Continuous Automated Red Teaming (CART): A Comprehensive Guide
Explore Continuous Automated Red Teaming (CART) and its role in modern cybersecurity. Learn how automation and real-time testing boost your organization’s defenses.
In today's fast-paced digital environment, cybersecurity is not just about defense, but also about intelligent, proactive offense. This is where Continuous Automated Red Teaming (CART) steps in, reshaping how organizations approach their cybersecurity. At the heart of CART is the concept of simulating sophisticated cyber attacks continuously to test and improve defenses. This guide dives into the essence of CART, providing insights into its role in modern cybersecurity and illustrating its implementation in various scenarios.
Central to this exploration is Trickest, an all-in-one offensive security platform that simplifies the CART process. Trickest brings a unique blend of automation, scalability, and collaboration to red teaming exercises, offering security teams a dynamic platform to test, refine, and evolve their security strategies. With its open-source tool library and customizable workflow templates, Trickest enables offensive security professionals and teams to develop and respond to the ever-changing threat landscape.
As we navigate through this guide, we'll explore the layers of red teaming, understand its differences from traditional security practices, and see how continuous automation boosts these processes to new heights. Whether you're part of a red team, blue team, or anywhere in between, this guide aims to provide you with the knowledge and tools to effectively implement and benefit from continuous automated red teaming instantly.
Understanding Continuous Automated Red Teaming
Continuous Automated Red Teaming (CART) represents a significant evolution in offensive cybersecurity strategies. Diverging from traditional red team exercises, CART integrates automation and continuous testing, providing a more dynamic and thorough approach to security assessments. By continuously simulating a wide array of cyber-attacks, CART helps organizations identify and correct vulnerabilities in real time, offering a more proactive perspective in their red teaming efforts.
Unlike the periodic and often manual nature of conventional red teaming, CART leverages advanced technologies to conduct automated, ongoing security evaluations. This approach not only broadens the scope of security testing but also enhances its frequency, ensuring that an organization's defenses are constantly running against the latest threat tactics. CART's unique capability to autonomously deploy sophisticated attack techniques enables it to uncover vulnerabilities that may go unnoticed in traditional testing.
CART's effectiveness lies in its ability to simulate real-world attacks across an organization's entire digital infrastructure, providing a broad view of potential security gaps. This continuous and automated methodology contrasts traditional penetration testing, which might focus on a limited set of targets and often requires manual intervention. With CART, security teams gain the advantage of ongoing vigilance, allowing them to quickly identify and address security weaknesses before actual attackers can exploit them.
How Continuous Automated Red Teaming (CART) Works
At its core, CART is about simulating real-world cyberattacks in a systematic and ongoing manner. This methodology goes beyond the periodic, manual nature of traditional red team exercises:
-
By employing automation, CART continuously probes an organization's defenses.
-
It tests and retests security measures to identify vulnerabilities that actual attackers could exploit.
The process begins with CART tools mapping the organization's digital footprint, mimicking the recon tactics of sophisticated adversaries:
-
Identifying exposed credentials, vulnerable databases, unprotected assets, open ports, and other potential entry points.
-
CART then launches simulated multi-stage attacks designed to uncover attack paths and security blind spots, mimicking the actions of real threat actors.
One of the critical advantages of CART over traditional methods is its capacity for regular and extensive testing:
-
This continuous approach ensures that evaluating security systems is not just a one-time event but an ongoing process.
-
It adapts to new threats and vulnerabilities as they emerge, providing security teams timely insights into their system's resilience.
-
This allows for immediate and effective response strategies, benefiting other teams within the organization.
Benefits of Continuous Automated Red Teaming in Cybersecurity
Continuous Automated Red Teaming (CART) offers several key benefits to organizations striving to strengthen their defenses against sophisticated cyber threats:
-
Proactive Security Posture: CART enables organizations to adopt an expedited proactive approach by continuously identifying and addressing vulnerabilities. This ongoing process ensures that defenses always align with the evolving malicious hackers.
-
Efficiency and Resource Optimization: CART allows security teams to focus on creativity and strategic analysis by automating manual and repetitive tasks. This not only improves efficiency but also maximizes the use of limited cybersecurity resources.
-
Complete Coverage and Visibility: CART tools provide extensive coverage, scanning across the entire IT infrastructure. This all-around approach offers a clear view of potential security gaps and vulnerabilities.
-
Timeliness and Relevance: The continuous nature of CART ensures that security assessments are always up-to-date, reflecting the latest threat intelligence and attack methods. This real-time feedback loop allows for fast adaptation and response to threats.
-
Cost-Effectiveness: Implementing CART can lead to substantial cost savings. Identifying and addressing security issues early helps avoid the potentially higher costs of responding to and recovering from successful cyber attacks.
-
Enriched Detection and Response Capabilities: CART's continuous testing and monitoring improve an organization's ability to detect and respond to threats. This elevated detection capacity helps in mitigating risks more effectively.
-
Prioritized Remediation Efforts: Through its thorough testing, CART provides valuable insights into which vulnerabilities require immediate attention, enabling organizations to prioritize their remediation efforts effectively.
Implementing Continuous Automated Red Teaming with Trickest
Trickest's Offensive Security Orchestration Platform enables security teams to automate various attack simulations. It empowers Red and Purple Teams, MSSPs, and SecOps teams to run offensive security operations easily, and it plays a pivotal role for CART to organizations' red teams.
The platform is designed to address the complexities of CART with precision and scalability. With its advanced Visual Workflow Builder, security engineers can create and manage custom red teaming workflows in a few clicks. This innovative approach replaces the need for extensive scripting, making the process more accessible and efficient.
Key Features and Benefits
- Customized Offensive Security Workflows:
- Build and orchestrate tailored attack simulations using various tools and methodologies.
- Integrate custom Bash or Python scripts for a more personalized approach to CART.
- Exhaustive OS Tools Library:
- Access over 300 open-source offensive security tools you can drag-and-drop and connect into the visual editor.
- Run any of 90+ ready-made workflow templates for diverse scenarios like Attack Surface Management and Threat Intelligence.
- Hyper-Scalable Execution Engine:
- Benefit from Trickest's managed cloud infrastructure, which can cover extensive external and internal infrastructure.
- Schedule and run automated workflows for continuous and updated security assessments.
- Collaborative Offensive Security:
- Facilitate team collaboration with easy sharing of workflows and results.
- Enhance collective problem-solving and knowledge exchange within and across teams.
- Custom Solution Engineering:
- Tailor your security solutions with Trickest’s Solution Engineering service to meet specific organizational needs.
Practical Workflows in Red Teaming
Trickest serves as a multipurpose platform, catering to various aspects of CART:
Attack Surface Management
Trickest's workflow for Attack Surface Management - Asset Discovery & Vulnerability Scanning - is a thorough tool that combines passive and active methods to discover hostnames, enumerate web servers, scan for open ports, and uncover vulnerabilities. This workflow analyzes an organization's infrastructure, yielding detailed reports on vulnerabilities (ranked by severity), open ports, web server technologies, and more. The output, enriched with screenshots, provides an insightful overview of potential security gaps.

Threat Intelligence
The Shodan Threat Intelligence workflow utilizes the Shodan API to offer a rich array of organized data. It efficiently gathers information on hostnames and web servers and conducts port scans on collected IP addresses. This workflow transforms raw data into actionable intelligence, giving teams a clearer view of the digital threats landscape.

Network Scanning
ASN Based Network Scan workflow is a powerful tool for network analysis. It expands Autonomous System Numbers (ASNs) into CIDR ranges and conducts thorough port scans across the top 1000 ports. This workflow is instrumental in uncovering potential network vulnerabilities and securing network perimeters.

Web Application Vulnerability Scanning
The Fuzz web app for vulnerabilities workflow specializes in probing web applications for vulnerabilities. It employs advanced fuzzing techniques to detect and report potential security weaknesses, helping teams prioritize remediation efforts and strengthen web application defenses.

OSINT
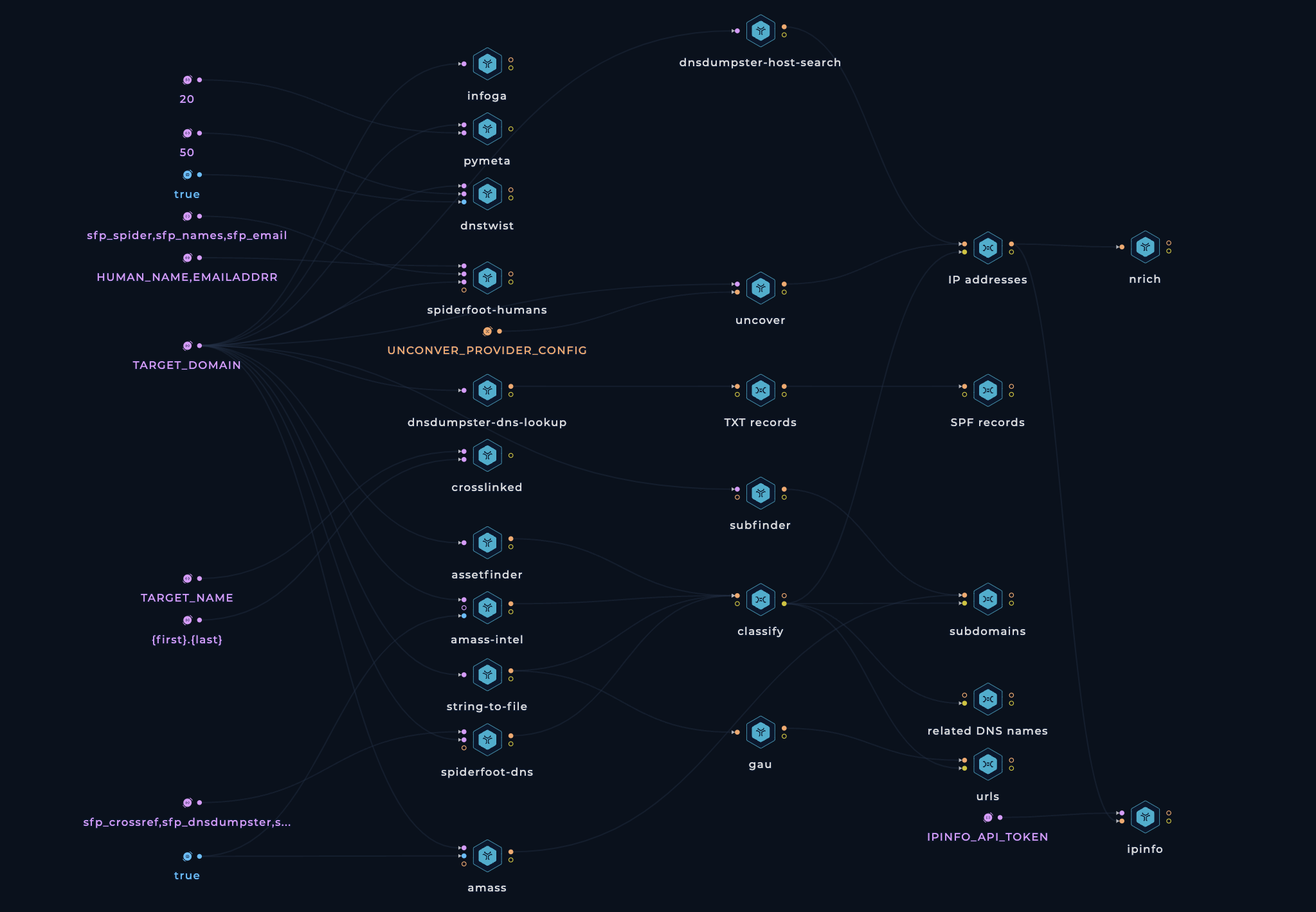
The Extensive OSINT workflow is an all-encompassing tool for gathering open-source intelligence. It collects a wide range of data, including IP addresses, open ports, vulnerabilities, technologies, DNS records, related domains, and more. This workflow aids threat analysts in understanding adversary tactics and strategies, contributing to a stronger defense mechanism against cyber threats.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
