How to Perform Threat Intelligence using Shodan & Trickest
Learn how to automate your threat intelligence work with a Trickest workflow to your advantage and stay one step ahead of the competition.
Do you know that your business is facing a threat? How do you know? Do you do an internal risk assessment every year?
It is not easy to get answers to these questions. The problem that most businesses face is that they don't know when they are under threat and how to manage it.
Threat Intelligence is an important aspect of making sure that you are running a safe business and that your data remains secure. This blog will look at different parts of this function and how you can implement it in our company.
What is threat intelligence?
Threat intelligence is a process of gathering, analyzing, and acting upon information that can help organizations protect themselves from potential threats.
It can come from various sources, including internal, external, and human intelligence. Internal data includes information about an organization's systems and networks, while external data includes information from the internet, social media, and other public sources. Human intelligence is information gathered by people, often through personal relationships or direct observation.
Threat intelligence must be timely, accurate, and actionable to be useful. It must also be tailored to an organization's specific needs, as different organizations will have different types of threats they need to protect against.
How can threat intelligence help you with security?
Threat intelligence is critical to security. It helps you understand the who, what, when, where, and why of attacks and provides actionable intelligence that can help thwart them. Also, it can help security teams make more informed decisions about protecting their systems and data. Without threat intelligence, you're essentially operating in the dark, and that's a recipe for disaster. Threat intelligence can help you in several ways.
Some of them include the following:
- It can help you identify potential threats and vulnerabilities. This information can then be used to harden your systems and make them more secure & less attractive targets for attackers.
- Threat intelligence can help you understand the motives and methods of attackers, which can give you insights into how to defend yourself better.
- Threat intelligence can help you stay ahead of the curve by providing advance warning of new attack methods and trends.
- Threat intelligence can also be used to monitor ongoing threats and assess the effectiveness of security measures.
Manual vs. automated threat intelligence: which one to choose?
The debate between manual and automated threat intelligence has been ongoing. There are pros and cons to both of these approaches, and ultimately the decision of which to use depends on the organization's specific needs.
Manual threat intelligence requires more workforce and resources but can be more thorough and customized to the organization's specific needs. Automated threat intelligence is more efficient and cost-effective, but it may not be as comprehensive as manual threat intelligence.
Companies should carefully consider their needs before deciding which approach to take. Manual threat intelligence is generally best for small organizations with limited resources, while automated threat intelligence is better suited for larger organizations.
Top 9 search engines used by hackers
Many tools are available for threat intelligence, but we wanted to cover nine we think are the most common.
Shodan
Shodan is a search engine that lets you find devices and systems connected to the internet. It gives you access to information about these devices and systems, including their location, hostnames, open ports, and running services. You can use it to find devices that are vulnerable to attack and monitor the internet for new devices and systems.
Censys
Censys is a search engine that enables researchers to query the internet's public resources. It provides access to network traffic data and allows users to explore the internet's infrastructure and services. Censys is also used to monitor Internet security threats and to research the security of Internet-connected devices.
Virus Total
Virus Total is a website that provides a free online service for scanning files and URLs for viruses, malware, and other malicious content. Security professionals and companies worldwide widely use it as a source of threat intelligence.
Google is one of the world's most popular and widely used search engines. It is also an excellent tool for threat intelligence. With its vast and constantly updated database, Google can be used to identify and track potential threats. Additionally, Google provides a variety of tools and resources that can be used to gather intelligence on potential threats.
Crt Sh
Crt.sh is a powerful tool for gathering threat intelligence that provides a searchable database of SSL/TLS certificates. This is a valuable resource for threat intelligence, as it can be used to identify patterns and trends in the issuance of certificates.
Hunter.io
Hunter.io is an excellent search engine for security professionals that allows you to find email addresses for people and businesses. You can search for a specific person or company or browse through their directory of people and businesses.
Dehashed
Dehashed is a website that allows users to search for and view leaked data. The website includes a database of leaked records, including email addresses, user names, passwords, and sensitive personal information. Dehashed also allows users to search for and view data from over 100,000 hacked websites.
PublicWWW
PublicWWW is a public search engine that enables users to search for websites that contain a given piece of code or keyword. This makes it a valuable tool for security engineers who want to find websites that use a particular technology or to identify websites that are relevant to their scope of testing. PublicWWW also offers an API that allows developers to access its data for use in their applications.
Have I Been Pwned
Have I Been Pwned (HIBP) is a website that allows users to check whether their personal data has been compromised in a data breach. The website provides a searchable database of data breaches and a notification service that alerts users if their email address has been involved in a breach.
What is Shodan Threat Intelligence?
Shodan is a powerful tool used for threat intelligence that can be used to gather information about potential threats. It can be used to identify vulnerable systems and collect information about the people and organizations behind potential attacks. It can also be used to monitor ongoing attacks and to track the movement of malware and other malicious actors.
Shodan can also be used to gather information about devices and networks. This information can be used to identify trends and patterns and understand the internet's infrastructure.
But implementing all this on a scale is such a tedious task. This is where Trickest comes into the picture.
Automating threat intelligence with Shodan & Trickest
We have discussed what Shodan is and how it can be used for threat intelligence, but doing it manually is a waste of time and resources for any organization. Organizations all across the globe use Trickest to automate manual tasks such as this in the form of workflows.
If you plan to create your workflow for Shodan, you don't have to, as we already have one in the Library. To use this workflow, you'll need:
- Shodan API Key
- Trickest Account (talk with us if you don't already have one)
- Name of organization
Once you copy the workflow from the Library, it's time to configure it per our use case. In this guide, we won't be making any changes in the workflow.
To run this workflow, we need to provide the API key to the workflow. On the left side of the workflow, you can see two purple blocks; these are the two string inputs (check the inputs tab to know more). Select them to enter the API key and the organization name.

Once done, it's time to run the workflow. Click on the Play button to run the workflow. You can track your previous runs from the Runs tab.
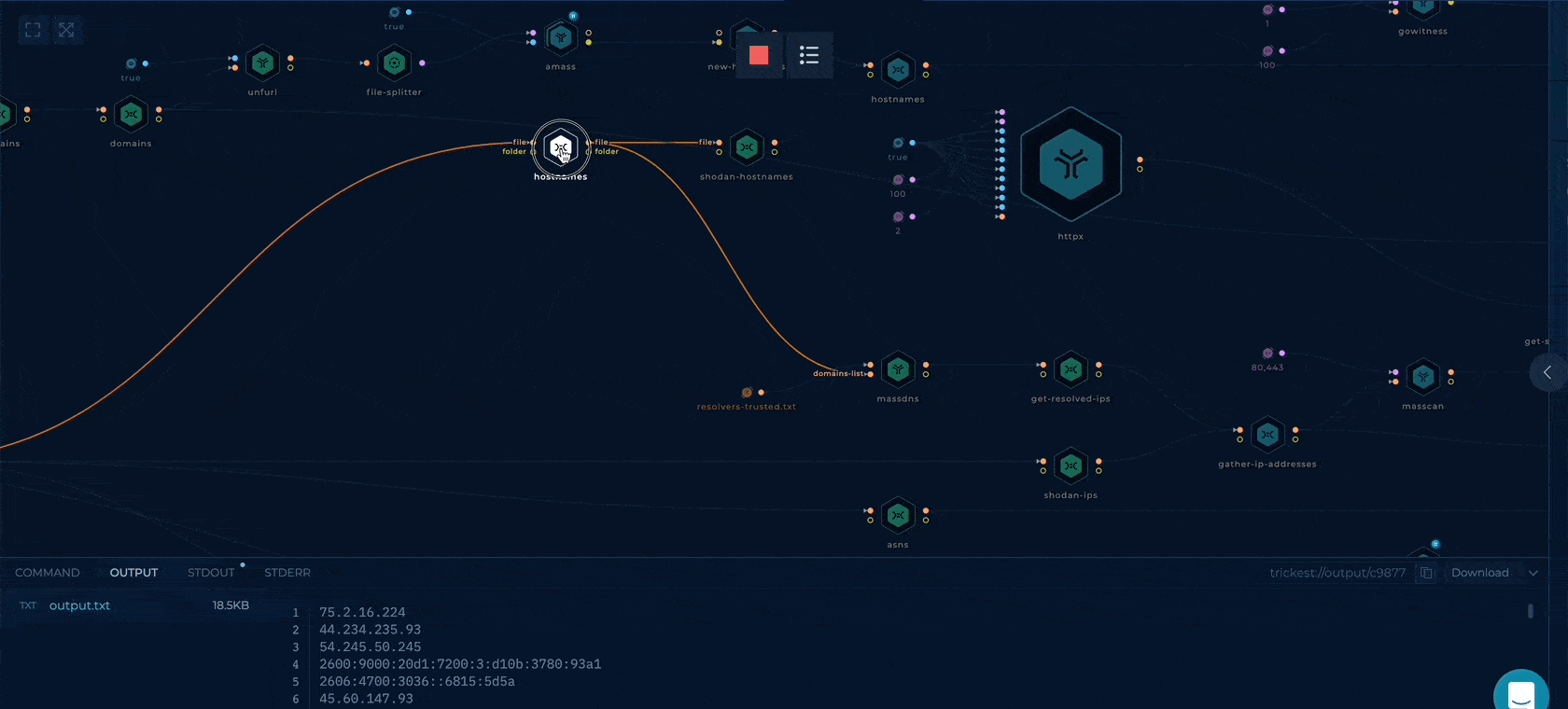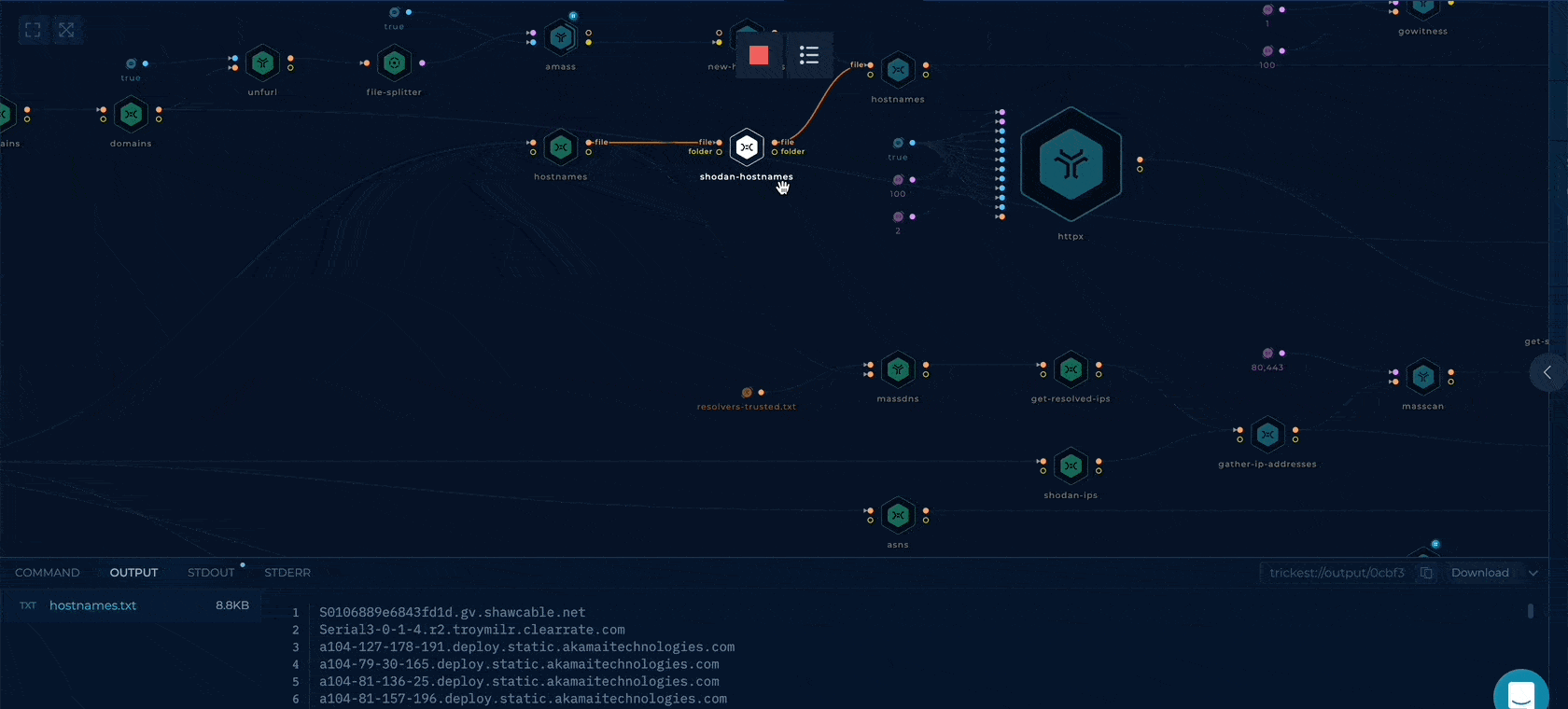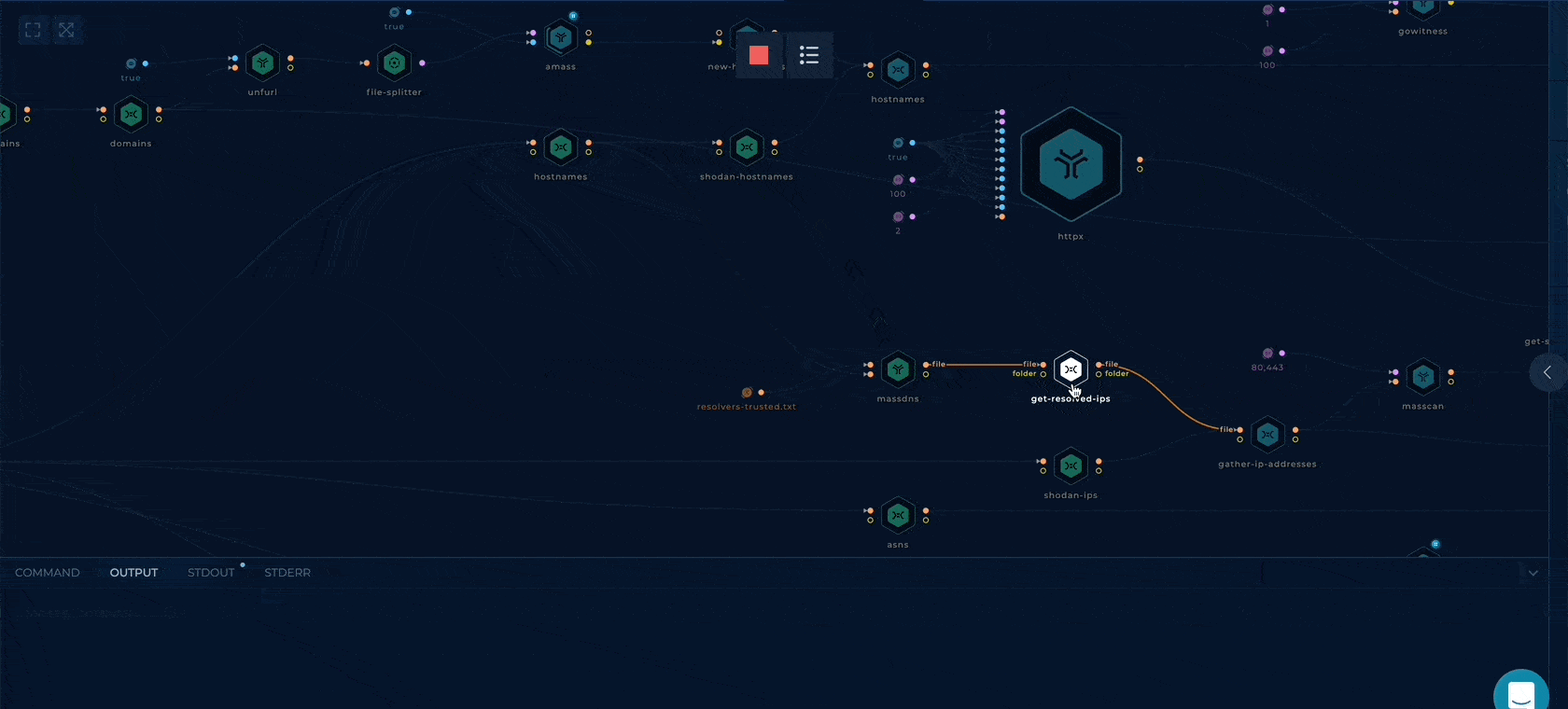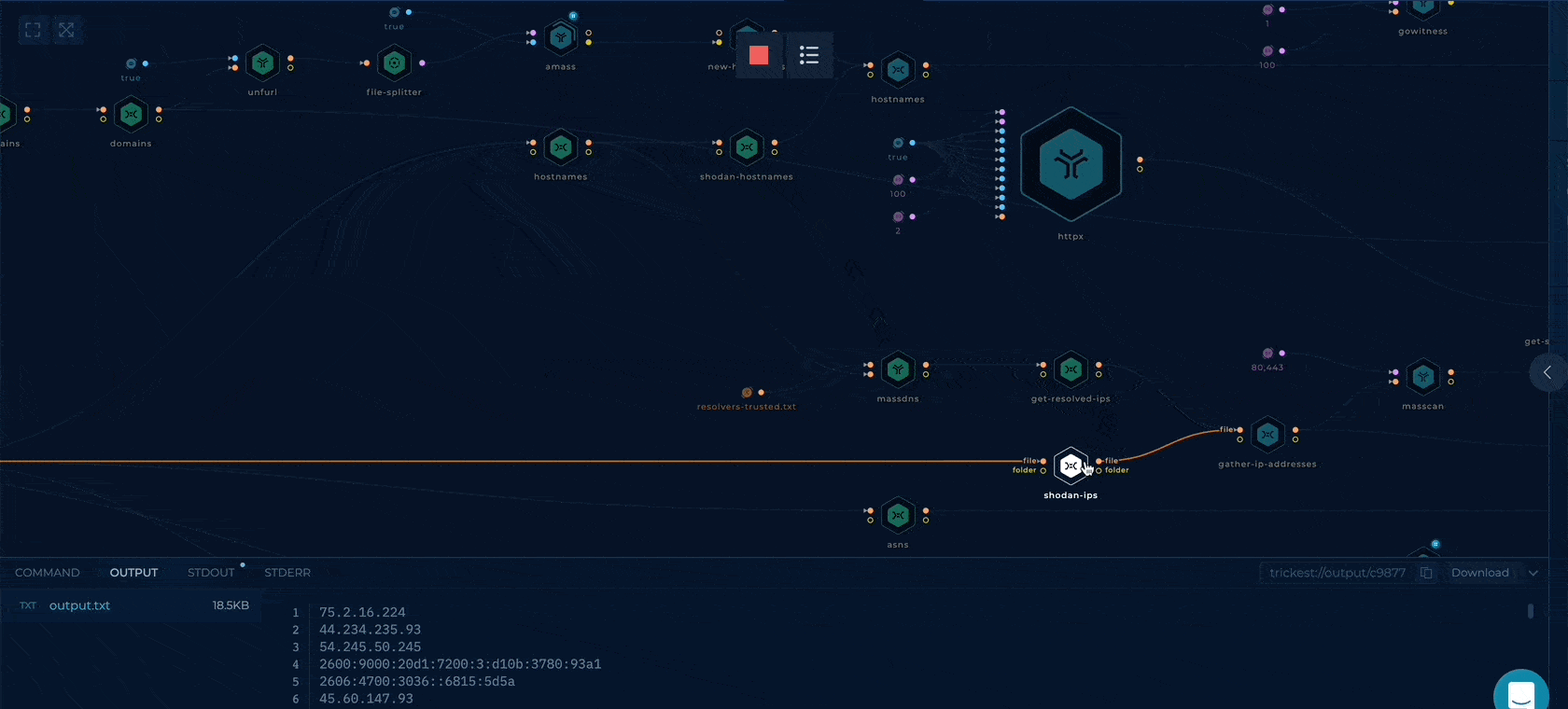
Note: Click on any node and check the Command & Output tab (bottom of the screen) to understand the function of the specific node.
Once the run is complete, click on the last node, ZIP-TO-OUT, and from the output tab (bottom of the screen), click on output.zip and then download. The zip contains all the relevant information the workflow could find about the organization from Shodan. Unzip the output.zip and use the data as per your use case.
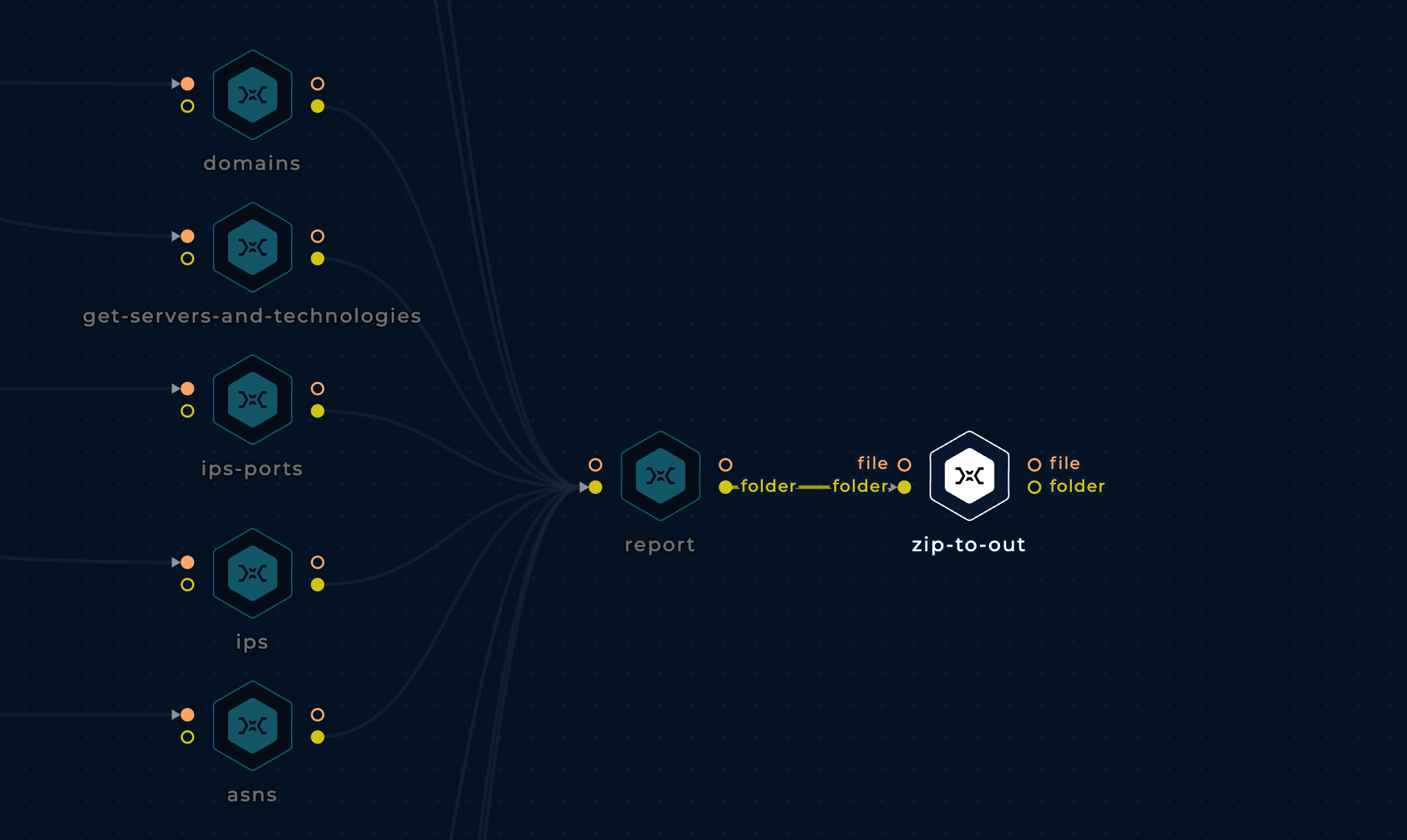
Feel free to edit the workflow, add or remove nodes, and tailor it to your needs.
Wrapping up
It is more important than ever for enterprises to monitor their security environment and make decisions based on the information they gather. So, how does threat intelligence help? It enables you to identify threats, understand the impact/risk of incidents, classify and prioritize the threats, and respond effectively. It is also a proactive way to identify threats and incidents before they impact you.
If you are looking to automate threat intelligence, you don't have to look any further. Talk with us in Trickest and with Shodan workflow, you can analyze the threat data, share the information with your security teams, and integrate the data into your existing tools.
Get a PERSONALIZED DEMO
See Trickest
in Action
Gain visibility, elite security, and complete coverage with Trickest Platform and Solutions.
