On this page
Get Started with WorfklowsWe are excited to delve into an important subject with remonsec: 403 bypass methods and how to use Trickest workflows to scan 403 endpoints.
HTTP 403 errors, indicating forbidden access, are a commonplace stumbling block in cybersecurity testing. There are several tools available to bypass these 403 endpoints. However, this workflow is aimed to incorporate techniques that are found to be effective, quick, and capable of scanning numerous endpoints in no time.
Let's begin by breaking down these methods and how they work. These techniques have been discovered and fine-tuned during bug bounty hunting, and while they lack a specific technical source, you'll find proofs-of-concept (POCs) available on remonsec's YouTube channel and write ups.
To be able to verify and test our methodologies, we've created our own Forbidden Lab!

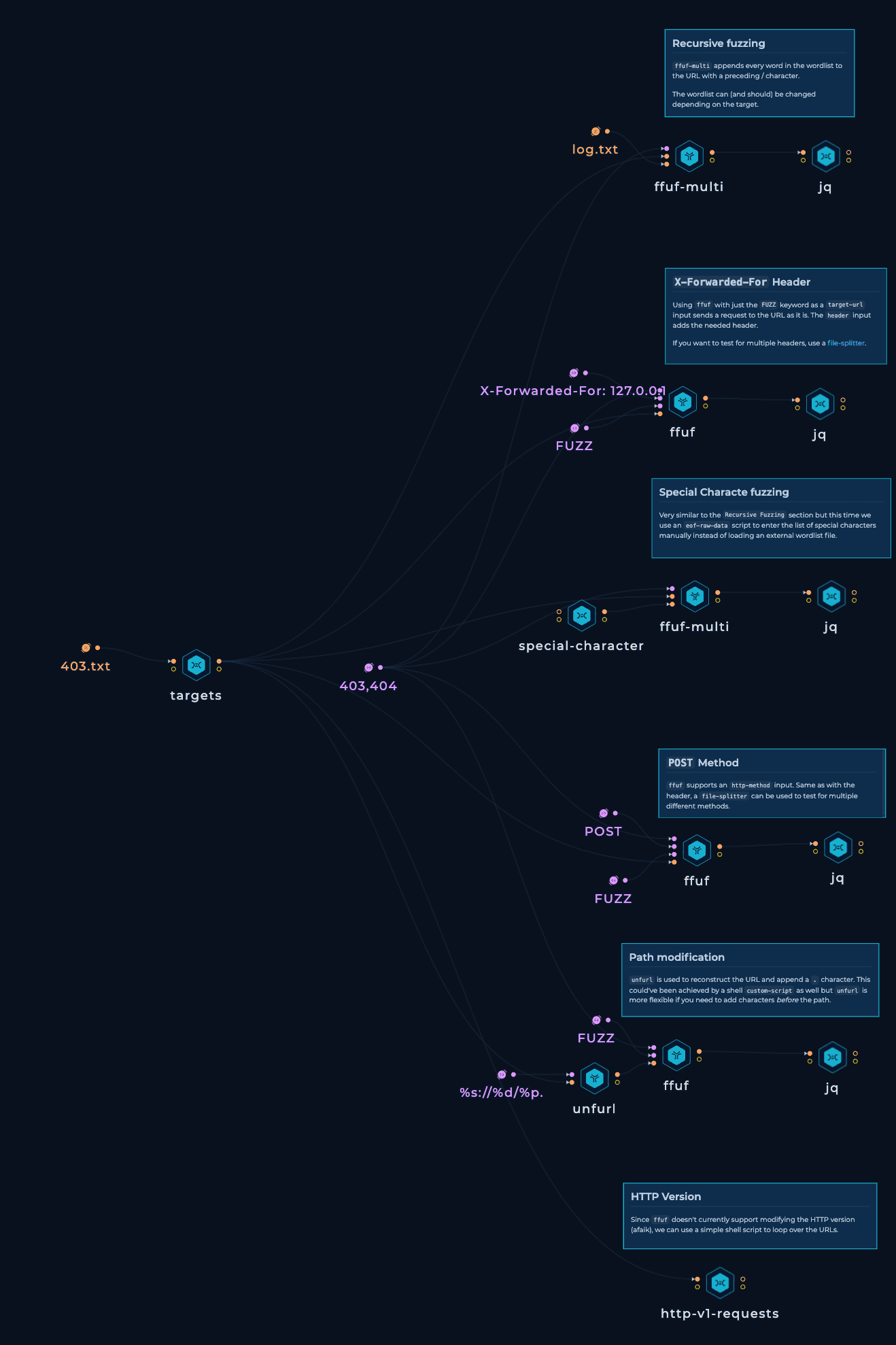
Recursive Fuzzing
Recursive fuzzing, in this context, refers to the process of fuzzing endpoints iteratively. It involves using a fuzzing tool like FFUF to fuzz a specific endpoint, such as "/dashboard," and then recursively fuzzing subsequent endpoints like "/dashboard/users." This approach allows for a comprehensive exploration of various endpoints and helps identify potential vulnerabilities across multiple levels of a web application or API.
Absolutely, this recursive fuzzing technique can be applied to 403 endpoints as well. In some cases, you might encounter a situation where accessing an endpoint like "/log" returns a 403 HTTP response, indicating that access is forbidden.

However, by employing recursive fuzzing on this "/log" endpoint, you might discover a sub-endpoint like "/log/log.txt" that returns a 200 HTTP response, indicating a successful request. This iterative approach enables you to bypass the initial 403 restriction and gain access to hidden resources.

Custom HTTP Header
Ever wondered how to sneak past those sneaky 403 endpoints? Well, here's a neat trick using a custom header called X-Forwarded-For! When you send a request to the server, it checks your IP address and headers to see if you're allowed in.

But with X-Forwarded-For, you can play a little hide-and-seek by adding a pretend IP address like 127.0.0.1 (that's like saying, "Hey, I'm from localhost!"). And voila! The server might just fall for the trick, thinking you're a trusted source, and grant you access to the once-forbidden endpoint.

Using Special Characters
A fine trick to outsmart those tricky 403 endpoints. Here's the scoop: sprinkle some special characters, like adding "" to the endpoint magic! Picture this: you try to open "/info.php," but it's a 403 HTTP status code. Add that magical "" to become "/info.php/*" and watch the server go, "Wait, what's this? A secret passageway!" and voila! You're in with a shiny 200 HTTP status code right where you wanna be! It's like playing hide-and-seek with the server's path patterns, and you're the crafty winner!

Changing HTTP Methods
Let's talk about a nifty trick to access restricted resources in a friendly way. When you encounter a 403 error, try sending a different request instead of the usual method, and the server might grant you access.

Maybe when it’s GET you use POST and when it’s POST you use GET, It cleverly leverages how servers handle different HTTP methods.

Changing Naming Scheme
Here's an awesome trick to know for accessing restricted resources. When faced with a 403 error on a resource like "/config.php" don't give up just yet!

Try adding an extra dot to the file name, like "/config.php." You might just unlock the door with a 200 HTTP status code and get access to what you need. This technique plays smart with how servers handle file name extensions.

Changing HTTP Protocol Version
When you encounter a frustrating 403 error on a resource like "/sql.php"

try this: use the curl command with the "--http1.0" option in your request. The server might interpret the protocol version differently, giving you a sweet 200 HTTP status code and granting access to that desired resource. This crafty technique plays with how servers handle different HTTP protocol versions.

Automate Everything With Trickest
Having dissected each method, it's time to automate the process. Trickest provides an ideal framework to do so. A 403 bypass workflow incorporates all these bypass methods into a unified, automated workflow.
The workflow is essentially a set of checks using different open-sourced tools. For recursive fuzzing, we used FFUF with suitable arguments.
During the workflow execution, you will be able to set the number of machines you want to run your workflow on, ensuring fast and efficient automation.
These techniques are elementary yet effective and frequently applied in wild-scope programs. If you have more bypass methods in mind, feel free to add them to this workflow and share them with the community.

Conclusion
And there you have it - a comprehensive overview of techniques to bypass pesky 403 forbidden errors and access restricted endpoints. These methods demonstrate that a little creativity and know-how can open many doors that may seem shut.
Automating these techniques as a unified workflow with Trickest provides a powerful means to thoroughly test web apps at scale. The ability to leverage multiple machines enables blazing fast execution to find vulnerabilities across vast scopes.
Whether you're a bug bounty hunter, penetration tester, or work in cybersecurity, implementing this automated 403 bypass workflow will become an invaluable asset in your toolkit. The techniques discussed are proven and effective, yet remain simple enough for anyone to understand and utilize.
So why not give it a try? Sign up for free on Trickest today and begin bypassing 403s like a pro. Unleash workflows across large scopes and uncover hidden flaws before they can be exploited by the bad guys. The power lies at your fingertips!
GET STARTED WITH TRICKEST TODAY
Complete our registration to elevate and automate your offensive security endeavors.
Get started