OSINT-Powered
Path Discovery
Leverage open-source intelligence to map and secure your digital infrastructure's hidden pathways.
Why OSINT Path Discovery Matters
Explore critical use cases for path discovery—identifying unknown attack vectors, uncovering high-risk exposures, and supporting stealthy Red Team operations to strengthen your application security.

01 Red Team Exercises
Enhance stealth in Red Team engagements with this module, which gathers valuable attack scenario insights without sending any requests to the target.




02 High-Risk Paths
Detect unauthenticated paths unique to your application that may expose sensitive data like PII, credentials, or payment details.

03 Unknown Attack Vectors
Detect unauthenticated paths unique to your application that may expose sensitive data like PII, credentials, or payment details.
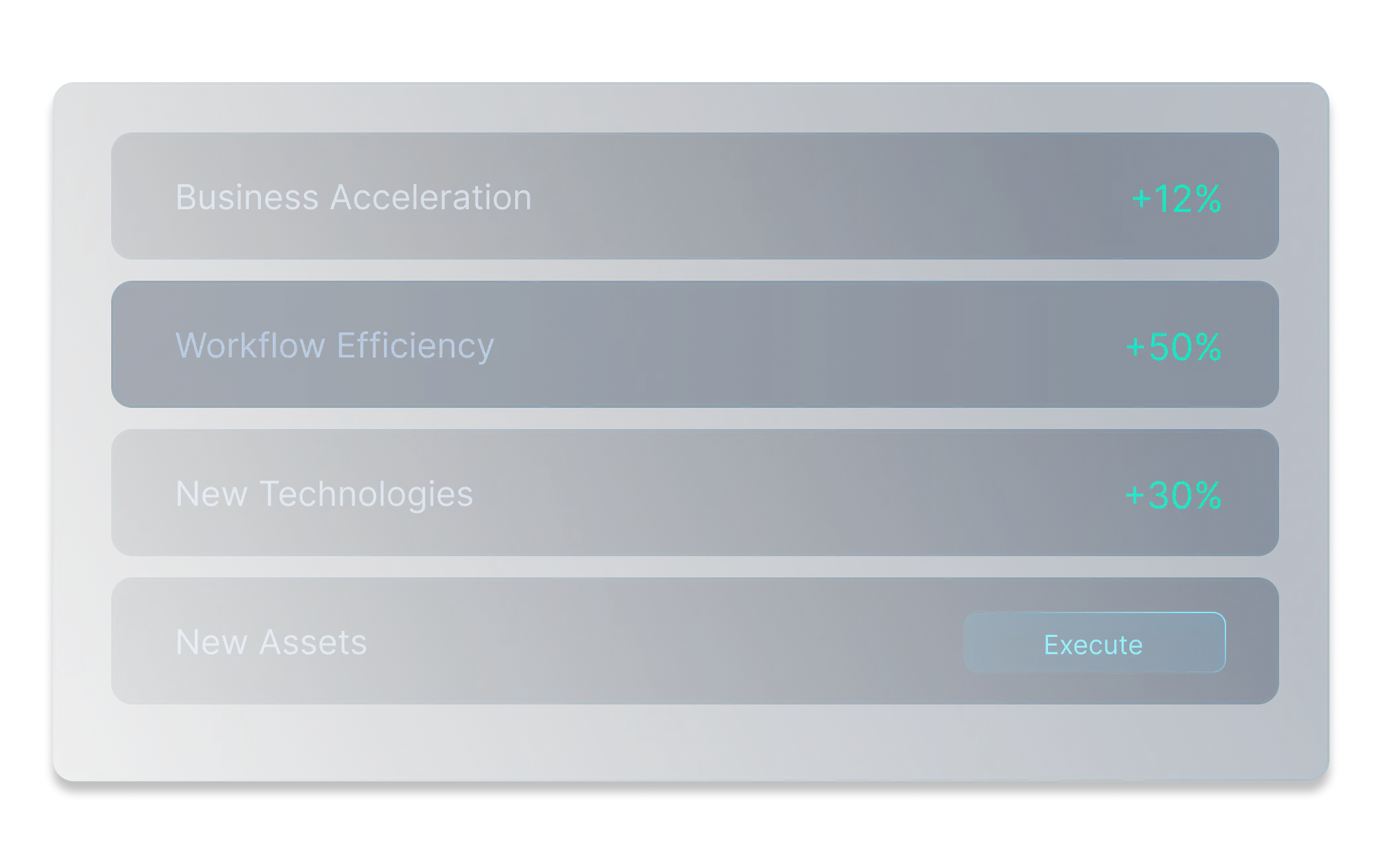
OSINT-Based Path Discovery for Enhanced Visibility
By leveraging OSINT-driven insights, organizations gain a broader perspective on their external landscape, supporting informed decision-making and reinforcing strategic security initiatives.
Protect Sensitive Data
Discover unauthenticated or exposed paths that can contain sensitive information like PII, credentials, or payment details, ensuring critical data remains secure.
Accelerate Security Operations
Support Red Team operations with stealthy path discovery, gathering valuable intelligence without interacting with the target, enabling realistic attack simulations.

Uncover Hidden Vulnerabilities
Identify overlooked attack vectors and high-risk paths unique to your applications that traditional scanners fail to detect, reducing the risk of exploitation.

Historical Data
Gain continuous insight into previously identified endpoints through consolidated historical data, ensuring that legacy or abandoned paths aren't left as lingering vulnerabilities.

Cleaning & Normalization
Automatically standardize URLs so they're consistent and ready for analysis, eliminating the need for manual, time-consuming data preprocessing.

Scalability
Effortlessly handle discovery tasks for thousands of hosts and web applications in parallel, enabling faster, more comprehensive external footprint assessments.

Built-In Integrations
Seamlessly integrate with diverse OSINT APIs to streamline content discovery workflows, ensuring a more efficient and thorough path enumeration process.
How OSINT Path Discovery Works
Explore critical use cases for path discovery—identifying unknown attack vectors, uncovering high-risk exposures, and supporting stealthy Red Team operations to strengthen your application security.
Enter Any Web Target
Leverage Trickest's OSINT path discovery so no paths get missed on any amount of targets you own.
- Target Agnostic
- No Asset-Based Pricing
- Parallel Processing

Get Endpoint Data Your Way
Integrate with your existing APIs, adjust everything to fit your team's workflow, and rely on consistently organized data to move from discovery to action in no time.
- Native API Integrations
- Fully Customizable Data
- Normalized & Structured Data
- Context Awareness

Extract Security Insights
Explore the output in a structured format, including detail path records with appropriate context where the path came from.
- Historical Data
- Status Processing
- Billions Of Records

Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.