Insider Threats: The Biggest Risk to Organizational Security
Learn how to defend and prevent insider threats and related risks such us phishing attacks, data leakage, and credential leakage via automated workflow engine.
In the post-pandemic period, businesses have more digitized operations and employees spread all over the globe. This has led to a more than 300% rise in cybercrimes, and the average cost of a data breach is now more than $4 million USD. Reducing the risk of insider threats has never been more critical.
Many organizations have been focused on security from an outside, internet-facing perspective rather than an insider's point of view. Meanwhile, the number of insider attacks increased by 44% in 2022. According to Verizon's 2021 Data Breach Investigations Report (DBIR), insider threats were responsible for approximately 22% of security incidents. Understanding insider threats and how organizations can develop countermeasures against such attacks is essential when developing a security strategy.
What is an Insider Threat?
An insider is a person who has access to insider information and systems of an organization. An insider threat is a threat that this person poses to the organization (intentionally or not). These insiders could be an employee or former employee, a contractor, or anyone that has privileged access within your organization.
Types of Insider Threats
- Malicious Insider: A malicious person is a potential entity who wants to harm the organization by leaking sensitive data or disrupting business operations. Their motivation for such attacks is often financial or revenge against the organization.
- Compromised Insider: A compromised insider is an entity that has been compromised with malware or is potentially hacked via social engineering attacks. Hackers use these types to exfiltrate sensitive data like PII or gain unauthorized access to resources.
- Negligent Insider: Negligent insiders are ordinary workers who make a mistake. An employee, for example, might send a confidential email to the incorrect person, email corporate data to personal accounts to conduct some work over the weekend, become a victim of a phishing or spear phishing assault, or lose their work equipment.
How to detect an Insider Threat
Finding an insider threat is quite challenging. Traditional security measures like firewalls and IDPS, among others, cannot cope with such circumstances. We need to examine digital traces and monitor user behavior to understand how to identify insider threats:
- Analyze if a user downloads sensitive information to storage devices like hard disk, pendrive, etc.
- Monitor emails that have been sent outside the org with any attachments.
- Check if a user requests elevated access to confidential documents and records within the organization without a clear need (e.g., the accounting team requesting sensitive technical information).
- Analyze the user's web history to check if he is trying to search for any sensitive information.
- Check for any instances of data theft, manipulation, or destruction inside the company.
- Constantly analyze any form of social engineering attacks like phishing.
Trickest's Insiders Workflow
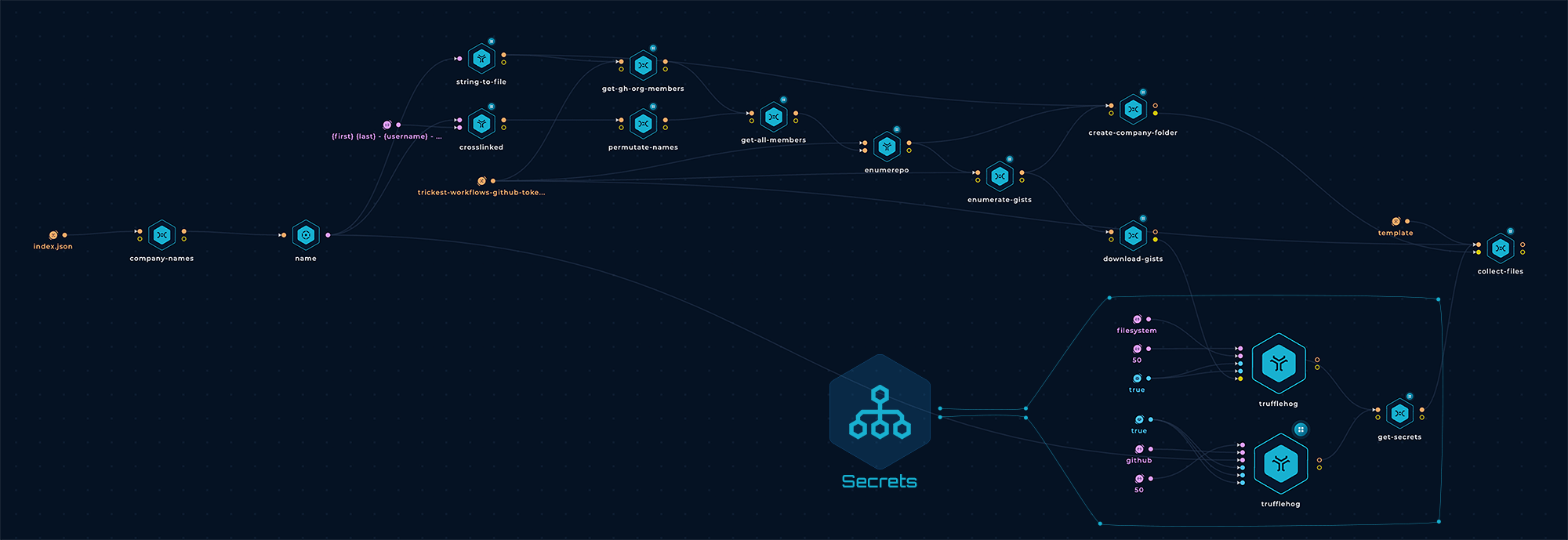
One common expression of an insider threat is when a developer at the organization leaks sensitive data through negligence. Individual developer accounts are more likely to expose secrets than official brand accounts. Trickest team built a workflow that aims to create a comprehensive archive of public code repositories belonging to the employees of companies that have bug bounty programs.
Check out a visual representation of the complete workflow and the workflow results in the Insiders GitHub repository. The workflow performs the following steps to enumerate the users associated with a GitHub org and check them for leaked secrets:
- Get the initial list of target names from Project Discovery's Chaos dataset (Thanks, ProjectDiscovery)
- Use a slightly modified version of CrossLinked to collect employee names and usernames from LinkedIn (Thanks, m8r0wn)
- Generate username permutations based on the collected names/usernames.
- Enumerate public GitHub organization members using the GitHub CLI (Thanks, GitHub)
- Merge the collected potential usernames and pass them to our enumerepo, which validates the usernames and enumerates their public repositories.
- All of the collected orgs/usernames/repos/gists are then passed to TruffleHog to find exposed secrets/credentials (Thanks Truffle Security!) as highlighted above in the Secrets workflow. Note that the results of this part are not pushed to this repository for obvious reasons. They are only accessible to our users, who can edit/customize this workflow to view the secrets, receive notifications about new ones, or export them using one of our integrations.
- In the end, we parse and organize the collected data and push it to the repository (except the Secrets part.)
- Workflow is scheduled to run regularly to keep the data up-to-date at all times.
This is an excellent workflow for discovering potentially sensitive data leakages due to insider threats from a hacker’s perspective! Set up a call with our team to create your own.
Insider Threat Statistics
Given the security landscape and the many threats linked with insider threats, the following are the most recent 2022 Ponemon Cost of Insider Threats:
- Organizations now spend $4.6 million on credential theft, up 65% from $2.79 million in 2020.
- On an annual basis, incidents that took longer than 90 days to contain cost companies $17.19 million on average.
- Organizations spend the greatest money on containment as a result of the rise in the amount of time needed to contain an insider threat incident from 77 to 85 days.
- Malicious insiders were responsible for 26% of the occurrences, costing $648,062 on average.
- The most expensive to address is credential theft, which costs $804,997 on average per incidence.
- In the research this year, stolen credentials were implicated in an average of 1,247 occurrences, or 18%.
- The report from 2022 indicates that 67% of businesses experience between 21 and more than 40 occurrences annually.
- The percentage of businesses between 21 and more than 40 occurrences increased to 60% in 2020 from 53% in 2018.
Impact of Insider Threats
Due to their dynamic nature, the impact can not be precisely measured, and the result of exploitation can range from informational to critical.
Most insider threats involve money or interfere with an organization's regular activities. A possible insider may give consumer information to an outside competitor or sell company data on the dark web, damaging the company's trust, brand and value. The exploitability of an insider threat depends on the ease of access to resources and the presence of existing policies within the organization. Mitigating such attacks is very difficult, but implementing proper regulations, access, and continual employee monitoring can help us reduce the likelihood of such attacks.
Typical Ways that Employees are Compromised
Here’s the outline of the methods that attackers will typically employ to manipulate company employees:
- Malware Infection: If the attacker's goal is to infect the employee with malware, the payload is typically delivered via social engineering attacks. The installed malware may be a crypter (ransomware) or an access trojan, with the goal of increasing the attacker's spread through the internal network.
- Credential Theft: There are several ways to steal credentials. Malware infestation and phishing are both frequent culprits. Social engineering is the practice of using deception to trick someone into disclosing their credentials. It may be used by some criminals. A frequent tactic is to phone the user pretending to be from the IT help desk and ask them to confirm their login and password.
- Data Leakage: Employees often reuse their personal credentials at work. If those personal credentials get leaked through a third-party breach, they may be used by an attacker to access internal company assets. Social Engineering: This type of attack is the most prevalent due to its simplicity. These attacks typically prey on staff security awareness.
Preventing Insider Threats
Insider threats will never be fully quelled, but there are some things that we can do to lessen their likelihood and severity:
- Implement Identity and Access Management: Businesses must ensure that workers have limited access to assets and information within the company, always following the principle of least privileges. Logging and monitoring should also be implemented for all tasks surrounding identity and access management, such as logins, failed logins, accessing assets, resetting passwords, etc.
- Implement Anti-Phishing and IT Security Training: Organizations must undertake IT security training so that employees know the fundamental security risks posed by malware and social engineering. The organization may also use anti-phishing software to make sure that the majority of bogus emails from outside the organization are eliminated from employee spam folders. Employee training and constant supervision might potentially remove the possibility of internal negligence.
- Implement Patch Management and Regular Software Updates: When it comes to security, deploying the correct solutions, such as patch management and regulatory software upgrades, is critical to avoiding zero-day vulnerabilities. These solutions guarantee that employees do not download or access potentially harmful pirated software and also use a self-service gateway within the enterprise for successful app downloads from reputable stores, potentially reducing the chance of being compromised.
- Implement a Strict, Strong Password Policy and Password Managers: Employees must update their passwords regularly in accordance with password standards, but they no longer need to remember them, all thanks to a combination of password managers. When passwords have the right length, contain special characters, and adhere to password regulations, the risk of credential leaking is decreased.
- Implement Employee Behavioral Analytics: Tracking, gathering, and analyzing user and machine data are all parts of user behavior analytics, sometimes referred to as user and entity behavior analytics (UEBA), which aims to identify risks within an organization. UEBA distinguishes abnormal behavior from normal activity using a variety of analytical methodologies. This is often accomplished by gathering data over time to identify the patterns of typical user activity, then highlighting conduct that deviates from those patterns. The obvious symptoms of insider threats, such as credential misuse, odd access patterns, and massive data uploads, may frequently be detected by UEBA.
Insider Threat Case Studies
In this part, we'll discuss some of the most well-known hacks that occurred in 2022 and examine several ways that an insider may harm a company.
Uber Hack led to unauthorized access to sensitive data
An 18-year-old teen hacked Uber in September 2022, potentially via a social engineering attack that provided him access to the VPN credentials. Using that person's credentials, the hacker was able to access several of Uber's internal systems, including the dashboard where the company's security experts submit bugs and vulnerabilities, a financial tool for invoices, and internal Slack chats. This is an illustration of a careless employee who may have been the victim of a social engineering assault that brought down Uber Security. The hacker later talked to reporters and claimed that they got access by employing social engineering tactics on a firm contractor, which Uber now believes the hacker to be a member of the Lapsus$ hacking organization, which has been responsible for multiple previous high-profile hacks. They built up a man-in-the-middle MFA gateway, pretending to be from Uber's IT department, and tricked this employee into providing his authentication credentials.
Taco Bell's Employee Steal Credit Cards Details
A Taco Bell employee stole a customer's credit card information in June 2022 to make many purchases for herself. The 36-year-old Laquawanda Hawkins, a drive-thru employee at Taco Bell, was immediately recognized as the information's source. According to CCTV evidence, she was caught on camera taking credit cards from clients and using the data to make a number of small-town purchases. One victim reported the suspect to the police after he reportedly tried to use his credit card to pay for the city's sanitation fees. After a police report was filed, the city gave the authorities the suspect's account information and paid the victim back for the incorrect sum.
General Electric Employee caught stealing trading secrets
General Electric, a US multinational corporation, discovered that an employee had stolen more than 8,000 confidential papers for eight years in July 2022. An employee named Jean Patrice Delia convinced an IT manager to give him access to private data, which he then stole to launch a competitor’s business. Delia had sent a co-conspirator commercially sensitive material through email, the FBI discovered after looking into the matter. After subsequently entering a guilty plea, he might have received a jail term of 87 months.
Conclusion
We examined insider threats and how organizations can develop tactics to combat such attacks. Since every employee might harm the company due to a lack of career advancement or financial benefit, eliminating internal risks is not viable. Insider threat dangers are unlikely to disappear soon, so combating such types of attacks is necessary.
Trickest platform can help you to automate much of the process of detecting and mitigating insider threats with the advanced workflow engine. If you'd like to explore more, visit our product page or request access immediately!
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
