Subdomain Discovery via
DNS Brute Force
Use DNS brute force techniques to uncover unknown subdomains across your infrastucture, delivering always verified intelligence that drives proactive security and making you on top of emerging threats.
Why you should consider DNS Brute Force
Simulating attacker behavior for finding subdomains via DNS Brute Force leverages custom or built-in wordlists leading to internal systems, third-party integrations, and overlooked assets with verified, false-positive-free results—giving your security team the same insights attackers would use to exploit your infrastructure.

01 Tailored Infrastructure Discovery
Adapt to each organization's unique structure by using custom wordlists that align with internal naming conventions, ensuring comprehensive and relevant subdomain discovery.

02 Verified Assets
Eliminate false positives with cross-checked DNS results—if a subdomain is found, it definitively exists, providing your team with reliable, actionable intelligence.

03 Attacker-Driven Enumeration Tactics
Mimic real-world attacker techniques with DNS Brute Forcing module, exposing the same hidden assets and vulnerabilities adversaries target.
Why is DNS Brute Force Essential for ASM
It uncovers hidden subdomains and overlooked assets that traditional tools miss, revealing internal systems and third-party connections. This attacker-simulated approach delivers verified, false-positive-free results, ensuring complete visibility and greater security intelligence.
Infrastructure Discovery of Unknown Assets
Uncover all active and unknown subdomains across your organization's root domains using DNS brute force with custom or built-in wordlists. This approach thoroughly identifies internal systems, third-party integrations, and more, providing an accurate view of your external attack surface.


High-Fidelity Enumeration with Verified Results
Eliminate false positives by cross-verifying discovered subdomains with a curated list of trusted DNS resolvers and advanced wildcard filtering. This guarantees that every detected subdomain exists, delivering actionable intelligence that security teams can confidently prioritize and address.

Adversary Simulation for Real World
Mimic real-world attacker behavior by aggressively brute-forcing DNS records to uncover hidden and vulnerable assets. This proactive strategy allows security teams to identify and remediate the same weak points adversaries target, strengthening overall security posture before exploitation occurs.
High-Accuracy Discovery
Utilizes a daily validated resolver list and trusted cross-checks to ensure precise and reliable subdomain enumeration with minimal false positives.

Customizable Wordlist Support
Enhance discovery by using the built-in wordlist or uploading a custom list tailored to your organization's unique naming conventions.

Wildcard Filtering
Automatically filters out wildcard DNS records to eliminate false positives and deliver cleaner, more actionable results.

Hyperscalable Enumeration
Effortlessly brute-force subdomains across thousands of domains simultaneously, accelerating large-scale attack surface analysis.
How Discovery through DNS Brute Force Works
This module uses built-in or custom wordlists, cross-verifies results with trusted resolvers, and filters out false positives to provide accurate, actionable insights into your organization's external attack surface.
Provide Your Domains & Wordlists
Start by supplying a list of domains to enumerate. Use the built-in wordlist or upload a custom one tailored to your organization's naming conventions for more precise discovery.
- Unlimited Targets
- Custom Wordlist Support
- Hyperscalable & Fast Enumeration

Launch DNS Brute Force
Run the module to brute-force DNS records, uncovering valid subdomains using high-accuracy techniques.
- Validated Resolvers
- False-Positive Checks
- Wildcard Filtering
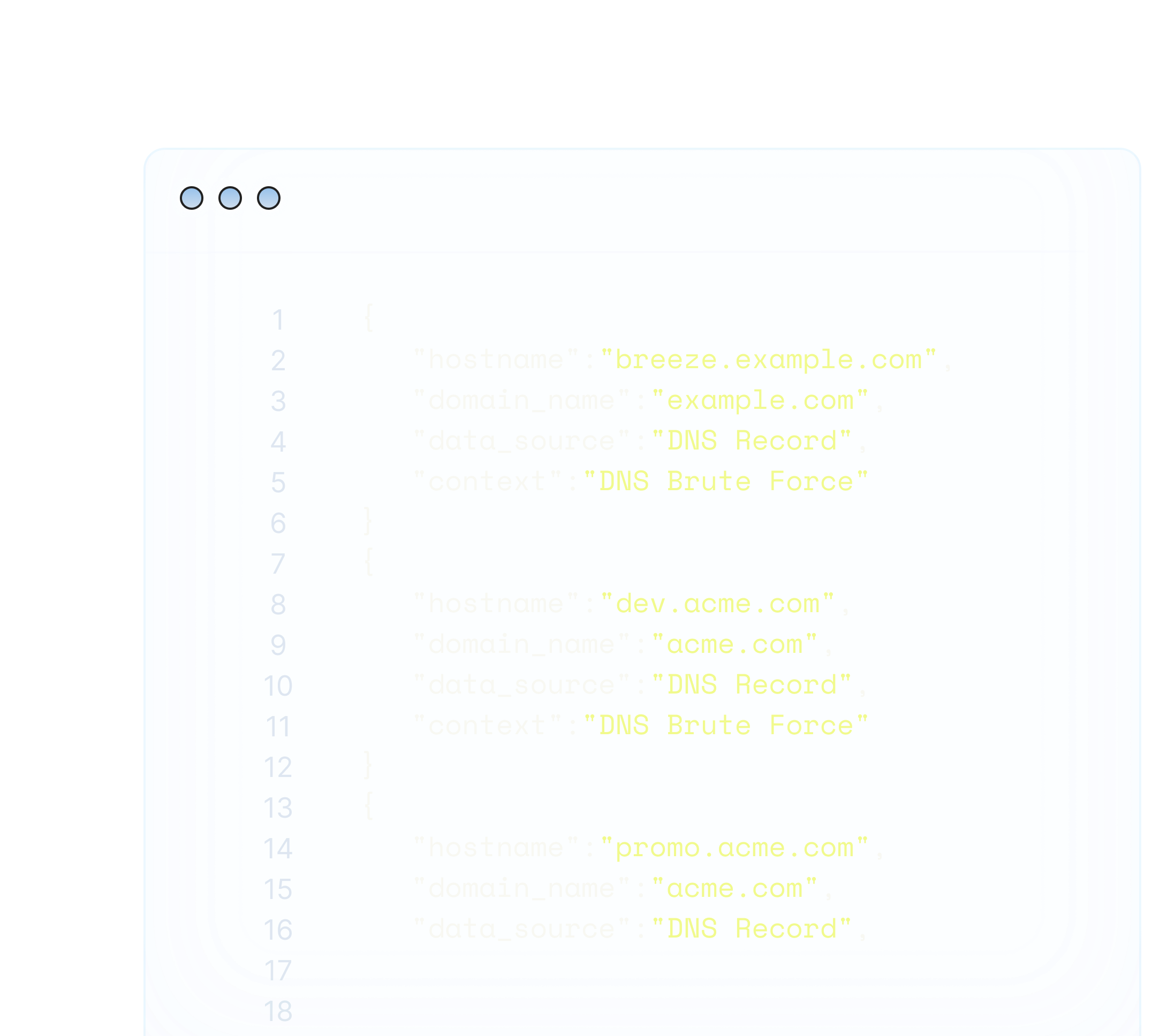
Review Results
Analyze the discovered subdomains in a structured format. Leverage detailed insights to detect hidden assets and enhance your security posture.
- Discovery Context
- Real-Time Updates
- Large Scale Enumeration

Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.