Securing Your IIS Server: A Comprehensive Guide
Explore key strategies to strengthen the security of your IIS server and protect your web applications. Learn about firewall configurations, automation, authentication, and more.
Decoding Recent Breaches: A Deep Dive into IIS Server Security
- 2022: Kaseya data breach: The Kaseya data breach exposed the sensitive data of over 1,500 businesses, including customer names, email addresses, and credit card numbers.
- 2021: SolarWinds data breach: Attackers gained access to the networks of over 18,000 organizations, including government agencies, Fortune 500 companies, and critical infrastructure providers.
- 2020: Microsoft Exchange hack: Attackers took control of the Email servers of over 30,000 organizations, including government agencies, businesses, and educational institutions.
Can you spot the unifying factor in these incidents? - IIS was at the heart of every breach.
According to a recent study by Trend Micro, IIS was the most targeted web server platform in 2022. Attackers are constantly exploiting vulnerabilities in IIS to gain access to web servers and steal data, install malware, or launch attacks against other systems on the network.
In this in-depth guide, you'll learn how to fortify your IIS (Internet Information Services) Server. Relying on Trickest’s automated workflows and a holistic understanding of cybersecurity, we equip you with the knowledge and tools to make your server as secure as a fortress.
What even is IIS?
IIS stands for "Internet Information Services." It is a web server software developed by Microsoft for use with Windows Server operating systems. IIS is designed to host websites and web applications on Windows servers, providing a platform for delivering web content, services, and applications over the internet.
Imagine IIS as a traffic cop for the internet. It manages all the incoming requests for your website, acting like a conductor that guides cars to the right place and ensures they receive the correct content, such as your website pages and files.
IIS is also your digital bouncer, just like the ones you see at clubs or parties. Its job is to verify IDs (requests for web pages), ensure that everything is in order, and grant access to reliable visitors while preventing entry to troublesome individuals like hackers and malicious bots.
IIS supports various web technologies, including ASP.NET, PHP, and more, making it a versatile choice for hosting a wide range of web applications. It also offers features like security, performance monitoring, and scalability to ensure the reliable and efficient operation of web services.
Why bother with IIS Security?
Think of IIS as your virtual security guard, whose primary duty is to prevent intruders, or hackers, from breaching your defenses and causing harm. As we have previously explained, it is essential to have robust security for IIS. We will now delve deeper into the importance of this.
In today's digital age, intruders and hackers are persistent and continuously improving their techniques. They tirelessly look for weaknesses and vulnerabilities to penetrate digital fortresses. That's why having a Virtual Security Guard, such as your IIS server, is not just a choice, but a crucial requirement. In the upcoming sections, we'll dive deeper into understanding the key vulnerabilities that malicious actors exploit, how can Trickest help in uncovering those vulnerabilities, as well as the robust security measures that can be implemented to improve your IIS server's defenses and strengthen your digital assets against potential threats.
The Detection: Where are the Potential Weaknesses?
Think of it like a checkup for your IIS server. Just as a doctor looks for signs of illness, we'll analyze the server's setup to find weaknesses that attackers could exploit. This proactive approach helps you prevent potential problems and maintain a healthy digital environment.
The issues might be anything from outdated software, and incorrect settings, to overlooked access control problems and more. Our aim is to spot and understand these issues thoroughly so that we can reinforce potentially “unsafe” areas and minimize the risk of security breaches.
And this is where Trickest comes into play. It takes all the powerful community tools and enables us to integrate them into various workflows neatly. It basically helps us do what we usually do, just significantly faster, smoother, and cheaper.
For the workflow, we use Nuclei with specific “iis" & “microsoft” tags to detect and uncover not just the assets using IIS but also the common vulnerabilities affecting those Servers.
-
We provide a list of Domains/Hosts as input.
-
From the Input file, we create Line Batches, i.e., splitting the input file into small batches and performing the execution in batches.
-
We pass those Batches as input to Nuclei with the following flags:
-concurrency 300- Max number of templates to be executed in parallel-templates- Folder to run templates-timeout 1- Time to wait before timeout (in seconds)-tags iis,microsoft- Only execute the templates that have an “iis” or “microsoft” tag-list- List of Target URLs to Scan
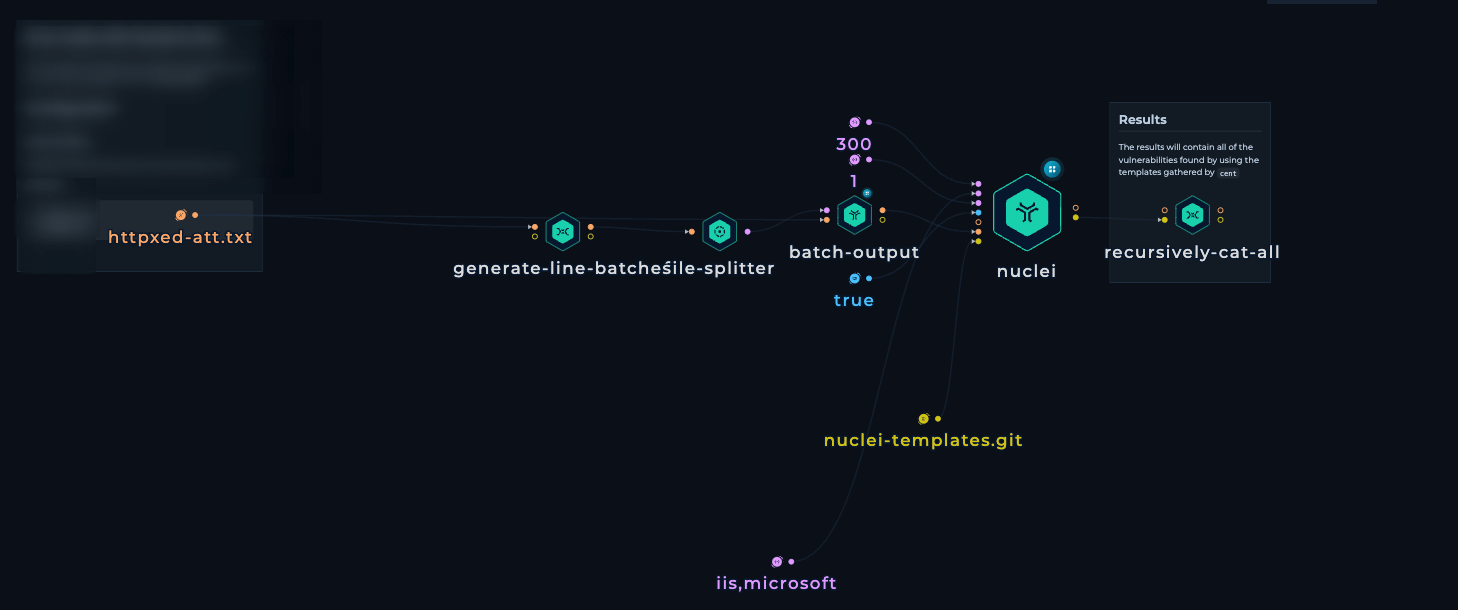 IIS security workflow
IIS security workflow -
Recursively cat the output files from Nuclei to get a combined CSV output file from all the batches.
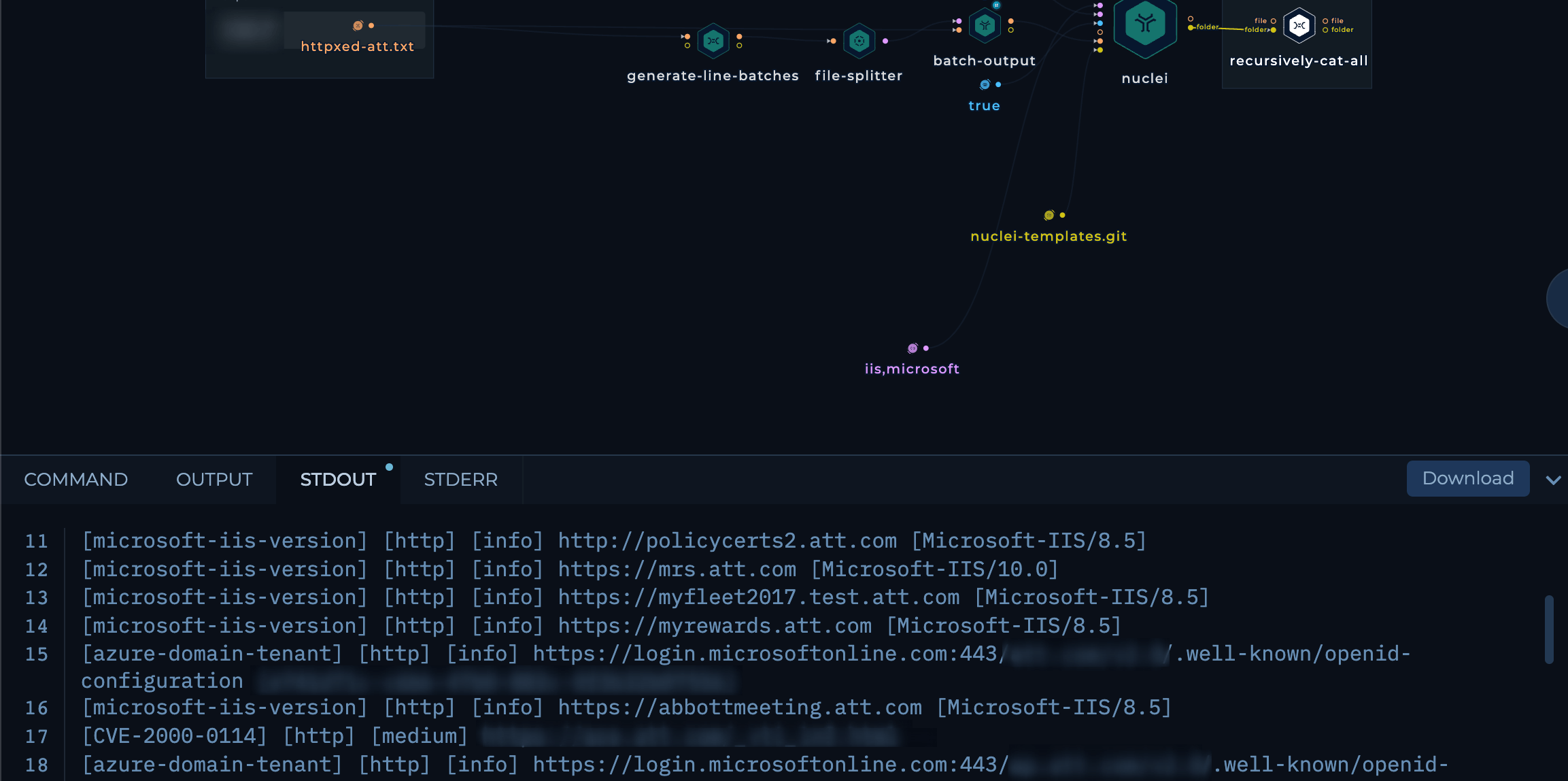 IIs security workflow run results
IIs security workflow run results
The Solution
Now that we've identified the challenges, it's time to take decisive action. We will implement defensive measures comparable to reinforcing the walls and gates of your digital fortress. Key components include:
1. Firewall Configuration
Your firewall is the digital equivalent of the imposing walls that surround a medieval fortress. Just as those walls protect the inner sanctum of the castle, your firewall is your server's first line of defense against cyber threats. It stands guard at the entrance to your digital domain, determining who gets in and who stays out.
Technical Details:
- Implement a robust firewall solution, such as Windows Firewall.
- Configure it to allow traffic only on essential ports, like 80 for HTTP and 443 for HTTPS.
- In cloud environments, use security groups or network security rules to manage traffic to and from your server.
- Regularly review and update firewall rules to adapt to evolving threats.
2. Updates and Patch Management
Just as a castle's armory must be equipped with the latest weaponry to repel invaders, your server and software must be kept up-to-date to defend against modern cyber threats. Software vendors regularly release patches and updates to fix newly discovered vulnerabilities. It is essential to consistently apply these updates to maintain a secure digital environment.
Technical Details:
- Enable automatic updates for your operating system and IIS software.
- Monitor for updates and schedule maintenance windows for timely patch deployment.
- Consider using a vulnerability scanning tool to identify any missing updates and prioritize them based on potential risk.
3. Authentication and Authorization
Effective user access management is fundamental in the digital realm, much like controlling who holds the keys to the castle gates. Ensuring that only authorized individuals can access your IIS server and its digital assets is crucial for maintaining security.
Technical Details:
- Implement stringent password policies.
- Consider deploying multi-factor authentication (MFA) for added security.
- Employ role-based access control (RBAC) to restrict access privileges.
- Utilize authentication methods like Windows Authentication.
- Configure authorization rules to control access to specific directories or applications.
4. SSL/TLS Encryption
SSL/TLS encryption serves as the cloak of invisibility for your data, much like encoding messages in a secret language that only trusted emissaries can decipher. This cryptographic layer ensures that information exchanged between your server and users remains confidential and secure.
Technical Details:
- Obtain and install an SSL/TLS certificate for your domain.
- Configure your IIS server to enforce HTTPS for web traffic.
- Regularly update your SSL/TLS protocols and ciphers to maintain the highest security standards.
5. Request Filtering
Request filtering is your digital fortress's gatekeeper, ensuring that only trustworthy visitors are allowed entry. Much like vigilant guards inspect all visitors at the castle gates, request filtering imposes strict rules for what is allowed and what is denied, safeguarding your server from malicious requests and attacks.
Technical Details:
- Configure request filtering rules to allow or deny specific URLs, query strings, or file extensions.
- Utilize the "Request Filtering" module in IIS to impose restrictions on request sizes, HTTP methods, and other parameters.
- Regularly update and fine-tune these rules to adapt to evolving threats.
6. Logging and Monitoring
Monitoring is the equivalent of having vigilant sentinels patrolling the castle walls, ready to raise the alarm at the first sign of danger. Just as they watch for suspicious activity, monitoring in the digital world involves keeping an eye on your server for any unusual or potentially threatening behavior.
Technical Details:
- Activate comprehensive logging in IIS to record detailed request information, errors, and security-related events.
- Implement a centralized logging system or SIEM (Security Information and Event Management) solution to aggregate and analyze logs from multiple sources.
- Set up alert mechanisms to promptly notify you of unusual or suspicious activity.
7. Backup and Recovery
A dependable backup and recovery plan is your digital fortress's safety net, much like having a spare set of armor and weaponry ready in case of unexpected battles. It ensures that in the event of data loss or a security breach, your server can be swiftly restored to full strength.
Technical Details:
- Regularly back up your server configuration, website content, and databases.
- Check your backups often to make sure they can be restored without any problems.
- Develop a well-documented disaster recovery plan outlining procedures for server restoration and data recovery, specifying roles and responsibilities for your digital guardians.
8. Third-Party Security Solutions
Consider augmenting your IIS server's security with third-party tools and services that offer advanced threat detection and intrusion prevention capabilities. Think of these tools as specialized units of knights who can reinforce your digital defenses when needed.
Technical Details:
- Research and select security tools tailored to your specific security requirements.
- These tools may encompass web application firewalls (WAFs), intrusion detection systems (IDS), and antivirus software.
- Configure and maintain these tools to seamlessly integrate with your IIS server, allowing them to work in harmony to protect your digital fortress.
By meticulously implementing these security measures, scheduling a Trickest workflow for IIS security, and focusing on technical details, you can substantially enhance the security posture of your IIS server, fortifying it against potential threats and vulnerabilities.
Remember that security is an ongoing endeavor, requiring regular assessments and updates to maintain a robust defense.
Conclusion
The security of your digital fortress depends on the vigilance of its inhabitants. Just as the strength of a real castle depends on the watchful eyes of its guards and the care taken by its residents to secure their gates, the security of your web applications relies on the actions and awareness of those who use and maintain them.
Just like most stuff in Security, securing your IIS server is an ongoing process, not a one-time task. Sign up to automate even more use cases with Trickest and to help safeguard your IIS Servers.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
