OSINT-Powered
Hostname Discovery
Uncover hidden & shadow hostnames with OSINT-driven insights—mapping your target's domain landscape inside-out while maintaining a stealthy, passive footprint.
Why OSINT Hostname Discovery Matters
Subdomain discovery isn't just about finding unknowns—it's about gaining a complete view of your infrastructure, running stealthy Red Team operations, and seeing exactly what attackers see, so you can remediate risks before they turn into real threats.

01 Holistic Infrastructure Awareness
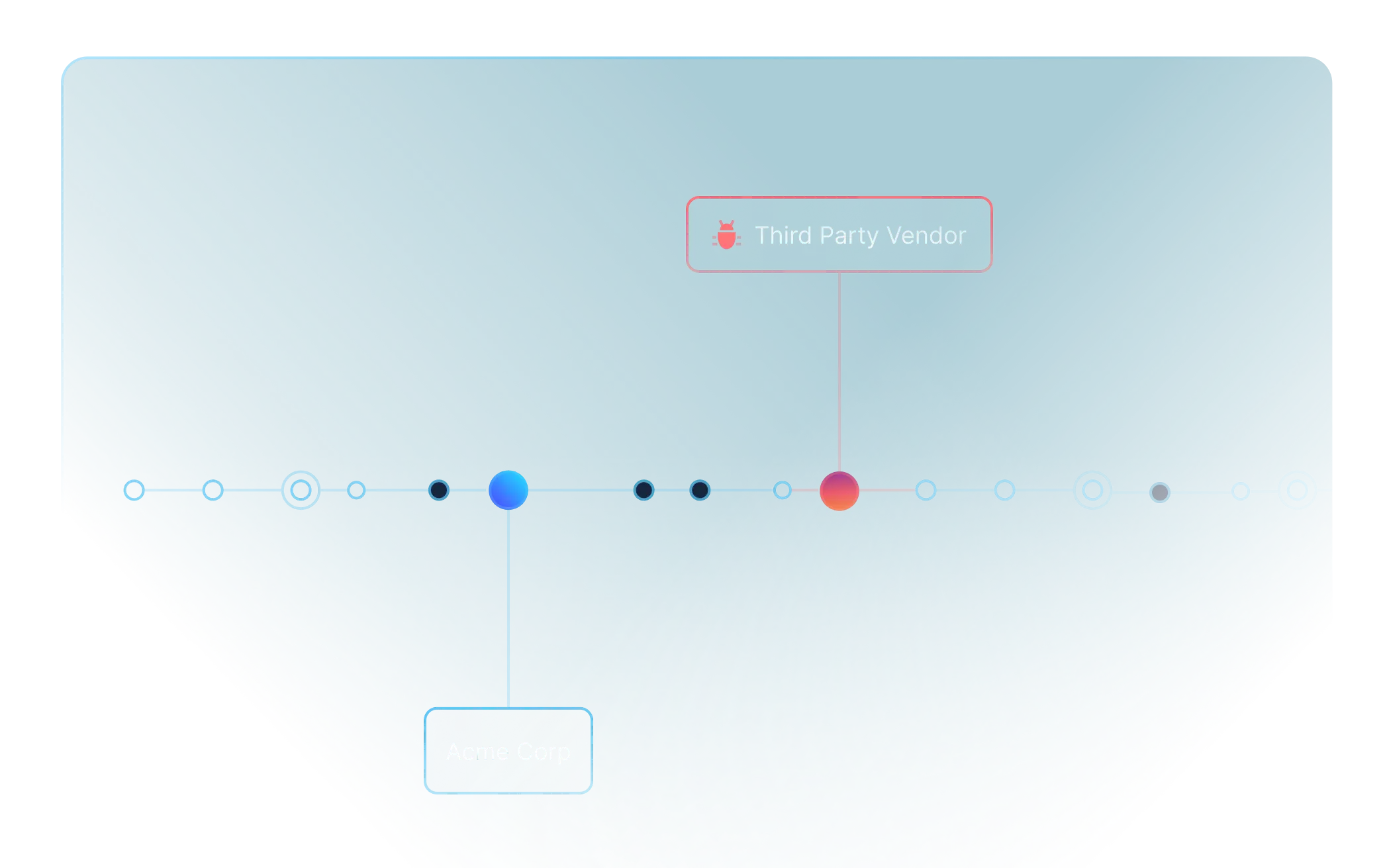
Identify not just your own subdomains, but also connections with third-party vendors, subsidiaries, and related external assets—revealing your full online footprint.

02 Stealthy Red Team Operations
Gather intelligence passively from OSINT sources without probing the target directly, keeping your red team operations undetected and low-profile.

03 Attacker's Perspective Insights
See exactly what external parties and potential adversaries can learn about your infrastructure, helping you prioritize and find unknown assets before they become real threats.
How you can leverage OSINT Hostname Discovery
Leverage diverse OSINT sources to reveal hidden subdomains and wildcard entries, enriching or validating your existing domain knowledge. Provide basic details or integrate optional APIs, then explore structured results that highlight potential vulnerabilities and guide more focused security strategies.
Comprehensive Attack Surface Mapping
Identify all domains, subdomains, and related external assets—including third-party and subsidiary connections. By revealing every potential doorway into your infrastructure, this use case helps ensure no obscure endpoint or orphaned resource is left unprotected.

Covert OSINT-Based Red Team Operations
Gather intelligence from wide range of APIs without probing the target directly. This maintains a low profile, allowing red teams to find information for stealthy attacker scenarios without triggering alarms.

Adversarial Exposure Evaluation
Determine exactly what assets are exposed from an external adversarial viewpoint. Figure out different connections between domains, third party vendors and cloud environments.
Comprehensive OSINT
Leverage a carefully curated set of passive data sources to maximize subdomain and hostname discovery, ensuring that no critical endpoints slip through the cracks.

Scalable Multi-Domain Processing
Effortlessly handle domain enumeration at scale—process thousands of domains in parallel without sacrificing performance or accuracy.

Extended Discovery Scope
Identify not only subdomains but also related hostnames and extra root domains, giving you a more complete view of your external attack surface.

Actionable Output & Insights
Generate detailed discovery logs that highlight which sources contributed each finding, enabling deeper investigations and more confident security decisions.
How OSINT Hostname Discovery Works
Leverage diverse OSINT sources to reveal hidden subdomains and wildcard entries, enriching or validating your existing domain knowledge. Provide basic details or integrate optional APIs, then explore structured results that highlight potential vulnerabilities and guide more focused security strategies.
Provide Your Domains & Configuration
Start by supplying the target domains you want to investigate. Optionally, include API keys for any OSINT data sources you'd like to enhance your results.
- 100k+ Domains Support
- Optional API Keys Integration
- Easy Setup

Launch Passive Enumeration
Once your inputs are ready, run the module to systematically uncover subdomains, wildcard entries, and related hostnames.
- Built-in OSINT providers
- Unlimited Domains
- Normalization and Deduplication

Review & Act on Insights
Explore the output in a structured format, including detail records and aggregate lists. Identify new attack surfaces, confirm known subdomains, and refine your threat intelligence.
- Source Context
- Status Processing
- Third Party Vendor Connections

Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.