Introduction
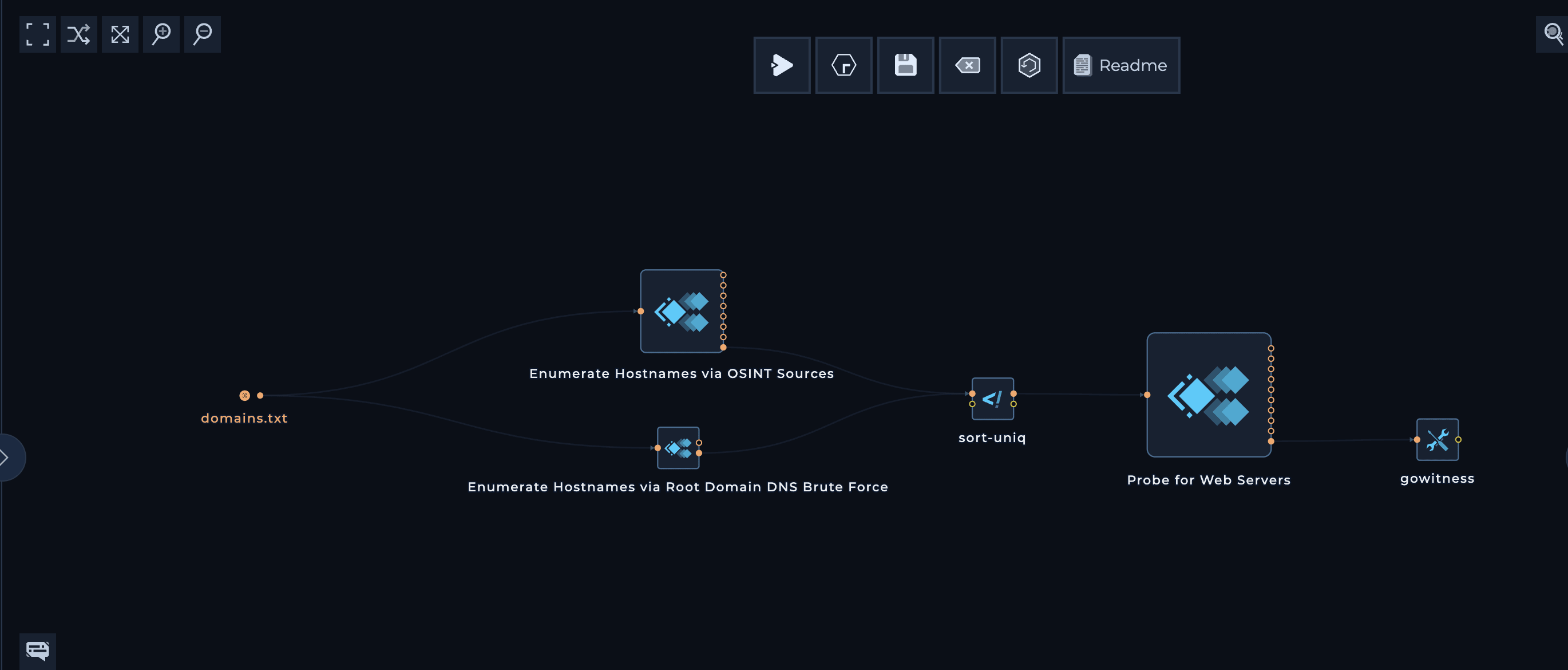
Modules are tools that help automate specific security tasks. Whether it’s discovering assets (like hostnames), enriching asset details such as port scanning IP addresses, or running vulnerability scans, modules handle the heavy lifting. They take care of the implementation details, evolving methodologies, maintenance, scalability, and low-level resource management, allowing you to focus on what needs to be done rather than how to do it.Getting Started
Modules are available in the Trickest library alongside tools and scripts. Find them under theModules section in the library sidebar or search for specific ones using the search bar.