Visualize, Operate & Scale Dynamic Application Security Testing
No target limits. No frustrations. You set the pace.
Trickest DAST shape to your needs, adjusting every scan on the fly for ultimate control. Threats evolve—so do we.
Various security alerts requiring attention
Active critical severity vulnerabilities
Active high severity vulnerabilities

What's Holding Your DAST Back?
Outdated DAST solutions struggle with customization, accuracy, and scalability, leading to inefficiencies and missed vulnerabilities in complex environments.

Limited Customization and Transparency
- Inability to adapt to different application environments, limiting flexibility.
- No options to customize or fine-tune scanning processes to your needs.
- Lack of visibility into how scans are performed.

High False Positives
- Generates excessive false positives, distracting from genuine threats
- Triggering false alarms across organization and remediation teams
- Overburdens teams with unnecessary triage, slowing down critical fixes.

Inefficiency in Large Environments
- Struggles to handle large-scale applications, leading to incomplete scans.
- Performance bottlenecks slow down testing across extensive infrastructures
- Inability to adapt scans to varying scopes and targets across large infrastructures, resulting in missed vulnerabilities
Enhance Your Application Security with Trickest Unauthenticated & Authenticated DAST
Comprehensive Mapping
Leverage a fine-tuned set of content discovery techniques, including crawlers, web archives, custom wordlists, and brute force. By choosing the methods per scope, you ensure every path, endpoint, and parameter is revealed—discovering what run-and-scan tools often miss.
Precise Vulnerability Detection
Trickest enables rapid incorporation of new vulnerability checks in every scan, keeping scanning rules up-to-date. Both our team and users can quickly update the logic, eliminating delays from product requests or roadmap dependencies.
Beyond Fuzzing
Our solutions provide 100% coverage by addressing the most common vulnerabilities and allowing easy customization for any unique risks. Boost your security by adding custom checks with an easy drag-and-drop interface.
DAST Evolved
Fully customizable and ready-to-go DAST scanning with set of processes tailored for outstanding results.
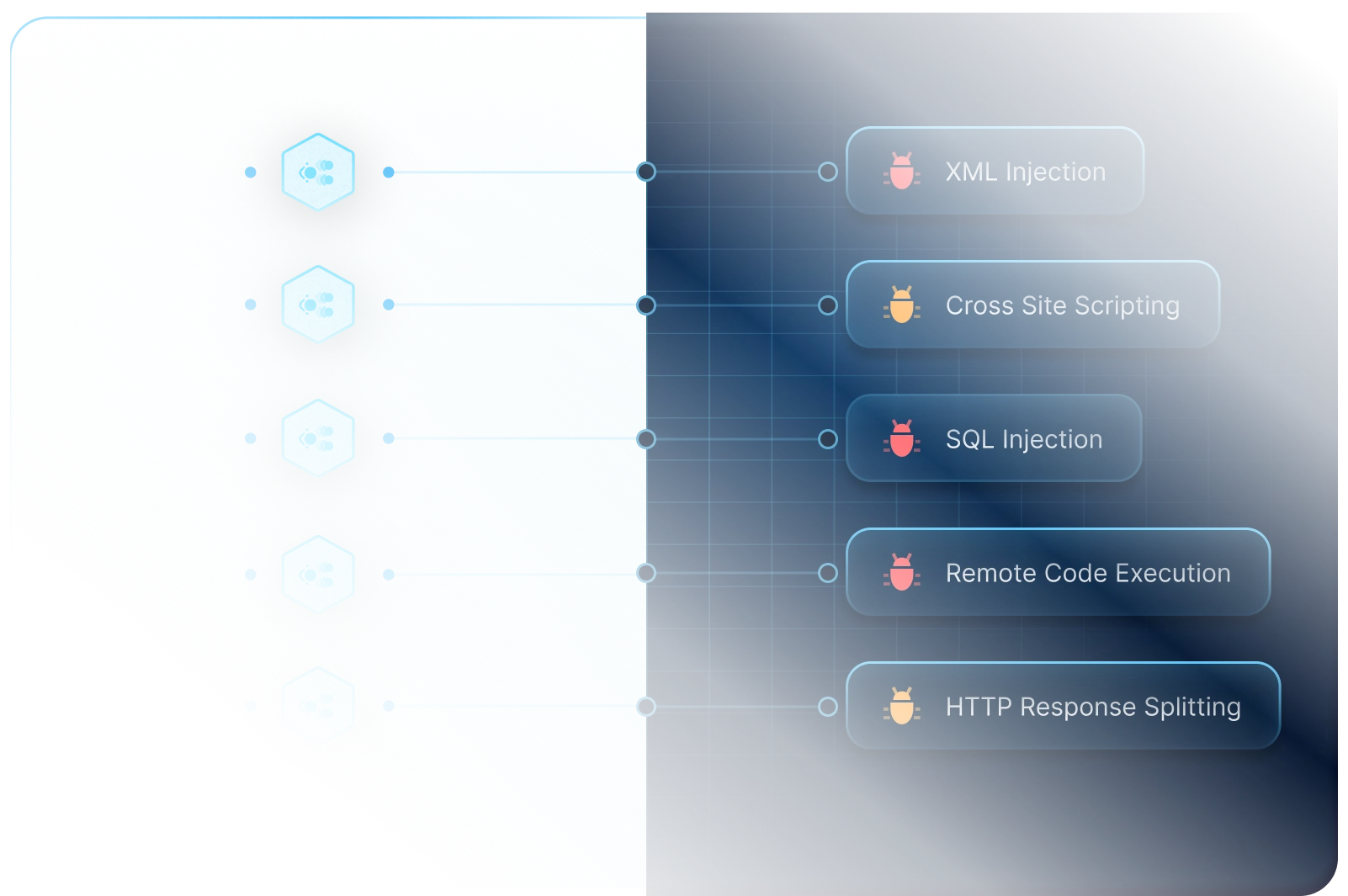
Uncover Novel Web Vulnerabilities
Every application is unique, and generic solutions often overlook hidden risks, leaving critical vulnerabilities exposed. Protect your apps with automated, custom scans for the OWASP TOP 10 and more.
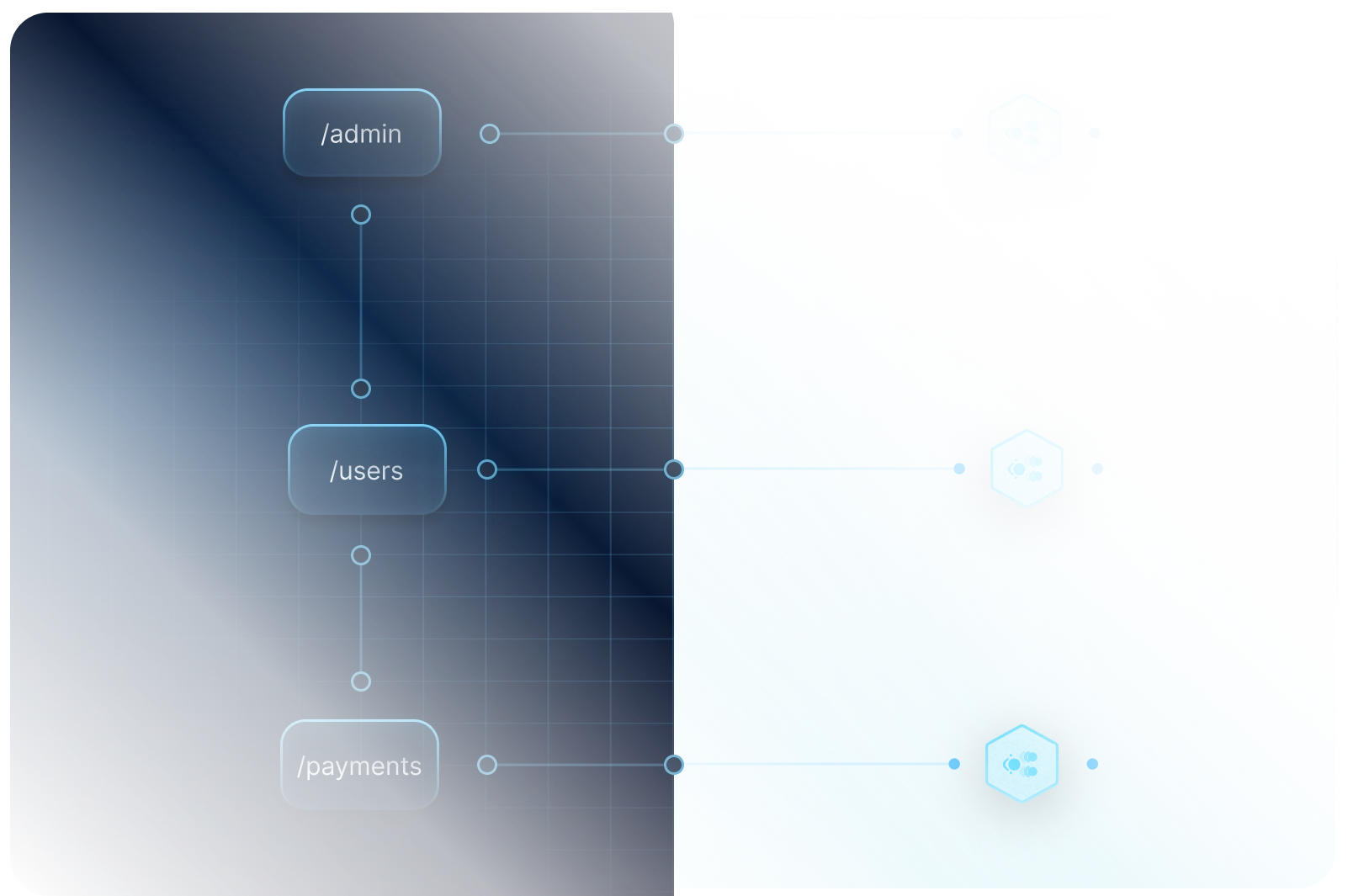
Find Your Most Sensitive Access Points
Everyday applications often include admin panels, backup directories, user management, and more. Ensure unauthorized access is blocked and prioritize the security of your users.
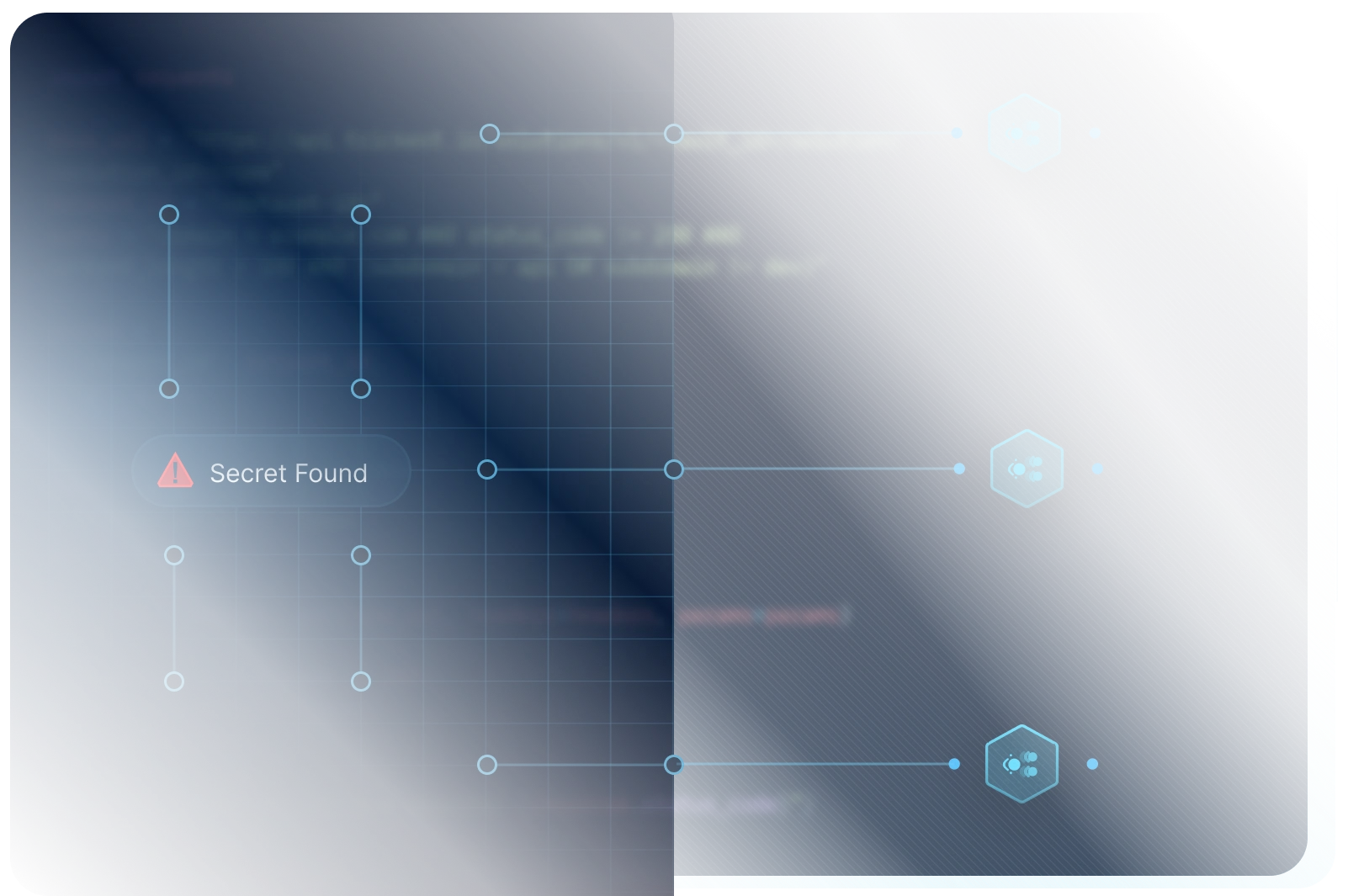
Detect Exposed Secrets
Third-party software credentials frequently get leaked online, leading to a total compromise of your data through your vendors. Identify exposed secrets and verify their validity to prevent credential misuse.
Secure Your Assets Against Targeted Attacks
Hackers often target vast lists of potential victims based on specific technologies. Don't become just another randomly chosen target.

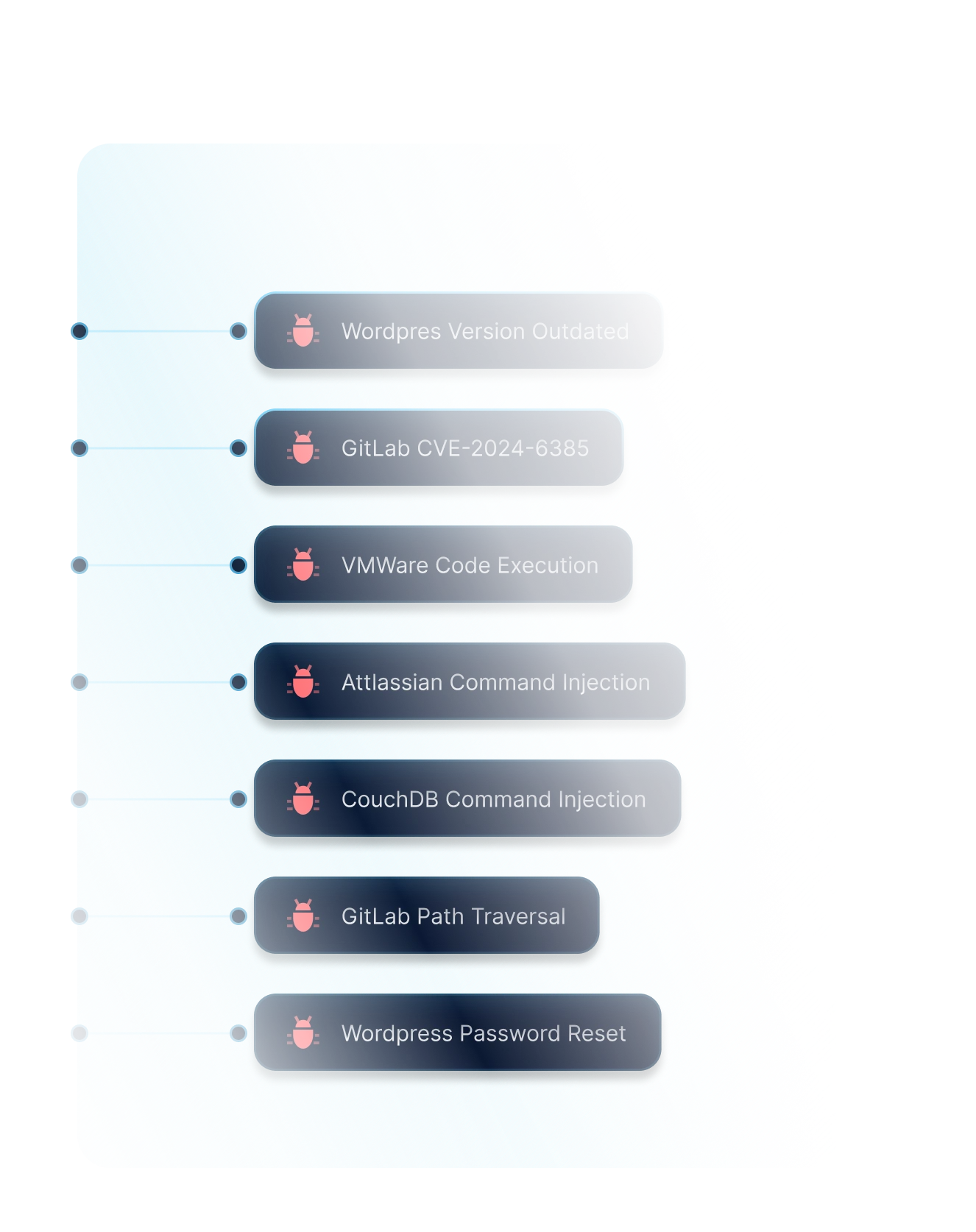
Scan for Misconfigurations and Outdated Systems
Misconfigurations can happen any time, software updates are constant. Stay ahead by having a continious and up-to-date scanning of all of your assets.
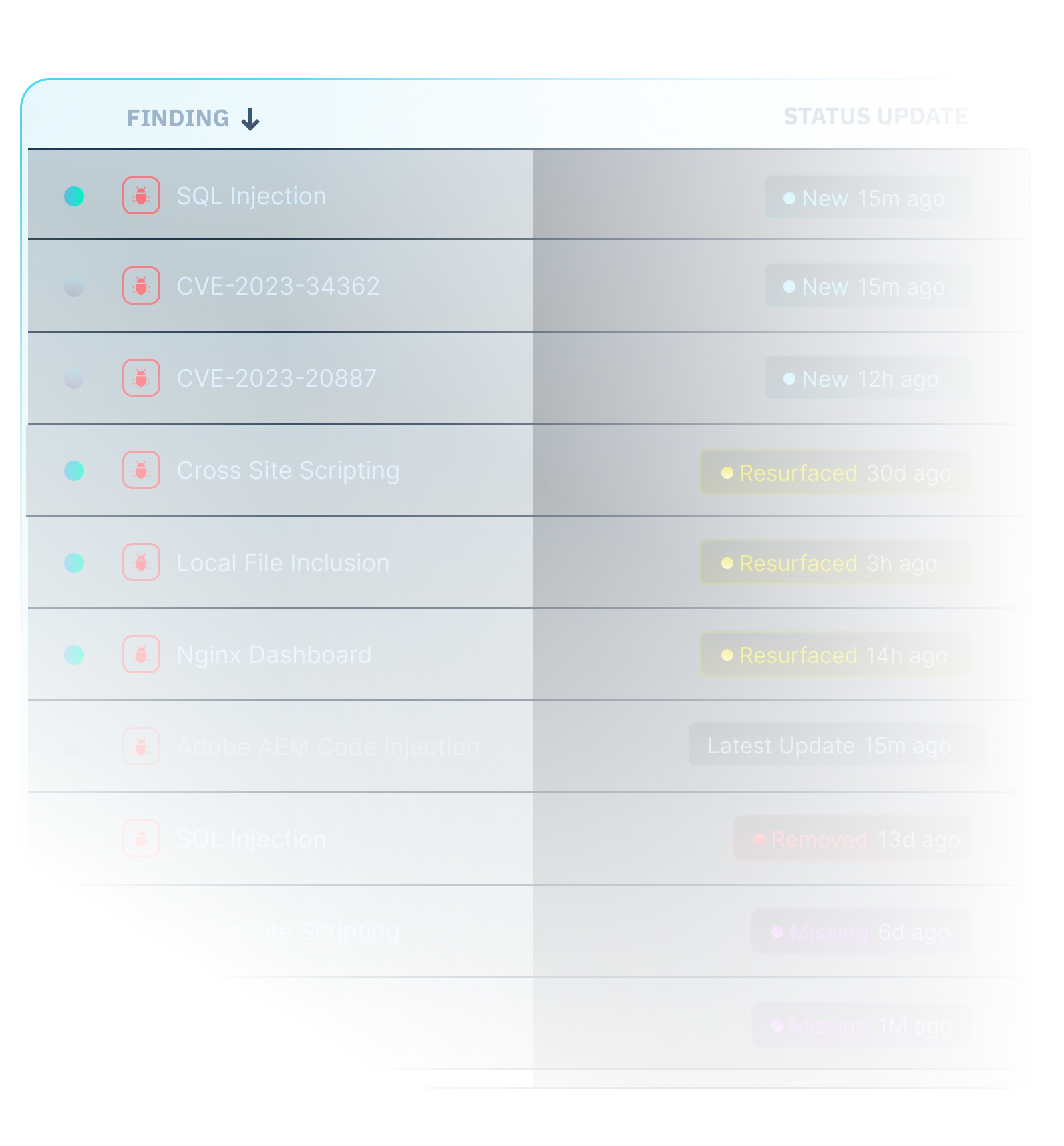
Centralize Vulnerability Management
Take control of your data. Centralize vulnerabilities, attack paths, secrets, directories, and endpoints into a single dashboard for comprehensive visibility into both your internal and external security posture.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
Explore more solutions
Discover other powerful solutions built to elevate your offensive security operations.