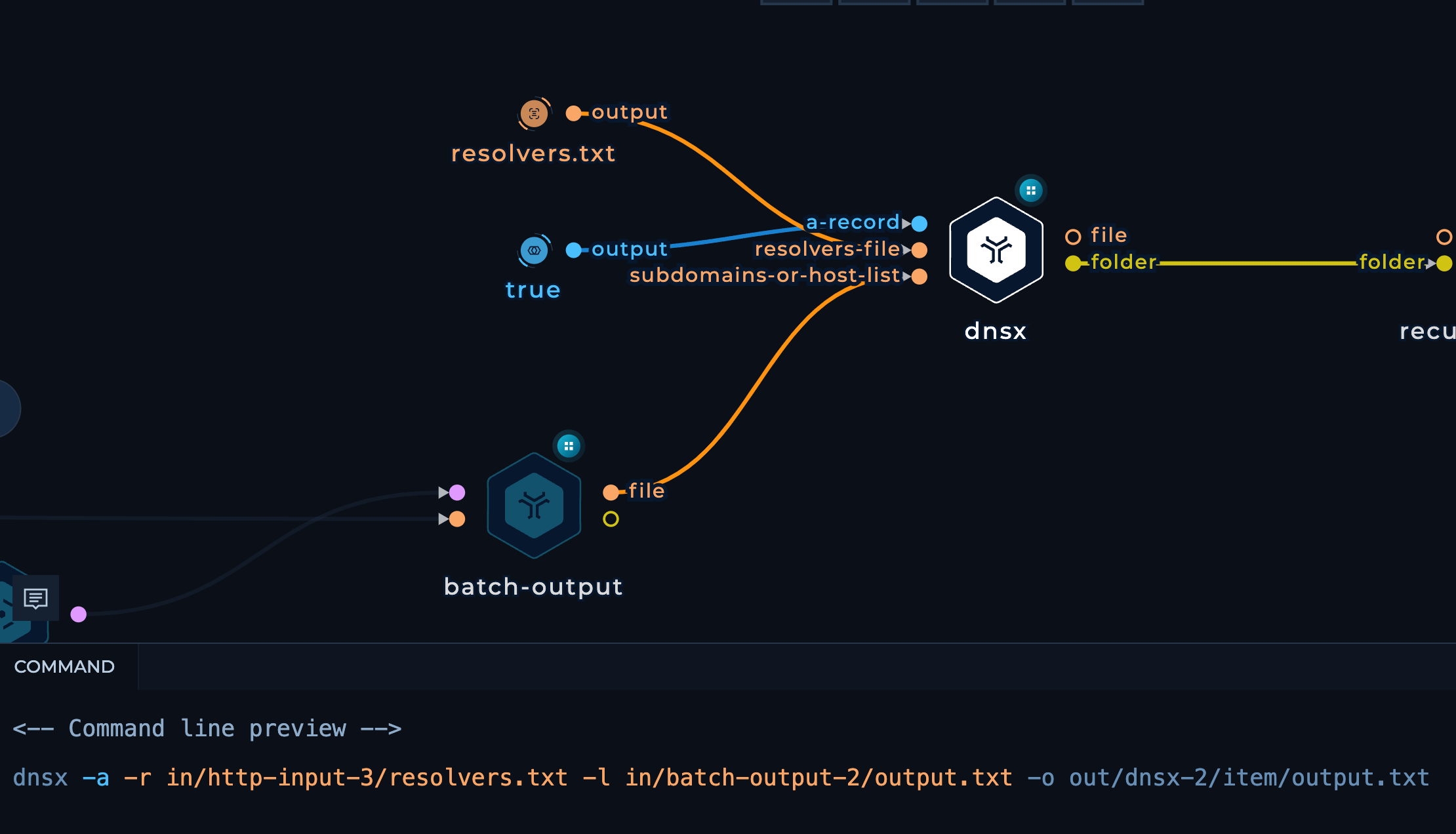
-
Again, from the DnsX output, we’ll perform the execution in Batches.
-
We pass those batches to both, Naabu & Nuclei with the following flags:
Naabu
-c 200- Max threads to use for parallel execution-port 2379,6666,4194,6443,8443,8080,10250,10255,10256,9099,6782-6784,30000-32767,44134- Potential Ports open for a Kubernetes Cluster (can play around with these)

Nuclei
-tags kubernetes- Only execute the templates that have a “kubernetes” tag-retries 3- Max number of retries-concurrency 14- Max number of templates to execute in parallel-no-httpx- Disable httpx
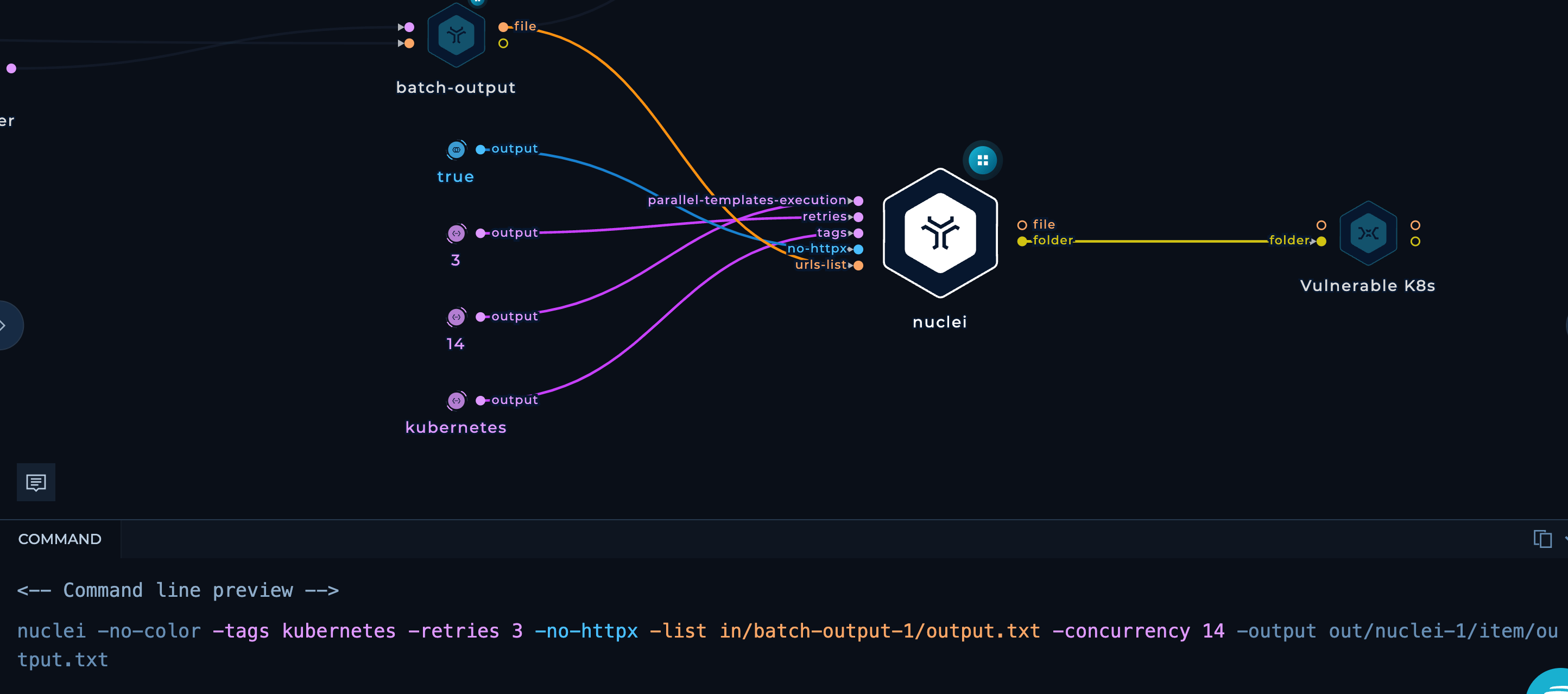
-
Recursively cat both Naabu and Nuclei and get a combined output of all batches for both the tools in their respective txt files.

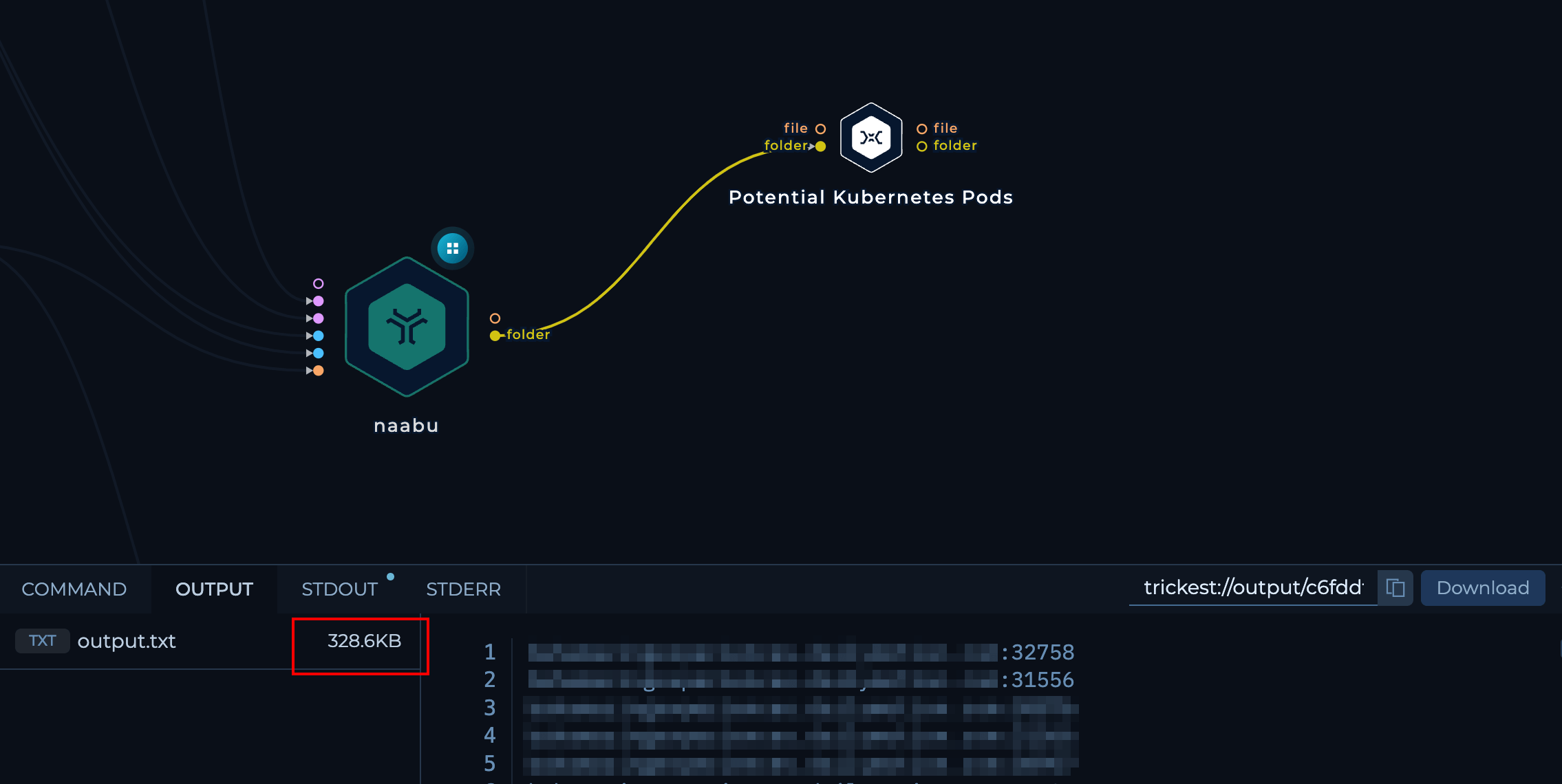

How to Secure Kubernetes?
Access Control and RBAC (Role-Based Access Control)
Access control and RBAC determines who is allowed to enter and what they are permitted to do once inside. RBAC, in particular, assigns specific permissions to roles, much like a security clearance system, ensuring that individuals have access only to the areas necessary for their role, thereby maintaining the integrity and safety of the system.
Pod Security Policies
Pod security policies act as a set of guidelines that govern the behavior of containers within the system. These policies set boundaries for container actions, ensuring that they operate within the safe confines of predefined rules, much like regulations that maintain order and safety within a community.
Image Scanning and Validation
Image scanning and validation function as a quality control checkpoint for container images, similar to a thorough inspection process. Before deploying an image, it is scanned for vulnerabilities and compliance with security standards, ensuring that only secure, verified images are utilized in your applications.
Network Security
Network security in Kubernetes is akin to a system of secure communication protocols within a company, dictating who can communicate with whom and what information can be exchanged. It establishes secure pathways and checkpoints within the network, ensuring data integrity and confidentiality.
Regular Updates and Patch Management
Keeping Kubernetes components up to date with regular updates and patch management is akin to performing routine maintenance on complex machinery. It involves regularly reviewing and enhancing the system with the latest updates and fixes, ensuring optimal performance and security.
Continuous Monitoring
Continuous monitoring in Kubernetes is the equivalent of a vigilant oversight committee, constantly overseeing activities within the system to detect any unusual or unauthorized actions. It provides immediate alerts and insights, enabling quick response to potential security incidents.
Backup and Disaster Recovery
Backup and disaster recovery strategies in Kubernetes are akin to an emergency response plan that prepares for worst-case scenarios. They involve creating and maintaining copies of critical system data and configurations, which can be used to restore normal operations in the event of a catastrophe, minimizing disruption and data loss.
Third-Party Security Solutions
Integrating third-party security solutions brings advanced capabilities and expertise, offering an additional layer of security to protect against sophisticated threats.
Conclusion
Securing Kubernetes is about building a strong defense system. Just like Securing anything Tech, it's not something you do once and forget about; it's a continuous process that demands attention and regular updates. By following the security practices we've discussed, you create a strong foundation to keep your Kubernetes environment protected.
As you dive deeper into Kubernetes security, remember that the aim is to create a system that's not just resistant to attacks but also adaptable and resilient, ensuring the smooth operation and reliability of your services. Trickest helps you streamline these efforts by automating kubernetes security operations, and many more for automated pentesting, with workflows and open-source tooling, making it easier to keep your defenses sharp and effective. And we’re practically just scratching the surface in this Blog post in terms of enumerating or attacking Kubernetes Clusters from an Offensive Security standpoint with Trickest. Sign up to explore and automate a various use cases with Trickest and actively secure your Clusters.
GET STARTED WITH TRICKEST TODAY
Complete our registration to elevate and automate your offensive security endeavors.
Get started