The Hidden Pitfalls of ASM: Navigating the Gaps Between Enterprise and DIY Solutions
Explore the pitfalls of relying solely on ASM platforms and the benefits of a hybrid approach combining custom solutions with enterprise tools. Learn how to optimize your security system for long-term scalability and efficiency.
I used to believe that staying ahead in cybersecurity was just about keeping up—reading the latest research, attending conferences, monitoring threat intelligence, and testing every new tool. But in reality, knowing isn't enough—the real challenge is turning that knowledge into meaningful action across your systems.
Here’s a story that might sound familiar.
When Your ASM Fails You
You invest in a top-tier attack surface management (ASM) platform—polished, feature-rich, scalable, and backed by excellent support. On paper, it covers all your needs.
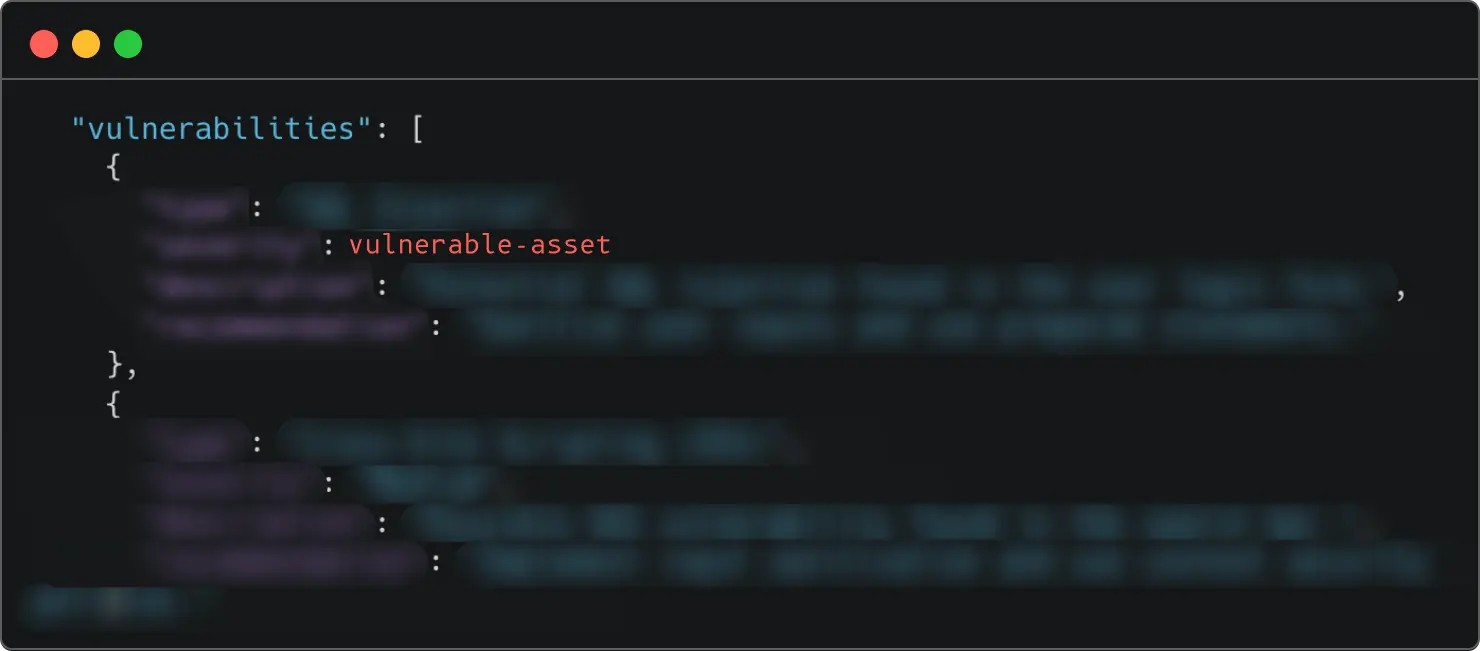
Then one day, during routine manual testing, you stumble upon a vulnerability—a glaring oversight, a simple, low-hanging fruit.
You check your asset inventory—the affected asset isn’t even listed.

Frustrated, you reach out to support. As you wait for an explanation, the question gnaws at you: How did my ASM miss something so obvious?
So, you test an open-source tool you’ve trusted for years. Within minutes—there it is, the missing asset.
Taking Matters Into Your Own Hands
After encountering one too many blind spots across different vendors, you’ve had enough.
You build your own solution—custom-tailored to your organization’s needs, designed with the precision that no off-the-shelf tool could match. And for a while, it works beautifully.
- It detects what commercial tools missed.
- It incorporates ideas you once suggested to vendors—ideas they ignored.
- It feels like the perfect fix.
Sure, the upfront costs were high, but the ROI seemed undeniable—your system was built for you, by you.
Until It Starts to Crack…
As your organization grows, so does your attack surface. New assets onboard daily, configurations change, and soon, your once-perfect system struggles to keep up.
- Detection gaps start appearing.
- Vulnerabilities slip through.
- Data processing bottlenecks slow everything down.
What was once your security ace-in-the-hole is now a resource drain. Maintenance consumes more and more time, and innovation slows to a crawl.
The Breaking Point
Leadership steps in. "Is this sustainable?" they ask. The enterprise tool covers most of our needs.
-
Is maintaining this custom-built solution worth the cost?
-
Should we be focusing resources elsewhere?
At this point, you face a hard choice:
- Do you double down and try to salvage your system? Or do you return to the enterprise solution you worked so hard to replace?
Finding the Balance
The goal isn’t to choose all-in on custom or all-in on off-the-shelf—but to strike the right balance between flexibility and stability.
The ideal approach? A hybrid model.
- Modular, flexible components that allow customization without overcomplicating.
- Enterprise tools that provide a stable, scalable foundation.
- Integration with essential security tools for visibility, infrastructure management, and collaboration.
Final Thoughts
ASM isn’t about choosing one path—it’s about adapting. The best approach isn’t just what works today, but what will continue working tomorrow.
Are you building a system that traps you in endless maintenance or the one that scales?
Discover how to combine the agility of in-house methodologies with the stability of enterprise solutions—talk to us to find the perfect balance.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
