Full Subdomain Discovery Using Automated Trickest Workflow - Part 1
Learn what subdomain discovery is, the best techniques to do it, and how to create a Trickest workflow to automate the discovery of subdomains using the best techniques.
When a pentester or bug hunter is asked to audit a company with a wide scope, the initial phase he should perform is the recon of the company. The more exposed assets belonging to the company he or she is able to discover, the better. This is because companies tend to forget assets exposed to the Internet that, at some point in time and generally due to lack of maintenance, become vulnerable.
Moreover, one of the main ways companies expose assets to the Internet is through subdomains, therefore the more subdomains from domains belonging to the company a pentester is able to discover, the most probable is he will discover something vulnerable.
In this post, we are going to learn how to automate a full subdomain discovery plan creating an awesome Trickest workflow that will allow us to discover many subdomains from a domain using a great variety of techniques.
Note that in this post, we are going to suppose that the reader already knows the very basics of Trickest, like how to create a new space and a new workflow. If you don't, don't miss this great introduction to the Trickest platform.
Intro to Subdomain Discovery
One of the phases I enjoy the most during the recon of a company is the discovery of subdomains. During this phase, depending on how good your enumeration is and how bad the company is keeping its infrastructure updated you could find gold: subdomain takeovers, old web pages running in HTTP and vulnerable to all kinds of common vulns (XSS, SQLI...), outdated platforms affected by known vulnerabilities or using default credentials...
Therefore, it's very important to try to find as many subdomains as possible during this phase.
In order to find subdomains of a company, there are two main techniques:
- OSINT sources: A lot of different platforms store for different reasons domains and subdomain names or web page URLs (that also contain the domain/subdomain names). Several tools search across tens of platforms storing this kind of information to find as many subdomains as possible.
- DNS Bruteforce: Once you have searched in OSINT resources, and supposing the DNS isn't vulnerable to Zone Transfer or the ANY DNS record isn't giving you all the records, you should try to discover new subdomain names by guessing. There are several huge wordlists of possible subdomain names that can help you find new valid subdomains.
In the following sections, we are going to create a Workflow capable of abusing both techniques to find as many subdomains from a domain as possible.
Initial Domain
To start this subdomains enumeration workflow, we are going to use set the domain as a string input connected to the node "STRING-TO-FILE". We do this because some of the tools we are going to be using need the input as string, and others need to input as file.

First Subdomain Discovery tool
The first tool we are going to integrate into this workflow is Oneforall. This tool will search in tens of OSINT platforms to search for subdomains of the given domains.
Note how we have linked the output of this tool with a script that will get the discovered subdomains and output them.

More OSINT Subdomain Discovery tools
Next, we are going to add 5 more tools that behave in a similar fashion to Oneforall: They are also going to search for subdomains in OSINT platforms. These tools are:
- Amass
- jldc-subdomains
- Vita
- Findomain
- securitytrails-subdomains You need to have an API key to use this one.
From time to time, new tools appear with new sources of information or new sources of information are added to these tools. You should try to keep them up to date to always find as many subdomains as possible.
This is what our workflow looks like at the moment:

Note that Trickest allows selecting the "size" of the machine to use on each node. There are 3 different sizes: small, medium, and large. The main difference between them is the resources (CPU and memory) the machine will have during the execution of the node and the price per started hour.
The tools we have used in our current workflow can run in "small machines" as they aren't going to be doing any kind of intensive work:

DNS Subdomain Bruteforce
It's time to add a tool to perform DNS bruteforce to try to find all those subdomains that, for some reason, don't appear in the OSINT platforms.
With this goal in mind, we are going to use puredns, this is a tool based on massdns to discover new subdomains quickly. Puredns is capable of filtering false positives from wildcard subdomains.
These are the params I set in puredns:
- mode:
<domain.name>(string) - mode:
resolve(string) - threads:
500(string) - resolvers:
https://raw.githubusercontent.com/trickest/resolvers/main/resolvers.txt(file) - resolvers-trusted:
https://raw.githubusercontent.com/trickest/resolvers/main/resolvers-trusted.txt(file) - wordlist:
https://localdomain.pw/subdomain-bruteforce-list/all.txt.zipthrough "UNZIP-TO-OUT" --> "RECURSIVELY-CAT-ALL" --> MKSUB nodes.
Note that in this case, I usually use a "large" machine with puredns because the actions puredns are going to be working are very intense. The MKSUB node needs to be at least of "medium" size.
This is how it will look like:

Grabbing All Subdomains
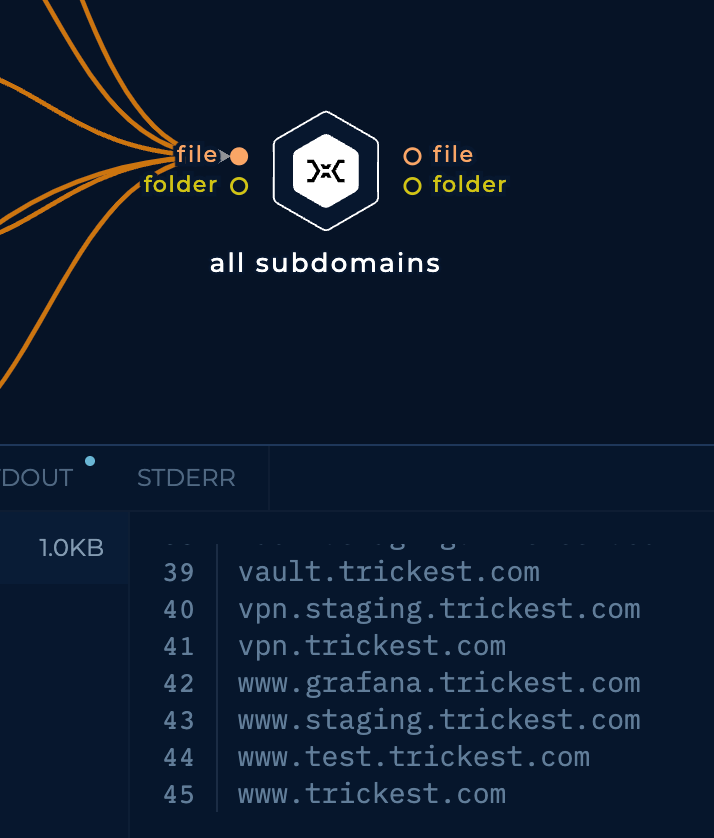
Finally, I will be connecting all the used tools in the single node that will read all the outputs and remove all the repeated subdomains:

Run it!
Let's give this workflow a try and see what it finds!

For the sake of brevity, I'm not going to list here all the discovered subdomains, but it discovered 45 subdomains:
Conclusions
In this post, we have seen how to discover subdomains from a single domain using several OSINT tools and DNS bruteforce. This should find the most important subdomains of a domain if not all.
However, is this the best workflow we could have created to discover subdomains? No, it isn't, there are several improvements that we could add:
- This workflow only supports one domain as input. But it could support a list of domains.
- This workflow doesn't create permutations with the discovered subdomain names to try to find even more subdomains.
Check out the part 2 and sign up on Trickest to be ready to test it by yourself!
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
