Private Agents - Scan Internal Environments On Any Device
See how Private Agents empower organizations to scan internal environments on any device using Trickest's solutions, workflows, and modules.
Companies often rely on internal defense mechanisms to protect their systems from exposure to the broader internet. When we think about defense in depth, a commonly used analogy is the onion, which has multiple layers that need to be peeled off to get to its core. We need to ensure that even if one layer is compromised, there are still enough layers to prevent malicious attackers from accessing our company's core assets such as intellectual property, bank accounts, user data, and more.
In recent years, there have been numerous cases of breaches affecting prominent companies. Understanding why these breaches occur can help us prevent them. Ransomware attacks are powerful and often target the weakest link in our systems: humans. After penetrating a system, attackers continue to scan the internal environment with infected systems, causing severe impact as they move through the network.
In the case of Uber, if confidential data had not been immediately exposed, the attacker would have caused less damage before being caught.
This is why companies need to include an additional layer of security. The approach to the external and internal environments should be the same. For instance, if one of your lead engineers accidentally made your entire network public, it could lead to an immediate breach. This underscores the importance of asking yourself:
- How would you feel if all internal development services were open to the public?
- Would you be breached immediately?
Many big companies would be, and it has already happened.
Why is Internal Scanning Important?
While external security assessments provide insight into your system's defenses against outside threats, they offer a limited view without deeper system access. Consider the significant impact of your internal infrastructure compared to the external one.
Cybercriminals use phishing, targeted malware, and ransomware, which can infiltrate even the most secure-looking systems. Additionally, vulnerabilities overlooked during external scans can often be exposed through a more comprehensive internal assessment.
Internal scanning addresses this critical gap. By thoroughly examining your internal systems, you create an additional layer of defense, making your organization far more resilient to breaches.
What are The Private Agents?
Trickest understands that when it comes to security, there is no one-size-fits-all solution. Every company and its security team are unique. Based on customer feedback, we have realized that security teams are becoming more concerned with not only their external surface but also their internal one. They want to employ the same methodologies within their internal environments.
Private Agents are lightweight executables directly linked to workflows, ready to execute tasks as assigned. They require no additional libraries, specific operating systems, or system requirements. They can run on any device and any network with Docker installed.
With Private Agents, you can scan your infrastructure behind VPN and office networks, integrating them within your infrastructure for 24/7 scans against your internal infrastructure.
How to Get Started?
Access Your Trickest Account
- Log in to your Trickest account. If you don't have an account, sign up.
- Navigate to the Fleet. When you log in, on the left sidebar, click Settings at the bottom, and locate the Fleet under Fleet Management.
If you don't have access to this feature yet, get in touch with us to discuss how we can help with scanning your internal environments.
Add Machine and Provide a Name—Click on Add Machine to receive instructions on how to deploy the Private Agent on your device.
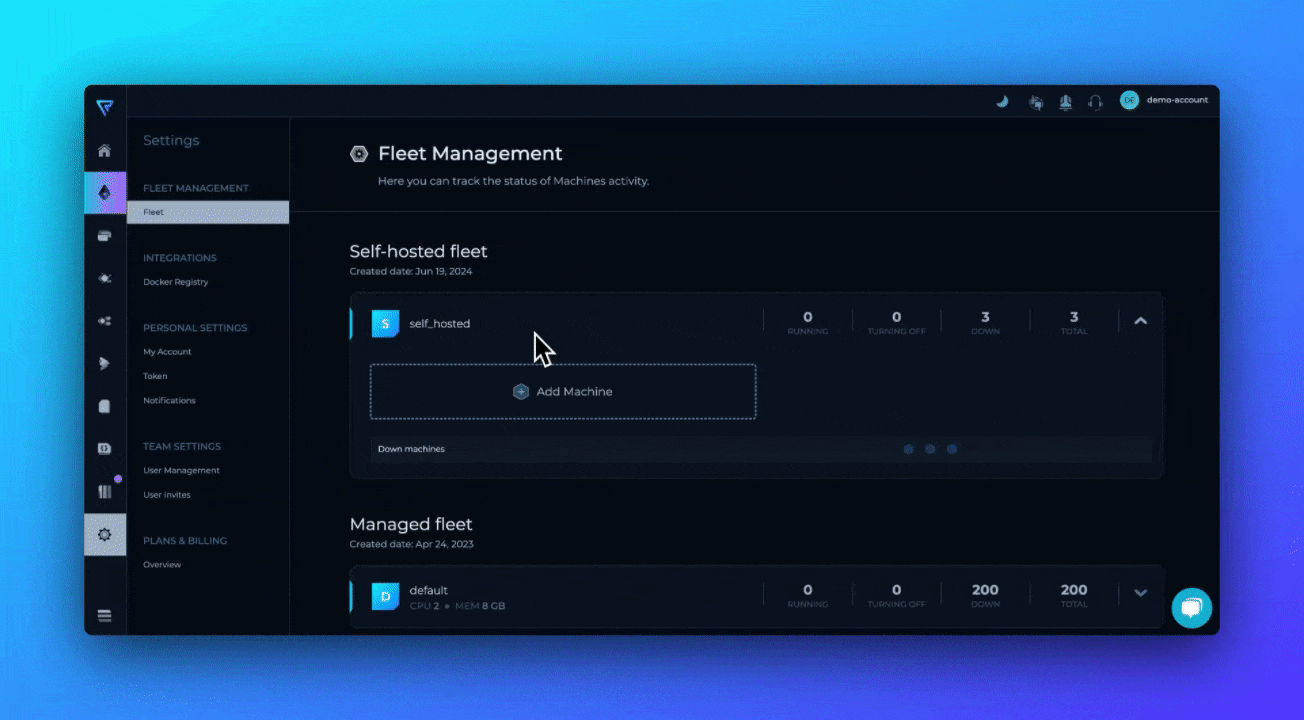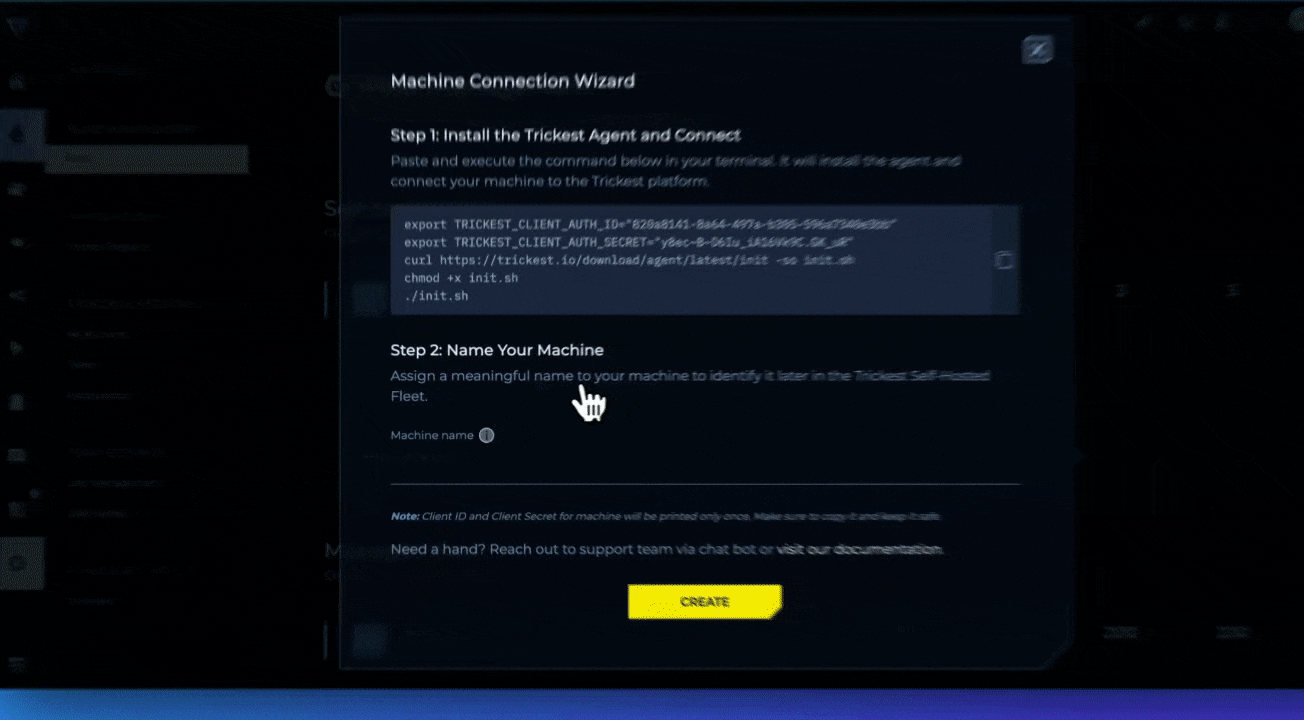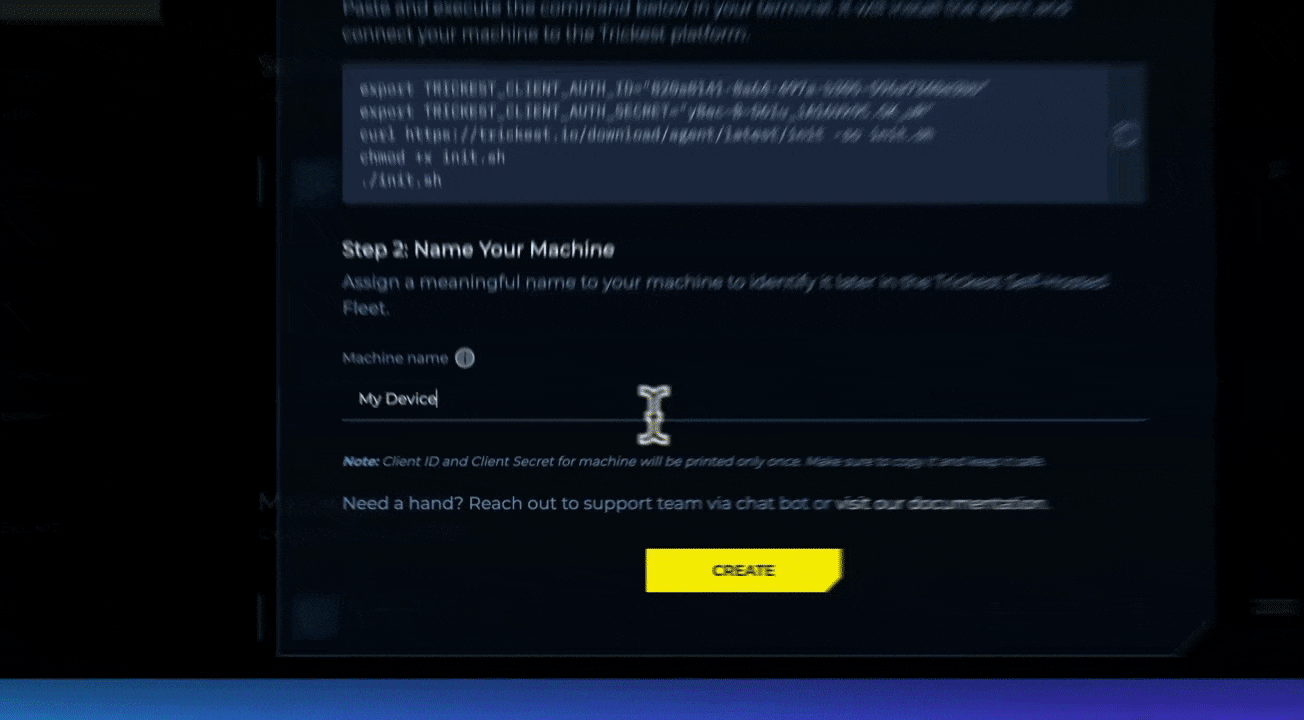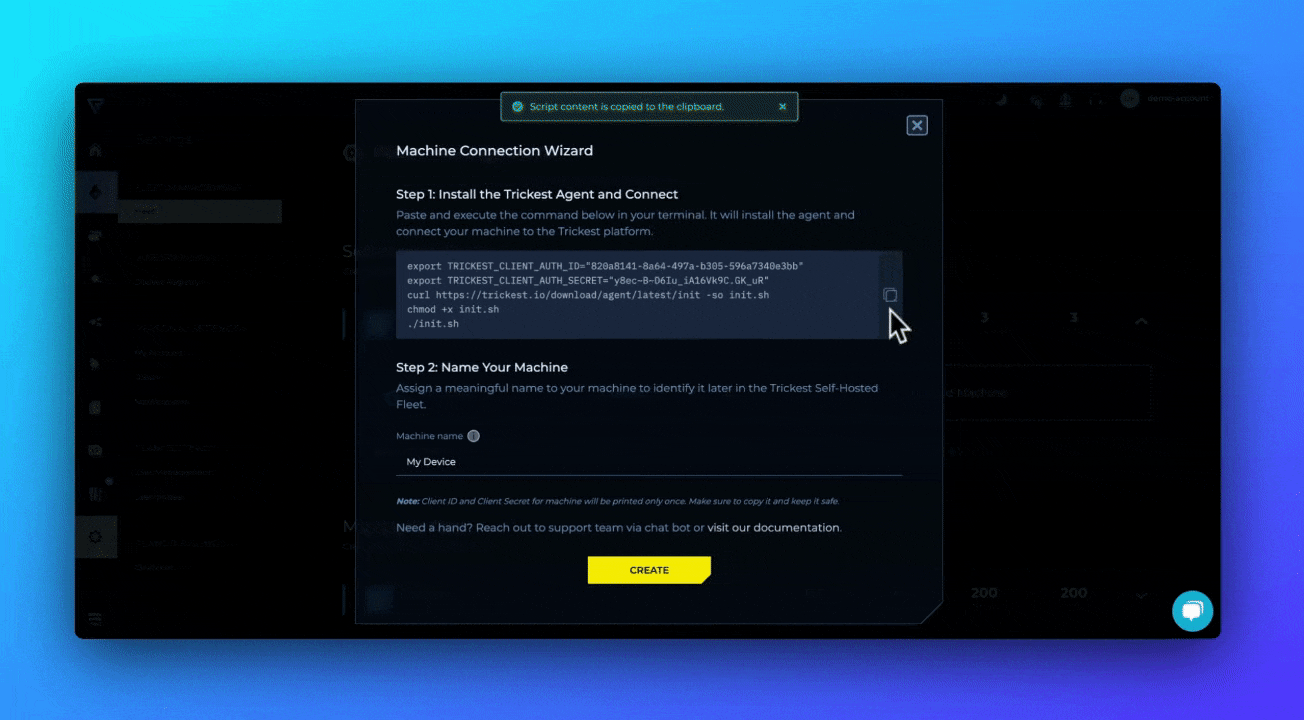
- Deploy the Private Agent. Execute the command provided on your device.
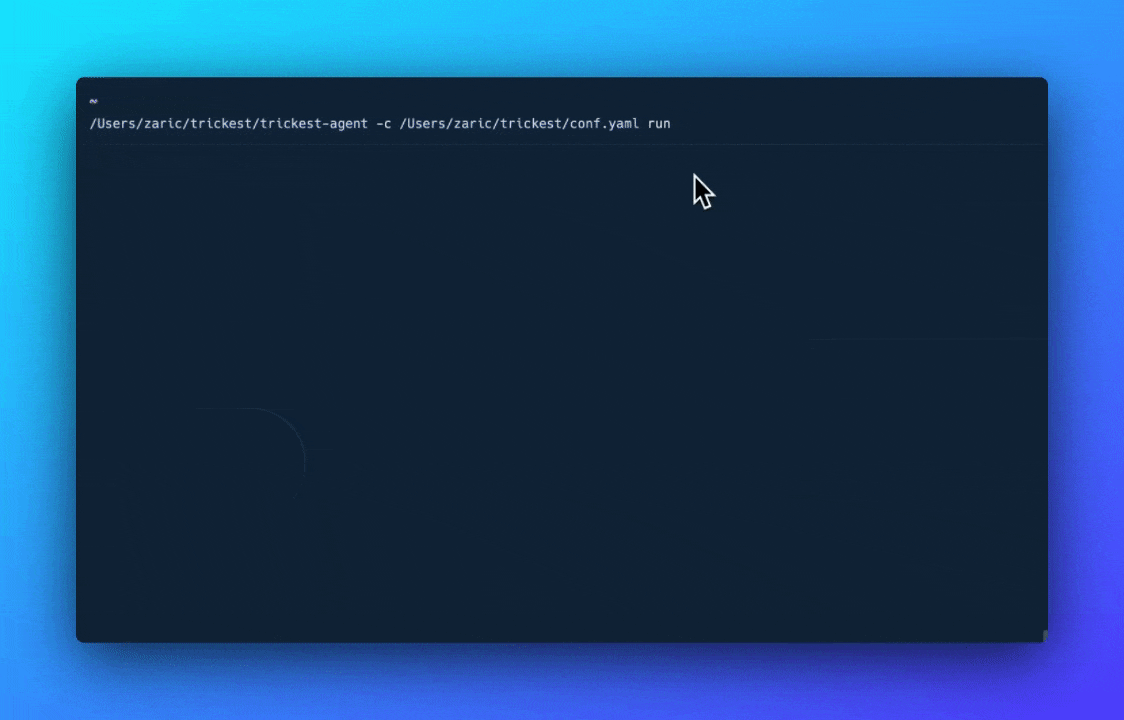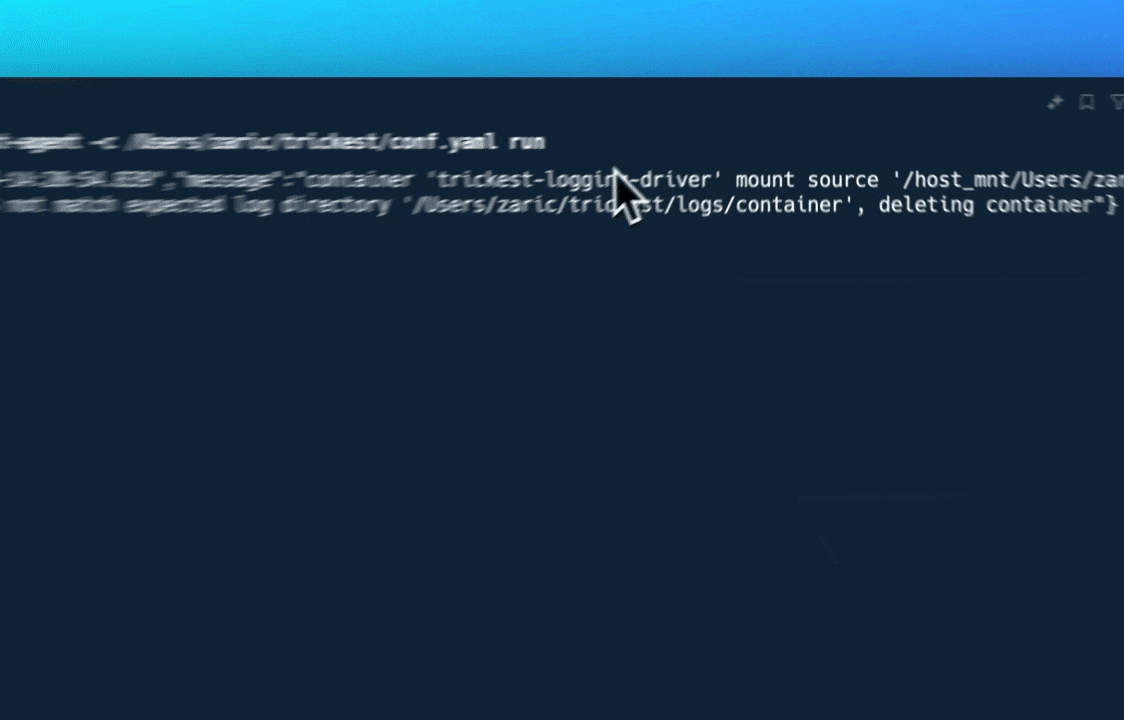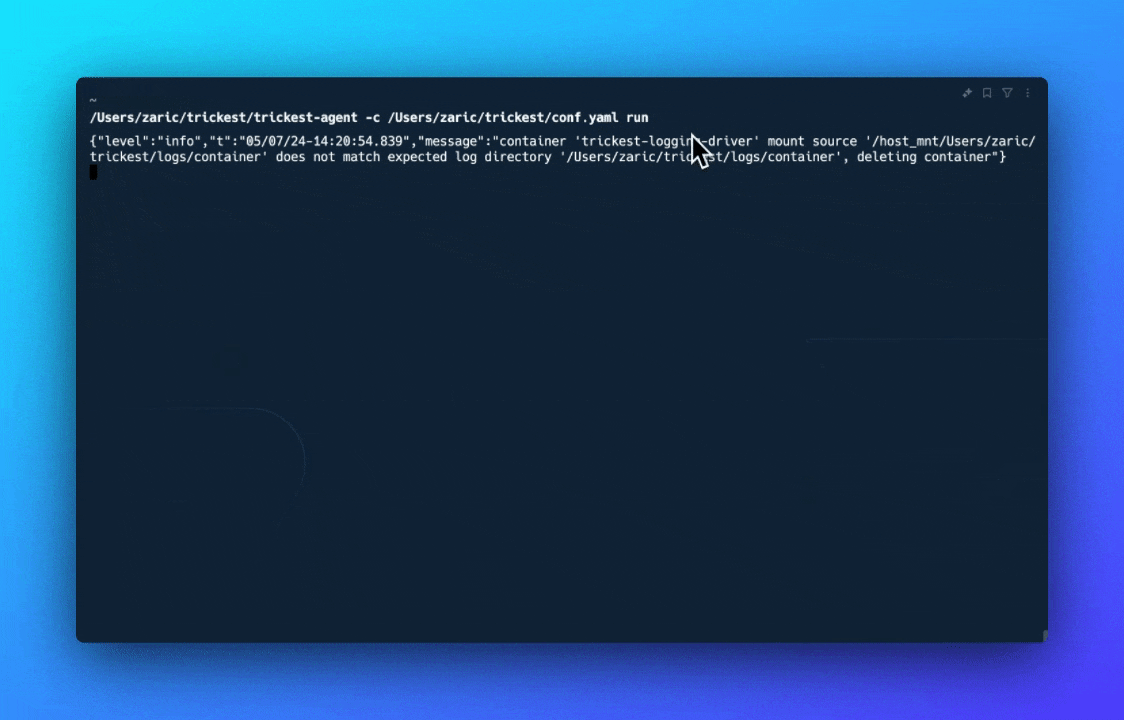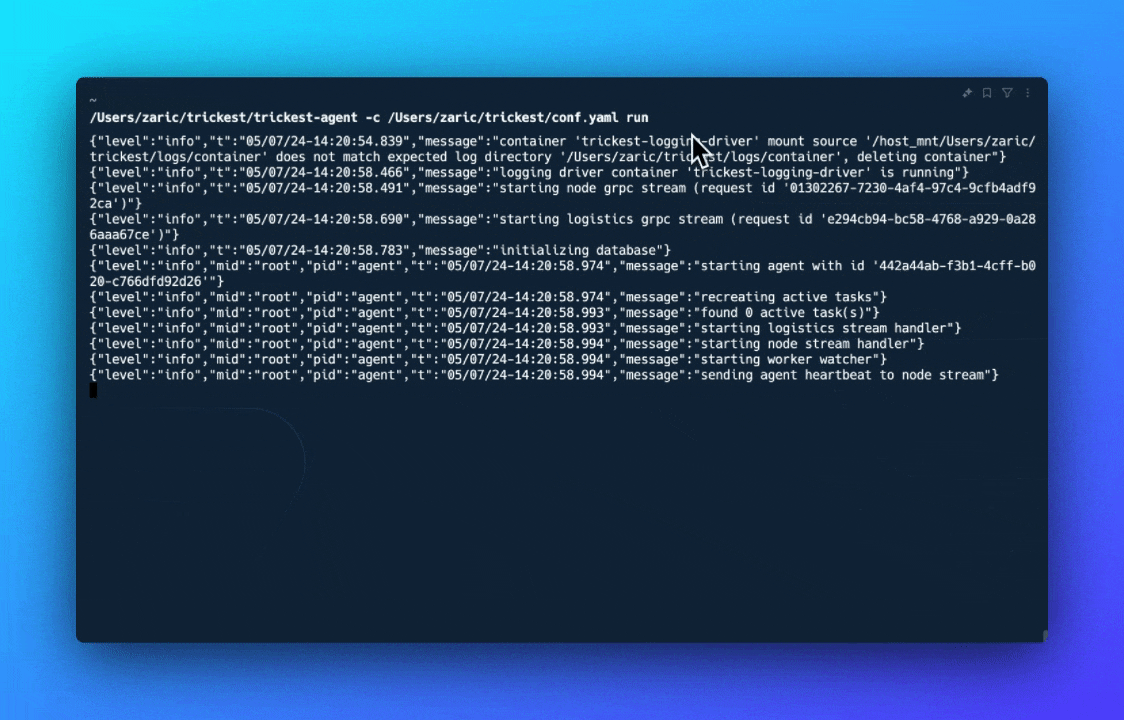
Private agents currently support OSX and Linux Operating Systems and can be deployed on any device.
Practical Example
Imagine you are in your office and want to determine which services on your internal network are exposed. You need to find out if there are any vulnerable services on your personal devices, printers, or any other infrastructure that you want to keep internal.
With our newly introduced modules this can be achieved with just a few clicks!
Here's how it works:
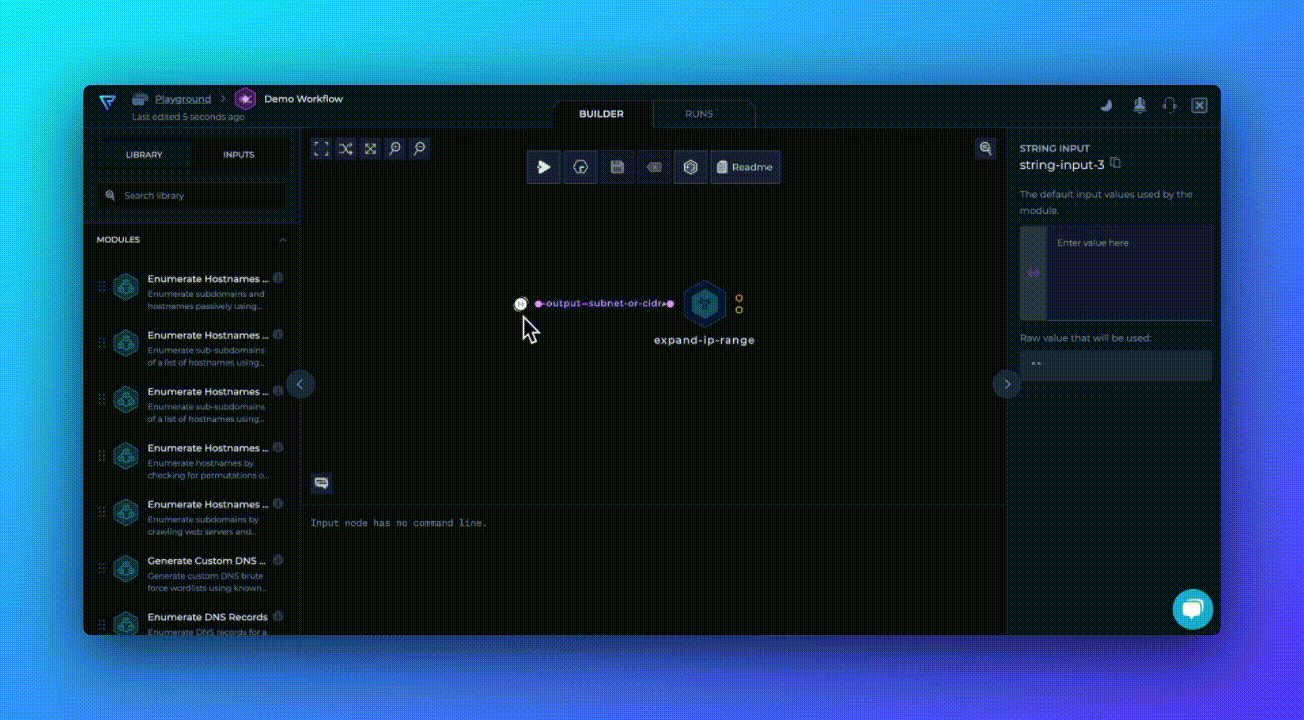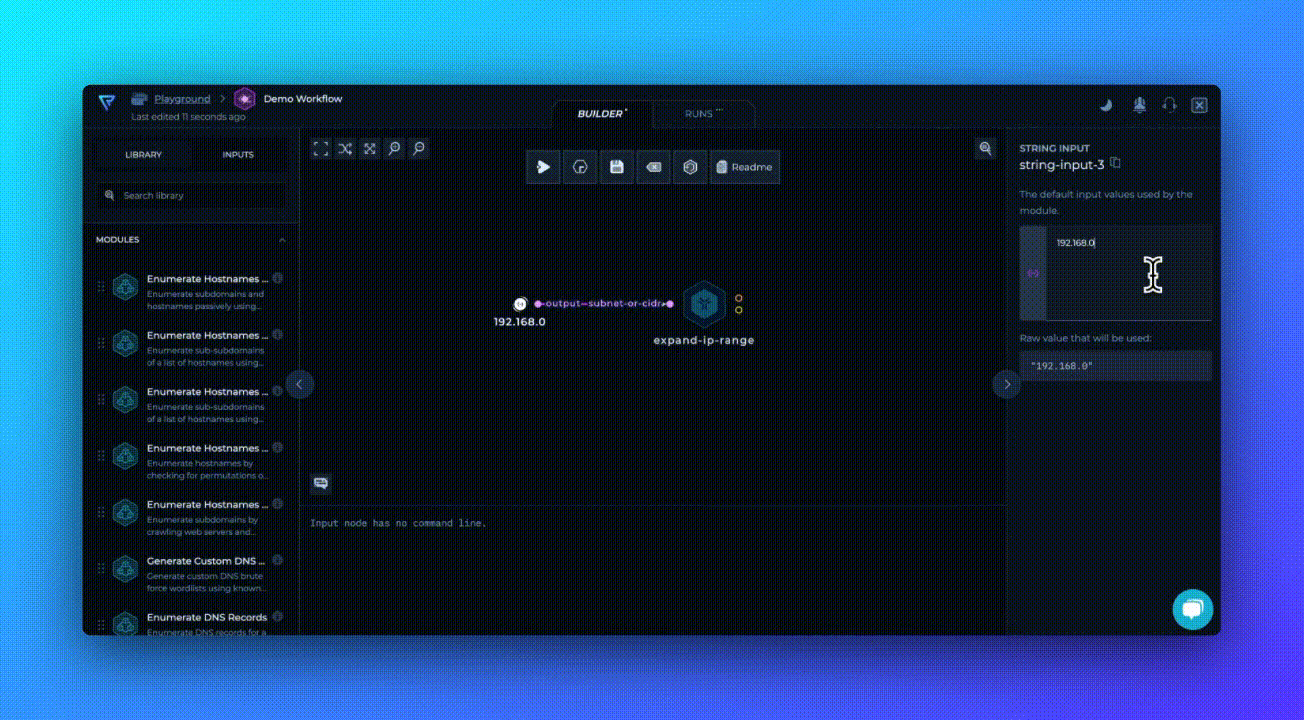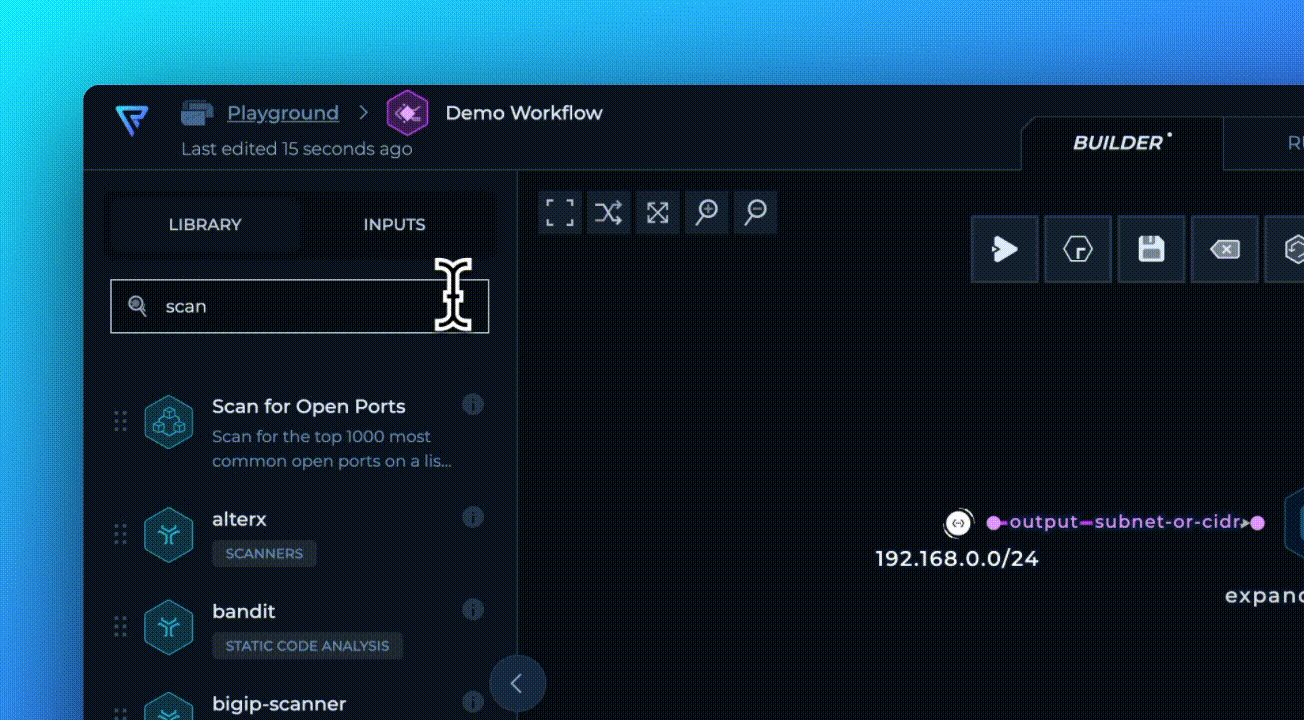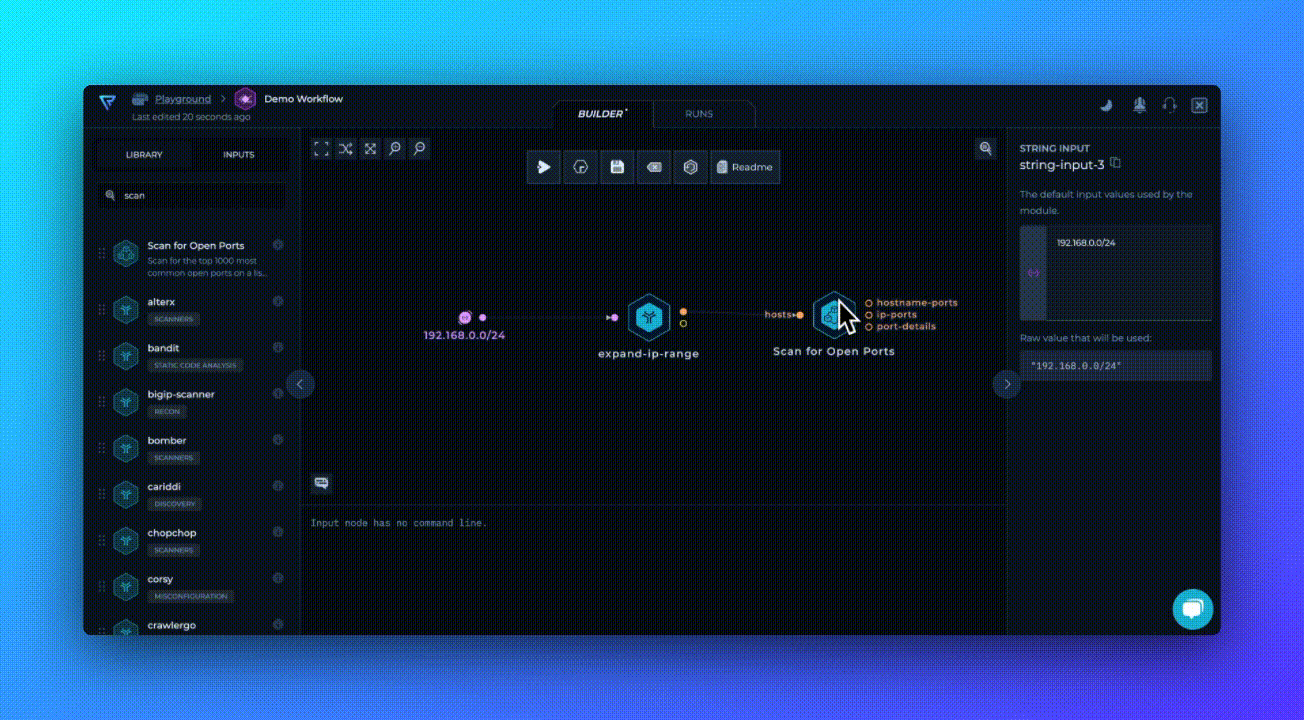
This workflow uses our latest module, Scan for Open Ports, which scans all of the available services on different ports using the provided list of IP addresses as input. It's that simple!
Use Cases
Internal Network Service Scanning
Internal network service scanning is essential for identifying and managing potential security risks within an organization's private network. Organizations can discover open ports and running services using different tools and modules, ensuring no unauthorized or vulnerable services are exposed. Deploying private agents on internal infrastructures improves this process by providing deeper insights and more accurate detection within the internal networks.
Internal Attack Surface Management
Continuous monitoring and analysis of internal assets help prioritize remediation efforts and implement effective security controls. Private agents facilitate this by offering real-time, comprehensive visibility into the internal network, enabling organizations to proactively reduce their attack surface and enhance security.
Internal Vulnerability Scanning
It's important to regularly scan for vulnerabilities within your organization's internal systems. This helps to identify security weaknesses like unpatched software and misconfigurations. Using private agents for these scans ensures thorough and precise detection, which allows vulnerabilities to be identified and addressed promptly, ultimately strengthening the internal security posture.
On-Site Pentests
On-site penetration testing involves ethical hackers conducting real-world attack simulations on an organization's internal network. Using private agents during these tests ensures a thorough and accurate assessment. They can execute tests within the internal infrastructure, providing valuable insights and actionable recommendations to improve security.
Conclusion
Incorporating internal scanning with private agents can significantly enhance your organization's defense mechanisms and proactively identify potential vulnerabilities. This was one of the most requested features from our users, aimed at enabling robust internal pentesting and comprehensive internal scans, and we are thrilled to kick it off.
Take the first step towards our all-in-one offensive security solution by speaking with our team today. Secure your internal environment and protect all environments of your organization.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
