Meet Trickest Query Language™: Unlock Deep Security Insights
Unify and analyze complex security data easily with the Trickest Query Language™. Discover how customizable filters and advanced queries can elevate your vulnerability management and help you prioritize threats efficiently.
In offensive security, dealing with multiple, often fragmented data sources can quickly become overwhelming. Data from various tools—especially custom command-line ones—usually comes in non-standard formats, creating complex layers that are hard to interpret.
Security teams find themselves spending hours manually reformatting and cross-referencing data, time that could be better spent discovering innovative ways to identify vulnerabilities or build powerful workflows.
Introducing the Trickest Query Language™
Trickest has developed a new query language to cut through the complexity of offensive security data. Built specifically for security professionals, this query language enables efficient, precise filtering across the biggest datasets, transforming the way you interact with your data. No matter the source or format, you can now apply intricate, multi-condition filters to make sense of everything from high-level summaries to the most granular details.
Imagine the possibilities:
- Targeted Insights: Dive deep into impacted assets, key vulnerabilities, or possible threat vectors.
- Confident Prioritization: Focus on critical issues without being overwhelmed with extreme data volumes.
- Boosted Team Collaboration: Share custom views and insights to keep everyone in the team on the same page.
The Power of Trickest Query Language™
The Trickest Query Language provides security teams with unparalleled control over their data. This language turns diverse, large datasets into actionable intelligence, far beyond basic filtering capabilities.
Intuitive Syntax for Complex Queries
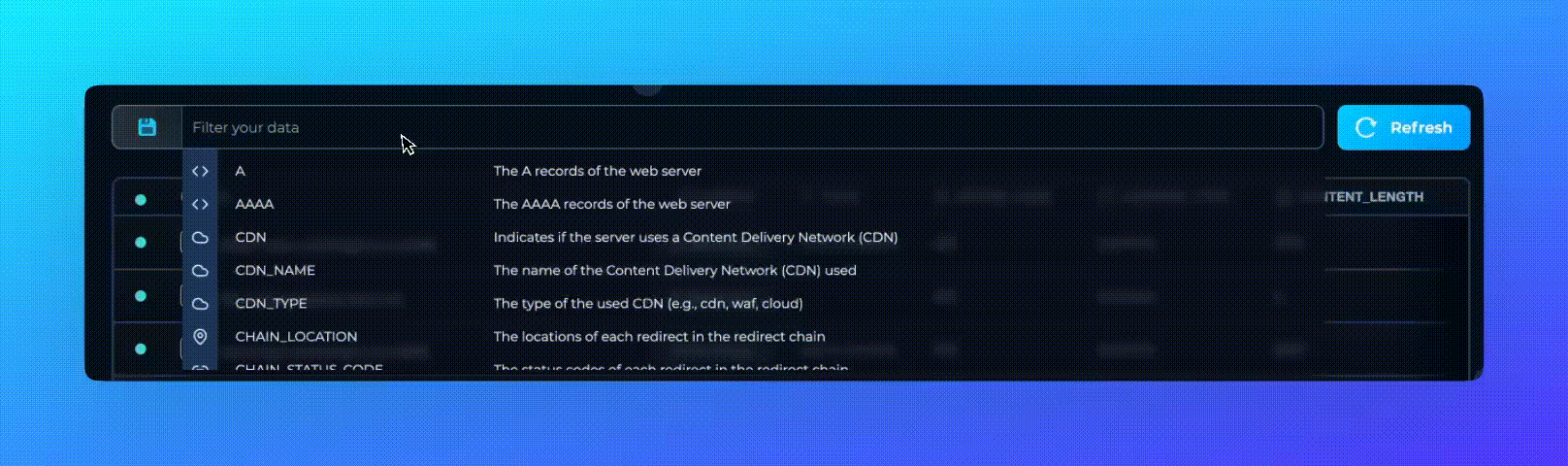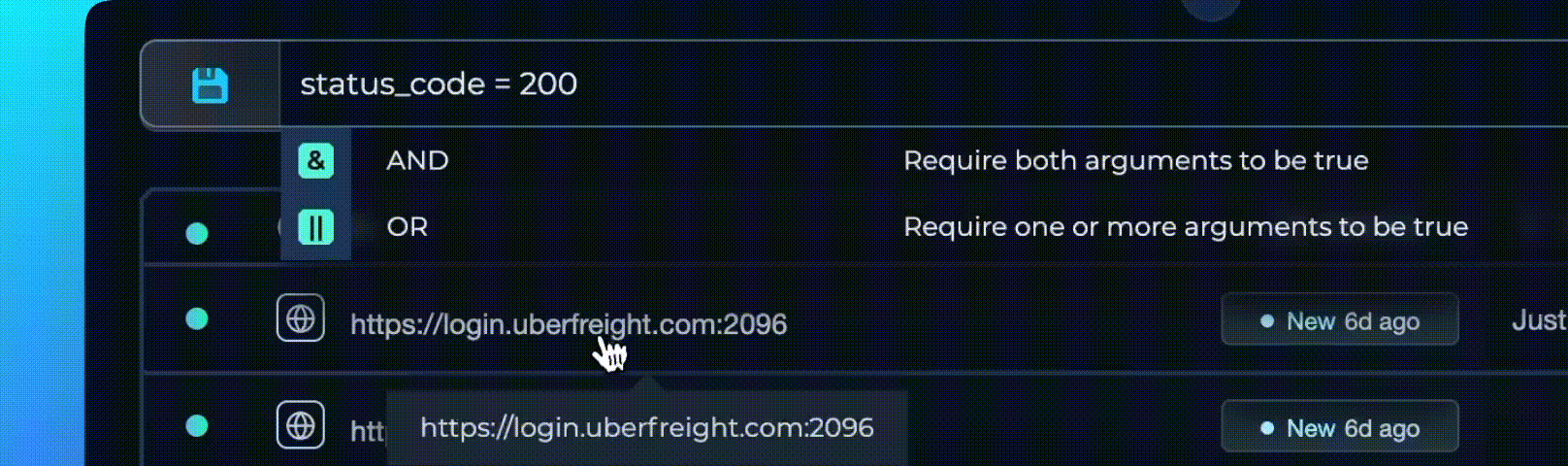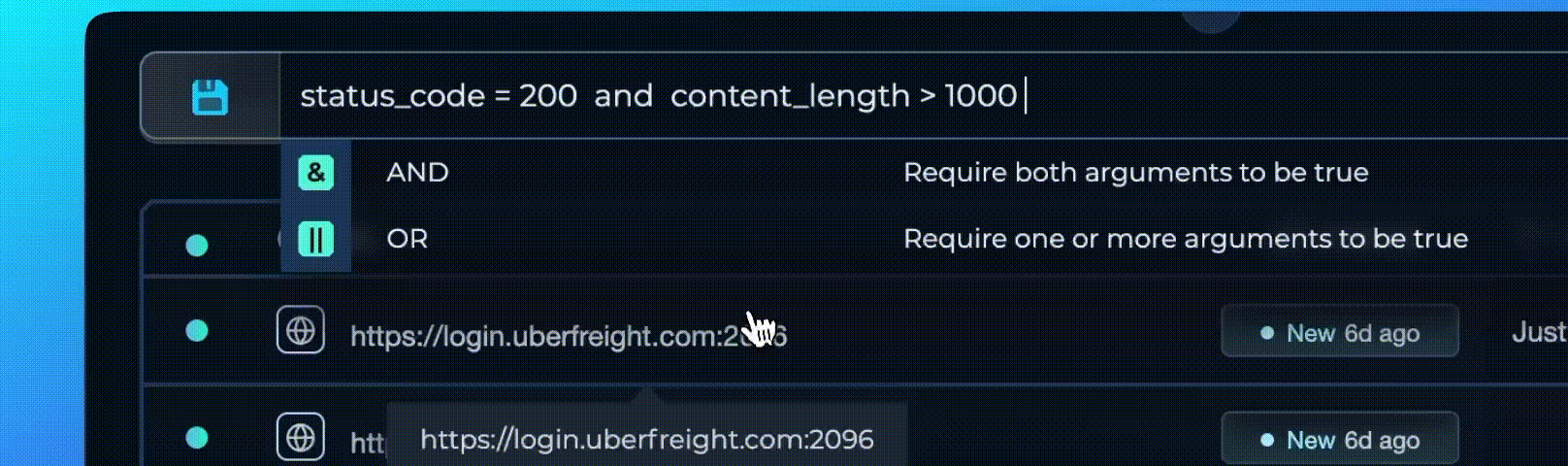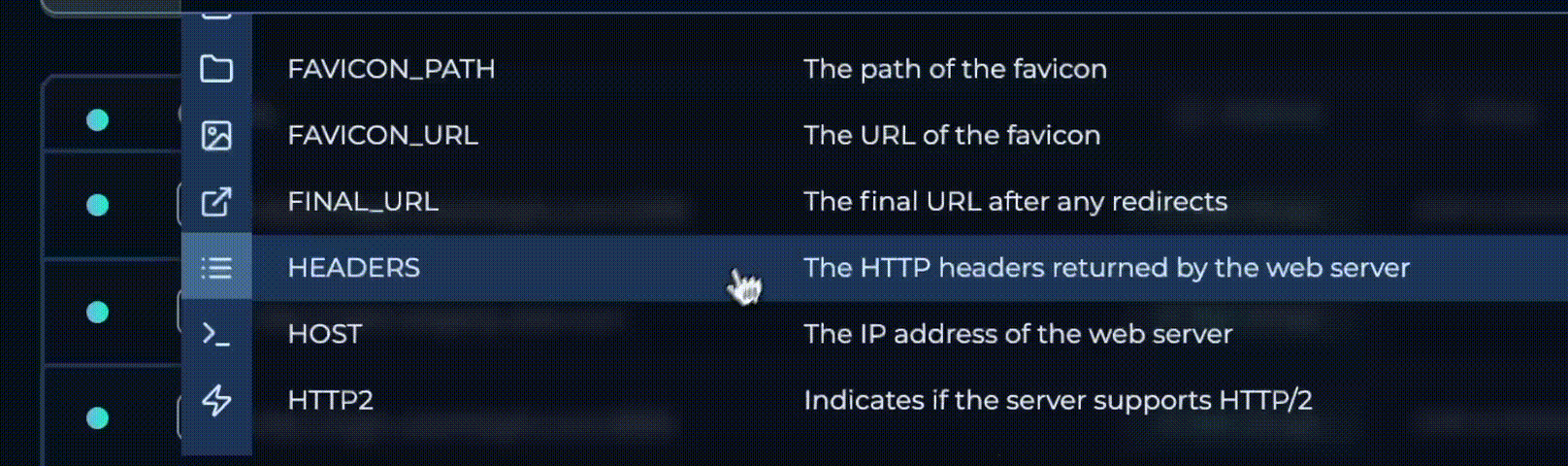
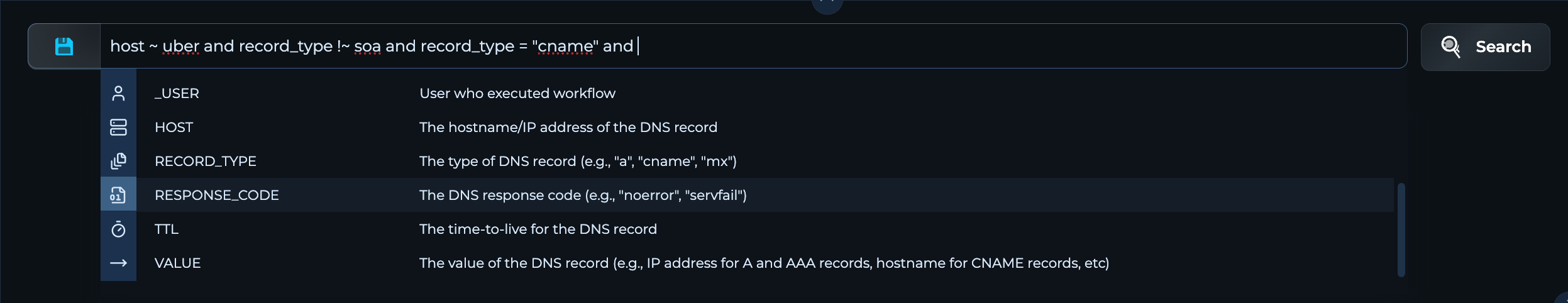
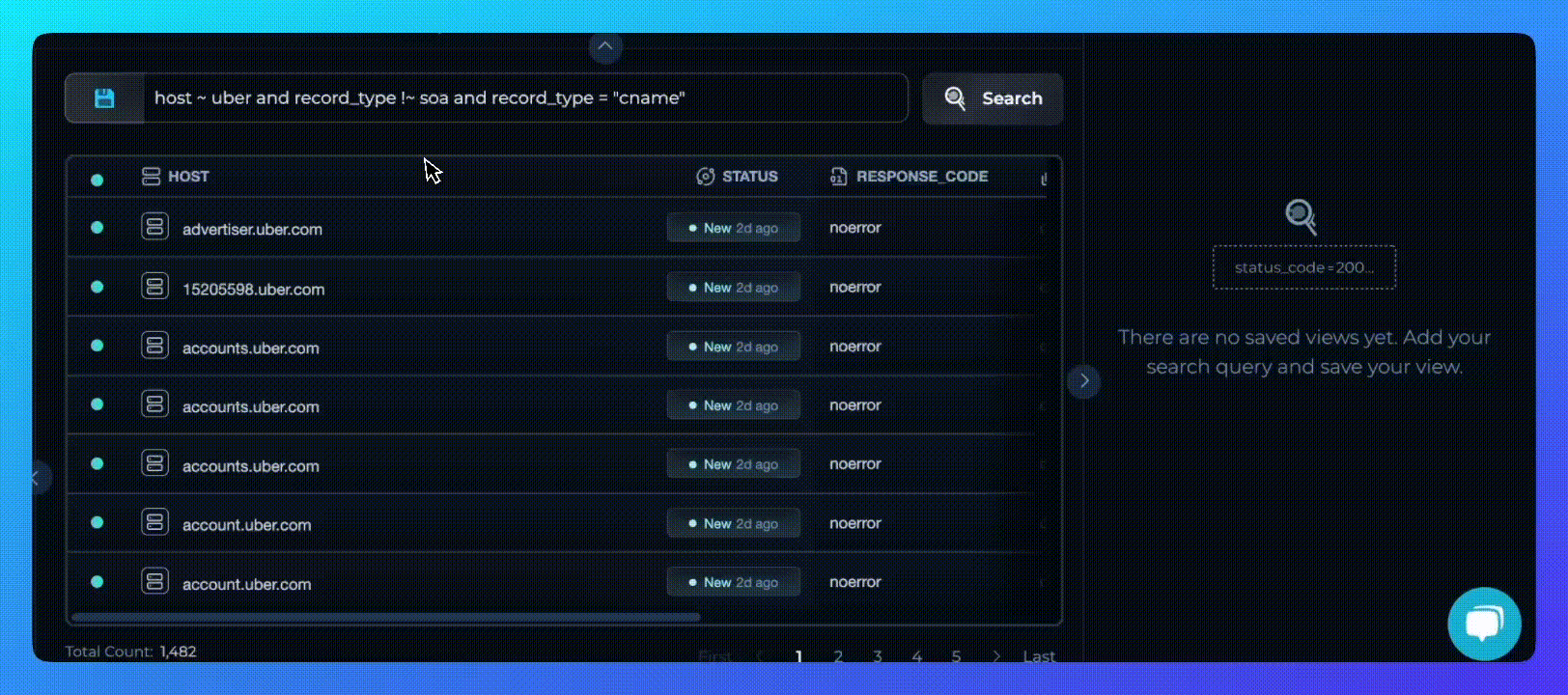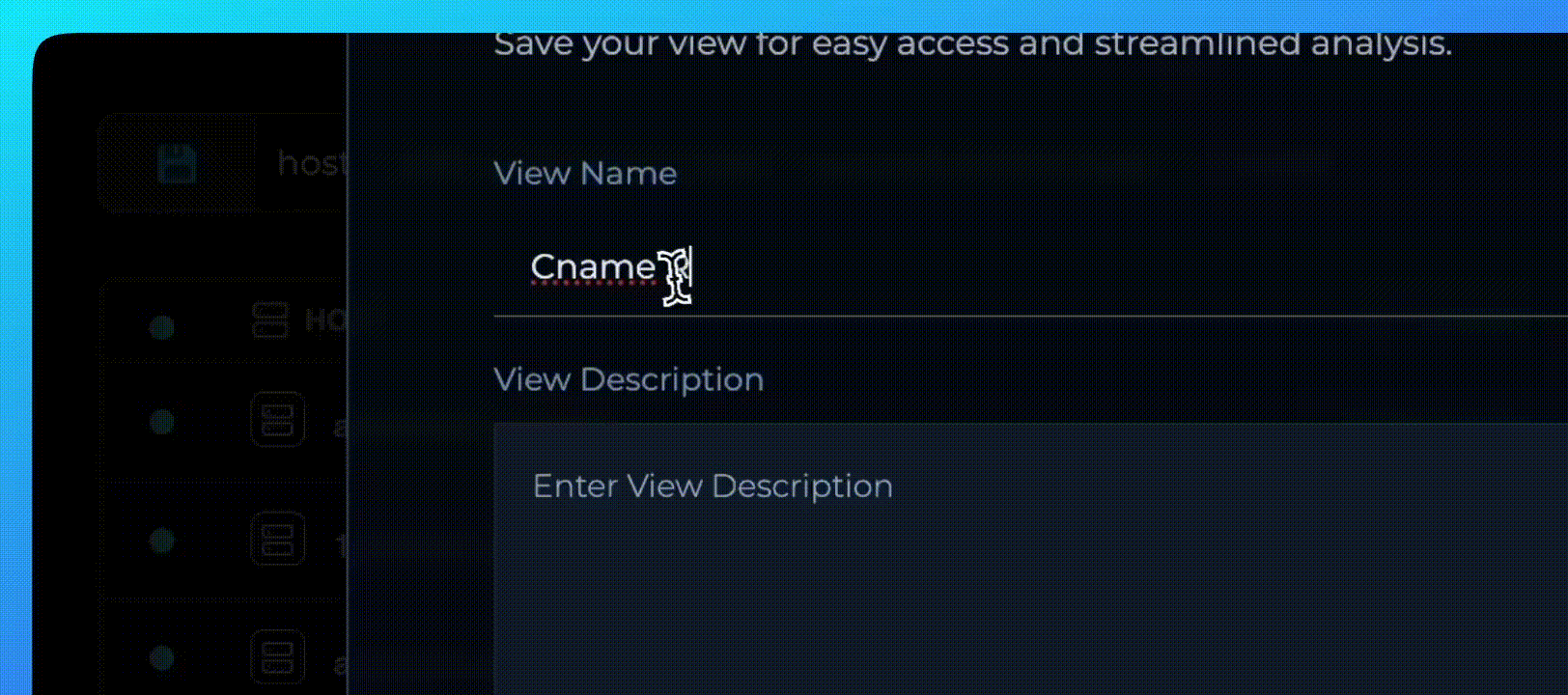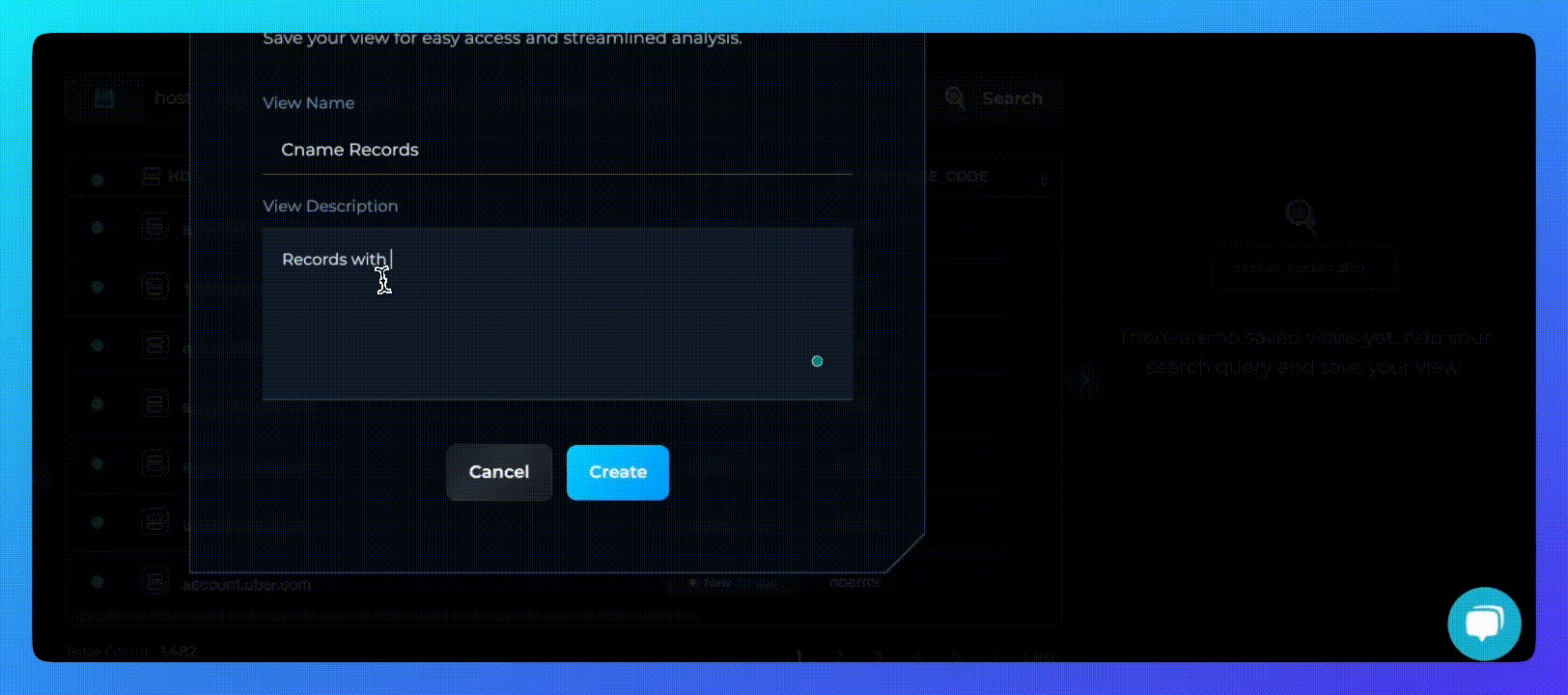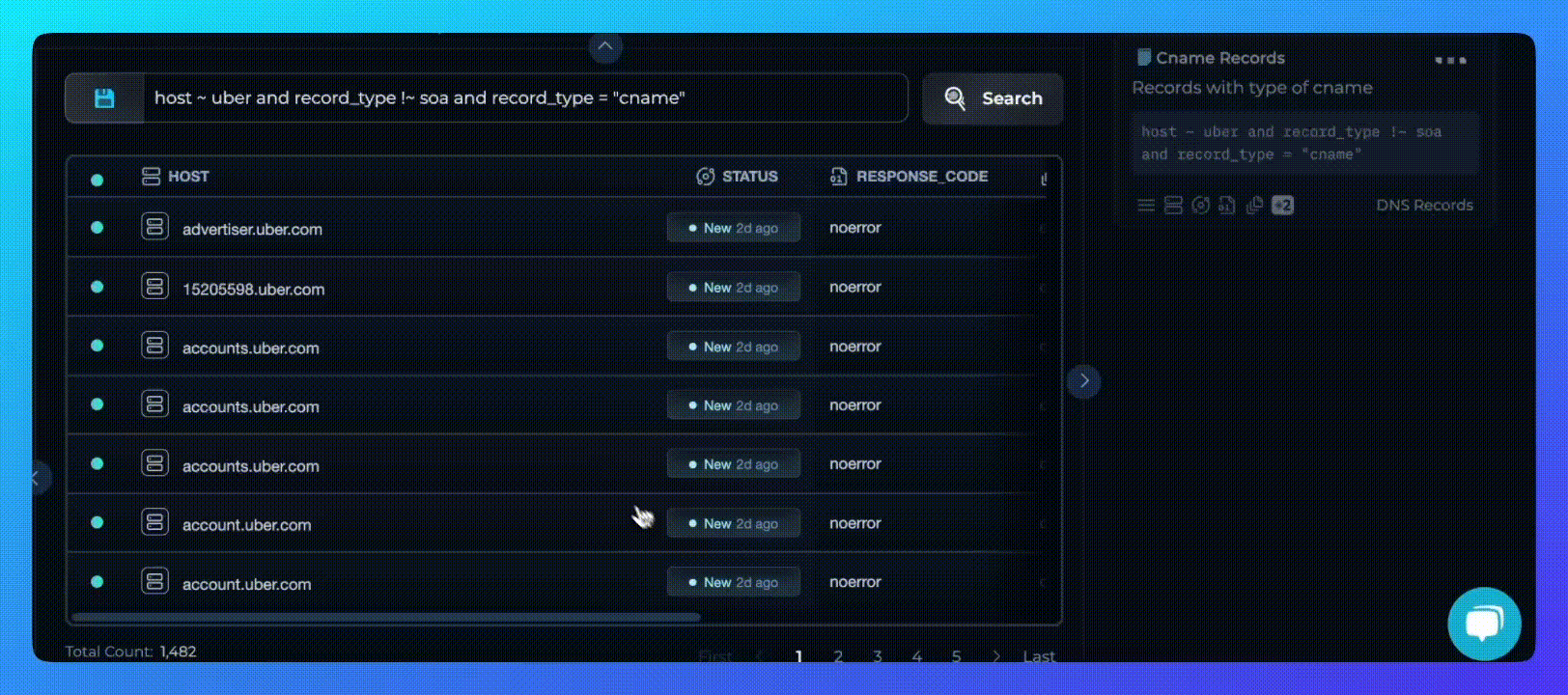
The Trickest Query Language™ uses a simple, intuitive syntax that feels natural yet is powerful enough for complex data queries. With easy-to-use operators and logical connectors, you can build queries that precisely target the information you need.
- Field-Based Conditions: Specify exactly what you're looking for by setting conditions on any data field. For example,
status_code = 200quickly filters for successful HTTP responses. - Comparison Operators: Use
=,!=,>,<to precisely define conditions. Need to find assets with high response times? A query likeresponse_time > 1000gets you there. - Pattern Matching with Regex: Leverage regex pattern matching (
~) or negative regex matching (!~) to search for patterns within your data. This is invaluable when dealing with complex strings. Need a search for vulnerable SSH Versions?
port = "22" and banner ~ "SSH-2\\.0-
OpenSSH_(8\\.5p1|8\\.6p1|8\\.7p1|8\\.8p1|8\\.9p1|9\\.0p1|9\\.1p1|9\\.2p1|
9\\.3p1|9\\.4p1|9\\.5p1|9\\.6p1|9\\.7p1|[5-9]\\.[5-9]p1|9\\.[0-3]p1)(?:\\s|$)"
Combine Conditions with Logical Connectors
The Trickest Query Language™ lets you combine multiple conditions using AND and OR for precise, nuanced filters.
- Narrow Down Results:
status_code = 200 AND content_length < 1000helps you find lightweight responses that succeeded, possibly indicating minimal content or redirects. - Broaden Your Search:
port = 80 OR port = 443ensures you look at standard web service ports, capturing HTTP and HTTPS traffic.
Creating Custom Views for Focused Analysis
With the new solutions interface, you can fine-tune which data fields are shown in your results. Customize your insights by selecting only the relevant fields.
- Precision-Focused: Choose relevant fields, like
ip_address,ports, and more, to reduce noise and sharpen insights. - Simple Organization: Use drag-and-drop to arrange your view, ensuring the most crucial data is always at hand.
Enabling Security Teams with Deep Insights
The real value of Trickest Query Language™ is in turning raw data into meaningful insights.
- Focus on Critical Threats: Use targeted filtering and sorting to prioritize pressing issues and address key vulnerabilities faster.
- Uncover Hidden Patterns: Advanced queries help uncover trends or anomalies that standard filters might overlook, like spikes in failed logins from specific IPs.
- Strengthen Team Collaboration: Share custom queries and custom data views with your team to ensure alignment on insights and methodologies.
Practical Examples
To illustrate the versatility of the Trickest Query Language™, consider these scenarios:
- Identify Exposed Services:
port != 80 AND port != 443helps you find services running on non-standard ports, which could be unintentionally exposed to the internet. - Detect Specific Vulnerabilities:
vulnerability_id = "CVE-2021-44228"quickly isolates assets affected by a known vulnerability like Log4Shell. - Monitor Asset Changes:
last_seen < "2023-01-01"allows you to find assets that haven't been scanned recently, highlighting potential blind spots in your security posture.
Integration with Your Workflow
The Trickest Query Language™ is built for smooth alignment with your existing security processes.
- API Access: Automate queries and feed results directly into your tools or dashboards with our RESTful API.
- Historical Comparison: Compare current data with historical snapshots, enabling quick identification of new or recurring issues.
Conclusion
Security data should empower your strategy, not complicate it. The Trickest Query Language™ transforms complex data analysis into an efficient, streamlined process, providing security teams with a powerful, user-friendly interface. With TQL, teams can dive deep into infrastructure and vulnerability data, extract critical insights, and quickly respond to new threats, turning data management into a strategic advantage.
Experience the difference the Trickest Query Language™ can make for your team. Contact us for a personalized demonstration, and see how this innovative approach can transform your offensive security, turning data overload into actionable insights.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
