Unified Dashboards for Everything Offensive Security
Discover how Trickest’s customizable dashboards unify offensive security data, improve visibility, and streamline vulnerability detection in real-time.
Introduction
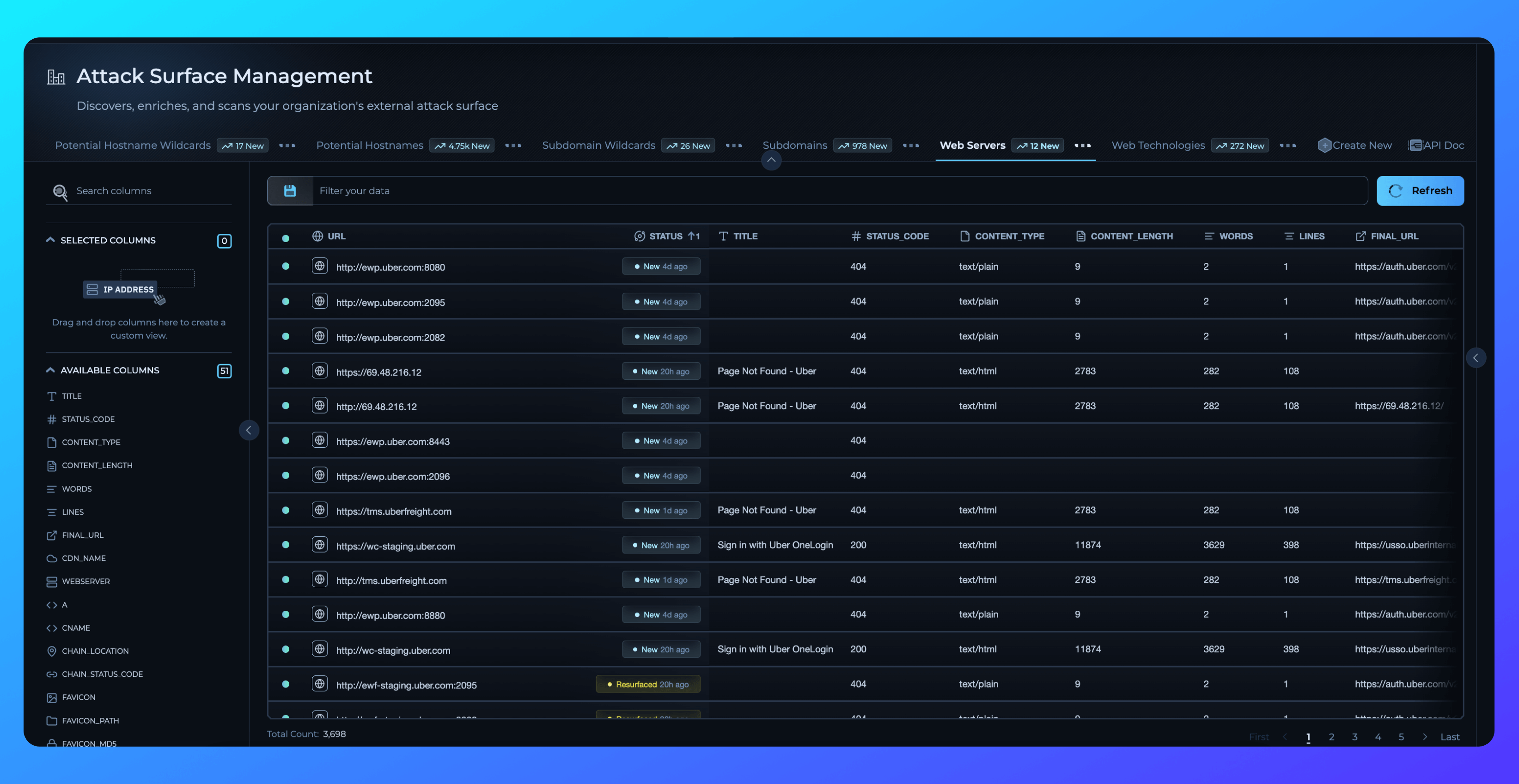
Command-line tools are crucial for security teams but often present a significant challenge—disorganized and inconsistent outputs. Each tool structures data differently, making unifying and interpreting results difficult. This lack of standardization creates significant pain points for teams, especially when time is tight. Security teams face the frustrating reality of manually normalizing data across tools, wasting valuable hours that could be spent identifying and addressing vulnerabilities.
At Trickest, we’ve developed Modules to solve this. They unify and standardize outputs across various tools, eliminating the chaos of mismatched data and making it easier for teams to collaborate and automate workflows. Modules directly address these pain points by allowing teams to focus on the core of their work—detecting vulnerabilities and improving security—rather than spending time reorganizing outputs.
Modules now come with Trickest’s customizable dashboards, offering data ingestion and insight at any volume of data.
They offer flexible layouts and smart filtering, allowing you to focus on the data that matters most. With statuses highlighting key changes—like new, missing, resurfaced, or removed keys—teams can make faster, more informed decisions.
The Challenge: Data Fragmentation in Offensive Security
Modern security operations face significant technical challenges:
- Data silos created by disparate security tools
- Inconsistent data formats hindering efficient analysis
- Limited visibility across the entire attack surface
- Difficulty in correlating findings from multiple sources
- Time-consuming manual processes for execution, data normalization, and reporting
These technical hurdles slow down security processes and lead to missed vulnerabilities and ineffective threat mitigation strategies.
Main Benefits
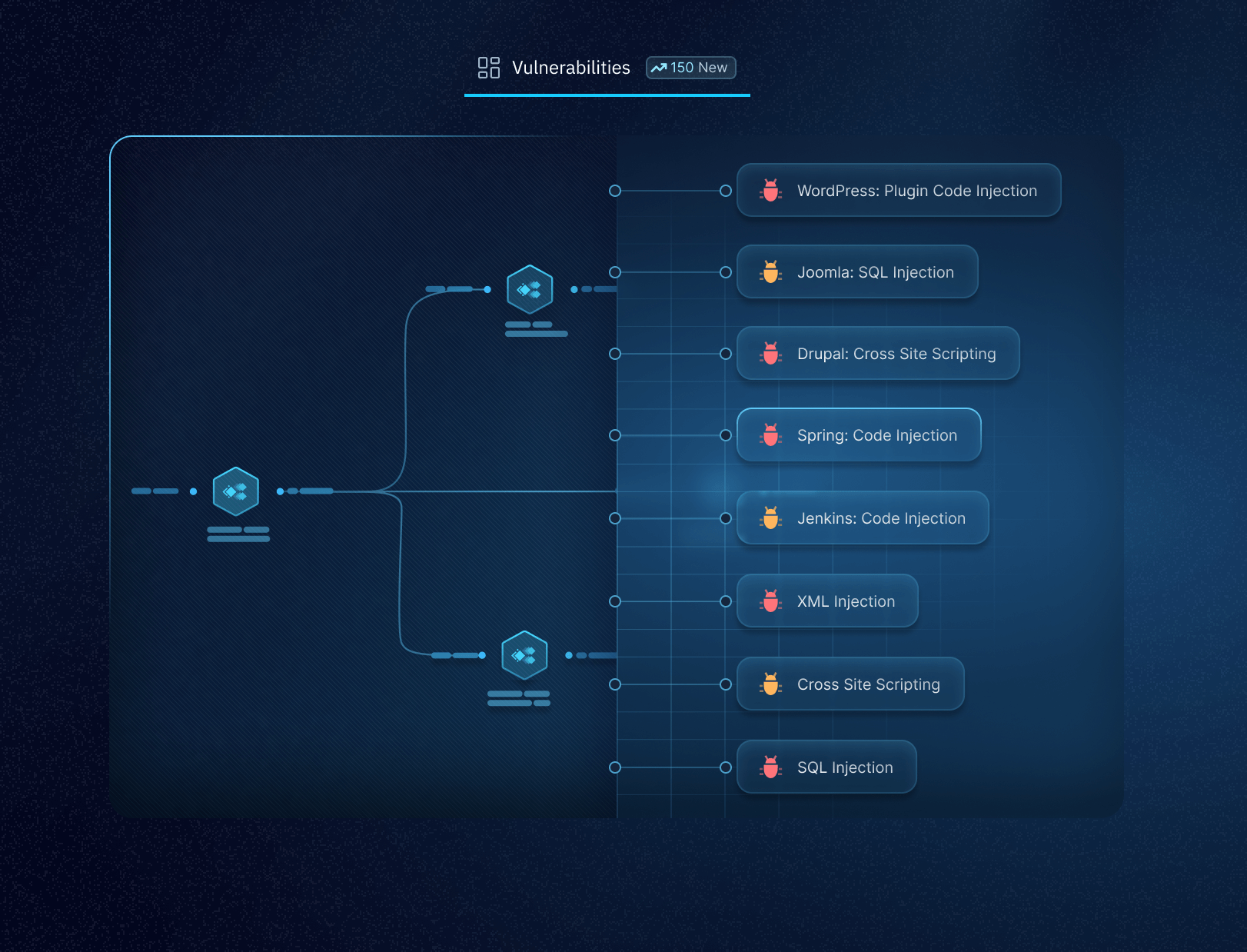
From managing vast security data to tracking historical changes, everything at Trickest is built with flexibility and customization in mind, ensuring your team can work smarter, not harder. Here’s a breakdown of the main benefits that make Trickest an indispensable tool for offensive security operations.
No matter the size, Trickest supports datasets ranging from just a few entries to billions, all stored in one centralized location for easy access. This makes it simple for teams to navigate, analyze, and act on the data, regardless of its volume.
Real-Time Data Processing Engine
Leveraging a high-performance, distributed processing architecture, Trickest's dashboards update in real time. This allows for immediate visibility into new vulnerabilities, changes in your attack surface, or emerging threats as soon as your security tools detect them.
Customizable Data Views
With our advanced data engine, you can build complex views of your security data. Trickest allows you to create the exact data views you need for deep, actionable insights.
Powerful Query Language for Advanced Filtering
Trickest incorporates a custom-built query language allowing complex, multi-condition filtering across all your aggregated data. This enables security professionals to quickly precisely isolate specific vulnerabilities, affected assets, or potential threat vectors.
API-Driven Architecture for Seamless Integration
Our RESTful API allows easy integration with your existing security workflow and automation tools. Pull aggregated data and integrate it with any existing systems.
Historical Tracking
Trickest's historical tracking makes tracking changes in your data effortless. You can easily see when critical data is newly discovered, resurfaced, or removed, giving your team a clear view of how your offensive security data evolves.
Conclusion
The threat landscape is evolving rapidly, and traditional, siloed approaches to security data management are no longer sufficient. Trickest's Dashboards equip your team with a state-of-the-art solution that sets a new standard for efficient, effective offensive security operations. Ready to experience the power of truly unified security data? Contact us today for an in-depth technical demonstration of how Trickest can revolutionize your offensive security operations. In cybersecurity, unified data isn't just an advantage – it's a necessity.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
