Easy Automation with Hakluke: Creating Serverless, Nocode Security Workflows
Creating automation for hacking workflows is satisfying, but complex. In this article, hakluke creates basic recon and scanning automation with Trickest in less than 30 minutes, without writing any code or managing infrastructure!
Creating automation for hacking workflows is satisfying, but complex. It typically requires some coding knowledge or, at minimum some bash fu, and some knowledge about setting up infrastructure.
Trickest gives you the ability to create complex automation workflows without doing any coding or setting up any infrastructure.
In this article I'm going to walk through the process of setting up a Trickest workflow that performs subdomain recon and then gathers the name servers associated with each discovered host. This is a task that I perform manually quite often when I'm searching for DNS takeovers.
The Setup
First we create a new space to house our workflows. Click "Create Space".

Name the space, and optionally set a description for your own use. Click "Create".
Next, choose a name and optionally a description for your workflow, click "Create".
You should now have a space with a single empty workflow in it.

Click on the workflow pane, then click the "Open Workflow" button. You will be greeted with the workflow builder. This is where the fun begins! 🎉
The Workflow Builder
The Trickest workflow builder allows us to build out security workflow automation by visually connecting nodes together. Each node is either an input source (string, file, boolean value or folder) or it is some kind of processor, like a tool or script that will act on the input passed to it.
Adding An Input Node
To start, let's create a file node, which will contain our hostnames. To do this, we click the inputs tab on the left pane:

Then we drag a File node to the builder:
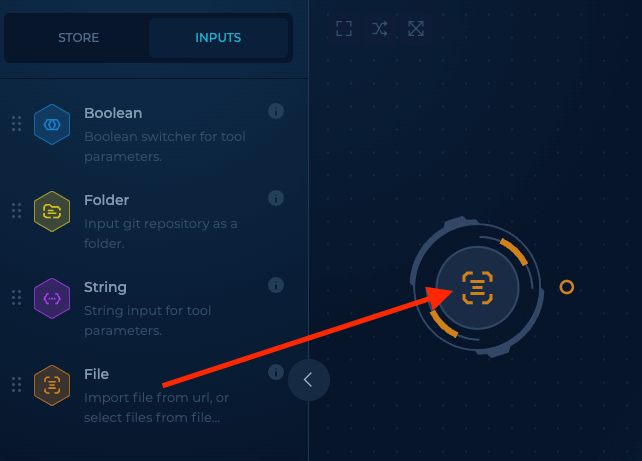
If you click the newly created node, you will note that options for that node display in the right pane:
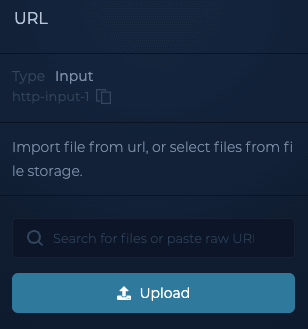
I created a file called rootdomains.txt on my local machine, and then uploaded it to this node.

The file contained two root domains, separated by a line:
trickest.com
trickest.io
Adding Some Subdomain Enumeration
Now that we have some root domains to work with, I created a subfinder node by clicking on the "Library" tab, searching "subfinder", and then dragging the subfinder node to the workflow builder. Subfinder is a tool that takes root domains as input, and finds associated subdomains, which is exactly what we will be doing.
You will note that when you hover your mouse over the subfinder node, you will see a bunch of coloured text pop up. These are inputs and outputs. The list on the left are all inputs, and the list on the right are outputs.
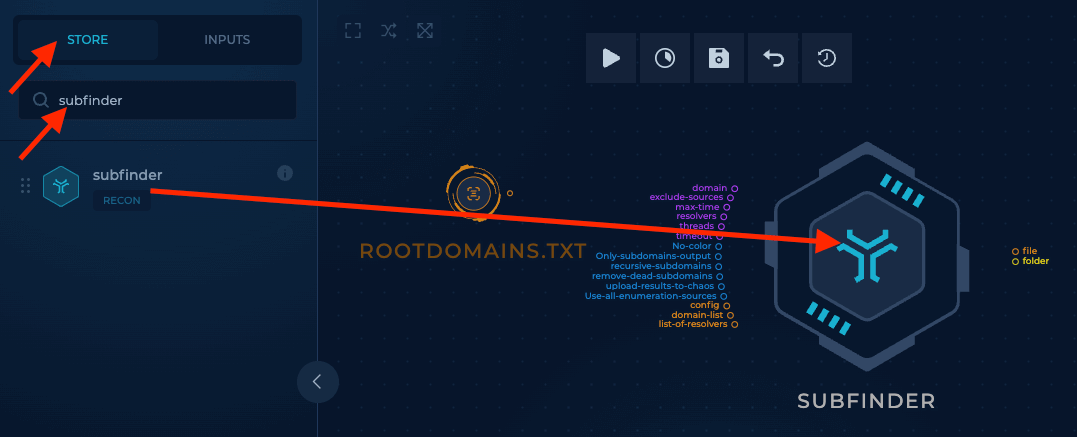
Purple items accept string input, blue accept boolean values and orange accept files.
We can provide the rootdomains.txt file we created earlier as input to subfinder by simply drawing a line between the output of rootdomains.txt and the domain-list file input on the subfinder node:
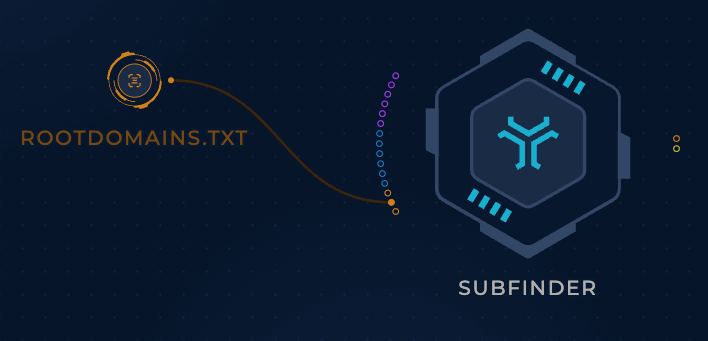
Finally we've connected our first two nodes! Hopefully you can start to see the power of Trickest, and the possibilities of more complex workflows are starting to form in your brain.
We can now click "Execute" to test out our workflow so far. Trickest will provide some options for different types of servers to run the nodes on. As this is a simple workflow, the defaults are fine.

While the workflow is running, we're able to watch the output for each node while it runs by navigating to the output, stdout or stderr tabs in the pane at the bottom.

We have successfully created and executed our first workflow!
We did get a bunch of informational output in the terminal, like some subfinder ASCII art, but we can set the only-subdomains by connecting it to a boolean node, and then connecting it up to the relevant subfinder option. This is the equivalent of specifying a boolean command-line flag for the tool:
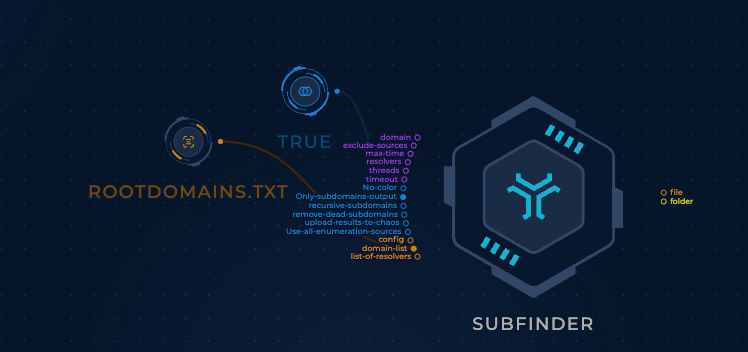
Now that we have this option set, next time we execute the workflow, the output of the subfinder node will just be a simple list of subdomains.
Performing NS Lookups
Next, let's add a DNSx node, which will be used to perform NS DNS lookups on each host. It's as simple as dragging the output of the subfinder node to the input of the DNSx node, and then using another boolean node to set the DNSx options that we require.
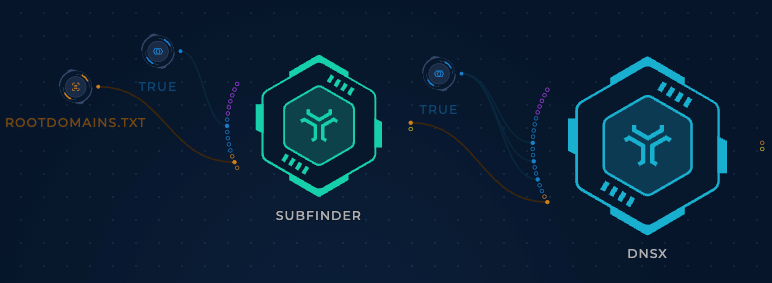
If we execute the workflow again, we get a list of hosts and their associated NS records.
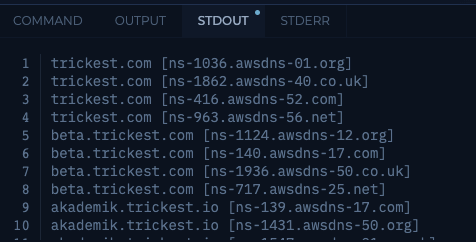
Voila! We have achieved our goal.
Going Further
Of course, this is a tiny, basic example of what is possible with the Trickest platform. If we wanted to expand our recon a little further, what else could we do? Here are a few examples:
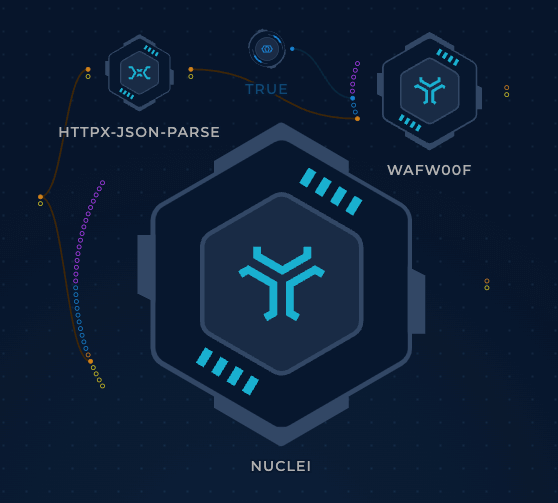
We could also send the subfinder output to HTTPx to perform HTTP probes and tech detection:

Want to know what WAFs the target might be using? You could pipe the output of HTTPx to wafw00f!

Want to introduce some vulnerability scanning? Why not also pipe the output of HTTPx into Nuclei?
What's Next?
Integrations
Along with being able to add more complexity to the workflow, we could also start integrating with 3rd party services - for example, we could have the results of these nodes pushed to a GitHub repository - or read the initial root domains from one.
That way - all we'd need to do is push some new root domains to a repository, and the Trickest workflow would automatically scan them on the next run.
Scheduling
Once we've got a good workflow going, we could schedule it to run at frequent intervals - perhaps to monitor the external attack surface of an organization.
Further Reading
Check out this blog by the Head of Workflows at Trickest, Mohammed Diaa which walks through the process of creating a recon and vulnerability scanner that integrates with GitHub for data management.
Conclusion
Typically, I'm a sucker for the CLI, and coding my own solutions - but I have to say, I'm impressed.
In about 30 minutes, I've created a system that can perform subdomain recon, DNS recon, HTTP(S) probes, WAF detection and vulnerability scanning. I could create this type of workflow myself by setting up a VPS and coding, but it would:
- Take longer
- Be more hassle
- Require coding knowledge
- Require infrastructure setup
- Feel janky
Throughout this process, building the workflow has felt like playing a computer game, the Trickest UI feels intuitive and functional. Editing the workflow or repurposing it for something else in future would be a breeze.
If you're after a solution to build out security custom workflows - especially if you're working in a team, give it a shot!
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
