Active Content Discovery
Map out all available paths, endpoints, parameters, and virtual hosts using various discovery and scanning techniques to ensure the success of your scans.
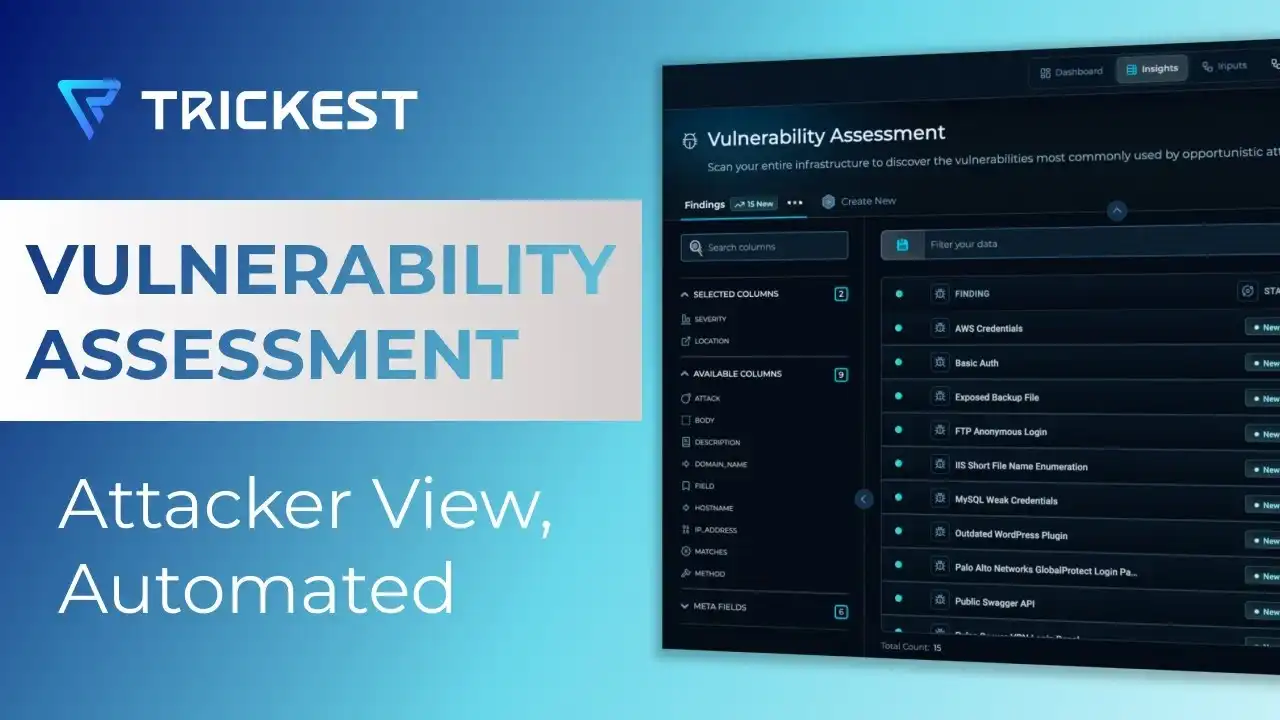
Identify and fix vulnerabilities with precision and speed using Trickest's cutting-edge solution with real-time improvements. Our baseline scanning of web servers ensures you catch CVEs, misconfigurations, and other vulnerabilities, making your vulnerability management more effective and scalable.
Various security alerts requiring attention
Active critical severity vulnerabilities
Active high severity vulnerabilities
Your current tools miss critical vulnerabilities, overwhelm your team with false positives and negatives, struggle with large-scale environments and to meet your compliance requirements. Overcome these challenges by surpassing the limitations of your current scanners.



Detect CVEs, misconfigurations, exposures, outdated software across your custom apps, off-the-shelf software and network infrastructure, and other vulnerabilities across vast infrastructures with unparalleled speed and efficiency.
Stay informed about every step of the process and extend it as you need. Our solution allows you to monitor, but also customize every aspect of your scanning process, ensuring you have full control and visibility over your vulnerability management.
Our execution engine efficiently handles infrastructures of any size, providing ultra-fast vulnerability scanning to secure even the largest environments.
Continuously scan your entire infrastructure to discover the vulnerabilities most commonly used by opportunistic attackers.
Identify assets running software versions affected by CVEs.

Detect misconfigurations and exposures using targeted scanning modules for each technology.
Find assets leaking sensitive information such as configuration files, tokens, credentials, backups, and internal API documentation.
Perform a comprehensive scan of the most critical assets.
Map out all available paths, endpoints, parameters, and virtual hosts using various discovery and scanning techniques to ensure the success of your scans.
Fuzz endpoints to identify vulnerabilities in your custom-built applications, such as SQL injection, XSS, and more.
Conduct a full network check-up to identify vulnerabilities, misconfigurations, and weak credentials affecting your open ports.
Trusted By
Get a PERSONALIZED DEMO
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
Discover other powerful solutions built to elevate your offensive security operations.